Tutorial: Connect, set up, and activate Azure Stack Edge Pro FPGA
Important
Azure Stack Edge Pro FPGA devices reached end-of-life in February 2024.
This tutorial describes how you can connect to, set up, and activate your Azure Stack Edge Pro FPGA device by using the local web UI.
The setup and activation process can take around 20 minutes to complete.
In this tutorial, you learn how to:
- Connect to a physical device
- Set up and activate the physical device
Prerequisites
Before you configure and set up your Azure Stack Edge Pro FPGA device, make sure that:
- You've installed the physical device as detailed in Install Azure Stack Edge Pro FPGA.
- You have the activation key from the Azure Stack Edge service that you created to manage the Azure Stack Edge Pro FPGA device. For more information, go to Prepare to deploy Azure Stack Edge Pro FPGA.
Connect to the local web UI setup
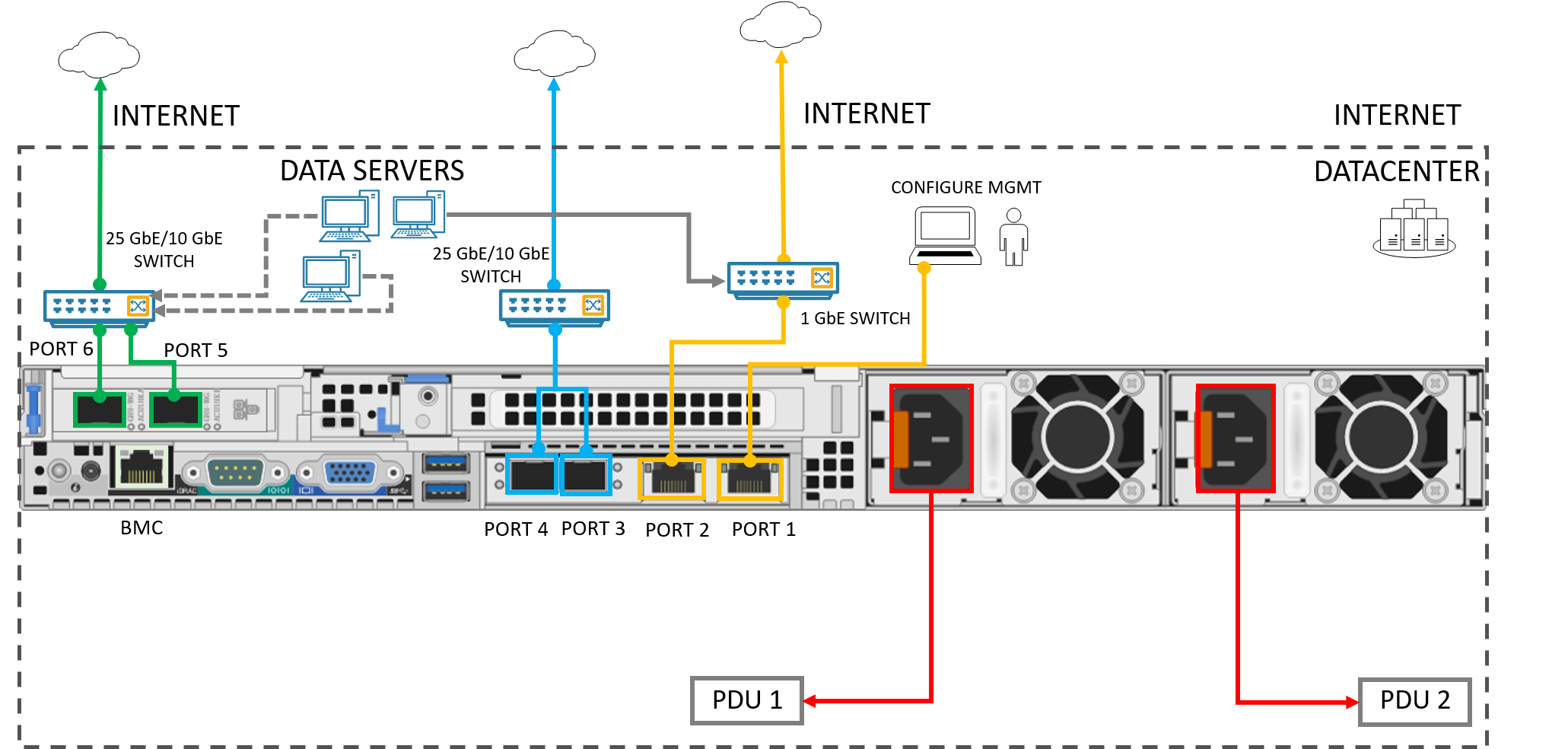
Configure the Ethernet adapter on your computer to connect to the Azure Stack Edge Pro FPGA device with a static IP address of 192.168.100.5 and subnet 255.255.255.0.
Connect the computer to PORT 1 on your device. Use the following illustration to identify PORT 1 on your device.
Open a browser window and access the local web UI of the device at
https://192.168.100.10.
This action may take a few minutes after you've turned on the device.You see an error or a warning indicating that there is a problem with the website's security certificate.
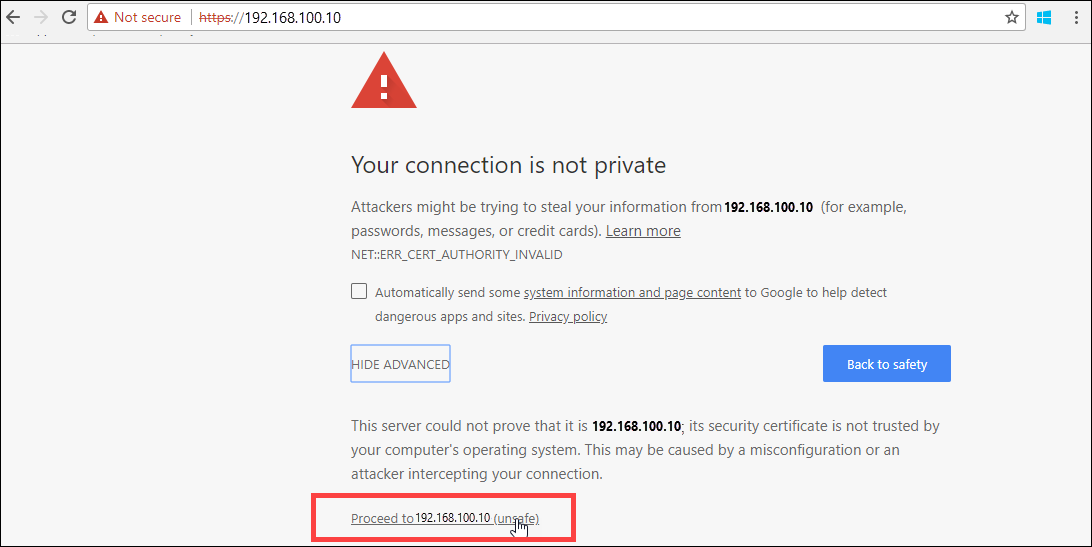
Select Continue to this webpage.
These steps might vary depending on the browser you're using.Sign in to the web UI of your device. The default password is Password1.
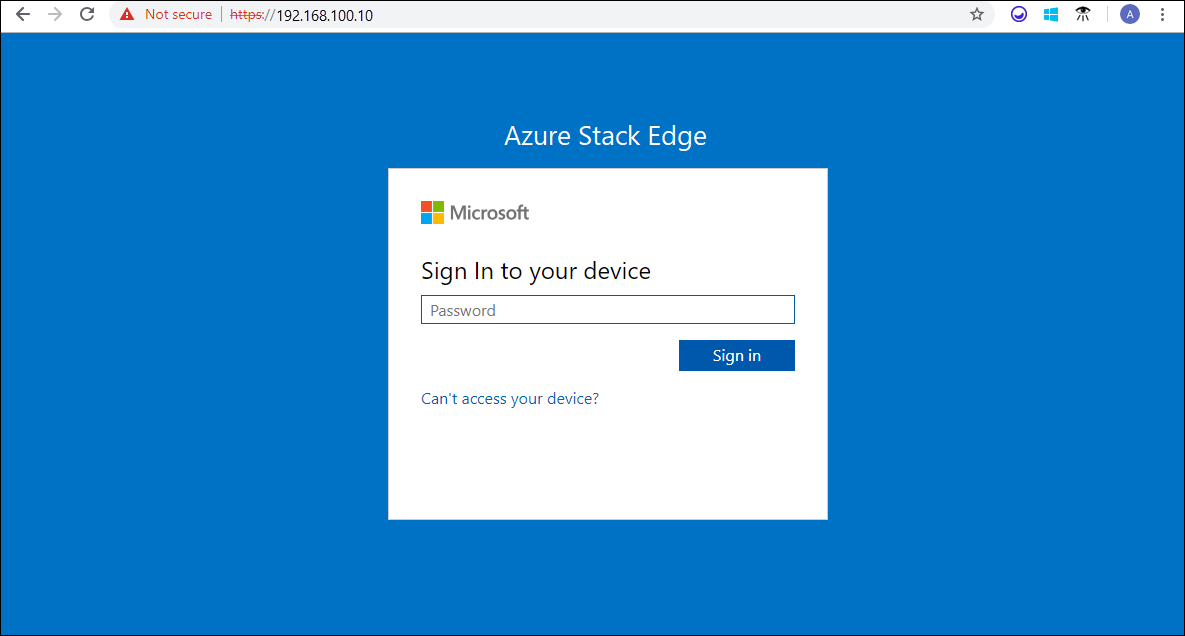
At the prompt, change the device administrator password.
The new password must contain between 8 and 16 characters. It must contain three of the following characters: uppercase, lowercase, numeric, and special characters.
You're now at the dashboard of your device.
Set up and activate the physical device
Your dashboard displays the various settings that are required to configure and register the physical device with the Azure Stack Edge service. The Device name, Network settings, Web proxy settings, and Time settings are optional. The only required settings are Cloud settings.
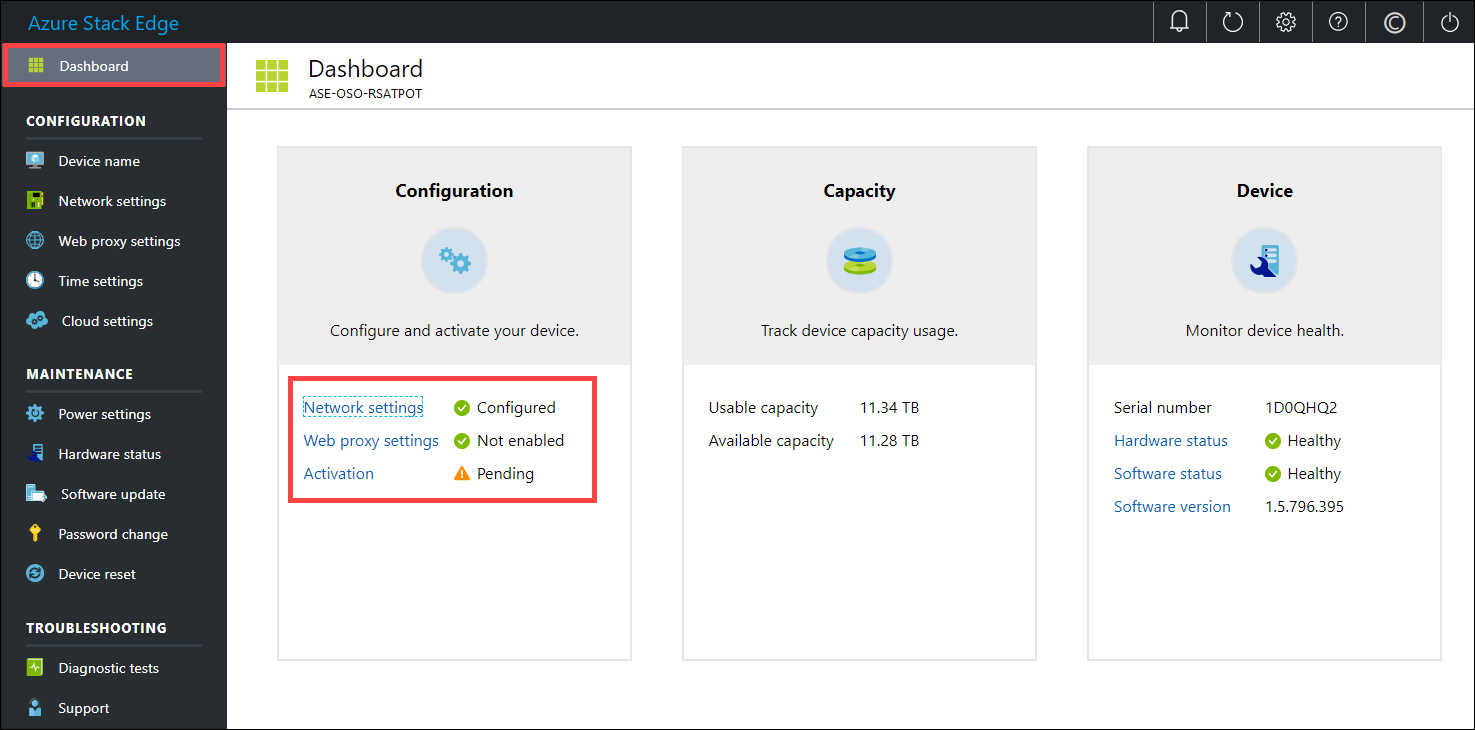
In the left pane, select Device name, and then enter a friendly name for your device.
The friendly name must contain from 1 to 15 characters and have letters, numbers, and hyphens.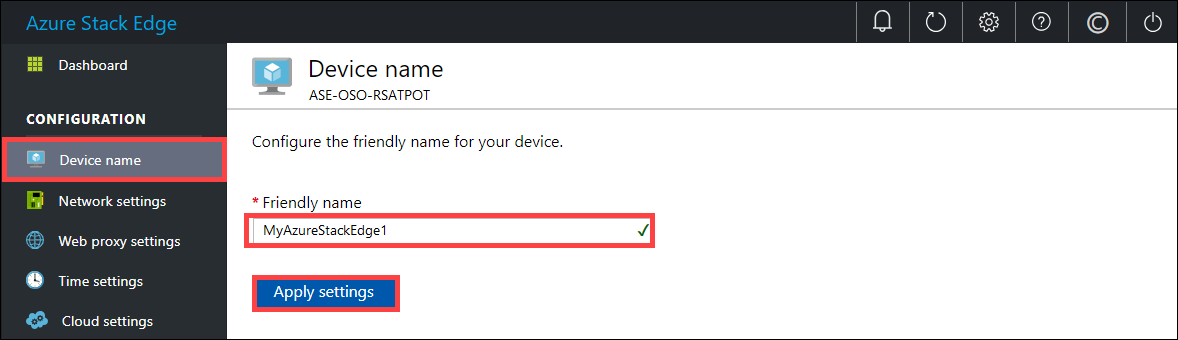
(Optional) In the left pane, select Network settings and then configure the settings.
On your physical device, there are six network interfaces. PORT 1 and PORT 2 are 1-Gbps network interfaces. PORT 3, PORT 4, PORT 5, and PORT 6 are all 25-Gbps network interfaces that can also serve as 10-Gbps network interfaces. PORT 1 is automatically configured as a management-only port, and PORT 2 to PORT 6 are all data ports. The Network settings page is as shown below.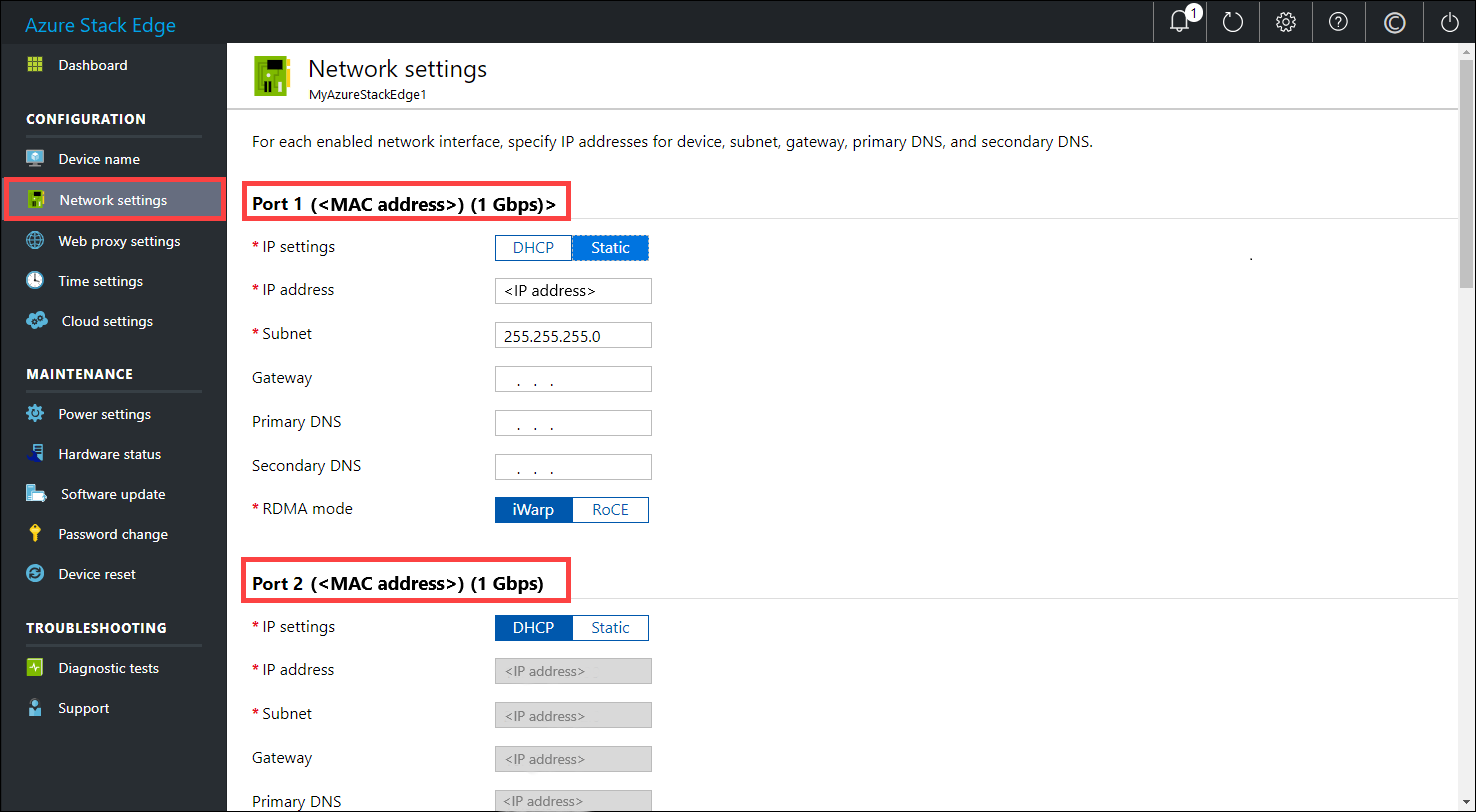
As you configure the network settings, keep in mind:
If DHCP is enabled in your environment, network interfaces are automatically configured. An IP address, subnet, gateway, and DNS are automatically assigned.
If DHCP isn't enabled, you can assign static IPs if needed.
You can configure your network interface as IPv4.
Note
We recommend that you do not switch the local IP address of the network interface from static to DHCP, unless you have another IP address to connect to the device. If using one network interface and you switch to DHCP, there would be no way to determine the DHCP address. If you want to change to a DHCP address, wait until after the device has registered with the service, and then change. You can then view the IPs of all the adapters in the Device properties in the Azure portal for your service.
(Optional) In the left pane, select Web proxy settings, and then configure your web proxy server. Although web proxy configuration is optional, if you use a web proxy, you can configure it on this page only.
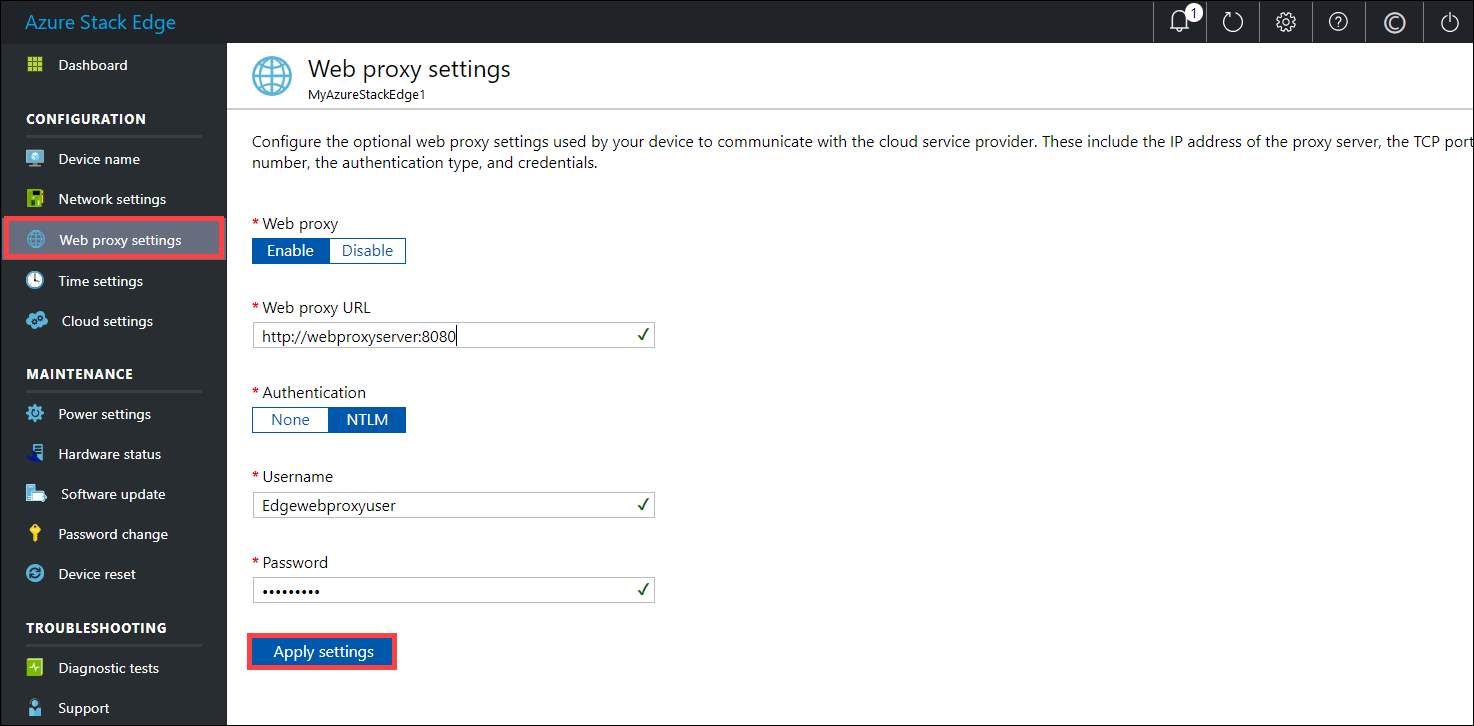
On the Web proxy settings page, do the following:
a. In the Web proxy URL box, enter the URL in this format:
http://host-IP address or FQDN:Port number. HTTPS URLs are not supported.b. Under Authentication, select None or NTLM. If you enable compute and use IoT Edge module on your Azure Stack Edge Pro FPGA device, we recommend you set web proxy authentication to None. NTLM is not supported.
c. If you're using authentication, enter a username and password.
d. To validate and apply the configured web proxy settings, select Apply settings.
Note
Proxy-auto config (PAC) files are not supported. A PAC file defines how web browsers and other user agents can automatically choose the appropriate proxy server (access method) for fetching a given URL. Proxies that try to intercept and read all the traffic (then re-sign everything with their own certification) aren't compatible since the proxy's cert is not trusted. Typically transparent proxies work well with Azure Stack Edge Pro FPGA.
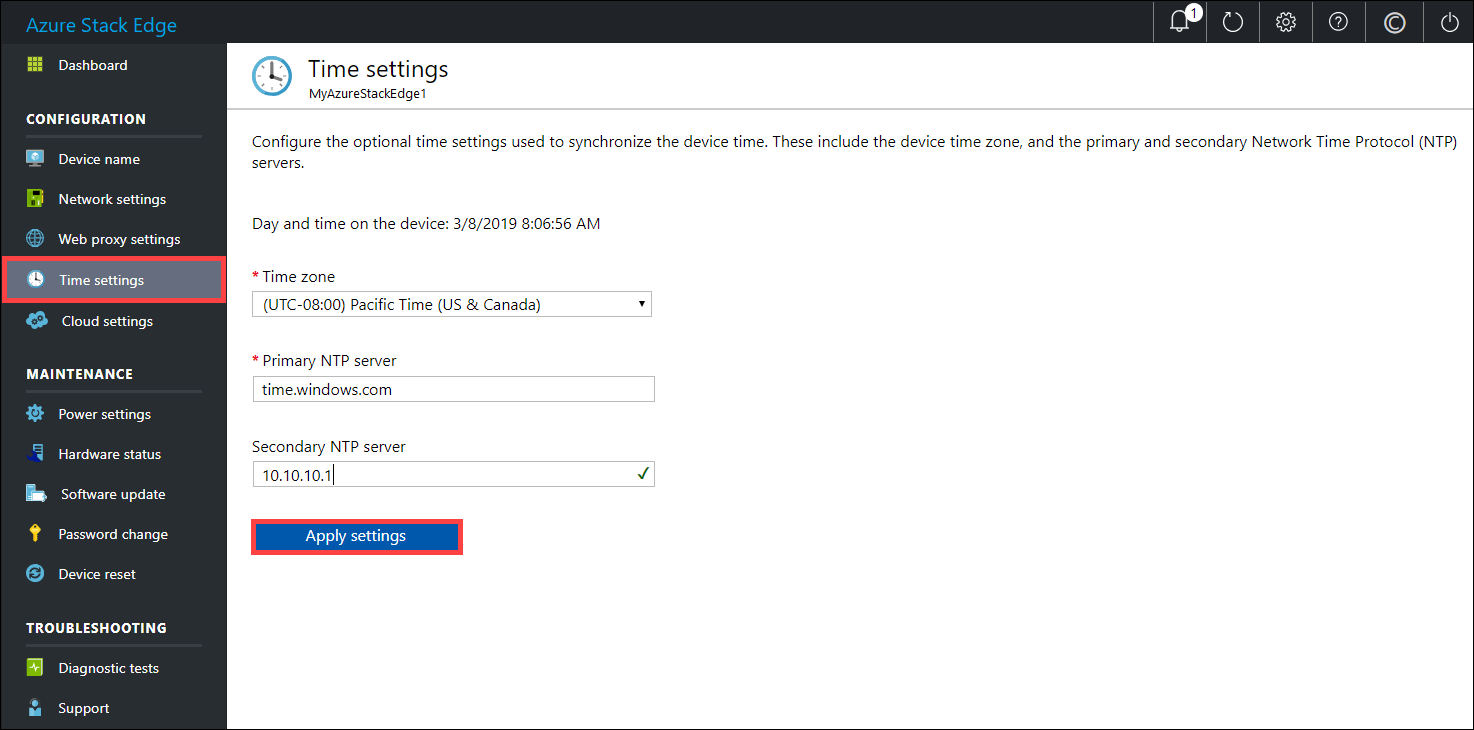
(Optional) In the left pane, select Time settings, and then configure the time zone and the primary and secondary NTP servers for your device.
NTP servers are required because your device must synchronize time so that it can authenticate with your cloud service providers.On the Time settings page, do the following:
In the Time zone drop-down list, select the time zone that corresponds to the geographic location in which the device is being deployed. The default time zone for your device is PST. Your device will use this time zone for all scheduled operations.
In the Primary NTP server box, enter the primary server for your device or accept the default value of time.windows.com.
Ensure that your network allows NTP traffic to pass from your datacenter to the internet.Optionally, in the Secondary NTP server box, enter a secondary server for your device.
To validate and apply the configured time settings, select Apply settings.
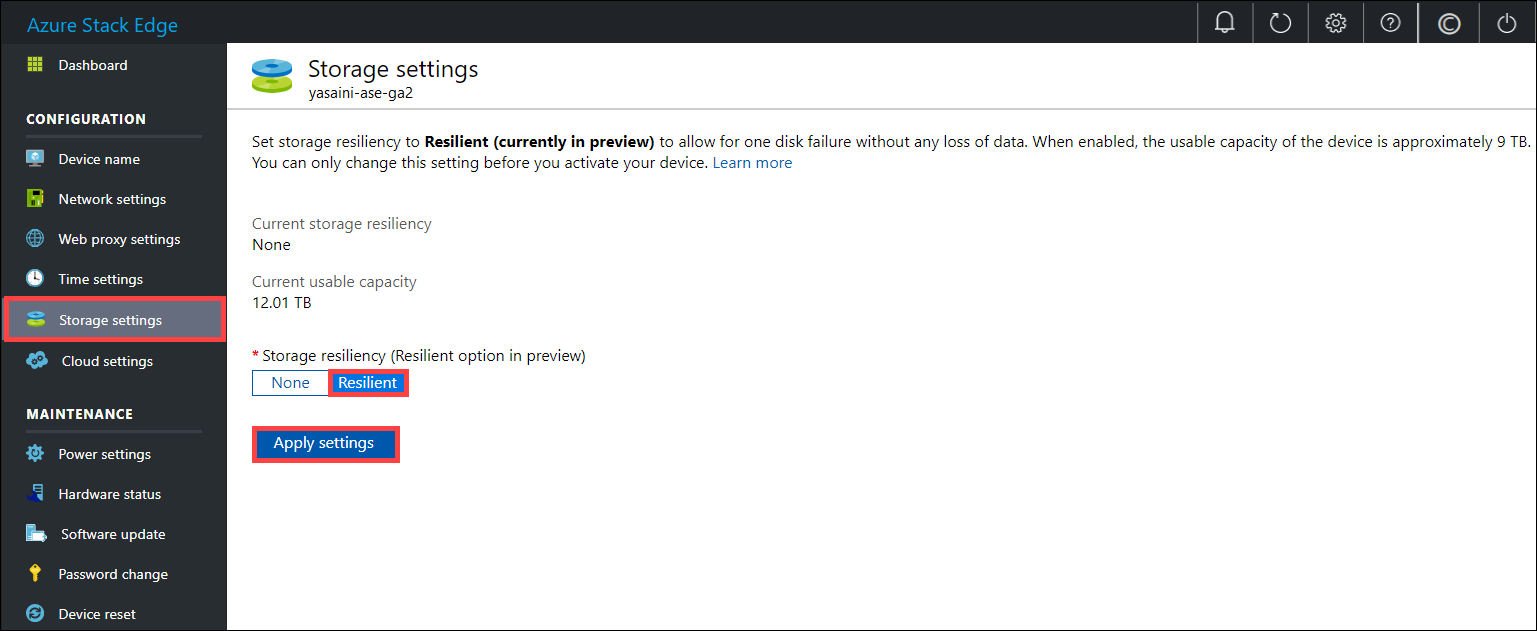
(Optional) In the left pane, select Storage settings to configure the storage resiliency on your device. This feature is currently in preview. By default, the storage on the device is not resilient and there is data loss if a data disk fails on the device. When you enable the Resilient option, the storage on the device will be reconfigured and the device can withstand the failure of one data disk with no data loss. Configuring the storage as resilient will reduce the usable capacity of your device.
Important
The resiliency can only be configured before you activate the device.
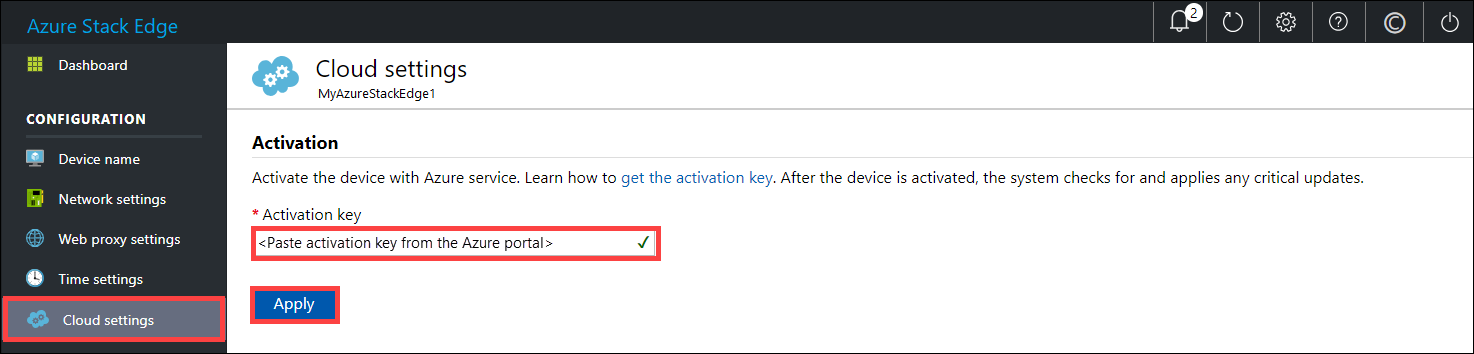
In the left pane, select Cloud settings, and then activate your device with the Azure Stack Edge service in the Azure portal.
In the Activation key box, enter the activation key that you got in Get the activation key for Azure Stack Edge Pro FPGA.
Select Apply.
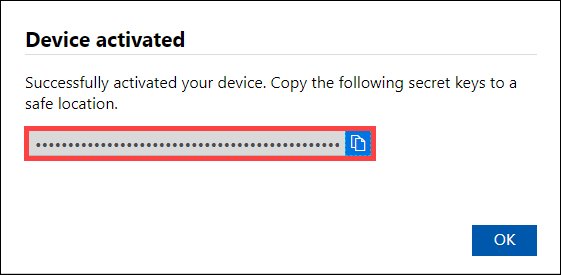
First the device is activated. The device is then scanned for any critical updates and if available, the updates are automatically applied. You see a notification to that effect.
The dialog also has a recovery key that you should copy and save it in a safe location. This key is used to recover your data in the event the device can't boot up.
You may need to wait several minutes after the update is successfully completed. The page updates to indicate that the device is successfully activated.
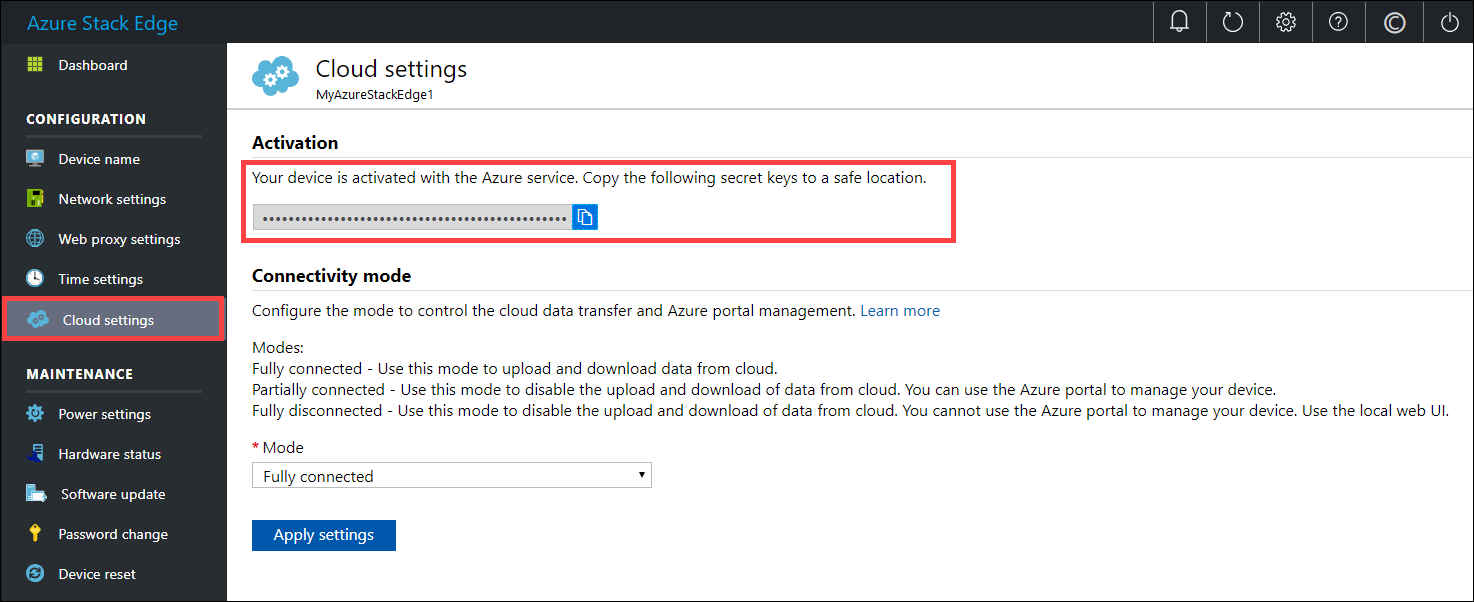
The device setup is complete. You can now add shares on your device.
Next steps
In this tutorial, you learned how to:
- Connect to a physical device
- Set up and activate the physical device
To learn how to transfer data with your Azure Stack Edge Pro FPGA device, see: