Microsoft Entra Connect: Enabling device writeback
Note
A subscription to Microsoft Entra ID P1 or P2 is required for device writeback.
The following documentation provides information on how to enable the device writeback feature in Microsoft Entra Connect. Device Writeback is used in the following scenarios:
- Enable Windows Hello for Business using hybrid certificate trust deployment
- Enable Conditional Access based on devices to ADFS (2012 R2 or higher) protected applications (relying party trusts).
This provides additional security and assurance that access to applications is granted only to trusted devices. For more information on Conditional Access, see Managing Risk with Conditional Access and Setting up On-premises Conditional Access using Microsoft Entra Device Registration.
Important
Part 1: Install Microsoft Entra Connect
Install Microsoft Entra Connect using Custom or Express settings. Microsoft recommends starting with all users and groups successfully synchronized before you enable device writeback.
Part 2: Enable device writeback in Microsoft Entra Connect
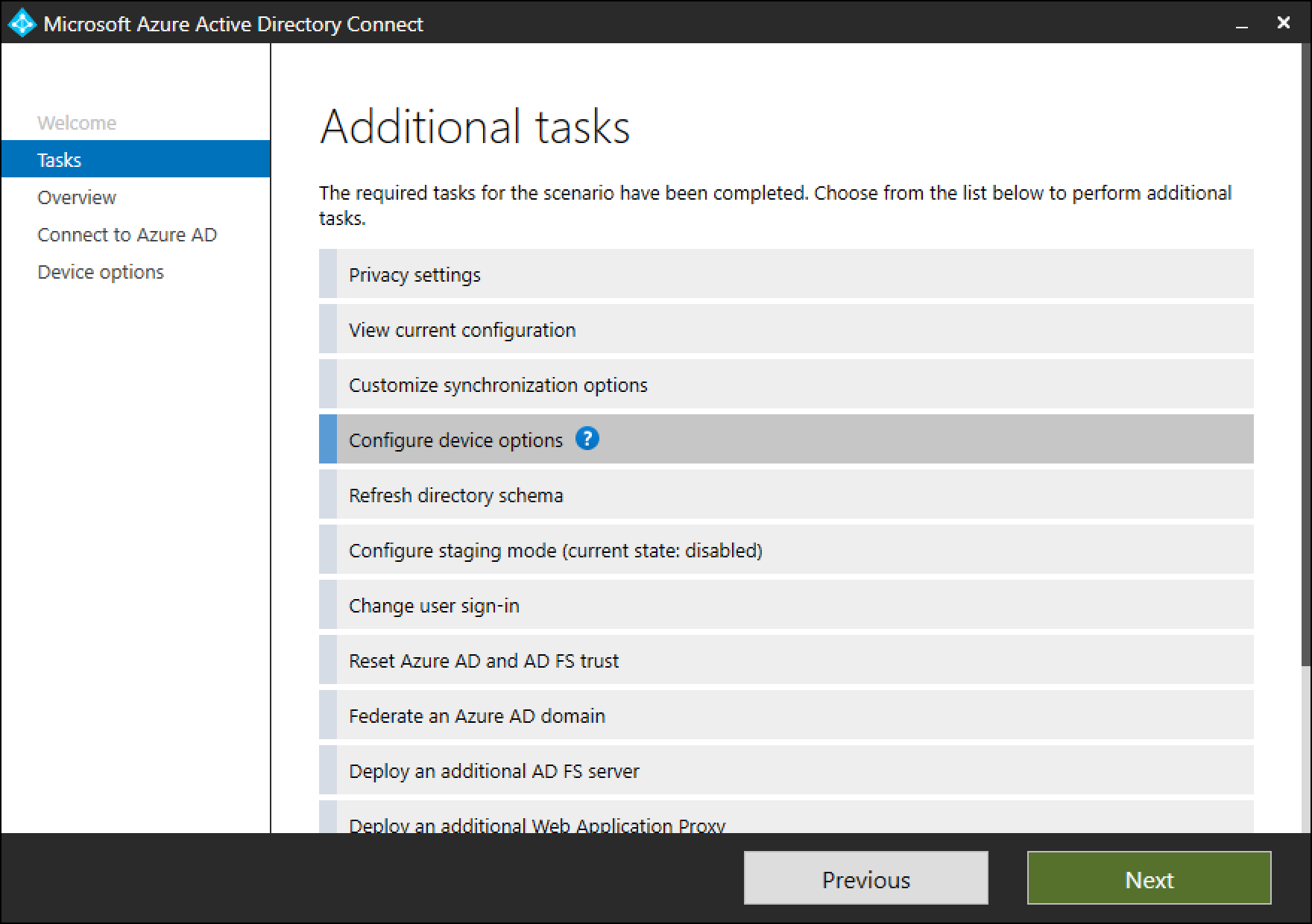
Run the installation wizard again. Select Configure device options from the Additional Tasks page and select Next.
Note
The new Configure device options is available only in version 1.1.819.0 and newer.
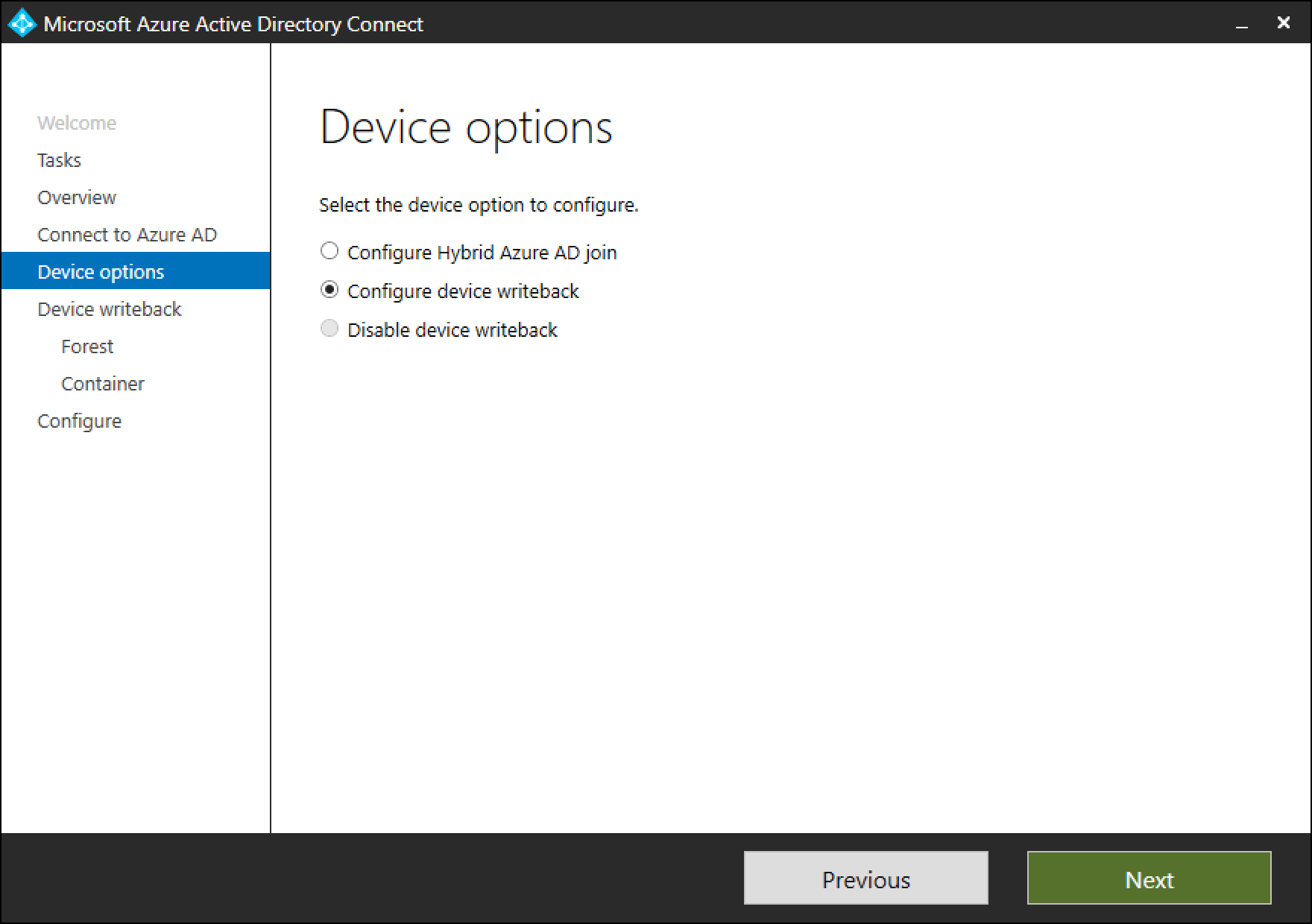
On the device options page, select Configure device writeback. Option to Disable device writeback isn't available until device writeback is enabled. Select on Next to move to the next page in the wizard.
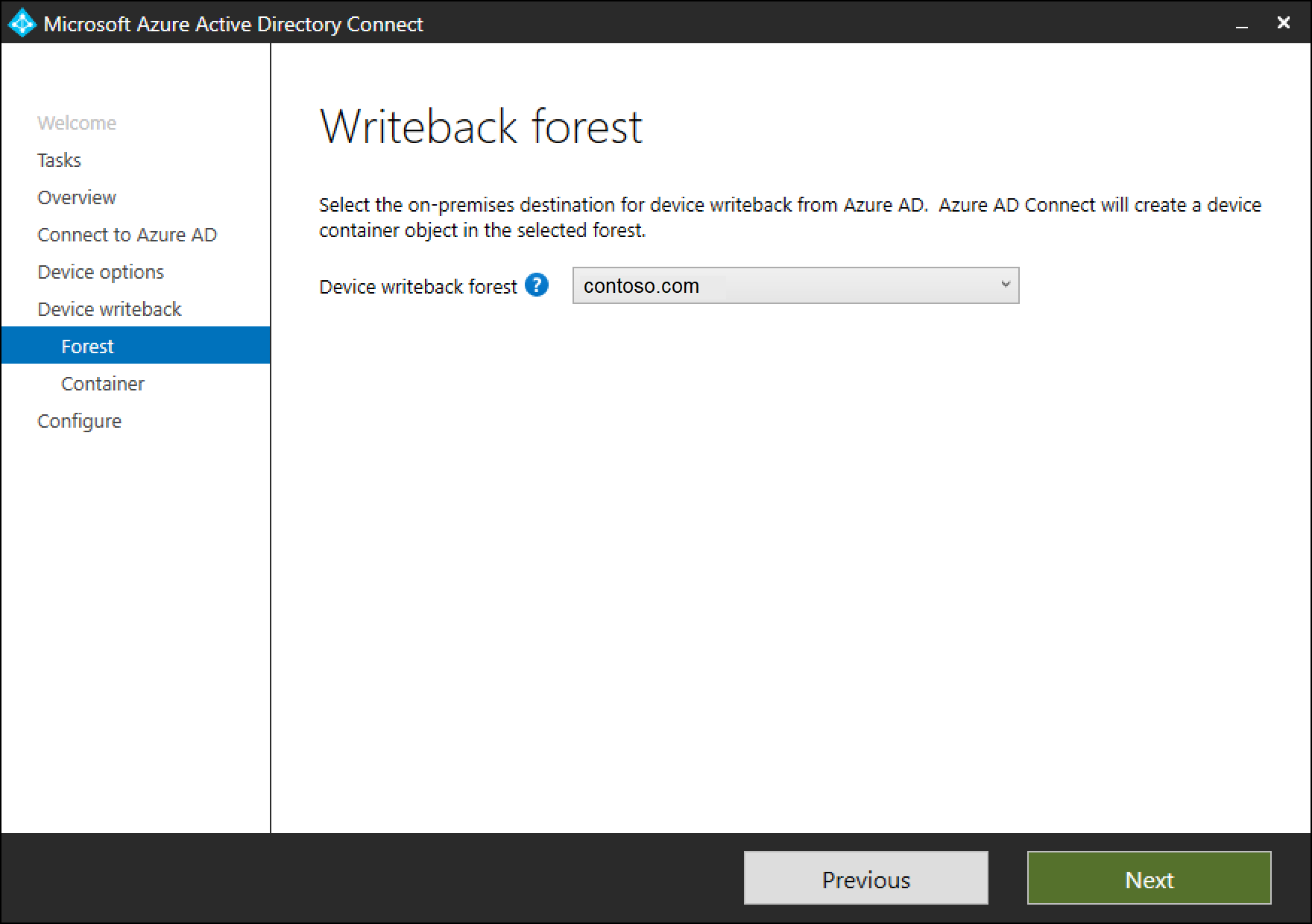
On the writeback page, you'll see the supplied domain as the default Device writeback forest.
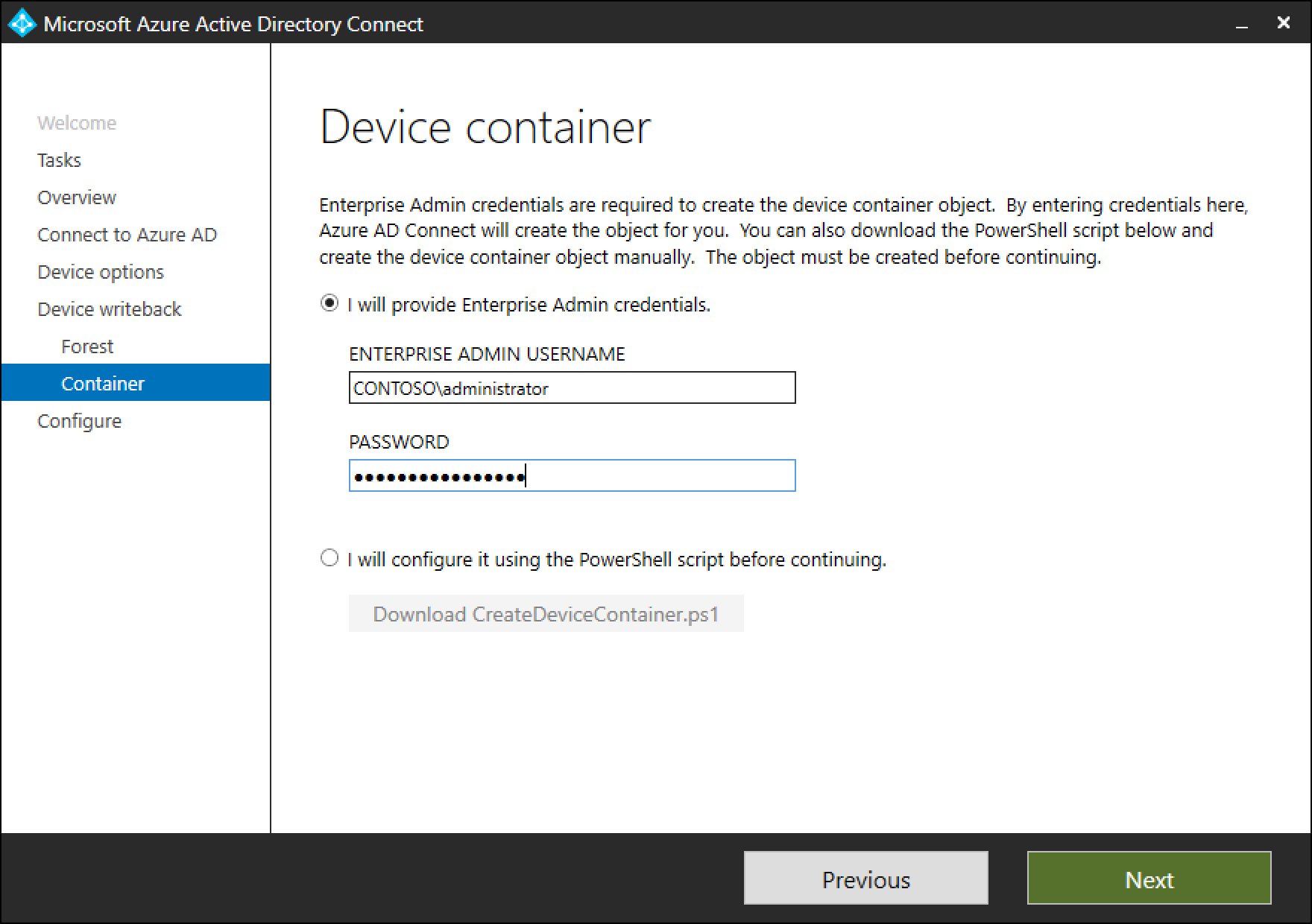
Device container page provides option of preparing the active directory by using one of the two available options:
a. Provide enterprise administrator credentials: If the enterprise administrator credentials are provided for the forest where devices need to be written back, Microsoft Entra Connect prepares the forest automatically during the configuration of device writeback.
b. Download PowerShell script: Microsoft Entra Connect autogenerates a PowerShell script that can prepare the active directory for device writeback. In case the enterprise administrator credentials can't be provided in Microsoft Entra Connect, it's suggested to download the PowerShell script. Provide the downloaded PowerShell script CreateDeviceContainer.ps1 to the enterprise administrator of the forest where devices are written back to.
The following operations are performed for preparing the active directory forest:
- If they don't exist already, creates and configures new containers and objects under CN=Device Registration Configuration,CN=Services,CN=Configuration,[forest-dn].
- If they don't exist already, creates and configures new containers and objects under CN=RegisteredDevices,[domain-dn]. Device objects are created in this container.
- Sets necessary permissions on the Microsoft Entra Connector account, to manage devices on your Active Directory.
- Only needs to run on one forest, even if Microsoft Entra Connect is being installed on multiple forests.
Verify Devices are synchronized to Active Directory
Device writeback should now be working properly. It can take up to 3 hours for device objects to be written-back to AD. To verify that your devices are being synced properly, do the following steps after the sync rules complete:
Launch Active Directory Administrative Center.
Expand RegisteredDevices, within the Domain that is being federated.
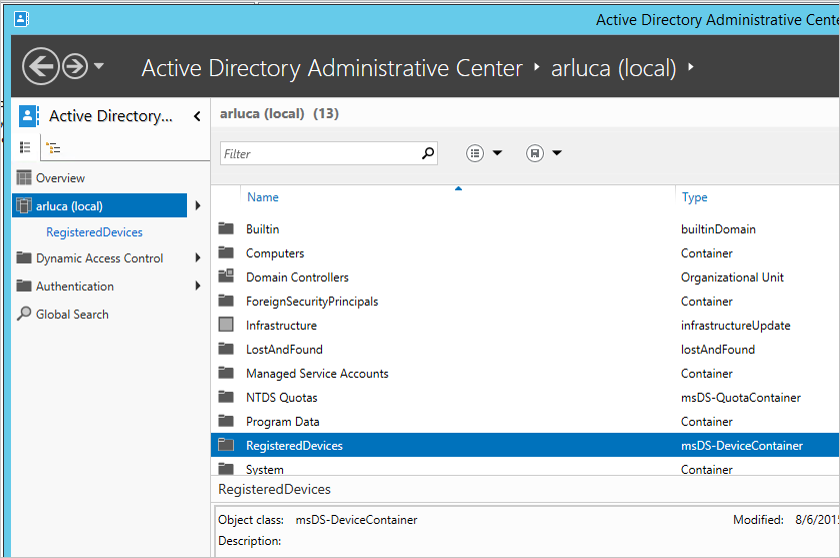
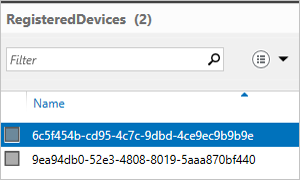
Current registered devices are listed there.
Enable Conditional Access
Detailed instructions to enable this scenario are available within Setting up On-premises Conditional Access using Microsoft Entra Device Registration.
Troubleshooting
The writeback checkbox is still disabled
If the checkbox for device writeback isn't enabled even though you've followed the previous steps, the following steps guide you through what the installation wizard is verifying before the box is enabled.
First things first:
- The forest where the devices are present must have the forest schema upgraded to Windows 2012 R2 level so that the device object and associated attributes are present .
- If the installation wizard is already running, then any changes aren't detected. In this case, complete the installation wizard and run it again.
- Make sure the account you provide in the initialization script is actually the correct user used by the Active Directory Connector. To verify this, follow these steps:
- From the start menu, open Synchronization Service.
- Open the Connectors tab.
- Find the Connector with type Active Directory Domain Services and select it.
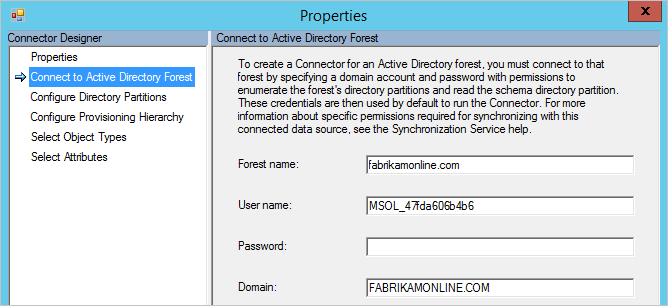
- Under Actions, select Properties.
- Go to Connect to Active Directory Forest. Verify that the domain and user name specified on this screen match the account provided to the script.
Verify configuration in Active Directory:
- Verify that the Device Registration Service is located in the following location (CN=DeviceRegistrationService,CN=Device Registration Services,CN=Device Registration Configuration,CN=Services,CN=Configuration) under configuration naming context.
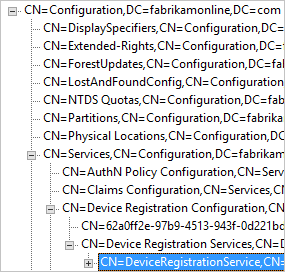
- Verify there's only one configuration object by searching the configuration namespace. If there's more than one, delete the duplicate.
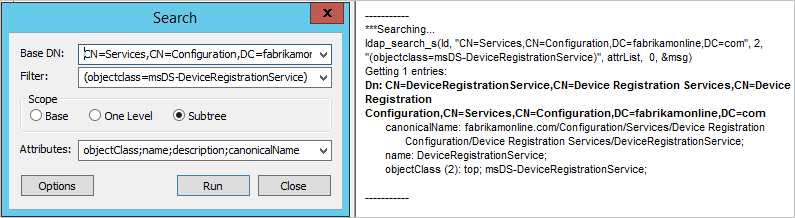
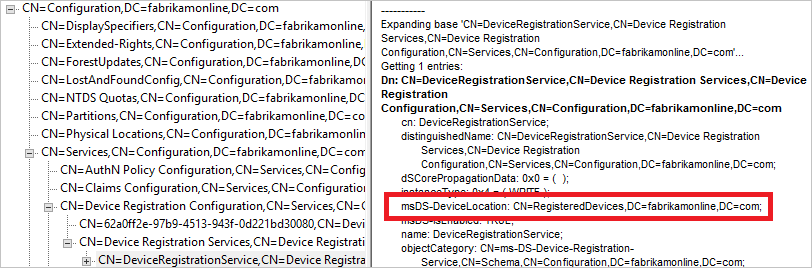
- On the Device Registration Service object, make sure the attribute msDS-DeviceLocation is present and has a value. Look up this location and make sure it's present with the objectType msDS-DeviceContainer.
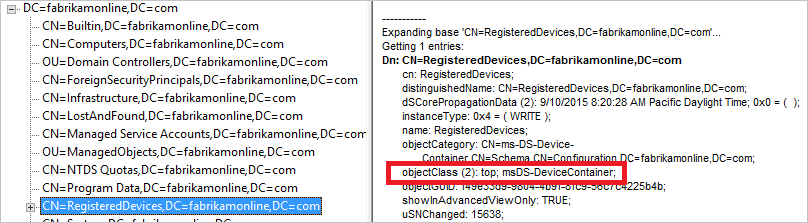
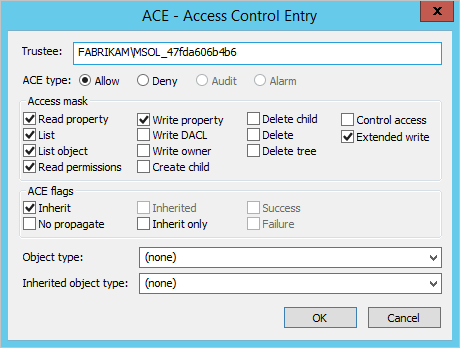
- Verify the account used by the Active Directory Connector has required permissions on the Registered Devices container found by the previous step. This is the expected permissions on this container:
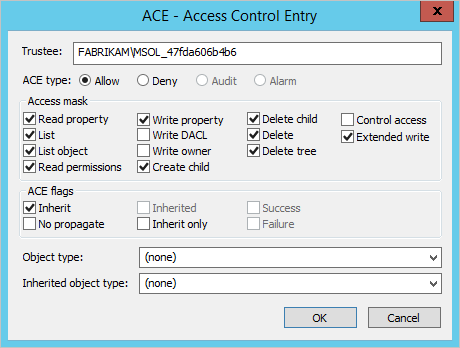
- Verify the Active Directory account has permissions on the CN=Device Registration Configuration,CN=Services,CN=Configuration object.
Additional Information
- Managing Risk With Conditional Access
- Setting up On-premises Conditional Access using Microsoft Entra Device Registration
Next steps
Learn more about Integrating your on-premises identities with Microsoft Entra ID.