Load test secured endpoints with Azure Load Testing
In this article, you learn how to use Azure Load Testing with application endpoints that require authentication. Depending on your application implementation, you might use an access token, user credentials, managed identity or client certificates for authenticating requests.
Azure Load Testing supports the following options for authenticated endpoints:
- Authenticate with a shared secret or user credentials
- Authenticate with client certificates
- Authenticate with a managed identity
Prerequisites
- An Azure account with an active subscription. If you don't have an Azure subscription, create a free account before you begin.
- An Azure load testing resource. To create a load testing resource, see Create and run a load test.
Authenticate with a shared secret or credentials
In this scenario, the application endpoint requires that you use a shared secret, such as an access token, an API key, or user credentials to authenticate.
The following diagram shows how to use shared secrets or credentials to authenticate with an application endpoint in your load test.
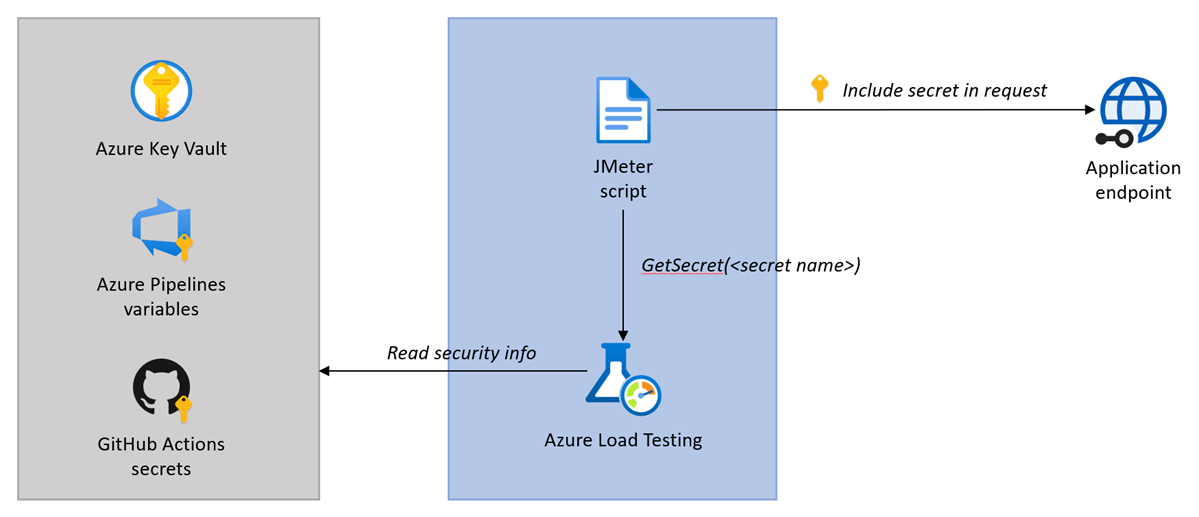
The flow for authenticating with a shared secret or user credentials is:
- Securely store the secret or credentials, for example in Azure Key Vault, or the CI/CD secrets store.
- Reference the secret in the load test configuration.
- In the JMeter script, retrieve the secret value with the
GetSecretfunction and pass the secret value to the application request.
Securely store the secret
To avoid storing, and disclosing, security information in the JMeter script, you can securely store secrets in Azure Key Vault or in the CI/CD secrets store.
You can add the security information in a secrets store in either of two ways:
Add the secret information in Azure Key Vault. Follow the steps in Parameterize load tests with secrets to store a secret and authorize your load testing resource to read its value.
Add the secret information as a secret in CI/CD (GitHub Actions secrets or Azure Pipelines secret variables).
Reference the secret in the load test configuration
Before you can retrieve the secret value in the JMeter test script, you have to reference the secret in the load test configuration.
In the Azure portal, you can reference secrets that are stored in Azure Key Vault. To add and configure a load test secret in the Azure portal:
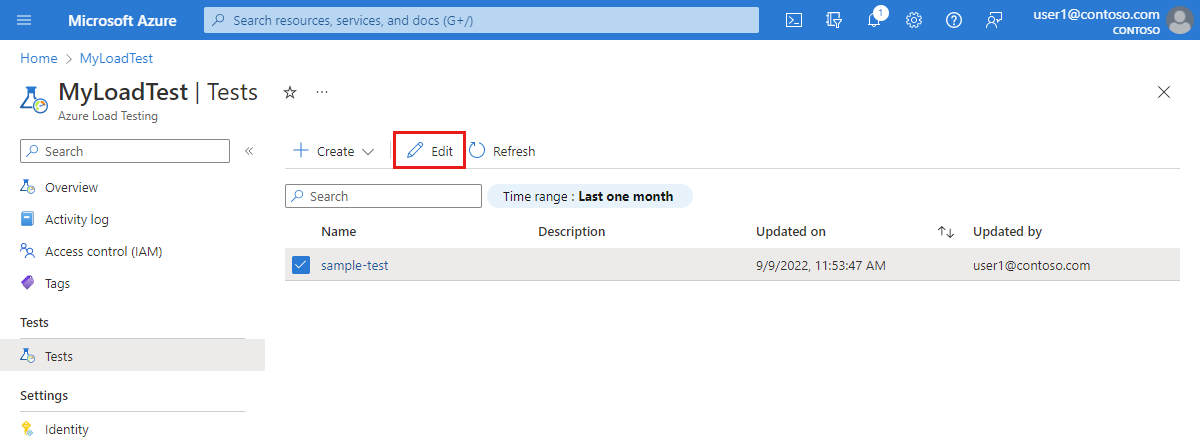
Navigate to your load testing resource in the Azure portal, and then select Tests to view the list of load tests.
Select your test from the list, and then select Edit to edit the load test configuration.
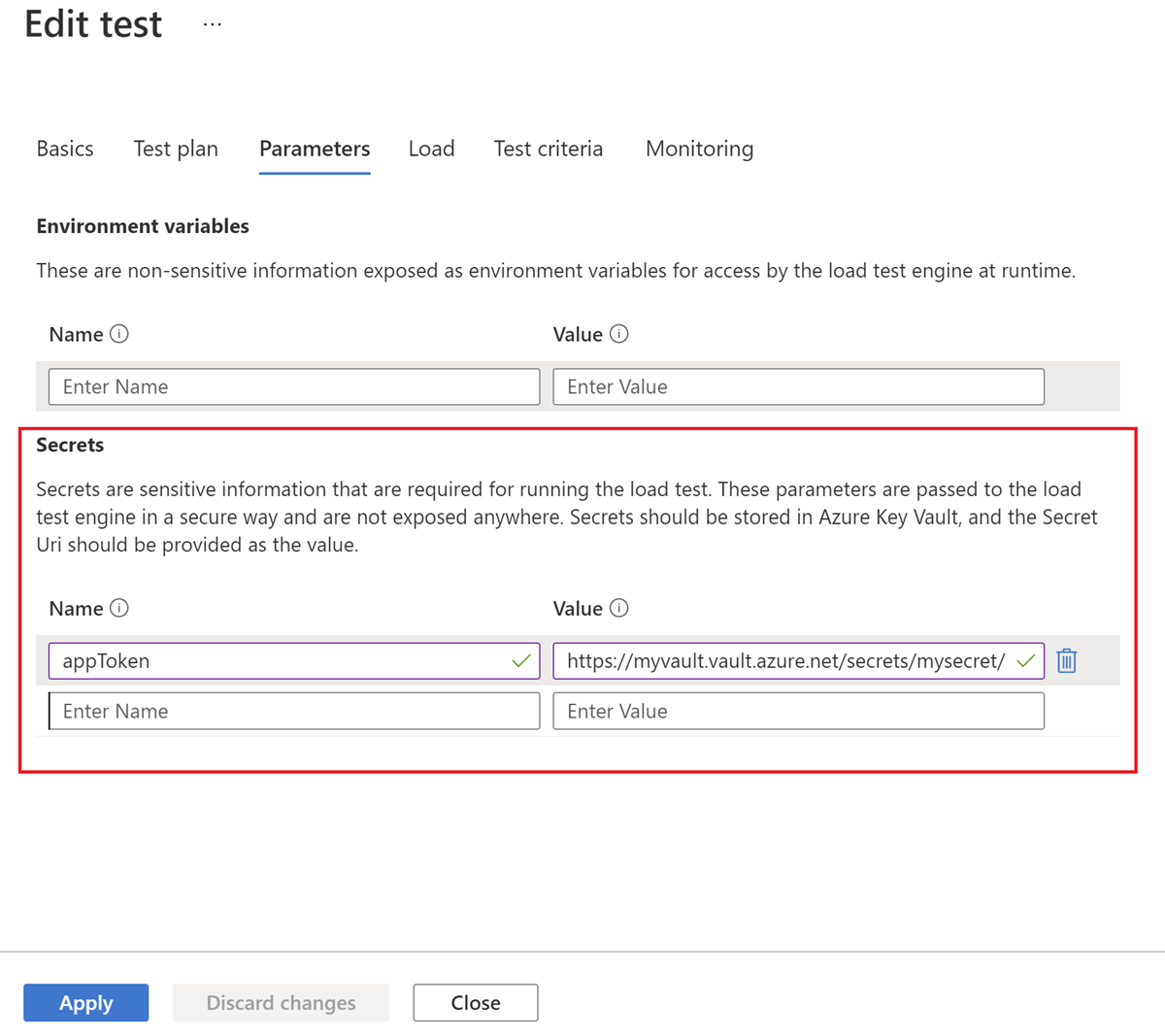
On the Parameters tab, enter the details of the secret.
Field Value Name Name of the secret. You provide this name to the GetSecretfunction to retrieve the secret value in the JMeter script.Value Matches the Azure Key Vault Secret identifier. Select Apply, to save the load test configuration changes.
Retrieve and use the secret value in the JMeter script
You can now retrieve the secret value in the JMeter script by using the GetSecret custom function and pass it to the application request. For example, use an Authorization HTTP header to pass an OAuth token to a request.
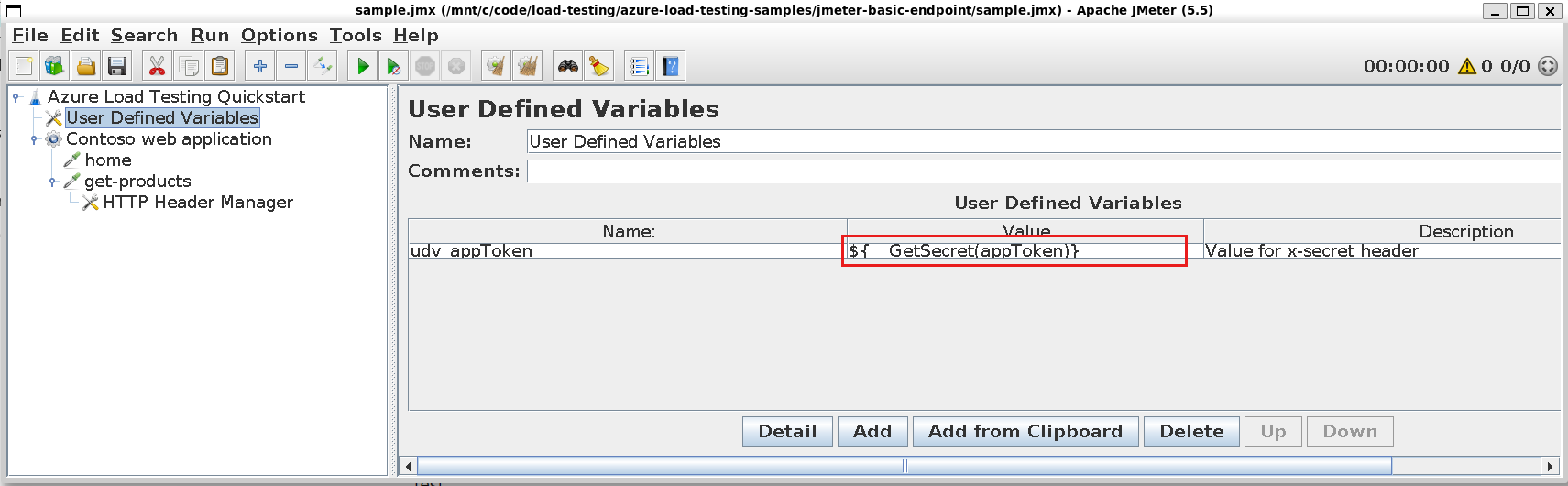
Create a user-defined variable that retrieves the secret value with the
GetSecretcustom function:The
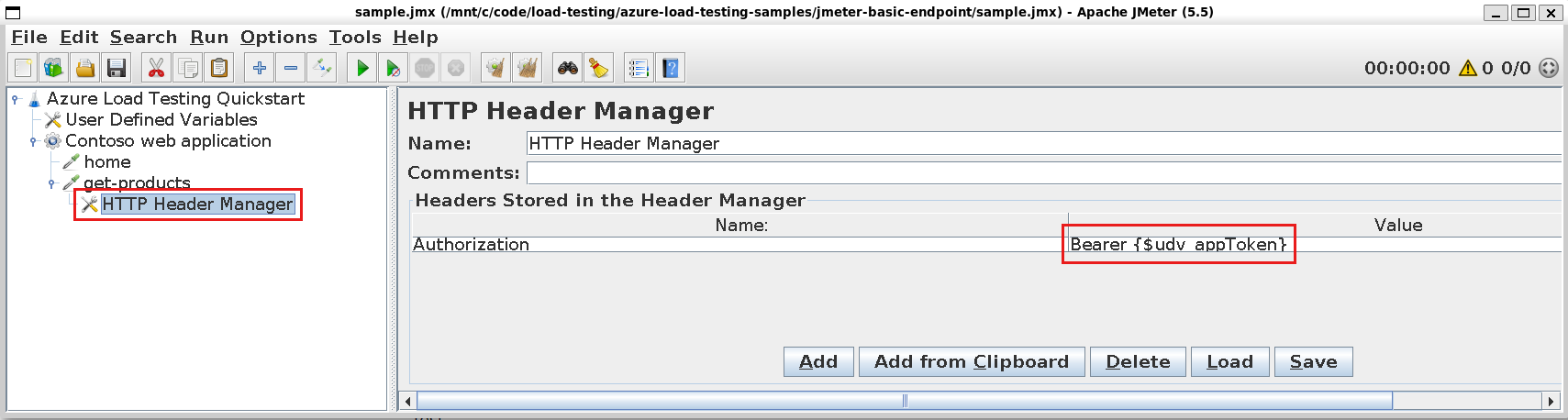
GetSecretfunction abstracts retrieving the value from either Azure Key Vault or the CI/CD secrets store.Update the JMeter sampler component to pass the secret in the request.
For example, to provide an OAuth2 access token, you configure the
AuthorizationHTTP header by adding anHTTP Header Manager:
Authenticate with client certificates
In this scenario, the application endpoint requires that you use a client certificate to authenticate. Azure Load Testing supports Public Key Certificate Standard #12 (PKCS12) type of certificates. You can use only one client certificate in a load test.
The following diagram shows how to use a client certificate to authenticate with an application endpoint in your load test.
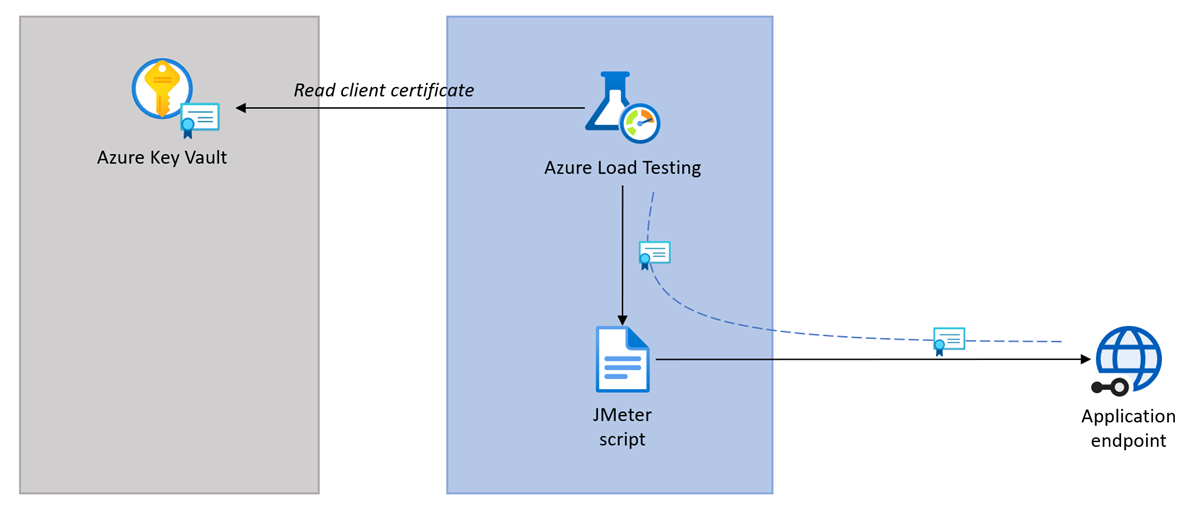
The flow for authenticating with client certificates is:
- Securely store the client certificate in Azure Key Vault.
- Reference the certificate in the load test configuration.
- Azure Load Testing transparently passes the certificate to all application requests in JMeter.
Store the client certificate in Azure Key Vault
To avoid storing, and disclosing, the client certificate alongside the JMeter script, you store the certificate in Azure Key Vault.
Follow the steps in Import a certificate to store your certificate in Azure Key Vault.
Important
Azure Load Testing only supports PKCS12 certificates. Upload the client certificate in PFX file format.
Grant access to your Azure key vault
When you store load test secrets or certificates in Azure Key Vault, your load testing resource uses a managed identity for accessing the key vault. After you configure the manage identity, you need to grant the managed identity of your load testing resource permissions to read these values from the key vault.
To grant your Azure load testing resource permissions to read secrets or certificates from your Azure key vault:
In the Azure portal, go to your Azure key vault resource.
If you don't have a key vault, follow the instructions in Azure Key Vault quickstart to create one.
On the left pane, select Access Policies, and then select + Create.
On the Permissions tab, under Secret permissions, select Get, and then select Next.
Note
Azure Load Testing retrieves certificates as a secret to ensure that the private key for the certificate is available.
On the Principal tab, search for and select the managed identity for the load testing resource, and then select Next.
If you're using a system-assigned managed identity, the managed identity name matches that of your Azure load testing resource.
Select Next again.
When your test runs, the managed identity that's associated with your load testing resource can now read the secrets or certificates for your load test from your key vault.
Reference the certificate in the load test configuration
To pass the client certificate to application requests, you need to reference the certificate in the load test configuration.
To add a client certificate to your load test in the Azure portal:
Navigate to your load testing resource in the Azure portal. If you don't have a load test yet, create a new load test using a JMeter script.
On the left pane, select Tests to view the list of load tests.
Select your test from the list, and then select Edit, to edit the load test configuration.
On the Parameters tab, enter the details of the certificate.
Field Value Name Name of the certificate. Value Matches the Azure Key Vault Secret identifier of the certificate. Select Apply, to save the load test configuration changes.
When you run your load test, Azure Load Testing retrieves the client certificate from Azure Key Vault, and automatically injects it in each JMeter web request.
Authenticate with a managed identity
In this scenario, the application endpoint requires that you use a managed identity to authenticate. You can use both system-assigned and user-assigned managed identities.
The flow for authenticating using a managed identity is:
- Assign the managed identity that the target endpoint identifies to the Azure Load Testing resource.
- Select the managed identity in the load test configuration.
You need to set up your load tests script to fetch access token using managed identity and to use the token to authenticate the requests to the target endpoint. For example, you can get a token through an HTTP REST call to the Azure Instance Metadata Service (IMDS) endpoint and then pass the token to a request using the Authorization HTTP header.
Assign the managed identity
Assign the managed identity that has the required access to the target endpoint to your Azure Load Testing resource. When you run the test, Azure Load Testing assigns this identity to the engine instances. This ensures that your requests to fetch access tokens using the managed identity are successful.
You can use either a system-assigned managed identity or a user-assigned managed identity,
To use a system-assigned managed identity, first assign a system-assigned managed identity to your Azure Load Testing resource. Once it is enabled, provide the required RBAC permissions for this identity on the target endpoint.
To use a user-assigned managed identity, first assign the user-assigned identity to your Azure Load Testing resource. If this identity does not have the required RBAC permissions on the target endpoint, provide the required permissions. If your test script uses multiple user-assigned multiple identities, assign the multiple identities to your resource and ensure that they have the required RBAC permissions.
Select the managed identity in the load test configuration
Select the required managed identity when you create or edit a test in Azure Load Testing.
To select and configure a managed identity for authentication in the Azure portal:
Navigate to your load testing resource in the Azure portal, and then select Tests to view the list of load tests.
Select your test from the list, and then select Edit to edit the load test configuration.
On the Test plan tab, configure the Managed identity for authentication scenarios. Select 'System-assigned identity' or 'User-assigned identity' as required.
If you selected 'User-assigned identity', select the required identities from the User-assigned identity dropdown.
Select Apply, to save the load test configuration changes.
Important
Load distribution across regions is not enabled when you use managed identities for authentication.
Related content
Learn more about how to parameterize a load test.
Learn more about using multiple certificates in a load test.