SharePoint 2016 MIM and SAML/FBA User Profiles
There is not much out there about MIM and SharePoint 2016 with FBA or SAML user profiles. Using Active Directory Import is still the same as it was in 2013. Below we will be going through how to set this up for SAML(ADFS) and MIM.
This guide assumes the environment has been setup from these steps at https://technet.microsoft.com/en-us/library/mt637055(v=office.16).aspx
Why should we do this?
The account name for user profiles are important and what is used to get the profile. Windows Authentication user profiles are just "domain\username" for the account name. When SAML or FBA users invoke the user profiles, the profile service will search for the complete claim(example: "i:05.t|adfs30|User1"). If the user profile is not there, a stub profile will be created. This will give the user two profiles. The main one with SAML/FBA will NOT be sync'd since we would need configure MIM know the claim prefix.
1. Open MIM client then Metaverse Designer. Select "person" then "Add Attribute".
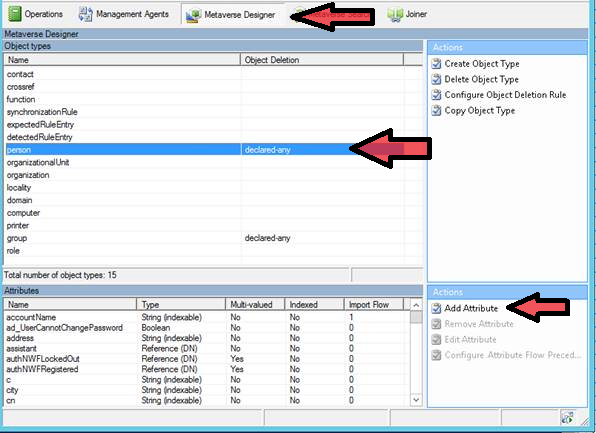
New Attribute button.
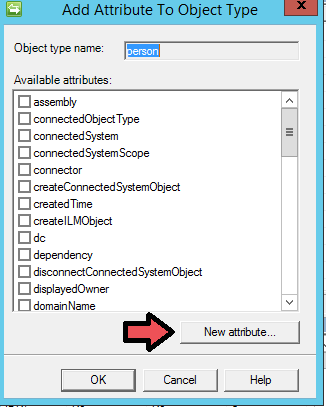
Type in "SPS-ClaimID" for Attribute Name
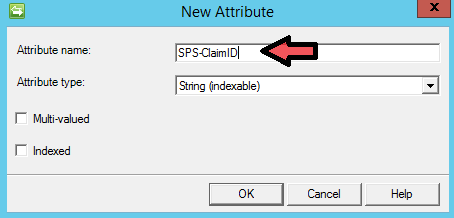
Click OK
2. Open the ADMA then Configure Attribute Flow. Select user/person

a. Map your Claim identifier for your SAML users to SPS-ClaimID. The direction should be Import and Direct.

b. Click "New".
Find SPS-ClaimProviderType and SPS-ClaimProviderID in MetaVerse object type. Below is PowerShell to find your SAML Identity Claim.
$tips = Get-SPTrustedIdentityTokenIssuer foreach($tip in $tips) { $name = $tip.Name $claims = $tip.ClaimTypeInformation foreach($claim in $claims) { If($claim.IsIdentityClaim -eq $true) { Write-Host -ForegroundColor DarkGreen "The Identity Claim is listed below for $name" $claim } }} |

Select "Advanced" for "Mapping type" and "Import" for Direction. Click New.
The constant value SPS-ClaimProviderID will be the name of your SAML provider when you created it.
SPS-ClaimProviderType will be "Trusted" if you're using a Trusted provider.

3. Open SharePoint MA(SPMA). Click on Select Attributes. Check the box for SPS-ClaimID.
4. Configure Attribute Flow. Select user/person.
a. Map SPS-ClaimID to SPS-ClaimID. The direction will be export and Direct. Click new.
I'm using UPN for my environment. This will be the identifier claim which could be email or samaccountname(see above for PowerShell).

5. Run a full sync
Comments
- Anonymous
August 23, 2017
Understatement of the year 'not much out there about MIM and SharePoint 2016 with FBA or SAML '. You are my hero, thanks!- Anonymous
September 16, 2017
Glad I could help!
- Anonymous
- Anonymous
June 28, 2018
Do you have experience with Search Alerts in connection with a SAML based IDP in 2016? We have a couple customers that are having issues with this. We have tried specifying the above mentioned properties in their user profiles and keep getting a "Error trying to search in the UPA. The exception message is 'System.ArgumentException: Exception of type 'System.ArgumentException' was thrown. Parameter name: value" error.Any help would be greatly appreciated.- Anonymous
June 28, 2018
I would check to make sure the User Profiles are being imported with the correct claim. Do you have a complete call stack?- Anonymous
June 28, 2018
So there's the rub, we are not importing at all. The identity provider is external. We are consuming their SAML 2.0 claim and then issuing a SAML 1.1 claim via a gateway. The good news is we have complete control over the SAML assertion coming in but there is no possible way that we can sync sharepoint user profiles with anything. The id provider is in of itself a federation with trusts of other identity providers.Error trying to search in the UPA. The exception message is 'System.ArgumentException: Exception of type 'System.ArgumentException' was thrown. Parameter name: value at Microsoft.SharePoint.Administration.Claims.SPIdentityProviders.GetIdentityProviderType(String value) at Microsoft.Office.Server.Security.UserProfileIdentityClaimMapper.SearchUsingNameIdOrThrow(UserProfileManager upManager, String nameId, String nameIdIssuer) at Microsoft.Office.Server.Security.UserProfileIdentityClaimMapper.GetSingleUserProfileFromClaimsList(UserProfileManager upManager, IEnumerable1 identityClaims)'The only place im seeing this error talked about is relating to either workflows or hybrid spo search. I feel that the underlying problem is sharepoints attempt to rehydrate the claim.The two additional unexpecteds are:STS Call Claims Saml: Problem getting output claims identity. Exception: 'System.InvalidOperationException: Exception of type 'System.ArgumentException' was thrown. Parameter name: value ---> System.ArgumentException: Exception of type 'System.ArgumentException' was thrown. Parameter name: value at Microsoft.SharePoint.Administration.Claims.SPIdentityProviders.GetIdentityProviderType(String value) at Microsoft.Office.Server.Security.UserProfileIdentityClaimMapper.SearchUsingNameIdOrThrow(UserProfileManager upManager, String nameId, String nameIdIssuer) at Microsoft.Office.Server.Security.UserProfileIdentityClaimMapper.GetSingleUserProfileFromClaimsList(UserProfileManager upManager, IEnumerable1 identityClaims) - -- End of inner exception stack trace --- at Microsoft.Office.Server.Security.UserProfileIdentityClaimMapper.GetSingleUserProfileFromClaimsList(UserProfileManager upManager, IEnumerable1 identityClaims) at Microsoft.Office.Server.Security.UserProfileIdentityClaimMapper.c__DisplayClass6.b__0() at Microsoft.SharePoint.Utilities.SecurityContext.RunAsProcess(CodeToRunElevated secureCode) at Microsoft.SharePoint.SPSecurity.RunWithElevatedPrivileges(WaitCallback secureCode, Object param) at Microsoft.SharePoint.SPSecurity.RunWithElevatedPrivileges(CodeToRunElevated secureCode) at Microsoft.Office.Server.Security.UserProfileIdentityClaimMapper.GetMappedIdentityClaim(Uri context, IEnumerable1 identityClaims) at Microsoft.SharePoint.IdentityModel.SPIdentityClaimMapperOperations.GetClaimFromExternalMapper(Uri contextUri, List1 claims) at Microsoft.SharePoint.IdentityModel.SPIdentityClaimMapperOperations.ResolveUserIdentityClaim(Uri contextUri, ClaimCollection inputClaims) at Microsoft.SharePoint.IdentityModel.SPIdentityClaimMapperOperations.GetIdentityClaim(Uri contextUri, ClaimCollection inputClaims, SPCallingIdentityType callerType) at Microsoft.SharePoint.IdentityModel.SPSecurityTokenService.GetLogonIdentityClaim(SPRequestInfo requestInfo, IClaimsIdentity inputIdentity, IClaimsIdentity outputIdentity, SPCallingIdentityType callerType) at Microsoft.SharePoint.IdentityModel.SPSecurityTokenService.EnsureSharePointClaims(SPRequestInfo requestInfo, IClaimsIdentity outputIdentity, SPCallingIdentityType callerType) at Microsoft.SharePoint.IdentityModel.SPSecurityTokenService.AugmentOutputIdentityForRequest(SPRequestInfo requestInfo, IClaimsIdentity outputIdentity) at Microsoft.SharePoint.IdentityModel.SPSecurityTokenService.GetOutputClaimsIdentity(IClaimsPrincipal principal, RequestSecurityToken request, Scope scope)'.and STS Call Claims Saml: Problem getting token lifetime. Exception: 'System.InvalidOperationException: Exception of type 'System.ArgumentException' was thrown. Parameter name: value ---> System.ArgumentException: Exception of type 'System.ArgumentException' was thrown. Parameter name: value at Microsoft.SharePoint.Administration.Claims.SPIdentityProviders.GetIdentityProviderType(String value) at Microsoft.Office.Server.Security.UserProfileIdentityClaimMapper.SearchUsingNameIdOrThrow(UserProfileManager upManager, String nameId, String nameIdIssuer) at Microsoft.Office.Server.Security.UserProfileIdentityClaimMapper.GetSingleUserProfileFromClaimsList(UserProfileManager upManager, IEnumerable1 identityClaims) - -- End of inner exception stack trace --- at Microsoft.Office.Server.Security.UserProfileIdentityClaimMapper.GetSingleUserProfileFromClaimsList(UserProfileManager upManager, IEnumerable1 identityClaims) at Microsoft.Office.Server.Security.UserProfileIdentityClaimMapper.c__DisplayClass6.b__0() at Microsoft.SharePoint.Utilities.SecurityContext.RunAsProcess(CodeToRunElevated secureCode) at Microsoft.SharePoint.SPSecurity.RunWithElevatedPrivileges(WaitCallback secureCode, Object param) at Microsoft.SharePoint.SPSecurity.RunWithElevatedPrivileges(CodeToRunElevated secureCode) at Microsoft.Office.Server.Security.UserProfileIdentityClaimMapper.GetMappedIdentityClaim(Uri context, IEnumerable1 identityClaims) at Microsoft.SharePoint.IdentityModel.SPIdentityClaimMapperOperations.GetClaimFromExternalMapper(Uri contextUri, List`1 claims) at Microsoft.SharePoint.IdentityModel.SPIdentityClaimMapperOperations.ResolveUserIdentityClaim(Uri contextUri, ClaimCollection inputClaims) at Microsoft.SharePoint.IdentityModel.SPIdentityClaimMapperOperations.GetIdentityClaim(Uri contextUri, ClaimCollection inputClaims, SPCallingIdentityType callerType) at Microsoft.SharePoint.IdentityModel.SPSecurityTokenService.GetLogonIdentityClaim(SPRequestInfo requestInfo, IClaimsIdentity inputIdentity, IClaimsIdentity outputIdentity, SPCallingIdentityType callerType) at Microsoft.SharePoint.IdentityModel.SPSecurityTokenService.EnsureSharePointClaims(SPRequestInfo requestInfo, IClaimsIdentity outputIdentity, SPCallingIdentityType callerType) at Microsoft.SharePoint.IdentityModel.SPSecurityTokenService.AugmentOutputIdentityForRequest(SPRequestInfo requestInfo, IClaimsIdentity outputIdentity) at Microsoft.SharePoint.IdentityModel.SPSecurityTokenService.GetOutputClaimsIdentity(IClaimsPrincipal principal, RequestSecurityToken request, Scope scope) at Microsoft.SharePoint.IdentityModel.SPSecurityTokenService.GetTokenLifetimeForOAuthRequest() at Microsoft.SharePoint.IdentityModel.SPSecurityTokenService.GetTokenLifetime(SPRequestInfo requestInfo, Lifetime requestLifetime)'.
- Anonymous
- Anonymous
- Anonymous
January 03, 2019
Hello Adam,I configured my MIM and followed all the steps as mentioned in the blog but the adfs user profiles are not getting synced with user profile service application in SharePoint. Only after the user visits the site , i am able to see his adfs claims profiles in the user profile service application for SharePoint . Following are my doubts related to the steps you mentioned in the blog :-Doubt no 1 :- In step no 2.b , when you enter the constant value for ClaimProviderID you have mentioned ADFS30. My doubt is should it be ADFS3.0 or ADFS30 ?Doubt no 2 :- Similarly in step no 2.b , should i enter the value of Claim Provider type as trusted in the constant option . I didn't get where to enter the trusted value as mentioned by you in the blog.Can you please help me with this Adam ?- Anonymous
January 03, 2019
I will try to clarify what is needed to put in.SPS-ClaimProviderType = "Trusted" -- Trusted for SAML(ADFS)SPS-ClaimProviderID = Name of your trusted provider. We can get that by running the PowerShell belowGet-SPTrustedIdentityTokenIssuer | select nameThis blog is moving to https://adamsorenson.com and this post is migrating to https://adamsorenson.com/sharepoint-2016-mim-and-samlfba-user-profiles/
- Anonymous
- Anonymous
April 16, 2019
Thanks a lot :)- Anonymous
April 24, 2019
Glad it could help. I have migrated this blog to https://adamsorenson.com. New posts are there.
- Anonymous