Hi all,
We are currently doing a PoC for External ID. For the administration of the tenant I've set up a bunch of cloud-only admin accounts (type=member, NOT local accounts). These should be used for configuration of the tenant, user flows etc. I've created a Conditional Access Policy enforcing MFA for all users (my initial guest account is excluded for fallback scenario).
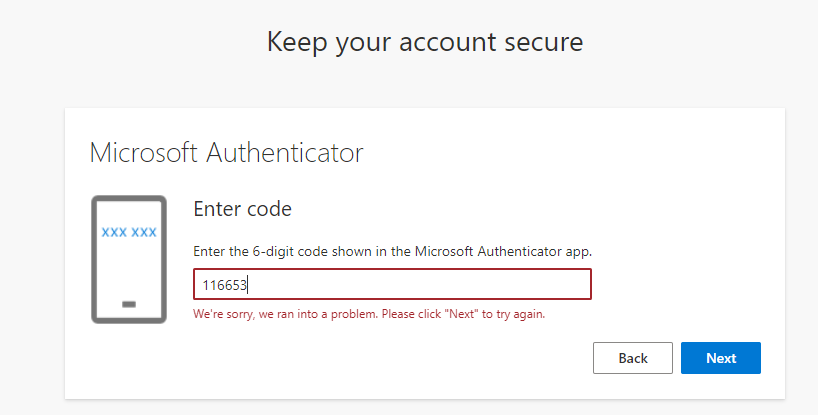
When now new cloud admins sign-in the first time they get prompted for MFA registration (which is intended). However, during the setup of MFA with Authenticator (QR Code & 6-digit code) they get a the generic error "We're sorry, we ran into a problem. Please click "Next" to try again." This happens for QR code scan but also for entering a code instead. First of all, fun thing is that they get prompted for Authenticator by default, which is officially not supported by External ID (only SMS / Email OTP). However, this method worked for my initial (workforce tenant) Guest Account, from which i created the External ID tenant initially from but not for newly created regular member accounts.
I've then tried to disable Authenticator and Software OATH as method (leaving SMS & Email OTP) in the authentication methods (which are by default enabled - but not supported officially?!) and tried to login with a newly created test user (Type = member / NOT local account) ******@xxxxciam.onmicrosoft.com and get the message "AADSTS500208: The domain is not a valid login domain for the account type":
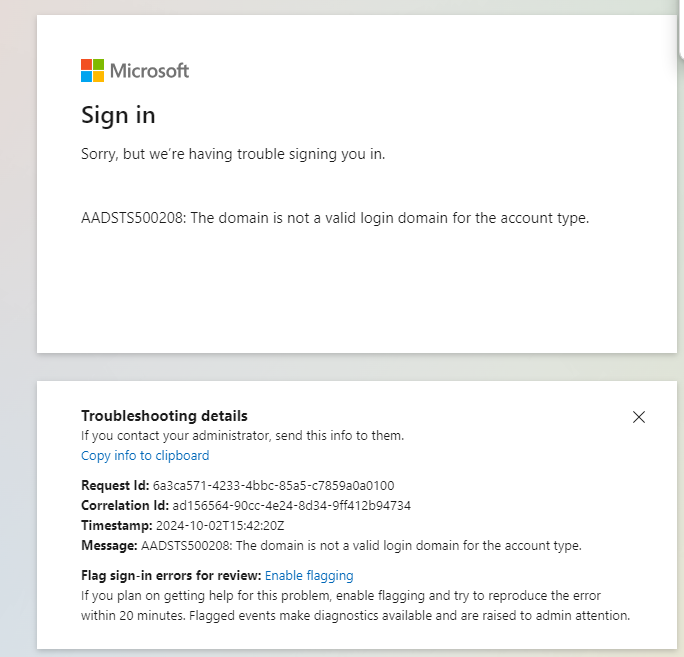
I know that this error can happen for app registration with web apps (customer flow), but there we don't have the issue - this works as expected (with the correct ciamlogin.com endpoint). The issue is just for "admins" I'd like to manage as regular member users (NOT local account).
Meanwhile I got new admins working by sending out guest invites to admin users of our "connected" workforce tenant (the one from which the External ID tenant was originally created from). But even there i first had "We ran into a problem errors" - but after logout and sign-in again it worked.
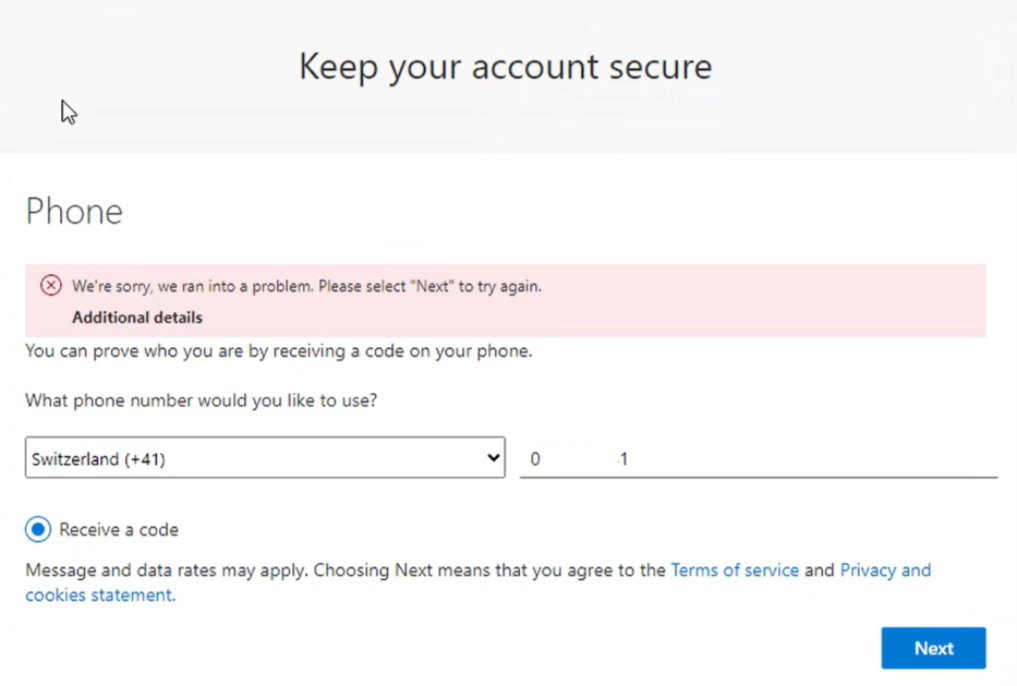
The whole concept of the External ID tenant administration in combination with MFA methods seems to have failures in the MFA registration flows implementation. Why is it even possible to configure authentication methods that are not supported? And why does e.g. Authenticator work for Guest accounts but not for member accounts (non Local Account). Can you please assist me on these issues? I've also created a post in the Microsoft Identity Advisors in parallel.
This blocks a proper setup of further admins created as member users (non Local Accounts).
Thanks for your support.
Reto