Deploy a Python (Django or Flask) web app with PostgreSQL in Azure
In this tutorial, you'll deploy a data-driven Python web app (Django or Flask) to Azure App Service with the Azure Database for PostgreSQL relational database service. Azure App Service supports Python in a Linux server environment.
To complete this tutorial, you'll need:
- An Azure account with an active subscription. If you don't have an Azure account, you can create one for free.
- Knowledge of Python with Flask development or Python with Django development
- An Azure account with an active subscription. If you don't have an Azure account, you can create one for free.
- Azure Developer CLI installed. You can follow the steps with the Azure Cloud Shell because it already has Azure Developer CLI installed.
- Knowledge of Python with Flask development or Python with Django development
Skip to the end
With Azure Developer CLI installed, you can deploy a fully configured sample app shown in this tutorial and see it running in Azure. Just running the following commands in an empty working directory:
azd auth login
azd init --template msdocs-flask-postgresql-sample-app
azd up
Sample application
Sample Python applications using the Flask and Django framework are provided to help you follow along with this tutorial. To deploy them without running them locally, skip this part.
To run the application locally, make sure you have Python 3.7 or higher and PostgreSQL installed locally. Then, clone the sample repository's starter-no-infra branch and change to the repository root.
git clone -b starter-no-infra https://github.com/Azure-Samples/msdocs-flask-postgresql-sample-app
cd msdocs-flask-postgresql-sample-app
Create an .env file as shown below using the .env.sample file as a guide. Set the value of DBNAME to the name of an existing database in your local PostgreSQL instance. Set the values of DBHOST, DBUSER, and DBPASS as appropriate for your local PostgreSQL instance.
DBNAME=<database name>
DBHOST=<database-hostname>
DBUSER=<db-user-name>
DBPASS=<db-password>
Create a virtual environment for the app:
py -m venv .venv
.venv\scripts\activate
Install the dependencies:
pip install -r requirements.txt
Run the sample application with the following commands:
# Run database migration
flask db upgrade
# Run the app at http://127.0.0.1:5000
flask run
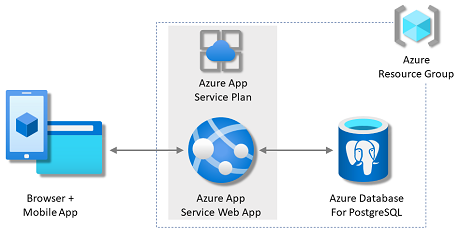
1. Create App Service and PostgreSQL
In this step, you create the Azure resources. The steps used in this tutorial create a set of secure-by-default resources that include App Service and Azure Database for PostgreSQL. For the creation process, you'll specify:
- The Name for the web app. It's the name used as part of the DNS name for your webapp in the form of
https://<app-name>.azurewebsites.net. - The Region to run the app physically in the world.
- The Runtime stack for the app. It's where you select the version of Python to use for your app.
- The Hosting plan for the app. It's the pricing tier that includes the set of features and scaling capacity for your app.
- The Resource Group for the app. A resource group lets you group (in a logical container) all the Azure resources needed for the application.
Sign in to the Azure portal and follow these steps to create your Azure App Service resources.
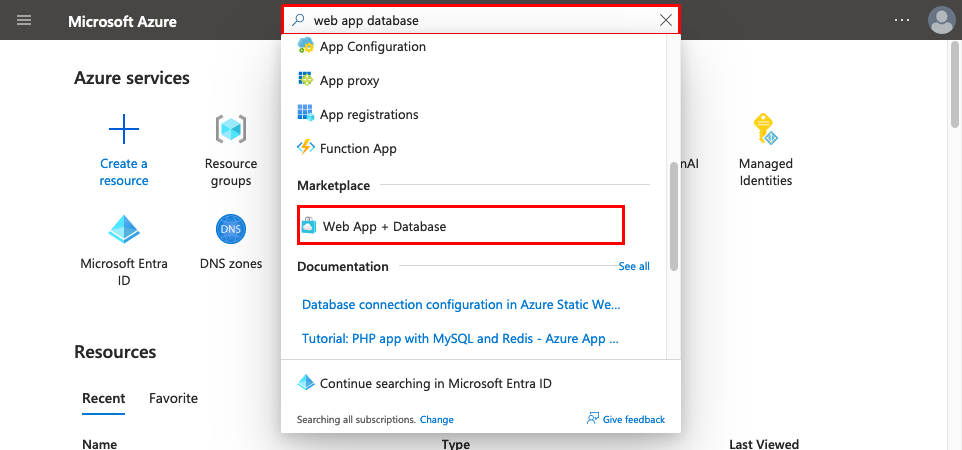
Step 1: In the Azure portal:
- Enter "web app database" in the search bar at the top of the Azure portal.
- Select the item labeled Web App + Database under the Marketplace heading. You can also navigate to the creation wizard directly.
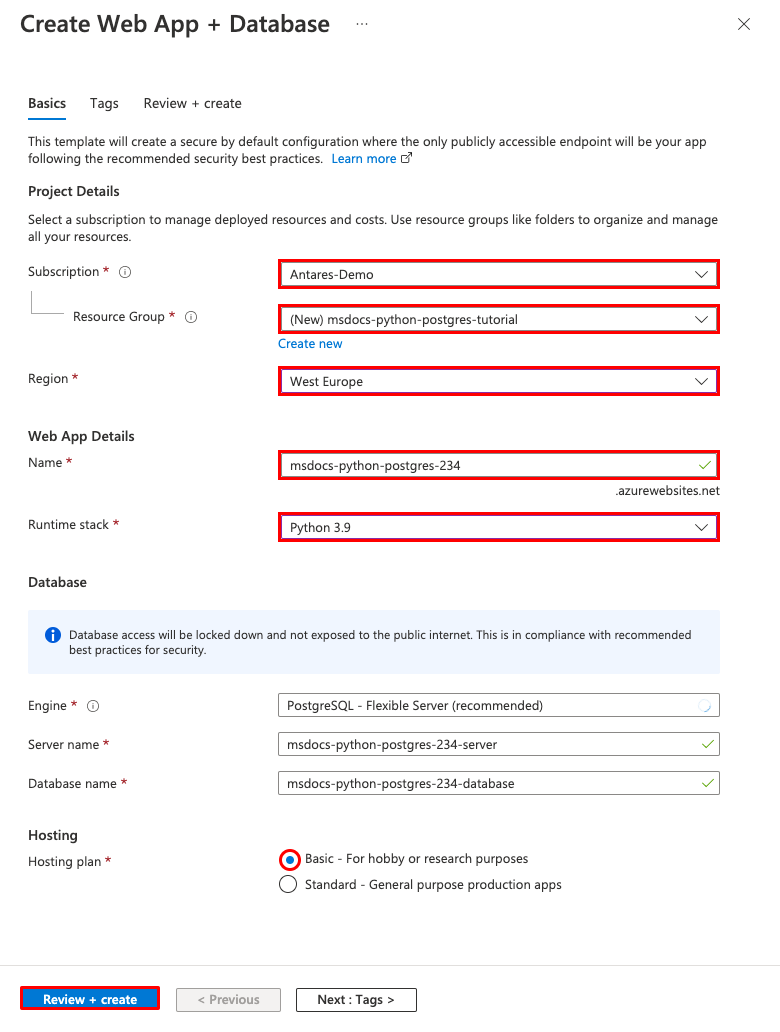
Step 2: In the Create Web App + Database page, fill out the form as follows.
- Resource Group → Select Create new and use a name of msdocs-python-postgres-tutorial.
- Region → Any Azure region near you.
- Name → msdocs-python-postgres-XYZ where XYZ is any three random characters. This name must be unique across Azure.
- Runtime stack → Python 3.10.
- Database → PostgreSQL - Flexible Server is selected by default as the database engine. The server name and database name are also set by default to appropriate values.
- Hosting plan → Basic. When you're ready, you can scale up to a production pricing tier later.
- Select Review + create.
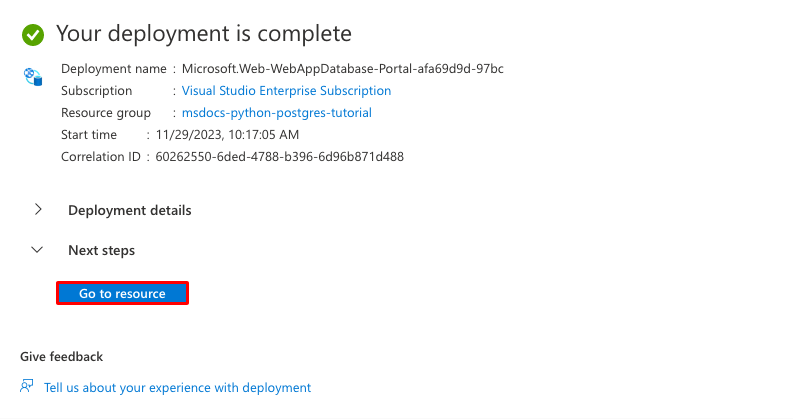
- After validation completes, select Create.
Step 3: The deployment takes a few minutes to complete. Once deployment completes, select the Go to resource button. You're taken directly to the App Service app, but the following resources are created:
- Resource group → The container for all the created resources.
- App Service plan → Defines the compute resources for App Service. A Linux plan in the Basic tier is created.
- App Service → Represents your app and runs in the App Service plan.
- Virtual network → Integrated with the App Service app and isolates back-end network traffic.
- Azure Database for PostgreSQL flexible server → Accessible only from within the virtual network. A database and a user are created for you on the server.
- Private DNS zone → Enables DNS resolution of the PostgreSQL server in the virtual network.
2. Secure connection secrets
The creation wizard generated the database connectivity string for you already as an app setting. However, the security best practice is to keep secrets out of App Service completely. You move your secrets to a key vault and change your app setting to a Key Vault reference with the help of Service Connectors.
Step 1: Retrieve the existing connection string
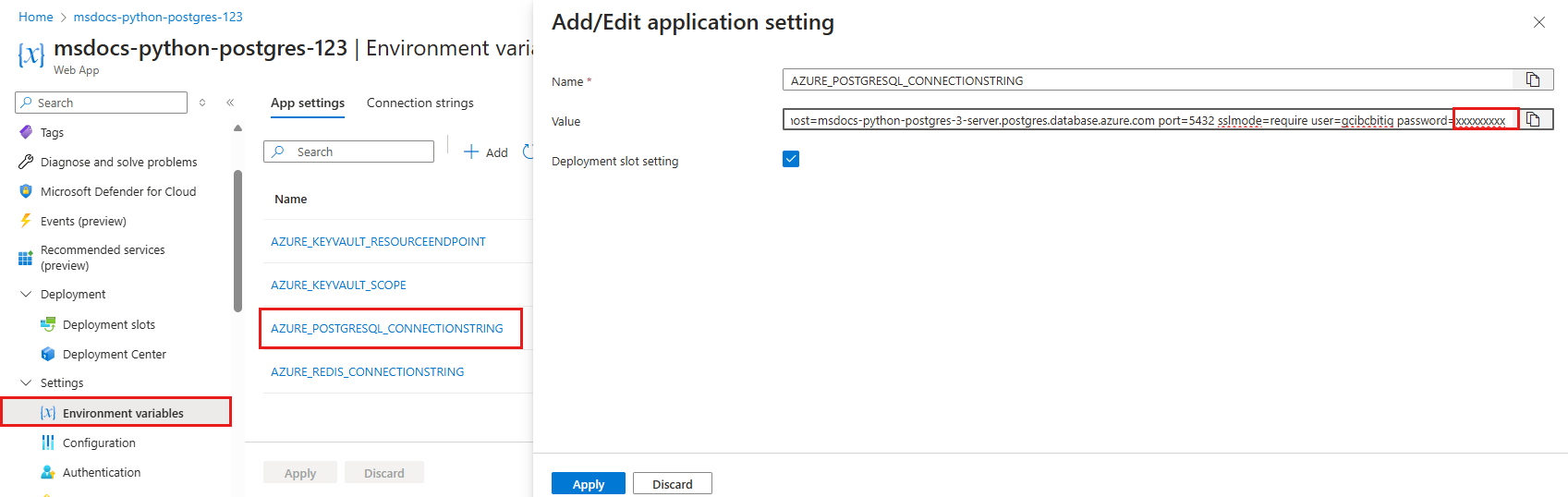
- In the left menu of the App Service page, select Settings > Environment variables.
- Select AZURE_POSTGRESQL_CONNECTIONSTRING.
- In Add/Edit application setting, in the Value field, find the password= part at the end of the string.
- Copy the password string after Password= for use later. This app setting lets you connect to the Postgres database secured behind a private endpoint. However, the secret is saved directly in the App Service app, which isn't the best. You'll change this.
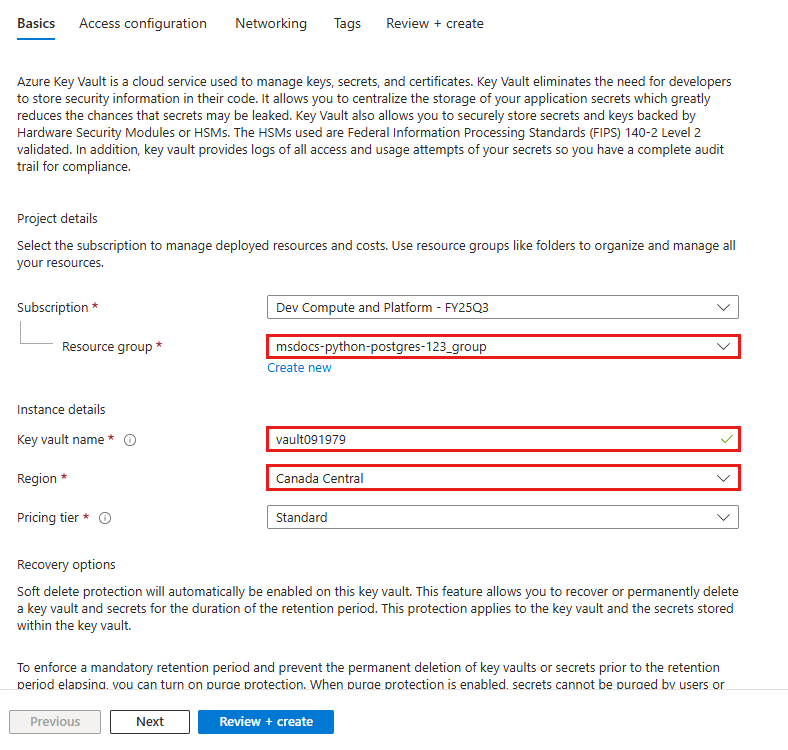
Step 2: Create a key vault for secure management of secrets
- In the top search bar, type "key vault", then select Marketplace > Key Vault.
- In Resource Group, select msdocs-python-postgres-tutorial.
- In Key vault name, type a name that consists of only letters and numbers.
- In Region, set it to the same location as the resource group.
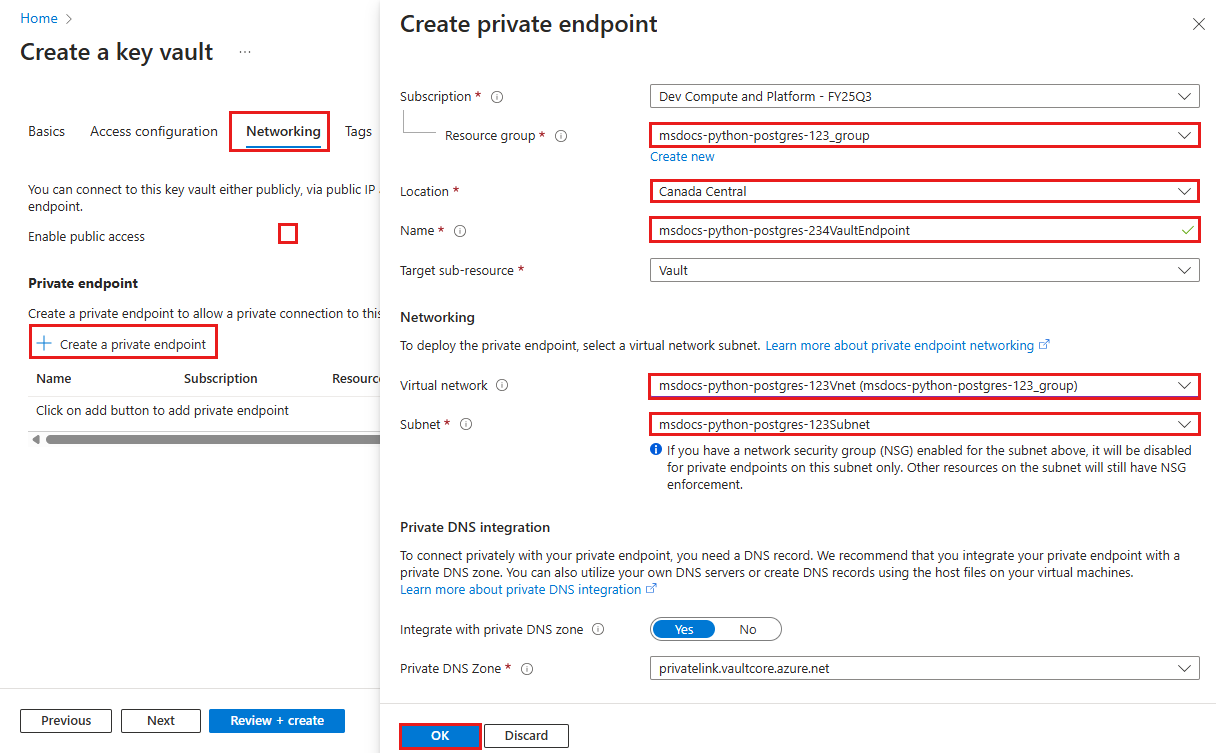
Step 3: Secure the key vault with a Private Endpoint
- Select the Networking tab.
- Unselect Enable public access.
- Select Create a private endpoint.
- In Resource Group, select msdocs-python-postgres-tutorial.
- In Name, type a name for the private endpoint that consists of only letters and numbers.
- In Region, set it to the same location as the resource group.
- In the dialog, in Location, select the same location as your App Service app.
- In Resource Group, select msdocs-python-postgres-tutorial.
- In Name, type msdocs-python-postgres-XYZVaultEndpoint.
- In Virtual network, select msdocs-python-postgres-XYZVnet.
- In Subnet, msdocs-python-postgres-XYZSubnet.
- Select OK.
- Select Review + create, then select Create. Wait for the key vault deployment to finish. You should see "Your deployment is complete."
Step 4: Configure the Service Connector
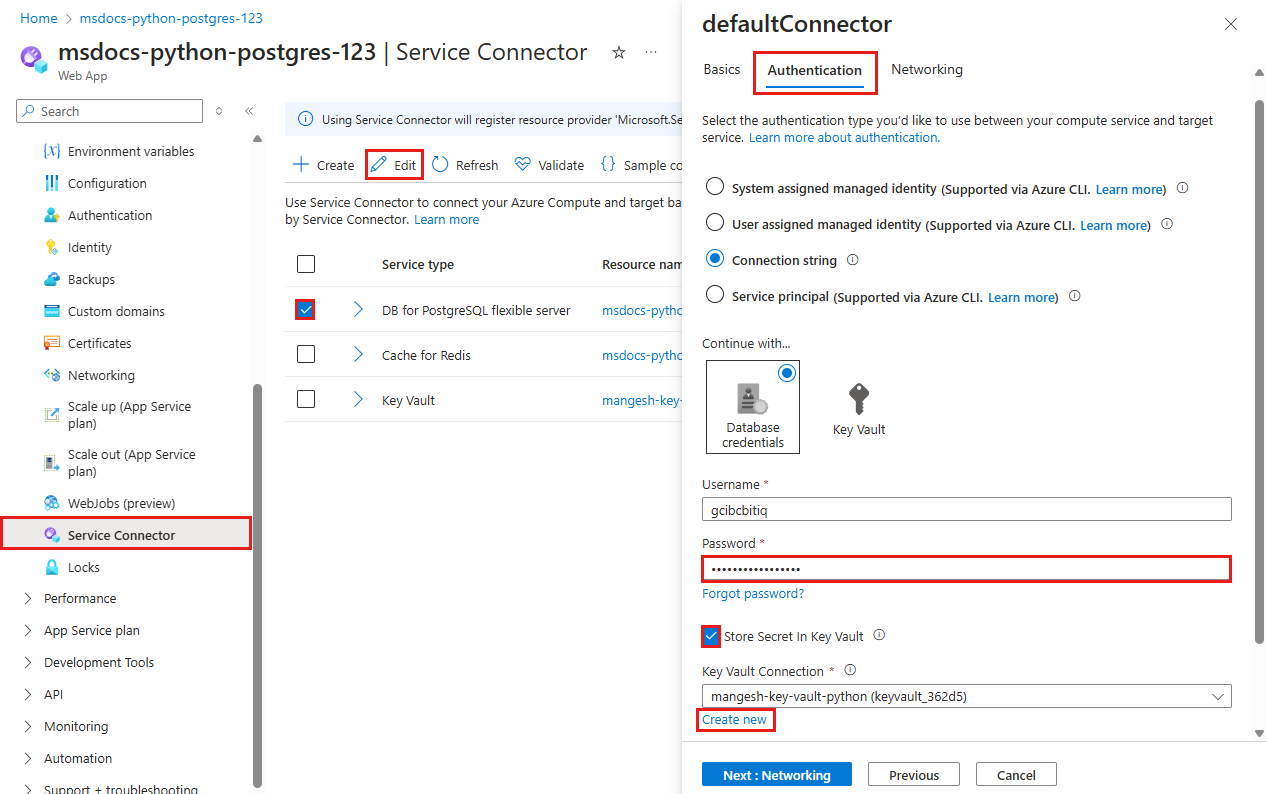
- In the top search bar, type msdocs-python-postgres, then select the App Service resource called msdocs-python-postgres-XYZ.
- In the App Service page, in the left menu, select Settings > Service Connector. There's already a connector, which the app creation wizard created for you.
- Select checkbox next to the connector, then select Edit.
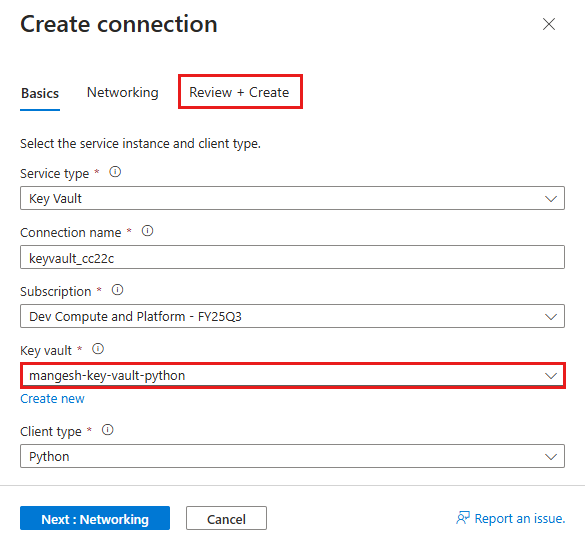
- In the Basics tab, under PostgreSQL database select the PostgreSQL database that was created.
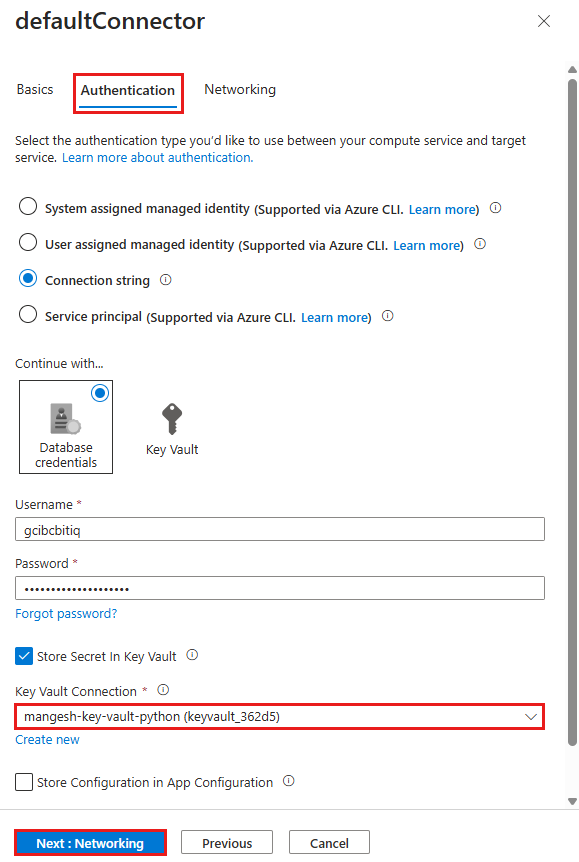
- Select the Authentication tab.
- In Password, paste the password you copied earlier.
- Select Store Secret in Key Vault.
- Under Key Vault Connection, select Create new. A Create connection dialog is opened on top of the edit dialog.
Step 5: Establish the Key Vault connection
- In the Create connection dialog for the Key Vault connection, in Key Vault, select the key vault you created earlier.
- Select Review + Create.
- When validation completes, select Create.
Step 6: Finalize the Service Connector configuration
- You're back in the edit dialog for defaultConnector. In the Authentication tab, wait for the key vault connector to be created. When it's finished, the Key Vault Connection dropdown automatically selects it.
- Select Next: Networking.
- Select Save. Wait until the Update succeeded notification appears.
Step 7: Verify the Key Vault integration
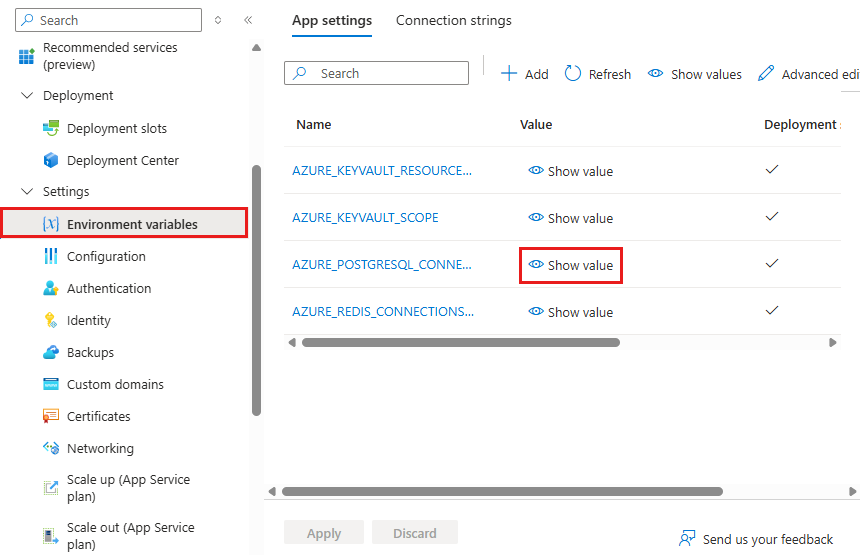
- From the left menu, select Settings > Environment variables again.
- Next to AZURE_POSTGRESQL_CONNECTIONSTRING, select Show value. The value should be
@Microsoft.KeyVault(...), which means that it's a key vault reference because the secret is now managed in the key vault.
To summarize, the process involved retrieving the PostgreSQL connection string from the App Service's environment variables, creating an Azure Key Vault for secure secret management with private access, and updating the service connector to store the password in the key vault. A secure connection between the App Service app and key vault was established using a system-assigned managed identity, and the setup was verified by confirming the connection string uses a Key Vault reference.
Having issues? Check the Troubleshooting section.
3. Deploy sample code
In this step, you'll configure GitHub deployment using GitHub Actions. It's just one of many ways to deploy to App Service, but also a great way to have continuous integration in your deployment process. By default, every git push to your GitHub repository will kick off the build and deploy action.
Step 1: In a new browser window:
- Sign in to your GitHub account.
- Navigate to https://github.com/Azure-Samples/msdocs-flask-postgresql-sample-app.
- Select Fork.
- Select Create fork.
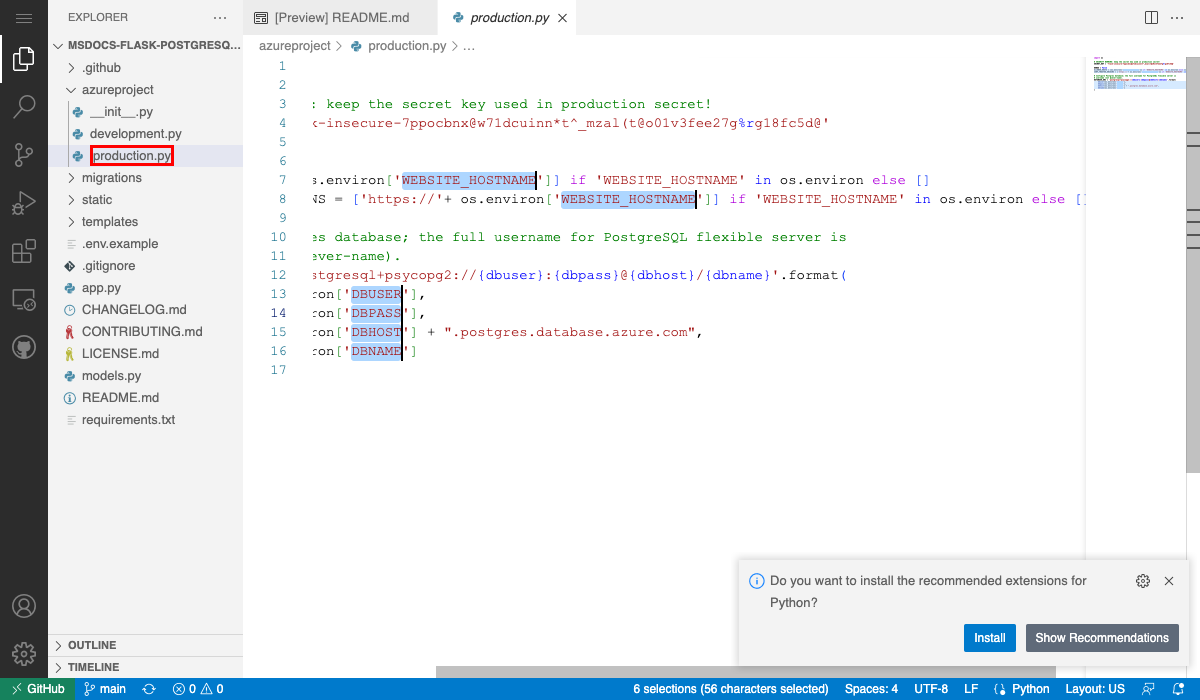
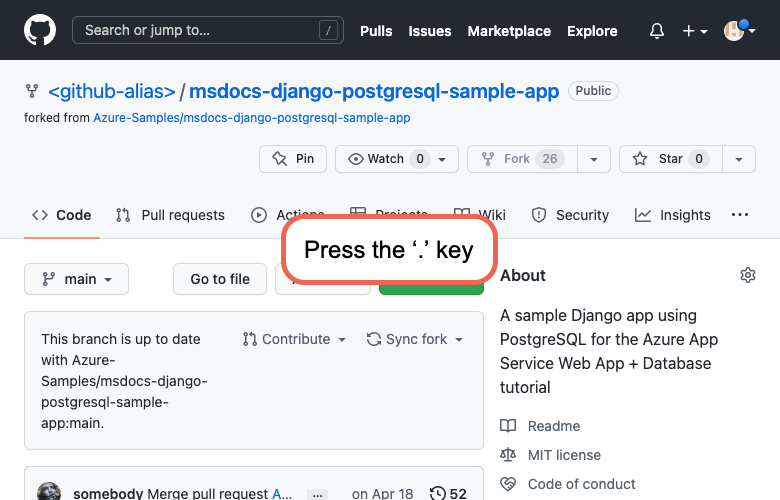
Step 2: In the GitHub page, open Visual Studio Code in the browser by pressing the . key.
Step 3: In Visual Studio Code in the browser, open azureproject/production.py in the explorer. See the environment variables being used in the production environment, including the app settings that you saw in the configuration page.
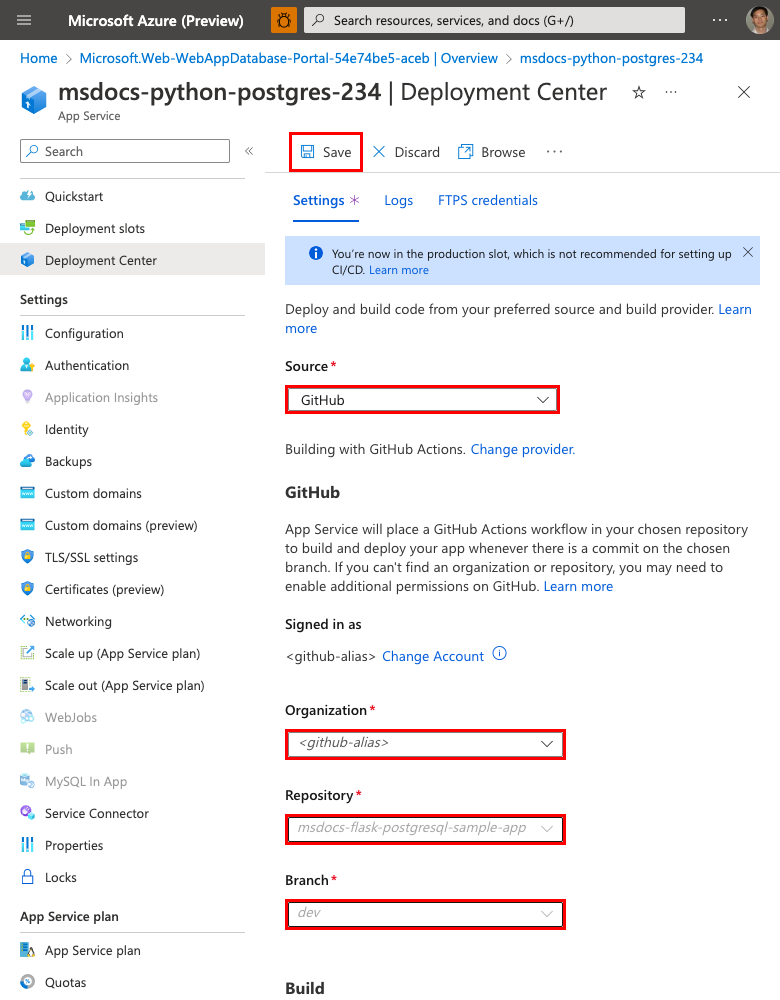
Step 4: Back in the App Service page, in the left menu, select Deployment Center.
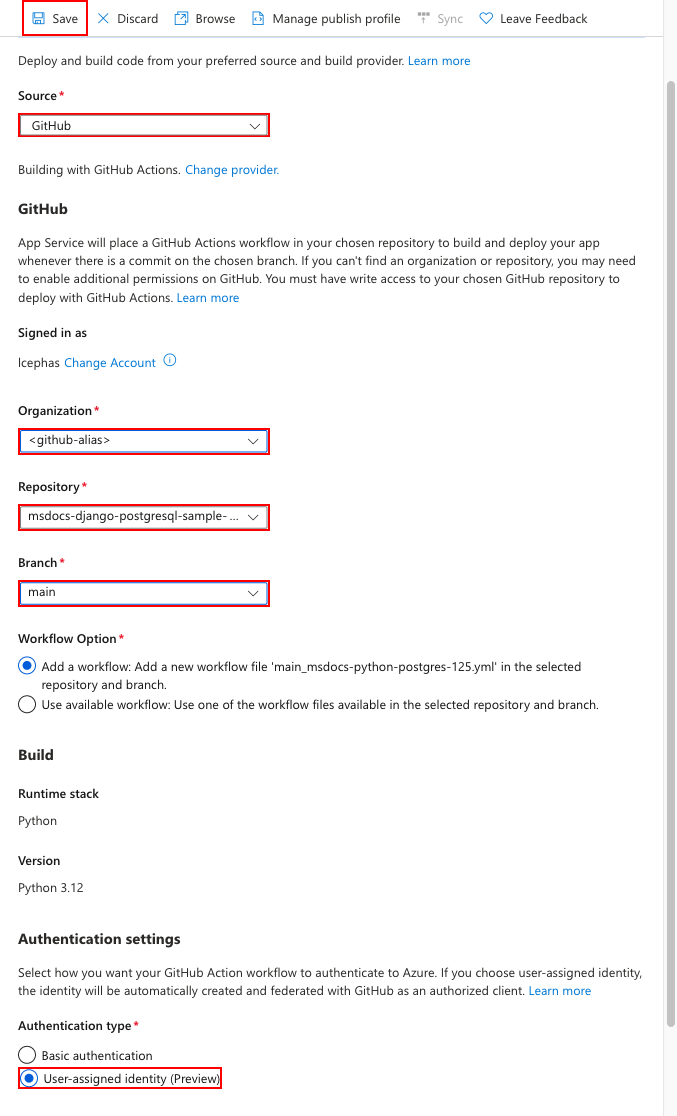
Step 5: In the Deployment Center page:
- In Source, select GitHub. By default, GitHub Actions is selected as the build provider.
- Sign in to your GitHub account and follow the prompt to authorize Azure.
- In Organization, select your account.
- In Repository, select msdocs-flask-postgresql-sample-app.
- In Branch, select main.
- Keep the default option selected to Add a workflow.
- Under Authentication type, select User-assigned identity.
- In the top menu, select Save. App Service commits a workflow file into the chosen GitHub repository, in the
.github/workflowsdirectory.
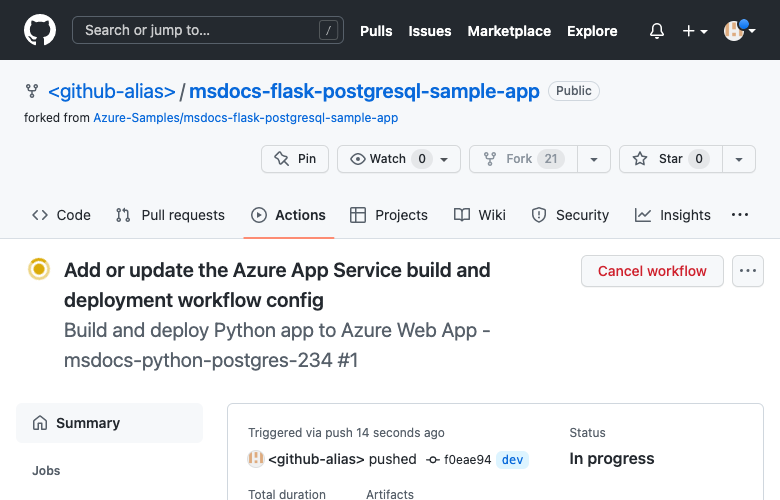
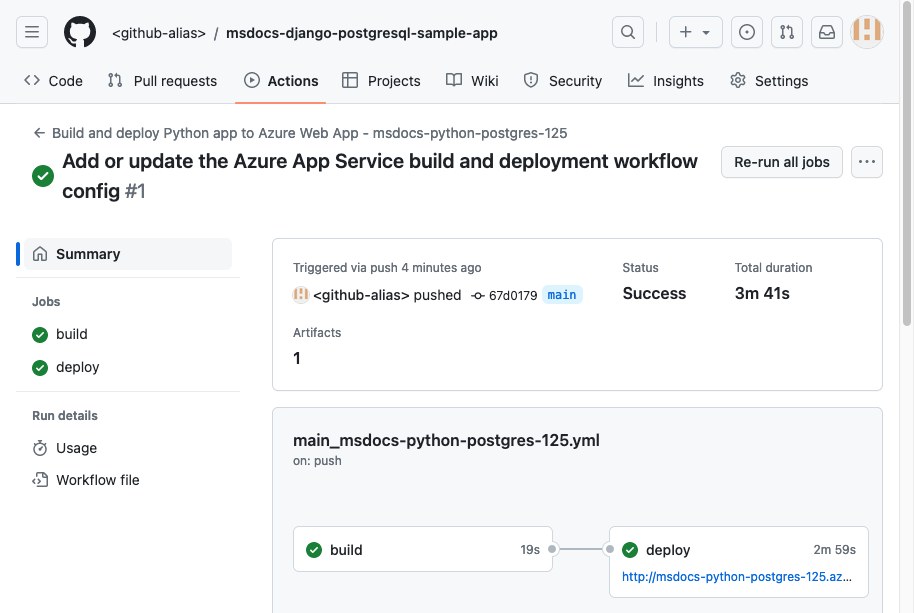
Step 6: In the Deployment Center page:
- Select Logs. A deployment run is already started.
- In the log item for the deployment run, select Build/Deploy Logs.
Step 7: You're taken to your GitHub repository and see that the GitHub action is running. The workflow file defines two separate stages, build and deploy. Wait for the GitHub run to show a status of Complete. It takes about 5 minutes.
Having issues? Check the Troubleshooting guide.
4. Generate database schema
With the PostgreSQL database protected by the virtual network, the easiest way to run Flask database migrations is in an SSH session with the App Service container.
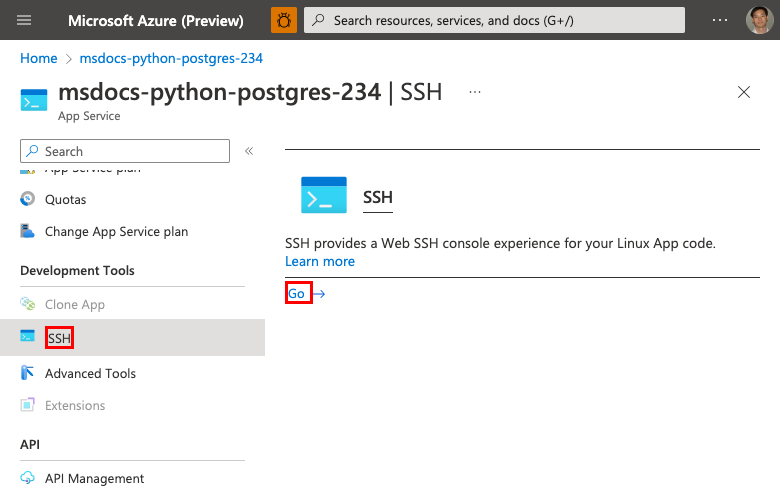
Step 1: Back in the App Service page, in the left menu,
- Select SSH.
- Select Go.
Step 2: In the SSH terminal, run flask db upgrade. If it succeeds, App Service is connecting successfully to the database.
Only changes to files in /home can persist beyond app restarts. Changes outside of /home aren't persisted.
5. Browse to the app
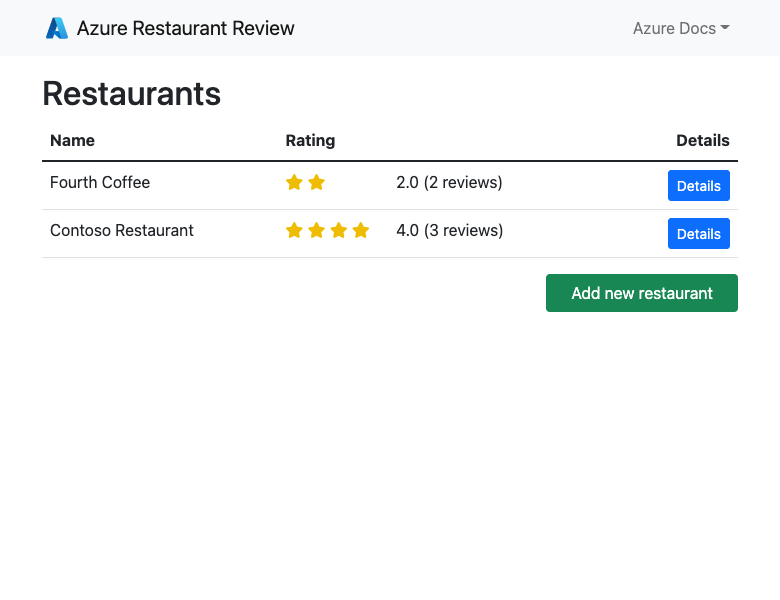
Step 1: In the App Service page:
- From the left menu, select Overview.
- Select the URL of your app. You can also navigate directly to
https://<app-name>.azurewebsites.net.
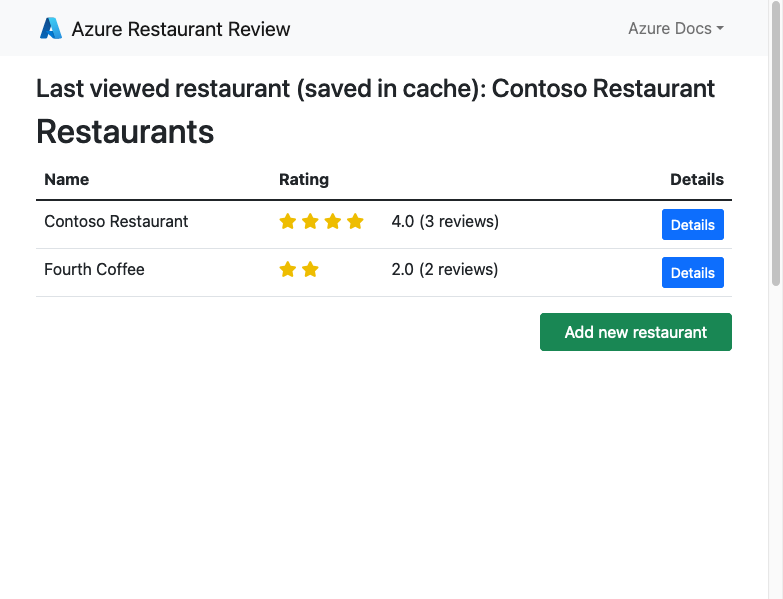
Step 2: Add a few restaurants to the list. Congratulations, you're running a web app in Azure App Service, with secure connectivity to Azure Database for PostgreSQL.
6. Stream diagnostic logs
Azure App Service captures all messages output to the console to help you diagnose issues with your application. The sample app includes print() statements to demonstrate this capability as shown below.
@app.route('/', methods=['GET'])
def index():
print('Request for index page received')
restaurants = Restaurant.query.all()
return render_template('index.html', restaurants=restaurants)
Step 1: In the App Service page:
- From the left menu, select App Service logs.
- Under Application logging, select File System.
- In the top menu, select Save.
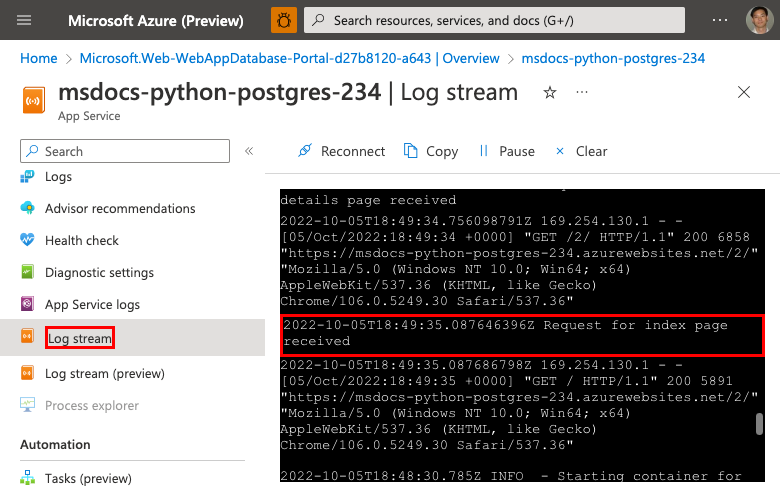
Step 2: From the left menu, select Log stream. You see the logs for your app, including platform logs and logs from inside the container.
Learn more about logging in Python apps in the series on setting up Azure Monitor for your Python application.
7. Clean up resources
When you're finished, you can delete all of the resources from your Azure subscription by deleting the resource group.
Step 1: In the search bar at the top of the Azure portal:
- Enter the resource group name.
- Select the resource group.
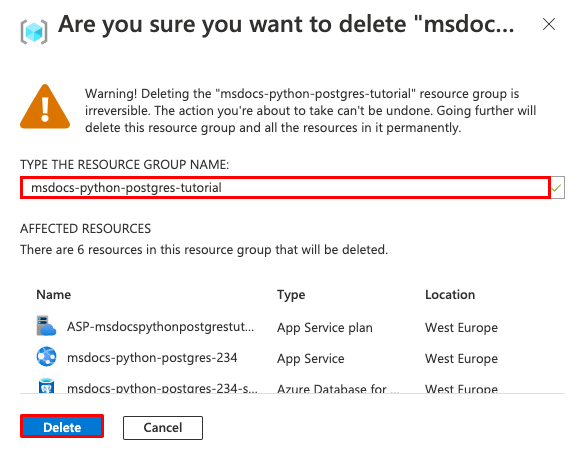
Step 2: In the resource group page, select Delete resource group.
Step 3:
- Enter the resource group name to confirm your deletion.
- Select Delete.
1. Create Azure resources and deploy a sample app
In this step, you create the Azure resources and deploy a sample app to App Service on Linux. The steps used in this tutorial create a set of secure-by-default resources that include App Service and Azure Database for PostgreSQL.
If you haven't already, clone the sample repository's
starter-no-infrabranch in a local terminal.git clone -b starter-no-infra https://github.com/Azure-Samples/msdocs-flask-postgresql-sample-app cd msdocs-flask-postgresql-sample-appThis cloned branch is your starting point. It contains a simple data-drive Flask application.
From the repository root, run
azd init.azd init --template python-app-service-postgresql-infraWhen prompted, give the following answers:
Question Answer The current directory is not empty. Would you like to initialize a project here in '<your-directory>'? Y What would you like to do with these files? Keep my existing files unchanged Enter a new environment name Type a unique name. The azd template uses this name as part of the DNS name of your web app in Azure ( <app-name>.azurewebsites.net). Alphanumeric characters and hyphens are allowed.Run the
azd upcommand to provision the necessary Azure resources and deploy the app code. If you are not already signed-in to Azure, the browser will launch and ask you to sign-in. Theazd upcommand will also prompt you to select the desired subscription and location to deploy to.azd upThe
azd upcommand might take a few minutes to complete. It also compiles and deploys your application code, but you'll modify your code later to work with App Service. While it's running, the command provides messages about the provisioning and deployment process, including a link to the deployment in Azure. When it finishes, the command also displays a link to the deploy application.This azd template contains files (azure.yaml and the infra directory) that generate a secure-by-default architecture with the following Azure resources:
- Resource group → The container for all the created resources.
- App Service plan → Defines the compute resources for App Service. A Linux plan in the B1 tier is specified.
- App Service → Represents your app and runs in the App Service plan.
- Virtual network → Integrated with the App Service app and isolates back-end network traffic.
- Azure Database for PostgreSQL flexible server → Accessible only from within the virtual network. A database and a user are created for you on the server.
- Private DNS zone → Enables DNS resolution of the PostgreSQL server in the virtual network.
- Log Analytics workspace → Acts as the target container for your app to ship its logs, where you can also query the logs.
2. Use the database connection string
The azd template you use generated the connectivity variables for you already as app settings and outputs the them to the terminal for your convenience. App settings are one way to keep connection secrets out of your code repository.
In the azd output, find the app settings and find the settings
AZURE_POSTGRESQL_CONNECTIONSTRINGandAZURE_REDIS_CONNECTIONSTRING. To keep secrets safe, only the setting names are displayed. They look like this in the azd output:App Service app has the following settings: - AZURE_POSTGRESQL_CONNECTIONSTRING - AZURE_REDIS_CONNECTIONSTRING - FLASK_DEBUG - SCM_DO_BUILD_DURING_DEPLOYMENT - SECRET_KEYAZURE_POSTGRESQL_CONNECTIONSTRINGcontains the connection string to the Postgres database in Azure, andAZURE_REDIS_CONNECTIONSTRINGcontains the connection string to the Redis cache in Azure. You need to use them your code to connect to it. Open azureproject/production.py, uncomment the following lines, and save the file:conn_str = os.environ['AZURE_POSTGRESQL_CONNECTIONSTRING'] conn_str_params = {pair.split('=')[0]: pair.split('=')[1] for pair in conn_str.split(' ')} DATABASE_URI = 'postgresql+psycopg2://{dbuser}:{dbpass}@{dbhost}/{dbname}'.format( dbuser=conn_str_params['user'], dbpass=conn_str_params['password'], dbhost=conn_str_params['host'], dbname=conn_str_params['dbname'] )Your application code is now configured to connect to the PostgreSQL database in Azure. If you want, open
app.pyand see how theDATABASE_URIenvironment variable is used.In the terminal, run
azd deploy.azd deploy
4. Generate database schema
With the PostgreSQL database protected by the virtual network, the easiest way to run Flask database migrations is in an SSH session with the App Service container.
In the azd output, find the URL for the SSH session and navigate to it in the browser. It looks like this in the output:
Open SSH session to App Service container at: https://<app-name>.scm.azurewebsites.net/webssh/host
In the SSH terminal, run
flask db upgrade. If it succeeds, App Service is connecting successfully to the database.Note
Only changes to files in
/homecan persist beyond app restarts. Changes outside of/homearen't persisted.
5. Browse to the app
In the azd output, find the URL of your app and navigate to it in the browser. The URL looks like this in the AZD output:
Deploying services (azd deploy) (✓) Done: Deploying service web - Endpoint: https://<app-name>.azurewebsites.net/
Add a few restaurants to the list.
Congratulations, you're running a web app in Azure App Service, with secure connectivity to Azure Database for PostgreSQL.
6. Stream diagnostic logs
Azure App Service can capture console logs to help you diagnose issues with your application. For convenience, the azd template has already enabled logging to the local file system as well as shipping them to a Log Analytics workspace.
The sample app includes print() statements to demonstrate this capability as shown in the following snippet.
@app.route('/', methods=['GET'])
def index():
print('Request for index page received')
restaurants = Restaurant.query.all()
return render_template('index.html', restaurants=restaurants)
In the azd output, find the link to stream App Service logs and navigate to it in the browser. The link looks like this in the azd output:
Stream App Service logs at: https://portal.azure.com/#@/resource/subscriptions/<subscription-guid>/resourceGroups/<group-name>/providers/Microsoft.Web/sites/<app-name>/logStream
Learn more about logging in Python apps in the series on setting up Azure Monitor for your Python application.
7. Clean up resources
To delete all Azure resources in the current deployment environment, run azd down.
azd down
Troubleshooting
Listed below are issues you might encounter while trying to work through this tutorial and steps to resolve them.
I can't connect to the SSH session
If you can't connect to the SSH session, then the app itself has failed to start. Check the diagnostic logs for details. For example, if you see an error like KeyError: 'AZURE_POSTGRESQL_CONNECTIONSTRING', it might mean that the environment variable is missing (you might have removed the app setting).
I get an error when running database migrations
If you encounter any errors related to connecting to the database, check if the app settings (AZURE_POSTGRESQL_CONNECTIONSTRING) have been changed. Without that connection string, the migrate command can't communicate with the database.
Frequently asked questions
- How much does this setup cost?
- How do I connect to the PostgreSQL server that's secured behind the virtual network with other tools?
- How does local app development work with GitHub Actions?
- How is the Django sample configured to run on Azure App Service?
How much does this setup cost?
Pricing for the created resources is as follows:
- The App Service plan is created in Basic tier and can be scaled up or down. See App Service pricing.
- The PostgreSQL flexible server is created in the lowest burstable tier Standard_B1ms, with the minimum storage size, which can be scaled up or down. See Azure Database for PostgreSQL pricing.
- The virtual network doesn't incur a charge unless you configure extra functionality, such as peering. See Azure Virtual Network pricing.
- The private DNS zone incurs a small charge. See Azure DNS pricing.
How do I connect to the PostgreSQL server that's secured behind the virtual network with other tools?
- For basic access from a command-line tool, you can run
psqlfrom the app's SSH terminal. - To connect from a desktop tool, your machine must be within the virtual network. For example, it could be an Azure VM that's connected to one of the subnets, or a machine in an on-premises network that has a site-to-site VPN connection with the Azure virtual network.
- You can also integrate Azure Cloud Shell with the virtual network.
How does local app development work with GitHub Actions?
Using the autogenerated workflow file from App Service as an example, each git push kicks off a new build and deployment run. From a local clone of the GitHub repository, you make the desired updates and push to GitHub. For example:
git add .
git commit -m "<some-message>"
git push origin main
How is the Django sample configured to run on Azure App Service?
Note
If you are following along with this tutorial with your own app, look at the requirements.txt file description in each project's README.md file (Flask, Django) to see what packages you'll need.
The Django sample application configures settings in the azureproject/production.py file so that it can run in Azure App Service. These changes are common to deploying Django to production, and not specific to App Service.
Django validates the HTTP_HOST header in incoming requests. The sample code uses the
WEBSITE_HOSTNAMEenvironment variable in App Service to add the app's domain name to Django's ALLOWED_HOSTS setting.# Configure the domain name using the environment variable # that Azure automatically creates for us. ALLOWED_HOSTS = [os.environ['WEBSITE_HOSTNAME']] if 'WEBSITE_HOSTNAME' in os.environ else []Django doesn't support serving static files in production. For this tutorial, you use WhiteNoise to enable serving the files. The WhiteNoise package was already installed with requirements.txt, and its middleware is added to the list.
# WhiteNoise configuration MIDDLEWARE = [ 'django.middleware.security.SecurityMiddleware', # Add whitenoise middleware after the security middleware 'whitenoise.middleware.WhiteNoiseMiddleware',Then the static file settings are configured according to the Django documentation.
SESSION_ENGINE = "django.contrib.sessions.backends.cache" STATICFILES_STORAGE = 'whitenoise.storage.CompressedManifestStaticFilesStorage'
For more information, see Production settings for Django apps.
Next steps
Advance to the next tutorial to learn how to secure your app with a custom domain and certificate.
Learn how App Service runs a Python app: