@SharmaAyushNokiaINGurgaon-5163, Thank you for reaching out. For fetching an access token for a certain API, you would need to specify in the scope section the permission for that exposed API. You can find the scopes under the Scopes section present under the Expose an API blade.
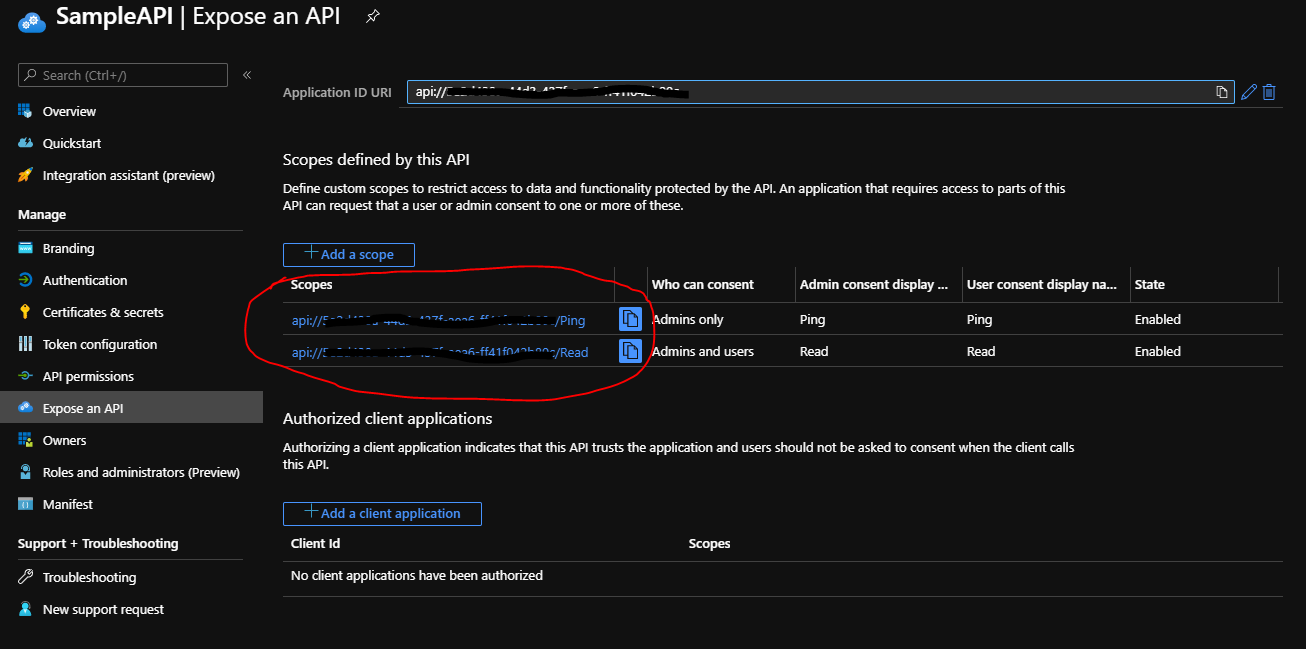
Once you have the scopes, in your request you can specify them. Please take a look at the sample request below:
https://login.microsoftonline.com/common/oauth2/v2.0/authorize?client_id=5e2d438a-44d3-437f-aea6-ff41f042b80c&response_type=code&redirect_uri=http%3A%2F%2Flocalhost%3A1234&response_mode=fragment&scope=openid%20offline_access%20https%3A%2F%2F5e2d438a-44d3-437f-aea6-ff41f042b80c%2FRead&state=12345
You can also use the scope "api://5e2d438a-44d3-437f-aea6-ff41f042b80c/.default" and it would add all the available permissions for that Exposed API in the request that is being sent.
To validate an id_token or an access_token, your app should validate both the token's signature and the claims. To validate access tokens, your app should also validate the issuer, the audience, and the signing tokens. These need to be validated against the values in the OpenID discovery document. For example, the tenant-independent version of the document is located at https://login.microsoftonline.com/common/.well-known/openid-configuration.
The Azure AD middleware has built-in capabilities for validating access tokens, and you can browse through our samples to find one in the language of your choice. [I have included the JAVA samples in the hyperlink above called samples]
For more details you can refer to the following doc: https://learn.microsoft.com/en-us/azure/active-directory/develop/access-tokens#validating-tokens
Hope this helps.
Do let us know if this helps and if there are any more queries around this, please do let us know so that we can help you further. Also, please do not forget to accept the response as Answer; if the above response helped in answering your query.