What threats does ATA look for?
Applies to: Advanced Threat Analytics version 1.9
ATA provides detection for the following various phases of an advanced attack: reconnaissance, credential compromise, lateral movement, privilege escalation, domain dominance, and others. These detections are aimed at detecting advanced attacks and insider threats before they cause damage to your organization. The detection of each phase results in several suspicious activities relevant for the phase in question, where each suspicious activity correlates to different flavors of possible attacks. These phases in the kill-chain where ATA currently provides detections are highlighted in the following image:
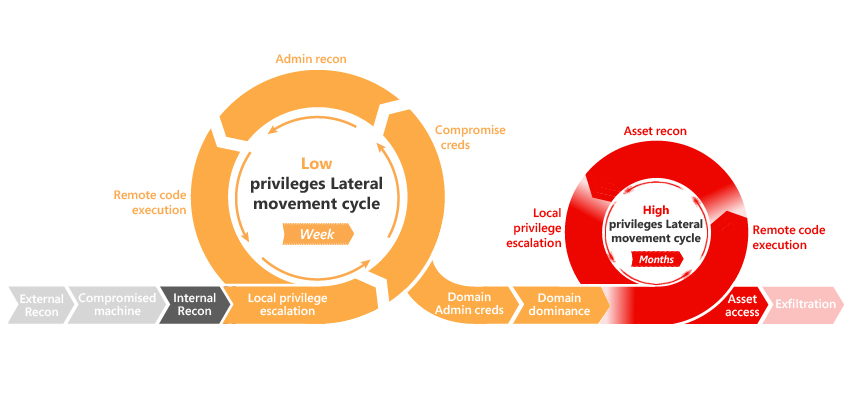
For more information, see Working with suspicious activities and the ATA suspicious activity guide.
What's next?
For more information about how ATA fits into your network: ATA architecture
To get started deploying ATA: Install ATA