Hi,
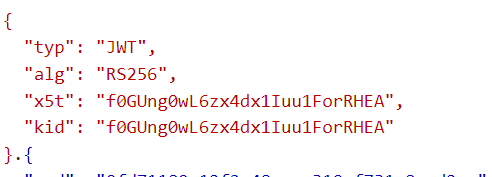
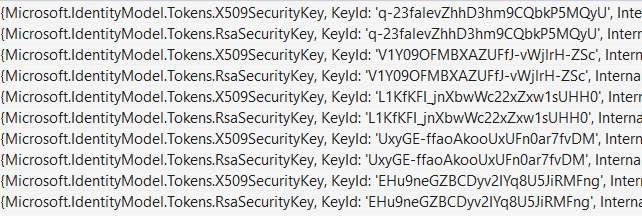
I'm trying to validate my access token signature from Microsoft Entra ID, as you can see in the below image, the "kid" attribute is different from the keys retrieved in the second image below that were retrieved from [domain+tenant]/.well-known/openid-configuration
This is causing the next error: The token's kid is: 'f0GUng0wL6zx4dx1Iuu1ForRHEA', but did not match any keys in TokenValidationParameters
Could you try to help me to understand if I am doing something wrong ? This only happens with Microsoft Entra ID, it works when using Azure AD B2C
StackTrace:
HResult=0x80131500
Message=IDX10503: Signature validation failed. The token's kid is: 'f0GUng0wL6zx4dx1Iuu1ForRHEA', but did not match any keys in TokenValidationParameters or Configuration. Keys tried: 'Microsoft.IdentityModel.Tokens.X509SecurityKey, KeyId: 'q-23falevZhhD3hm9CQbkP5MQyU', InternalId: 'q-23falevZhhD3hm9CQbkP5MQyU'. , KeyId: q-23falevZhhD3hm9CQbkP5MQyU
Microsoft.IdentityModel.Tokens.RsaSecurityKey, KeyId: 'q-23falevZhhD3hm9CQbkP5MQyU', InternalId: 'S_S12adpbe27-_qkluYZHCSMRJ6EcrW5Ho4cyLGEjG8'. , KeyId: q-23falevZhhD3hm9CQbkP5MQyU
Microsoft.IdentityModel.Tokens.X509SecurityKey, KeyId: 'V1Y09OFMBXAZUFfJ-vWjlrH-ZSc', InternalId: 'V1Y09OFMBXAZUFfJ-vWjlrH-ZSc'. , KeyId: V1Y09OFMBXAZUFfJ-vWjlrH-ZSc
Microsoft.IdentityModel.Tokens.RsaSecurityKey, KeyId: 'V1Y09OFMBXAZUFfJ-vWjlrH-ZSc', InternalId: '21yYN7-15_HEG6Myr8mw1D07vAMCN503j4n1GnsWWJQ'. , KeyId: V1Y09OFMBXAZUFfJ-vWjlrH-ZSc
Microsoft.IdentityModel.Tokens.X509SecurityKey, KeyId: 'L1KfKFI_jnXbwWc22xZxw1sUHH0', InternalId: 'L1KfKFI_jnXbwWc22xZxw1sUHH0'. , KeyId: L1KfKFI_jnXbwWc22xZxw1sUHH0
Microsoft.IdentityModel.Tokens.RsaSecurityKey, KeyId: 'L1KfKFI_jnXbwWc22xZxw1sUHH0', InternalId: 'RlwaR9qe84mGeeFWVsLX3zezPkY88aZiSkDuuqUxftM'. , KeyId: L1KfKFI_jnXbwWc22xZxw1sUHH0
Microsoft.IdentityModel.Tokens.X509SecurityKey, KeyId: 'UxyGE-ffaoAkooUxUFn0ar7fvDM', InternalId: 'UxyGE-ffaoAkooUxUFn0ar7fvDM'. , KeyId: UxyGE-ffaoAkooUxUFn0ar7fvDM
Microsoft.IdentityModel.Tokens.RsaSecurityKey, KeyId: 'UxyGE-ffaoAkooUxUFn0ar7fvDM', InternalId: 'IC5xpkooVq3LolG30n_19Ollz-mDTXlIuq4MdlmjwFE'. , KeyId: UxyGE-ffaoAkooUxUFn0ar7fvDM
Microsoft.IdentityModel.Tokens.X509SecurityKey, KeyId: 'EHu9neGZBCDyv2IYq8U5JiRMFng', InternalId: 'EHu9neGZBCDyv2IYq8U5JiRMFng'. , KeyId: EHu9neGZBCDyv2IYq8U5JiRMFng
Microsoft.IdentityModel.Tokens.RsaSecurityKey, KeyId: 'EHu9neGZBCDyv2IYq8U5JiRMFng', InternalId: '4xRadtB97YyM0GXtJGF1MHO11LmoVHRCXd4Gp3tNb6Y'. , KeyId: EHu9neGZBCDyv2IYq8U5JiRMFng
'. Number of keys in TokenValidationParameters: '10'.


