Hi @Chris Crawshaw
Greeting! Welcome to Microsoft Q&A Forum. Thanks for posting your query here!
The error message AuthorizationPermissionMismatch indicates that the permissions assigned to AAD account are not sufficient to perform the requested operation on the Azure Table Storage.
However, since you have already mentioned that you have given the multiple roles to the user, including Storage Table Data Contributor.
In your storage account check if you have below roles assigned, if not please assign the below roles from screen shot as well as add Storage Blob Data Contributor, Storage Queue Data Contributor and ``Storage Queue Data Reader roles. 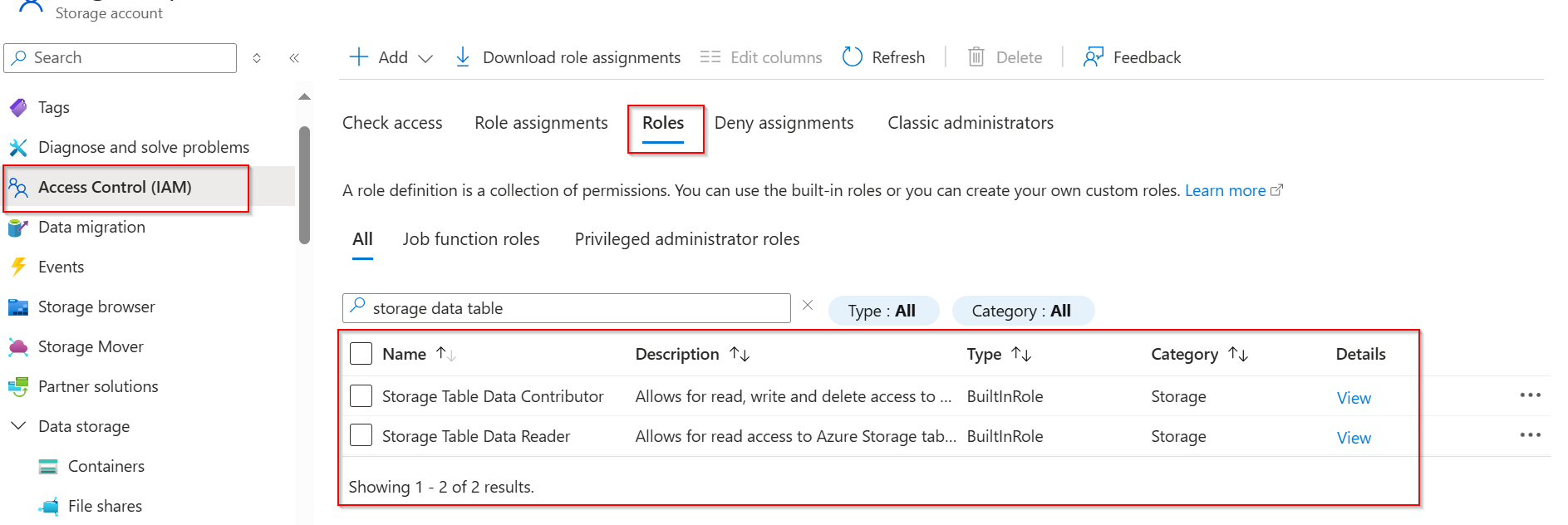
If the above roles are already assigned, please make sure that roles are given at the Storage account level. These roles must be assigned to the specific storage account, not only at resource group level or subscription level.
Azure has azure-built-in-roles-for-blobs please follow the link and make you have the appropriate roles at storage account level.
Sometimes, changes in role assignments can take a few minutes to propagate. If you recently assigned roles, wait a bit and try again.
Also, ensure that Default to Microsoft Entra authorization is the Azure portal is set to Enabled at Storage account level. Portal>>Storage account>>Configurations>>Default to Microsoft Entra authorization is the Azure portal>>Enable.
Since you mentioned that access is enabled from all networks, ensure that there are no additional network restrictions that might be affecting access.
As an additional troubleshooting step, try accessing the Table Storage using a service principal. Create a service principal in Azure AD, assign the necessary roles, and use its credentials in your code.
- Create a service principal and get its credentials (client ID, client secret, tenant ID).
- Assign the
Storage Table Data Contributor role to the service principal.
- Update your code to use
ClientSecretCredential:
AzureDefaultCredential by itself isn't enough for programmatic authentication. You need an application (service principal) with owner permissions for the specified resource group. You should include the service principal details in your PowerShell REST API call to create resources in the resource group.
Hope this helps to resolve the AuthorizationPermissionMismatch error and successfully access Azure Table Storage using DefaultAzureCredential or a service principal. Even though if the issue persists, please feel free to contact, we will work closely for the resolution.
Please do consider to click on "Accept Answer" and "Up-vote" on the post that helps you, as it can be beneficial to other community members.
