How to create a secure Azure AI Foundry hub and project with a managed virtual network
Important
Items marked (preview) in this article are currently in public preview. This preview is provided without a service-level agreement, and we don't recommend it for production workloads. Certain features might not be supported or might have constrained capabilities. For more information, see Supplemental Terms of Use for Microsoft Azure Previews.
You can secure your Azure AI Foundry hub, projects, and managed resources in a managed virtual network. With a managed virtual network, inbound access is only allowed through a private endpoint for your hub. Outbound access can be configured to allow either all outbound access, or only allowed outbound that you specify. For more information, see Managed virtual network.
Important
The managed virtual network doesn't provide inbound connectivity for your clients. For more information, see the Connect to the hub section.
Prerequisites
- An Azure subscription. If you don't have an Azure subscription, create a free account before you begin.
- An Azure Virtual Network that you use to securely connect to Azure services. For example, you might use Azure Bastion, VPN Gateway or ExpressRoute to connect to the Azure Virtual Network from your on-premises network. If you don't have an Azure Virtual Network, you can create one by following the instructions in Create a virtual network.
Create a hub
From the Azure portal, search for
Azure AI Foundryand create a new resource by selecting + New Azure AI.Enter your hub name, subscription, resource group, and location details. You can also select an existing Azure AI services resource or create a new one.
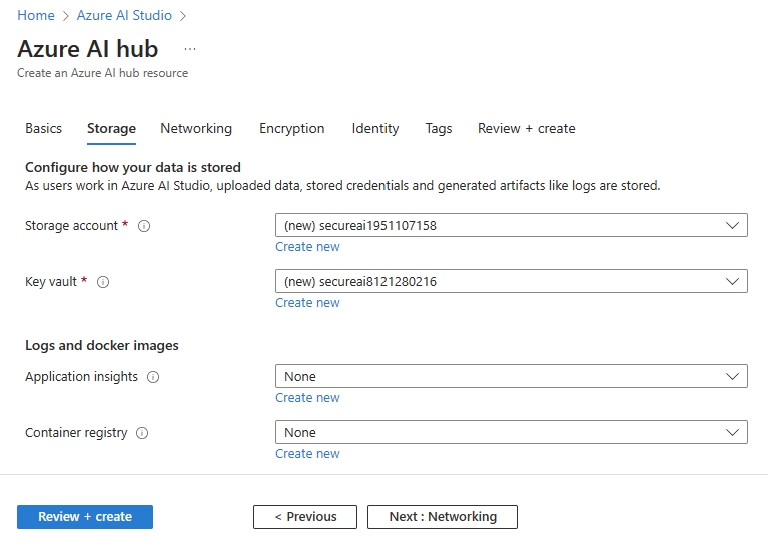
Select Next: Storage. Select an existing Storage account and Key vault resource or create new ones. Optionally, choose an existing Application insights, and Container Registry for logs and docker images.
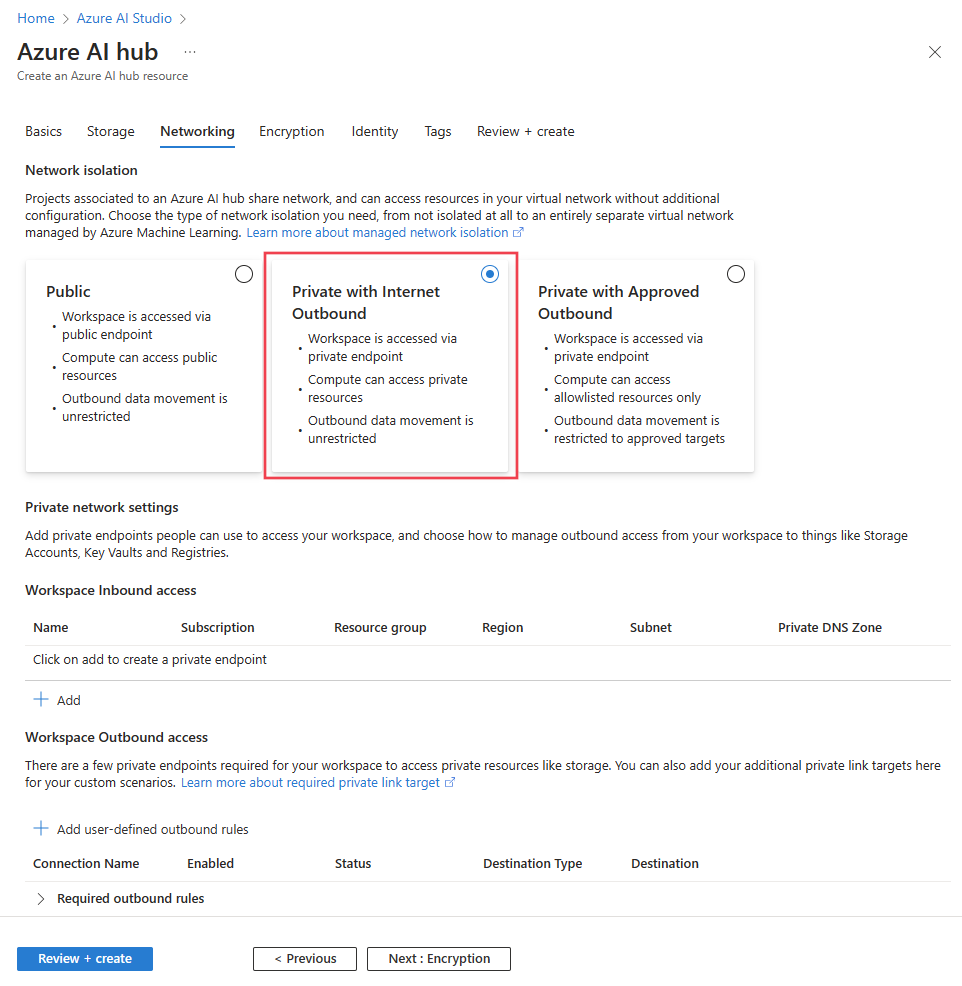
Select Next: Networking to configure the managed virtual network that Azure AI Foundry uses to secure its hub and projects.
Select Private with Internet Outbound, which allows compute resources to access the public internet for resources such as Python packages.
To allow your clients to connect through your Azure Virtual Network to the hub, use the following steps to add a private endpoint.
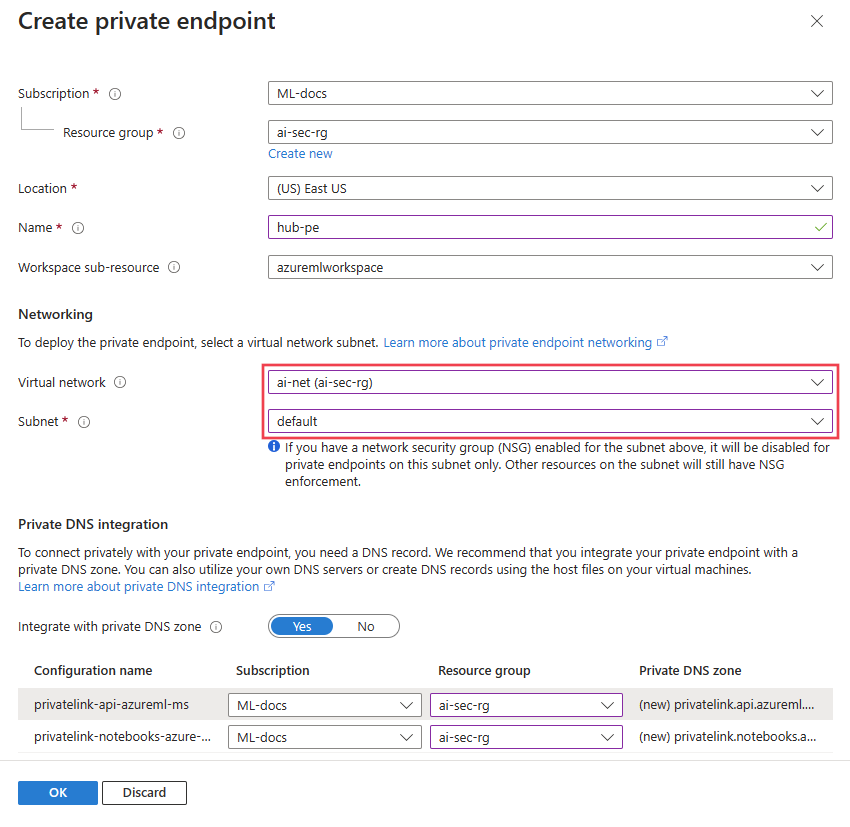
Select + Add from the Workspace inbound access section of the Networking tab. The Create private endpoint form is displayed.
Enter a unique value in the Name field. Select the Virtual network (Azure Virtual Network) that your clients connect to. Select the Subnet that the private endpoint connects to.
Select Ok to save the endpoint configuration.
Select Review + create, then Create to create the hub. Once the hub has been created, any projects or compute instances created from the hub inherit the network configuration.
Connect to the hub
The managed virtual network doesn't directly provide access to your clients. Instead, your clients connect to an Azure Virtual Network that you manage. There are multiple methods that you might use to connect clients to the Azure Virtual Network. The following table lists the common ways that clients connect to an Azure Virtual Network:
| Method | Description |
|---|---|
| Azure VPN gateway | Connects on-premises networks to an Azure Virtual Network over a private connection. Connection is made over the public internet. |
| ExpressRoute | Connects on-premises networks into the cloud over a private connection. Connection is made using a connectivity provider. |
| Azure Bastion | Connects to a virtual machine inside the Azure Virtual Network using your web browser. |