Set up traffic mirroring
This article provides a step-by-step guide to deploying your network sensor, ensuring the correct traffic mirroring options are chosen to achieve accurate and reliable network data collection.
Review the network architecture
Before you deploy the sensor to the network, it's crucial to review the network architecture. These steps include:
Review the network diagram. For more information, see review architecture or create a network diagram.
Estimate the total number of devices to be monitored. For more information, see calculate devices in your network.
Identify VLANs that contain OT networks. For more information, see customize a VLAN name.
Determine which OT protocols need to be monitored (Profinet, S7, Modbus, etc.). For more information, see supported protocols.
Select the sensor locations and traffic mirroring method
Based on the network architecture and the chosen mirroring method, select the best locations for your network sensors ensuring that they capture the necessary Layer 2 (L2) traffic.
Compile a list all of the locations in the network where the sensors should be placed. For more information, see identifying interesting traffic points.
Validate the sensor location
After deciding on a potential location for the sensor, users should validate the presence of L2 and OT protocols. It's recommended to use tools like Wireshark to verify these protocols at the potential sensor location. For example:
Wireshark displays the list of protocols identified by the sensor and the amount of data being monitored, thereby validating the location of your sensor. If protocols don't appear or don't detect any data, this indicates that the sensor is incorrectly placed or set up in the network. For example:
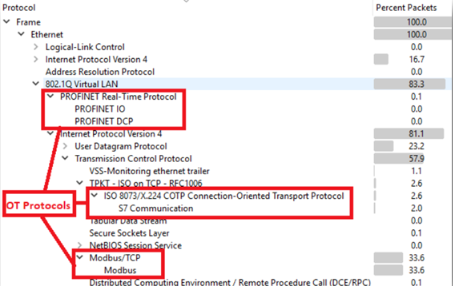
This step is crucial to ensure effective monitoring of your OT networks. For more information, see validate traffic mirroring.
Deploy your sensor
After validating the sensor and mirroring method, deploy the sensors. For more information, see install software on OT sensors.
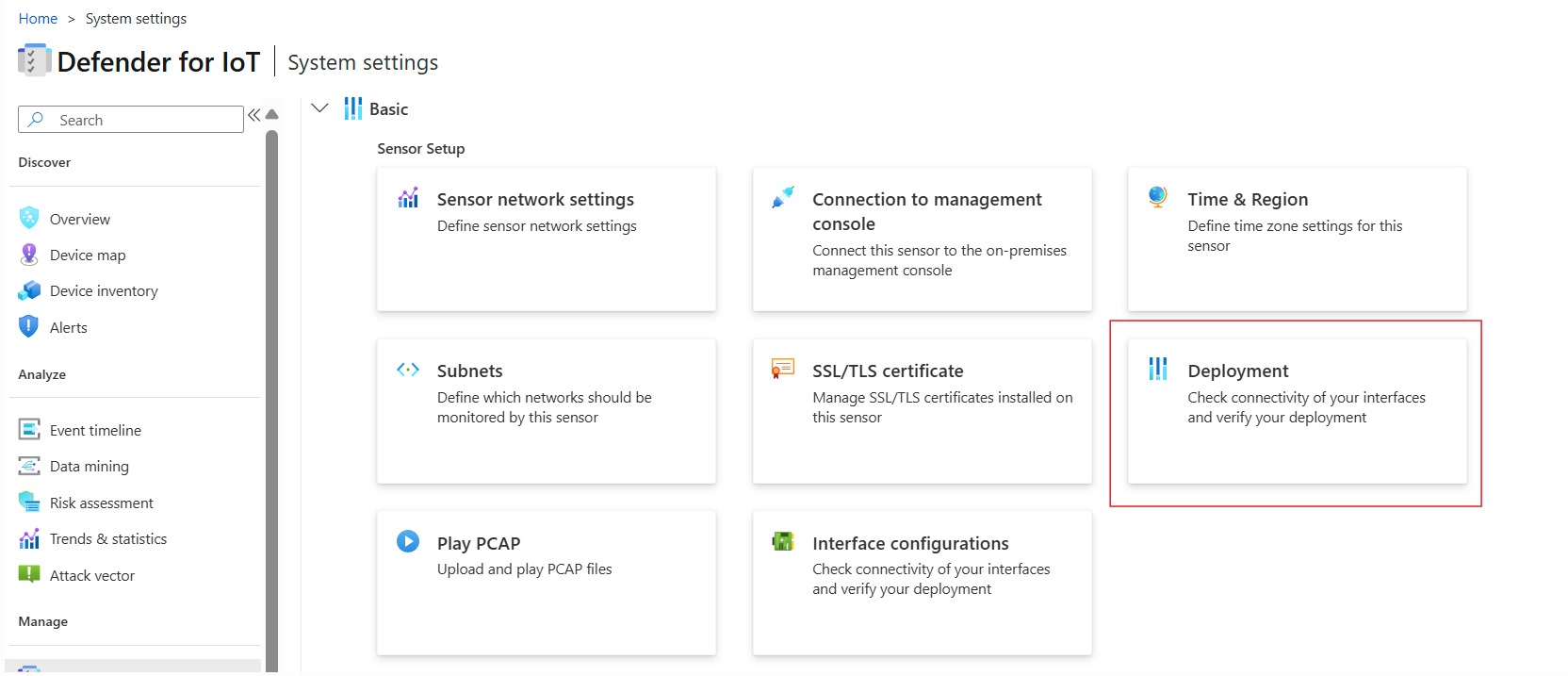
Validate after deployment
It's essential to validate the monitoring interfaces and activate them. We recommend using the Deployment tool in the sensor system setting to monitor the networks monitored by the sensor.
To validate your sensor:
Verify that the number of devices in the inventory is reasonable.
Check the type classification for devices listed in the inventory.
Confirm the visibility of OT protocol names on the device's inventory.
Ensure L2 protocols are monitored by identifying MAC addresses in the inventory.
If information doesn't appear, review the SPAN configuration and recheck the deployment tool in the sensor which provides visibility of the subnets monitored and the status of the OT protocols, for example: