Hello @Surjeet Singh,
Thank you for posting your query on Microsoft Q&A.
Please note that there are certain effective ways to manage external third parties in Microsoft Entra ID and limiting access to only a select number of staff members (e.g., 10) from the target.com domain to access your tenants and apps, rather than granting access to the entire organization.
1.Configure External Collaboration Settings:
You can specify what roles in your organization can invite external users for B2B collaboration. This includes options for allowing or blocking specific domains and restricting what external guest users can see in your Microsoft Entra directory.
2.Guest User Access:
By default, Guest users have limited access. You can configure the level of access guest users have, such as allowing them to view only their own profile information or restricting their view of group memberships.
3.Allow or Block Domains:
You can use collaboration restrictions to allow or deny invitations to specific domains. This ensures that only users from whitelisted domains can be invited.
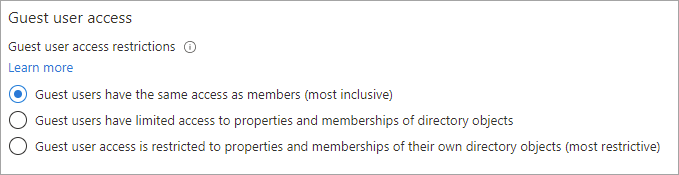
To configure guest user access
Sign in to the Microsoft Entra admin center.
Browse to Identity > External Identities > External collaboration settings.
- Under Guest user access, choose the level of access you want guest users to have:
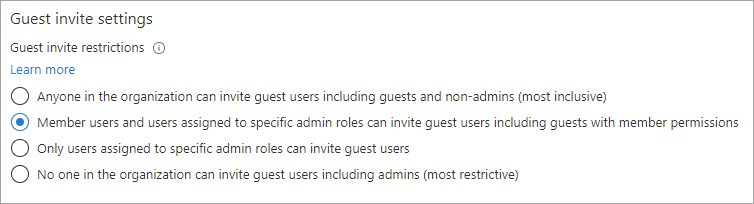
To configure guest invite settings
Sign in to the Microsoft Entra admin center.
Browse to Identity > External Identities > External collaboration settings.
Under Guest invite settings, choose the appropriate settings:
Add an allowlist
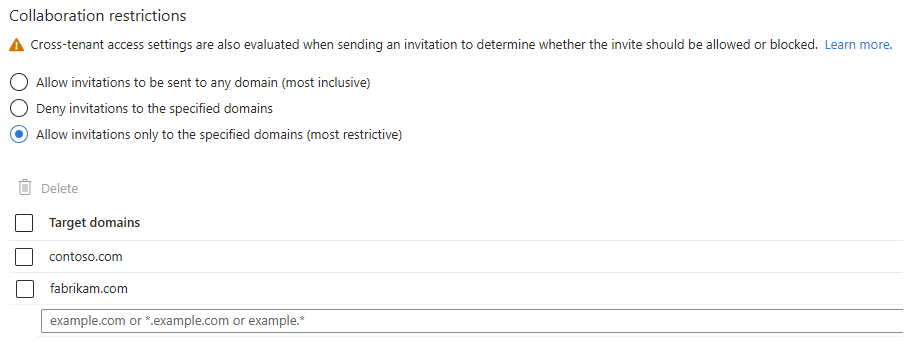
With this more restrictive configuration, you can set specific domains in the allowlist and restrict invitations to any other organizations or domains that aren't mentioned.
To add an allowlist:
Sign in to the Microsoft Entra admin center as a Global Administrator.
Browse to Identity > External Identities > External collaboration settings.
Under Collaboration restrictions, select Allow invitations only to the specified domains (most restrictive).
Under Target domains, enter the name of one of the domains that you want to allow. For multiple domains, enter each domain on a new line. For example:
When you're done, select Save.
After you set the policy, if you try to invite a user from a domain that's not on the allowlist, you receive a message saying that the domain of the user is currently blocked by your invitation policy.
For B2B collaboration with other Microsoft Entra organizations, you should also review your cross-tenant access settings to ensure your inbound and outbound B2B collaboration and scope access to specific users, groups, and applications.
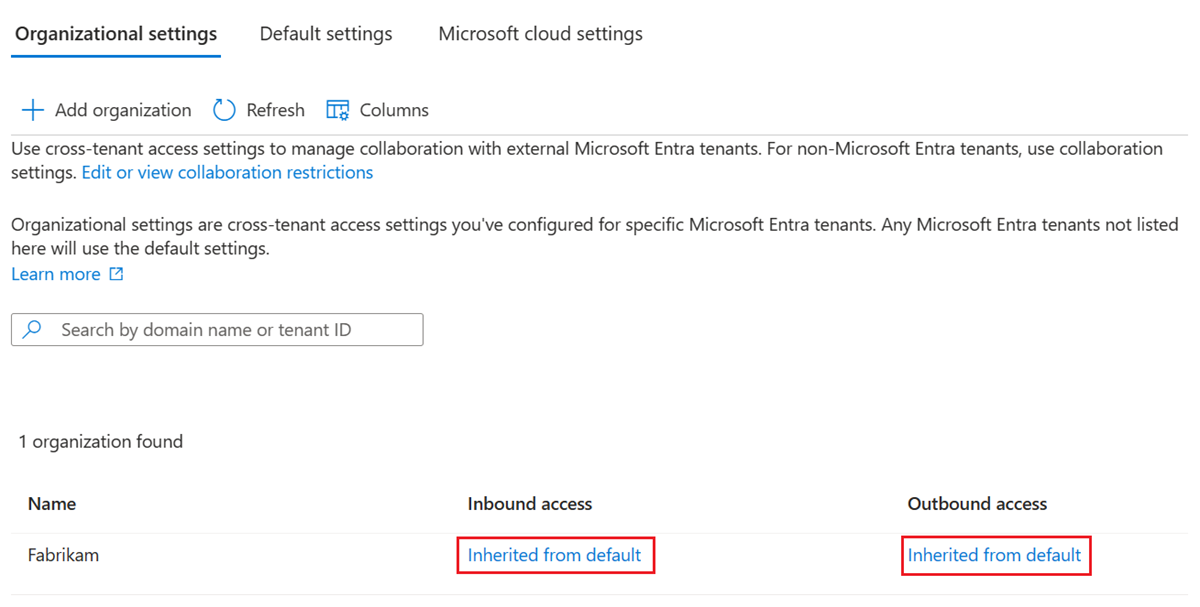
Add an organization
Please follow these below steps to configure customized settings for specific organizations.
- Sign in to the Microsoft Entra admin center as at least a Security Administrator.
- Browse to Identity > External Identities > Cross-tenant access settings, then select Organizational settings.
- Select Add organization.
- On the Add organization pane, type the full domain name (or tenant ID) for the organization.
5. Select the organization in the search results, and then select Add.
- The organization appears in the Organizational settings list. At this point, all access settings for this organization are inherited from your default settings. To change the settings for this organization, select the Inherited from default link under the Inbound access or Outbound access column.
- Modify the organization's settings by following the detailed steps in these sections:
For more additional information, please refer to the below documents for your reference.
B2B guest user properties - Microsoft Entra External ID | Microsoft Learn
Configure external collaboration - Microsoft Entra External ID | Microsoft Learn
Cross-tenant access settings - Microsoft Entra External ID | Microsoft Learn
Allow or Block Invitations - Microsoft Entra External ID | Microsoft Learn
I hope this above information provided is helpful. Please feel free to reach out if you have any further questions.
If the answer is helpful, please click "Accept Answer" and kindly upvote it. If you have extra questions about this answer, please click "Comment".