I'm confused about the compliance result I'm getting against a test NSG of mine. I've tried the policy rule with "equals" and "match" with the same result. Basically, the policy rule says the current value must not match the target value. The target value is for "80" as in port 80, and the current value is an empty array. The value doesn't match, but it still shows up as non-compliant. What gives?
Here is the policy rule:
if: {
allOf: [{
field: "type",
equals: "Microsoft.Network/networkSecurityGroups/securityRules"
},
{
field: "Microsoft.Network/networkSecurityGroups/securityRules/access",
equals: "Allow"
},
{
field: "Microsoft.Network/networkSecurityGroups/securityRules/direction",
equals: "Inbound"
},
{
anyOf: [
{
field: "Microsoft.Network/networkSecurityGroups/securityRules/sourceAddressPrefix",
in: [
"*",
"Internet",
"Any",
"0.0.0.0/0"
]
},
{
field: "Microsoft.Network/networkSecurityGroups/securityRules/sourceAddressPrefixes[*]",
in: [
"*",
"Internet",
"Any",
"0.0.0.0/0"
]
}
]
},
{
anyOf: [
{
field: "Microsoft.Network/networkSecurityGroups/securityRules/destinationPortRange",
equals: "80"
},
{
field: "Microsoft.Network/networkSecurityGroups/securityRules/destinationPortRange",
equals: "443"
},
{
field: "Microsoft.Network/networkSecurityGroups/securityRules/destinationPortRanges[*]",
match: "80"
},
{
field: "Microsoft.Network/networkSecurityGroups/securityRules/destinationPortRanges[*]",
match: "443"
}
]
}
]
},
then: {
effect: "[parameters('effect')]"
}
Here is the non-compliance message:
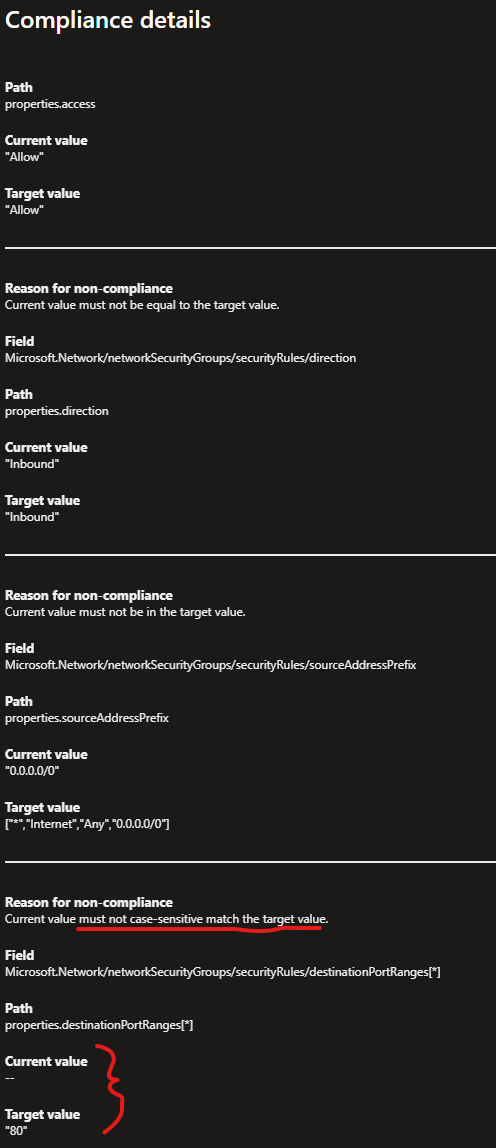
Here is the JSON from the NSG rule that should NOT be matching and should be marked compliant.
"securityRules": [
{
"name": "AllowTagCustom53Inbound",
"id": "/subscriptions/xxxx/resourceGroups/test1/providers/Microsoft.Network/networkSecurityGroups/sootestnsg01/securityRules/AllowTagCustom53Inbound",
"etag": "W/\"xxxx\"",
"type": "Microsoft.Network/networkSecurityGroups/securityRules",
"properties": {
"provisioningState": "Succeeded",
"description": "test bad rule 1",
"protocol": "UDP",
"sourcePortRange": "*",
"destinationPortRange": "53",
"sourceAddressPrefix": "Internet",
"destinationAddressPrefix": "*",
"access": "Allow",
"priority": 100,
"direction": "Inbound",
"sourcePortRanges": [],
"destinationPortRanges": [],
"sourceAddressPrefixes": [],
"destinationAddressPrefixes": []
}
},