Hi,
I seem to run into an issue when deploying a private endpoint for Azure Event Hubs or Azure Redis Cache (on the same tenant and subscription).
I'm automating the deployment with bicep templates (see below), and I deploy a "Private Dns Zone Group", as advised in the tutorial https://learn.microsoft.com/en-us/azure/private-link/create-private-endpoint-template.
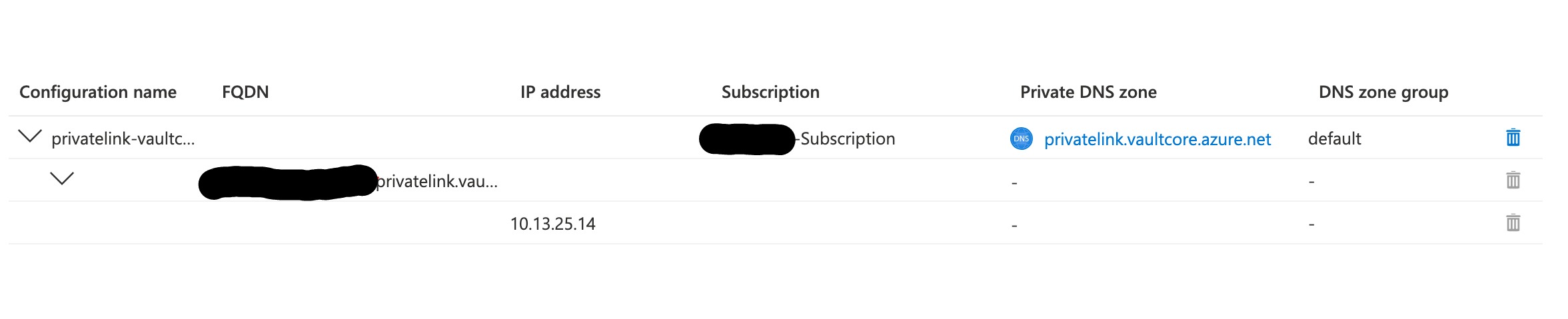
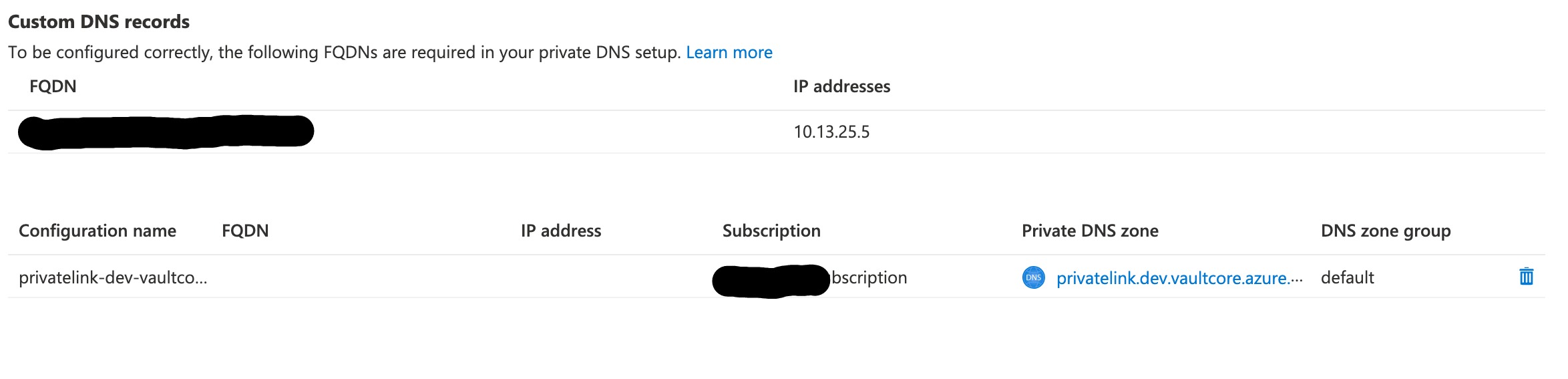
However when the deployment is done (successful), there is no record in the private DNS zone, so applications in the Vnet cannot resolve the service's private link domain (e.g. privatelink.redis.cache.windows.net). I used az network private-endpoint dns-zone-group list to see if the zone's status is correct:
[
{
"etag": "W/\"75028c29-638c-444a-b5e9-260eeded5a48\"",
"id": "/subscriptions/SUBSCRIPTION_ID/resourceGroups/RESOURCE_GROUP_ID/providers/Microsoft.Network/privateEndpoints/pe-redis-cache/privateDnsZoneGroups/default-zone-group",
"name": "default-zone-group",
"privateDnsZoneConfigs": [
{
"etag": "W/\"75028c29-638c-444a-b5e9-260eeded5a48\"",
"id": "/subscriptions/SUBSCRIPTION_ID/resourceGroups/RESOURCE_GROUP_ID/providers/Microsoft.Network/privateEndpoints/pe-redis-cache/privateDnsZoneGroups/default-zone-group/privateDnsZoneConfigs/pe-redis-cache-dns-zone-group-config",
"name": "pe-redis-cache-dns-zone-group-config",
"privateDnsZoneId": "/subscriptions/SUBSCRIPTION_ID/resourceGroups/RESOURCE_GROUP_ID/providers/Microsoft.Network/privateDnsZones/privatelink.redis.cache.windows.net",
"recordSets": [
{
"fqdn": "redis-internal-blabla.privatelink.redis.cache.windows.net",
"ipAddresses": [
"11.2.0.5"
],
"provisioningState": "Succeeded",
"recordSetName": "redis-internal-blabla",
"recordType": "A",
"ttl": 10
}
],
"resourceGroup": "RESOURCE_GROUP_ID",
"type": "Microsoft.Network/privateEndpoints/privateDnsZoneGroups/privateDnsZoneConfigs"
}
],
"provisioningState": "Succeeded",
"resourceGroup": "RESOURCE_GROUP_ID",
"type": "Microsoft.Network/privateEndpoints/privateDnsZoneGroups"
}
]
Everything seems fine but there is still no record. When I create the endpoint or even the DNS config manually via the portal, a record is correctly created. I checked the automation template suggested after the manual creation, and it's fundamentally the same as my bicep template.
Is there something I am missing? Should I also manually create the A record in the DNS zone?
Bicep template:
@minLength(1)
param privateEndpointsSubnetId string
@minLength(1)
param privateEndpointName string
@minLength(1)
param targetPrivateLinkResouceId string
@minLength(1)
//already created
param privateDnsZoneId string
@allowed([
'redisCache'
'namespace' // (event hub namespace)
])
@description('See https://learn.microsoft.com/en-us/azure/private-link/private-endpoint-dns#azure-services-dns-zone-configuration for the list of subresources. Make sure it matches the target resource.')
param targetSubResource string
@description('Tags to add to resources deployed by this template')
param commonTags object
resource privateEndpoint 'Microsoft.Network/privateEndpoints@2021-02-01' = {
name: privateEndpointName
location: resourceGroup().location
properties: {
subnet: {
id: privateEndpointsSubnetId
}
privateLinkServiceConnections: [
{
name: privateEndpointName
properties: {
privateLinkServiceId: targetPrivateLinkResouceId
groupIds: [
targetSubResource
]
}
}
]
}
tags: commonTags
}
resource privateDnsZoneGroup 'Microsoft.Network/privateEndpoints/privateDnsZoneGroups@2021-02-01' = {
name: 'default-zone-group'
parent: privateEndpoint
properties: {
privateDnsZoneConfigs: [
{
name: '${privateEndpointName}-dns-zone-group-config'
properties: {
privateDnsZoneId: privateDnsZoneId
}
}
]
}
}