Migrate identity management scenarios from SAP IDM to Microsoft Entra
In addition to its business applications, SAP offers a range of identity and access management technologies, including SAP Cloud Identity Services and SAP Identity Management (SAP IDM) to help their customers maintain the identities in their SAP applications. SAP IDM, which organizations deploy on-premises, historically provided identity and access management for SAP R/3 deployments. SAP will end maintenance for SAP Identity Management. For those organizations that were using SAP Identity Management, Microsoft and SAP are collaborating to develop guidance for those organizations to migrate their identity management scenarios from SAP Identity Management to Microsoft Entra.
Identity modernization is a critical and essential step towards improving an organization’s security posture and protecting their users and resources from identity threats. It is a strategic investment that can deliver substantial benefits beyond a stronger security posture, like improving user experience and optimizing operational efficiency. The administrators at many organizations expressed interest in moving the center of their identity and access management scenarios entirely to the cloud. Some organizations will no longer have an on-premises environment, while others integrate the cloud-hosted identity and access management with their remaining on-premises applications, directories and databases. For more information on cloud transformation for identity services, see cloud transformation posture and transition to the cloud.
Microsoft Entra offers a universal cloud-hosted identity platform that provides your people, partners, and customers with a single identity to access cloud and on-premises applications, and collaborate from any platform and device. This document provides guidance on migration options and approaches for moving Identity and Access Management (IAM) scenarios from SAP Identity Management to Microsoft Entra cloud-hosted services, and will be updated as new scenarios become available to migrate.
Overview of Microsoft Entra and its SAP product integrations
Microsoft Entra is a family of products including Microsoft Entra ID (formerly Azure Active Directory) and Microsoft Entra ID Governance. Microsoft Entra ID is a cloud-based identity and access management service that employees and guests can use to access resources. It provides strong authentication and secure adaptive access, and integrates with both on-premises legacy apps and thousands of software-as-a-service (SaaS) application, delivering a seamless end-user experience. Microsoft Entra ID Governance offers additional capabilities to automatically establish user identities in the apps users need to access, and update and remove user identities as job status or roles change.
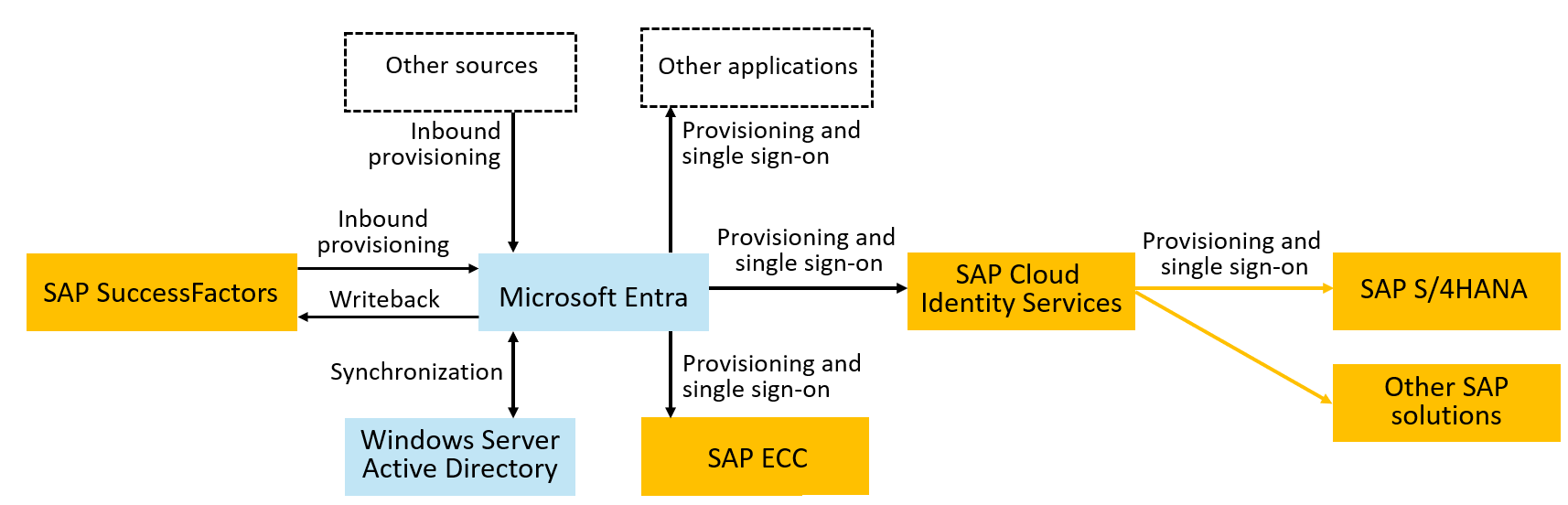
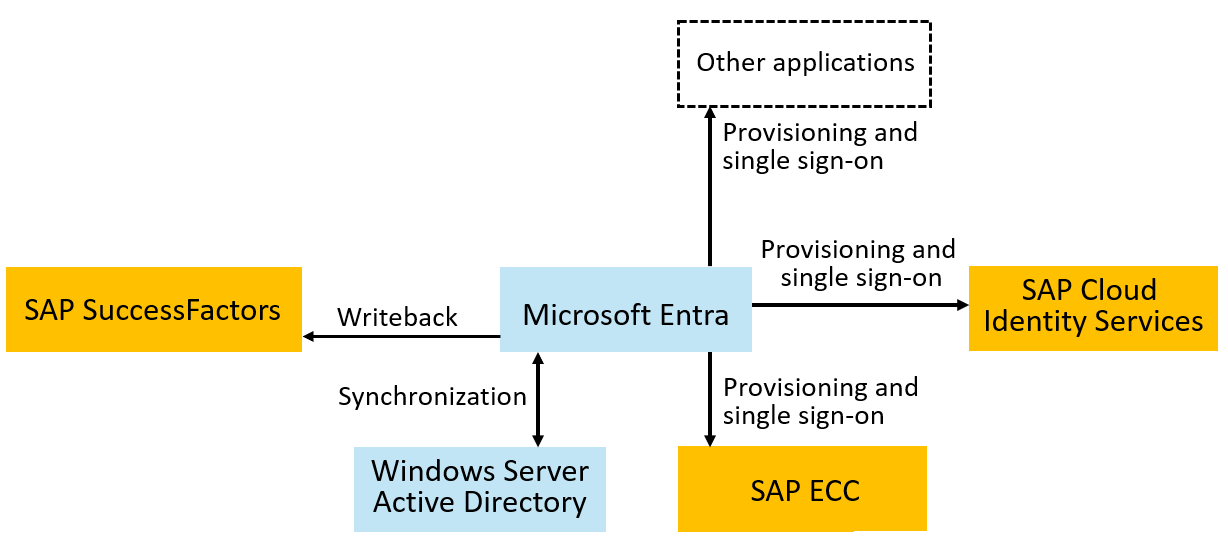
Microsoft Entra provides user interfaces, including the Microsoft Entra admin center, the myapps and myaccess portals, and provides a REST API for identity management operations and delegated end user self-service. Microsoft Entra ID includes integrations for SuccessFactors, SAP ERP Central Component (SAP ECC), and through the SAP Cloud Identity Services, can provide provisioning and single sign-on to S/4HANA and many other SAP applications. For more information on these integrations, see Manage access to your SAP applications. Microsoft Entra also implements standard protocols such as SAML, SCIM, SOAP, and OpenID Connect to directly integrate with many more applications for single sign-on and provisioning. Microsoft Entra also has agents, including Microsoft Entra Connect cloud sync and a provisioning agent to connect Microsoft Entra cloud services with an organization's on-premises applications, directories, and databases.
The following diagram illustrates an example topology for user provisioning and single sign-on. In this topology, workers are represented in SuccessFactors, and need to have accounts in a Windows Server Active Directory domain, in Microsoft Entra, SAP ECC, and SAP cloud applications. This example illustrates an organization that has a Windows Server AD domain; however, Windows Server AD isn't required.
Planning a migration of identity management scenarios to Microsoft Entra
Since the introduction of SAP IDM, the identity and access management landscape has evolved with new applications and new business priorities, and so the approaches recommended for addressing IAM use cases will in many cases be different today than those organizations previously implemented for SAP IDM. Therefore, organizations should plan a staged approach for scenario migration. For example, one organization may prioritize migrating an end-user self-service password reset scenario as one step, and then once that is complete, moving a provisioning scenario. For another example, organization may choose to first deploy Microsoft Entra features in a separate staging tenant, operated in parallel with the existing identity management system and the production tenant, and then bring configurations for scenarios one-by-one from the staging tenant to the production tenant and decommission that scenario from the existing identity management system. The order in which an organization chooses to move their scenarios will depend upon their overall IT priorities and the impact on other stakeholders, such as end users needing a training update, or application owners. Organizations may also structure IAM scenario migration alongside other IT modernization, such as moving other scenarios outside of identity management from on-premises SAP technology to SuccessFactors, S/4HANA, or other cloud services. You may also wish to use this opportunity to clean up and remove outdated integrations, access rights or roles, and consolidate where necessary.
To begin planning your migration,
- Identify current and planned IAM use cases in your IAM modernization strategy.
- Analyze the requirements of those use cases and match those requirements to the capabilities of Microsoft Entra services.
- Determine timeframes and stakeholders for implementation of new Microsoft Entra capabilities to support migration.
- Determine the cutover process for your applications to move the single sign-on, identity lifecycle, and access lifecycle controls to Microsoft Entra.
As a SAP IDM migration will likely involve integrations with existing SAP applications, review the integrations with SAP sources and targets guidance for how to determine the sequence of application onboarding and how applications will integrate with Microsoft Entra.
Services and integration partners for deploying Microsoft Entra with SAP applications
Partners can also help your organization with planning and deployment for Microsoft Entra with SAP applications such as SAP S/4HANA. Customers can engage partners listed in the Microsoft Solution Partner finder or can choose from these services and integration partners listed in the following table. The descriptions and linked pages are provided by the partners themselves. You can use the description to identify a partner for deploying Microsoft Entra with SAP applications that you may want to contact and learn more about.
| Name | Description |
|---|---|
| Accenture and Avanade | "Accenture and Avanade are global leaders in Microsoft Security and SAP Services. With our unique combination of Microsoft and SAP skills, we can help you to understand and successfully plan a migration from SAP IdM to Microsoft Entra ID. Through our delivery assets and expertise, Avanade and Accenture can help you accelerate your migration project to achieve your goals with less risk. Accenture is uniquely positioned to assist large global enterprises, complemented by Avanade’s deep experience with supporting both mid to large enterprises on their migration journey. Our extensive knowledge and experience can help you accelerate your journey to replace SAP IdM, whilst maximizing your investment in Microsoft Entra ID." |
| ARMIS | "ARMIS, with over 20 years of digital transformation experience, offers global technology solutions and is a trusted Microsoft Partner. We specialize in Security, Data & AI, and Business Applications, delivering innovative solutions that enhance efficiency and sustainable growth using the Microsoft Entra Suite for improved security and identity governance." |
| Campana & Schott | "Campana & Schott is an international management and technology consultancy with more than 600 employees in Europe and the U.S. We combine more than 30 years of project management and transformation experience with in-depth expertise in Microsoft technologies, IT strategy and IT organization. As a Microsoft Solution Partner for Microsoft Cloud, we provide modern security for Microsoft 365, SaaS applications and legacy on-premises applications." |
| DXC Technology | "DXC Technology helps global companies run their mission-critical systems and operations while modernizing IT, optimizing data architectures, and ensuring security and scalability across public, private, and hybrid clouds. With 30+ years of global strategic partnership with Microsoft and SAP, DXC has rich experience in SAP IDM implementations across industries." |
| Edgile, a Wipro Company | "Edgile, a Wipro Company, draws upon 25 years of expertise with both SAP and Microsoft 365 to seamlessly migrate identity and access management (IDM) for our valued customers. As a Microsoft Entra Launch Partner and an SAP Global Strategic Services Partner (GSSP), we stand out in the field of IAM modernization and change management. Our team of Edgile and Wipro experts take a unique approach, ensuring successful cloud identity and security transformations for our clients.” |
| IB Solution | "IBsolution is one of the most experienced SAP Identity Management consultancies throughout the world with a track record of more than 20 years. With a strategic approach and pre-packaged solutions, the company accompanies customers in their transition away from SAP IdM to SAP’s most recommended IdM successor Microsoft Entra ID Governance." |
| IBM Consulting | "IBM Consulting is a global leader in Microsoft Security and SAP transformation services. We are well-positioned to support our clients’ SAP IdM migration to Microsoft Entra ID. Our knowledge and experience in supporting large global enterprise clients, combined with deep expertise in cybersecurity, AI, and SAP services, helps deliver a seamless transition journey with minimal disruption to critical business services and functions." |
| KPMG | "KPMG and Microsoft further strengthen their alliance by delivering a comprehensive identity governance proposition. By adeptly navigating the complexities of identity governance, the combination of Microsoft Entra advanced tools with KPMG Powered Enterprise helps drive functional transformation. This synergy can propel accelerated digital capabilities, enhance operational efficiency, fortify security and ensure compliance." |
| ObjektKultur | "As a long-standing Microsoft partner, Objektkultur digitizes business processes through consulting, development and operations of innovative IT solutions. With profound experience in implementing identity & access management solutions within Microsoft Technologies and integrating applications, we guide customers seamlessly from the phased-out SAP IDM to the robust Microsoft Entra, guaranteeing a secure, governed and streamlined identity & access management in the cloud." |
| Patecco | "PATECCO is a German IT consulting company specializing in development, support and implementation of Identity & Access Management solutions based on the latest technologies. With high expertise in IAM and partnerships with industry leaders, it offers tailored services to customers from various sectors including banking, insurance, pharma, energy, chemistry and utility." |
| Protiviti | "As a Microsoft AI Cloud Solutions Partner and an SAP Gold Partner, Protiviti’s expertise in Microsoft and SAP solutions is unmatched in the industry. Bringing together our powerful partnerships will provide our customers a set of comprehensive solutions for centralized identity management and role governance." |
| PwC | "PwC's identity and access management services can help across all capability phases, from helping to assess your existing capabilities deployed in SAP IDM and strategize and plan your target future state and vision with Microsoft Entra ID Governance. PwC can also support and operate the environment as a managed service after the go live." |
| SAP | "With extensive experience in the design and implementation of SAP IDM, our SAP Consulting Team offers comprehensive expertise in migrating from SAP IDM to Microsoft Entra. With strong and direct connections to SAP development, we can drive customer requirements and implement innovative ideas. Our experience in integrating with Microsoft Entra allows us to provide customized solutions. Furthermore, we have best practices in handling SAP Cloud Identity Services and integrating SAP with non-SAP cloud products. Trust in our expertise and let our SAP Consulting Team support you in migrating to Microsoft Entra ID." |
| SITS | "SITS, leading cybersecurity provider in the DACH region, supports customers with top-tier consulting, engineering, cloud technologies and managed services. As a Microsoft Solutions Partner for Security, Modern Work, and Azure Infrastructure, we offer our customers consulting, implementation, support, and managed services around security, compliance, identity, and privacy." |
| Traxion | "Traxion, part of the SITS group, operates in the BeNeLux region. Traxion is an IT-security company with 160 employees and over 24 years of expertise, we specialize in Identity Management solutions. As a Microsoft Partner, we provide top-tier IAM advisory, implementation, and support services, ensuring strong, long-lasting client relationships." |
| TrustSis | "TrustSis, a Microsoft and SAP Gold Partner based in Brazil, offers unmatched expertise in integrating Microsoft Entra and SAP solutions. Specializing in access management, security, internal control, risk mitigation, and segregation of duties (SoD), TrustSis ensures every migration is secure and efficient. With extensive experience in SAP IDM, TrustSis guarantees strategic transitions that maintain operational excellence while fortifying security measures." |
Migration guidance for each SAP IDM scenario
The following sections provide links to guidance on how to migrate each SAP IDM scenario to Microsoft Entra. Not all the sections may be relevant to each organization, depending upon the SAP IDM scenarios an organization has deployed.
Be sure to monitor this article, the Microsoft Entra product documentation, and corresponding SAP product documentation, for updates, as capabilities of both products continue to evolve to unblock more migration and net new scenarios, including Microsoft Entra integrations with SAP Access Control (SAP AC) and SAP Cloud Identity Access Governance (SAP IAG).
| SAP IDM scenario | Guidance for Microsoft Entra |
|---|---|
| SAP IDM Identity Store | Migrate an Identity Store to a Microsoft Entra ID tenant and Migrate existing IAM data into Microsoft Entra ID tenant |
| User management in SAP IDM | Migrate user management scenarios |
| SAP SuccessFactors and other HR sources | Integrate with SAP HR sources |
| Provisioning identities for single-sign on in applications | Provision to SAP systems, Provision to non-SAP systems and Migrate authentication and single sign-on |
| End user self-service | Migrate end user self-service |
| Role assignment and access assignment | Migrate access lifecycle management scenarios |
| Reporting | Use Microsoft Entra for reporting |
| Identity federation | Migrate exchanging identity information across organizational boundaries |
| Directory server | Migrate applications requiring directory services |
| Extensions | Extend Microsoft Entra through integration interfaces |
Migrate an Identity Store to a Microsoft Entra ID tenant
In SAP IDM, an Identity Store is a repository of identity information, including users, groups, and their audit trail. In Microsoft Entra, a tenant is an instance of Microsoft Entra ID in which information about a single organization resides including organizational objects such as users, groups, and devices. A tenant also contains access and compliance policies for resources, such as applications registered in the directory. The primary functions served by a tenant include identity authentication as well as resource access management. Tenants contain privileged organizational data and are securely isolated from other tenants. In addition, tenants can be configured to have an organization's data persisted and processed in a specific region or cloud, which enables organizations to use tenants as a mechanism to meet data residency and handling compliance requirements.
Organizations that have Microsoft 365, Microsoft Azure, or other Microsoft Online Services will already have a Microsoft Entra ID tenant that underlies those services. In addition, an organization may have additional tenants, such as a tenant that has specific applications and that has been configured to meet standards such as PCI-DSS applicable to those applications. For more information on determining whether an existing tenant is suitable, see resource isolation with multiple tenants. If your organization does not have yet a tenant, review the Microsoft Entra deployment plans.
Before migrating scenarios to a Microsoft Entra tenant, you should review the step-by-step guidance to:
- Define the organization's policy with user prerequisites and other constraints for access to an application
- Decide on the provisioning and authentication topology. Similar to SAP IDM identity lifecycle management, a single Microsoft Entra ID tenant can connect to multiple cloud and on-premises applications for provisioning and single sign-on.
- Ensure organizational prerequisites are met in that tenant, including having the appropriate Microsoft Entra licenses in that tenant for the features you will be using.
Migrate existing IAM data into a Microsoft Entra ID tenant
In SAP IDM, the Identity Store represents identity data through entry types such as MX_PERSON, MX_ROLE, or MX_PRIVILEGE.
A person is represented in a Microsoft Entra ID tenant as a User. If you have existing users who are not yet in Microsoft Entra ID, you can bring them into Microsoft Entra ID. First, if you have attributes on the existing users which are not part of the Microsoft Entra ID schema, then extend the Microsoft Entra user schema with extension attributes for the additional attributes. Next, perform an upload to bulk create the users in Microsoft Entra ID from a source, such as a CSV file. Then, issue credentials to those new users so they can authenticate to Microsoft Entra ID.
A business role can be represented in Microsoft Entra ID Governance as an Entitlement Management access package. You can govern access to applications by migrating an organizational role model to Microsoft Entra ID Governance, which results in an access package for each business role. To automate the migration process, you can use PowerShell to create access packages.
A privilege or technical role in a target system could be represented in Microsoft Entra as either an app role or as a security group, depending upon the target system's requirements for how it uses Microsoft Entra ID data for authorization. For more information, see integrating applications with Microsoft Entra ID and establishing a baseline of reviewed access.
A dynamic group has separate possible representations in Microsoft Entra. In Microsoft Entra, you can automatically maintain collections of users, such as everyone with a particular value of a cost center attribute, using either Microsoft Entra ID dynamic membership groups or Microsoft Entra ID Governance entitlement management with access package automatic assignment policies. You can use PowerShell cmdlets to create dynamic membership groups or create automatic assignment policies in bulk.
Migrate user management scenarios
Through the Microsoft Entra admin center, Microsoft Graph API and PowerShell, administrators can easily perform day-to-day identity management activities, including creating a user, blocking a user from sign in, adding a user to a group, or deleting a user.
To enable operation at scale, Microsoft Entra enables organizations to automate their identity lifecycle processes.
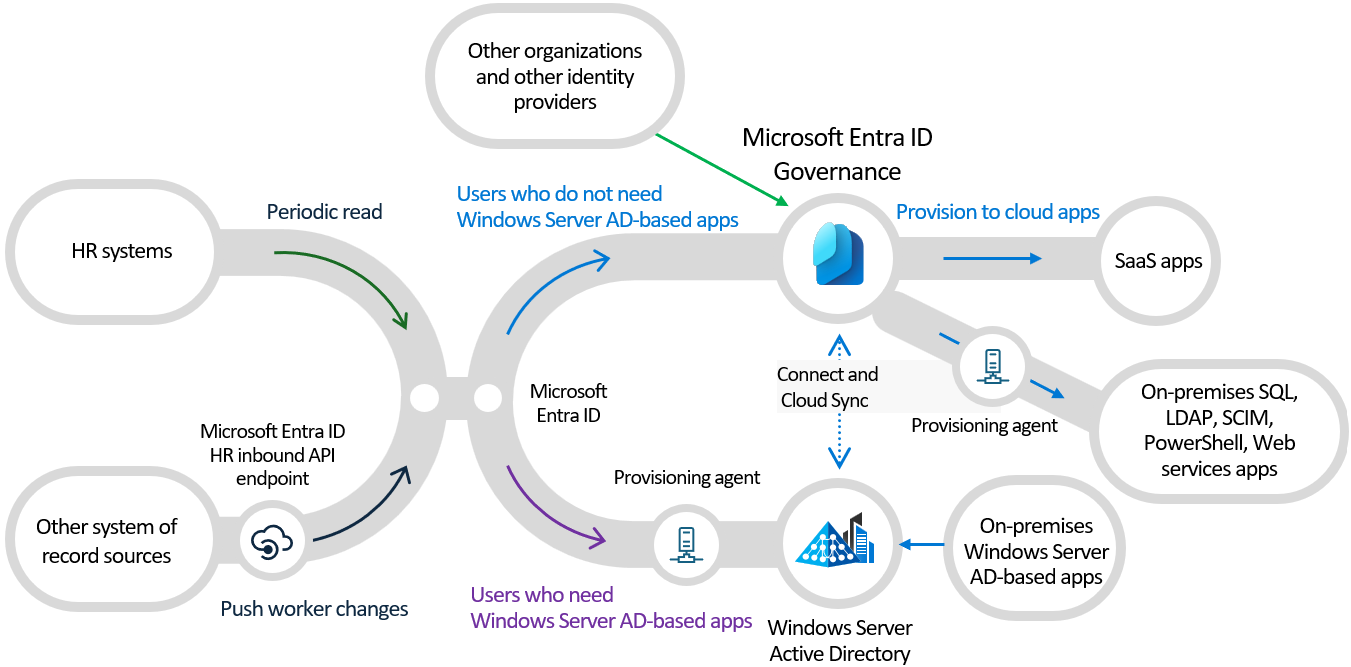
In Microsoft Entra ID and Microsoft Entra ID Governance, you can automate identity lifecycle processes using:
- Inbound provisioning from your organization's HR sources, retrieves worker information from Workday and SuccessFactors, to automatically maintain user identities in both Active Directory and Microsoft Entra ID.
- Users already present in Active Directory can be automatically created and maintained in Microsoft Entra ID using inter-directory provisioning.
- Microsoft Entra ID Governance lifecycle workflows automate workflow tasks that run at certain key events, such before a new employee is scheduled to start work at the organization, as they change status during their time in the organization, and as they leave the organization. For example, a workflow can be configured to send an email with a temporary access pass to a new user's manager, or a welcome email to the user, on their first day.
- Automatic assignment policies in entitlement management to add and remove a user's dynamic membership group, application roles, and SharePoint site roles, based on changes to the user's attributes. Users can also upon request, be assigned to groups, Teams, Microsoft Entra roles, Azure resource roles, and SharePoint Online sites, using entitlement management and Privileged Identity Management, as shown in the access lifecycle management section.
- Once the users are in Microsoft Entra ID with the correct dynamic membership group and app role assignments, user provisioning can create, update, and remove user accounts in other applications, with connectors to hundreds of cloud and on-premises applications via SCIM, LDAP and SQL.
- For guest lifecycle, you can specify in entitlement management the other organizations whose users are allowed to request access to your organization's resources. When one of those users's request is approved, entitlement management automatically adds them as a B2B guest to your organization's directory, and assigns appropriate access. And entitlement management automatically removes the B2B guest user from your organization's directory when their access rights expire or are revoked.
- Access reviews automates recurring reviews of existing guests already in your organization's directory, and removes those users from your organization's directory when they no longer need access.
When migrating from another IAM product, keep in mind that the implementations of IAM concepts in Microsoft Entra may be different from the implementations of those concepts in other IAM products. For example, organizations may express a business process for lifecycle events such as new employee onboarding, and some IAM products had implemented that through a workflow in a workflow foundation. By contrast, Microsoft Entra has many automation procedures built in, and doesn't require workflows to be defined for most identity management automation activities. For example, Microsoft Entra can be configured that when a new worker is detected in an HR system of record such as SuccessFactors, Microsoft Entra automatically creates user accounts for that new worker in Windows Server AD, Microsoft Entra ID, provisions them to applications, adds them to groups and assigns them appropriate licenses. Similarly, access request approval processing doesn't require a workflow to be defined. In Microsoft Entra, workflows are only required for the following situations:
- Workflows can be used in the Join/Move/Leave process for a worker, available with Microsoft Entra lifecycle workflows built-in tasks. For example, an administrator can define a workflow with a task for sending an email with a Temporary Access Pass for a new worker. An administrator can also add callouts from lifecycle workflows to Azure Logic Apps during Join, Move, and Leave workflows.
- Workflows can be used for adding steps in the access request and access assignment process. Steps for multi-stage approval, separation of duties checks, and expiration are already implemented in Microsoft Entra entitlement management. An administrator can define callouts from entitlement management during access package assignment request processing, assignment granting, and assignment removal to Azure Logic Apps workflows.
Integrate with SAP HR sources
Organizations that have SAP SuccessFactors could use SAP IDM to bring in employee data from SAP SUccessFactors. Those organizations with SAP SuccessFactors can easily migrate to bring identities for employees from SuccessFactors into Microsoft Entra ID or from SuccessFactors into on-premises Active Directory, by using Microsoft Entra ID connectors. The connectors support the following scenarios:
- Hiring new employees: When a new employee is added to SuccessFactors, a user account is automatically created in Microsoft Entra ID and optionally Microsoft 365 and other software as a service (SaaS) applications that Microsoft Entra ID supports.
- Employee attribute and profile updates: When an employee record is updated in SuccessFactors (such as name, title, or manager), the employee's user account is automatically updated in Microsoft Entra ID and optionally Microsoft 365 and other SaaS applications that Microsoft Entra ID supports.
- Employee terminations: When an employee is terminated in SuccessFactors, the employee's user account is automatically disabled in Microsoft Entra ID and optionally Microsoft 365 and other SaaS applications that Microsoft Entra ID supports.
- Employee rehires: When an employee is rehired in SuccessFactors, the employee's old account can be automatically reactivated or reprovisioned (depending on your preference) to Microsoft Entra ID and optionally Microsoft 365 and other SaaS applications that Microsoft Entra ID supports.
You can also write back from Microsoft Entra ID to SAP SuccessFactors properties such as email address.
For step-by-step guidance on the identity lifecycle with SAP SuccessFactors as a source, including setting up new users with appropriate credentials in Windows Server AD or Microsoft Entra ID, see Plan deploying Microsoft Entra for user provisioning with SAP source and target applications.
Some organizations also used SAP IDM to read from SAP Human Capital Management (HCM). Organizations that use both SAP SuccessFactors and SAP Human Capital Management (HCM) can also bring identities into Microsoft Entra ID. By using SAP Integration Suite, you can synchronize lists of workers between SAP HCM and SAP SuccessFactors. From there, you can bring identities directly into Microsoft Entra ID or provision them into Active Directory Domain Services by using the native provisioning integrations mentioned earlier.
If you have other systems of record sources besides SuccessFactors or SAP HCM, you can use the Microsoft Entra inbound provisioning API to bring in workers from that system of record as users in Windows Server or Microsoft Entra ID.
Provision to SAP systems
Most organizations with SAP IDM will have used it to provision users into SAP ECC, SAP IAS, SAP S/4HANA, or other SAP applications. Microsoft Entra has connectors to SAP ECC, SAP Cloud Identity Services, and SAP SuccessFactors. Provisioning into SAP S/4HANA or other applications requires the users to first be present in Microsoft Entra ID. Once you have users in Microsoft Entra ID, you can provision those users from Microsoft Entra ID to SAP Cloud Identity Services or SAP ECC, to enable them to sign in to SAP applications. SAP Cloud Identity Services then provisions the users originating from Microsoft Entra ID that are in the SAP Cloud Identity Directory into the downstream SAP applications, including SAP S/4HANA Cloud, SAP S/4HANA On-premise through the SAP cloud connector, AS ABAP, and others.
For step-by-step guidance on the identity lifecycle with SAP applications as the target, see Plan deploying Microsoft Entra for user provisioning with SAP source and target applications.
To prepare for provisioning users into SAP applications integrated with SAP Cloud Identity Services, confirm the SAP Cloud Identity Services have the necessary schema mappings for those applications, and provision the users from Microsoft Entra ID to SAP Cloud Identity Services. SAP Cloud Identity Services will subsequently provision users into the downstream SAP applications as necessary. You can then use HR inbound from SuccessFactors to keep the list of users in Microsoft Entra ID up to date as employees join, move, and leave. If your tenant has a license for Microsoft Entra ID Governance, you can also automate changes to the application role assignments in Microsoft Entra ID for SAP Cloud Identity Services. For more information on performing separation of duties and other compliance checks prior to provisioning, see migrate access lifecycle management scenarios.
For guidance on how to provision users into SAP ECC, confirm that the necessary Business APIs (BAPIs) for SAP ECC are ready for Microsoft Entra to use for identity management, then provision the users from Microsoft Entra ID to SAP ECC.
For guidance on how to update the SAP SuccessFactor worker record, see write back from Microsoft Entra ID to SAP SuccessFactors.
If you are using SAP NetWeaver AS for Java with Windows Server Active Directory as its data source, then Microsoft Entra SuccessFactors inbound can be used to automatically create and update users in Windows Server AD.
If you are using SAP NetWeaver AS for Java with another LDAP directory as its data source, then you can configure Microsoft Entra ID to provision users into LDAP directories.
After you configure provisioning for users into your SAP applications, you should enable Single sign-on for them. Microsoft Entra ID can serve as the identity provider and authentication authority for your SAP applications. Microsoft Entra ID can integrate with SAP NetWeaver using SAML or OAuth. For more information on how to configure single sign-on to SAP SaaS and modern apps, see enable SSO.
Provision to non-SAP systems
Organizations may also be using SAP IDM to provision users to non-SAP systems, including Windows Server AD, and other databases, directories, and applications. You can migrate these scenarios to Microsoft Entra ID to have Microsoft Entra ID provision its copy of those users into those repositories.
For organizations with Windows Server AD, the organization may have been using Windows Server AD as a source for users and groups for SAP IDM to bring into SAP R/3. You can use Microsoft Entra Connect Sync or Microsoft Entra Cloud Sync to bring users and groups from Windows Server AD into Microsoft Entra ID. In addition, Microsoft Entra SuccessFactors inbound can be used to automatically create and update users in Windows Server AD, and you can manage the memberships of groups in AD used by AD-based applications. Exchange Online mailboxes can be created automatically for users via a license assignment, using group-based licensing.
For organizations with applications relying on other directories, you can configure Microsoft Entra ID to provision users into LDAP directories, including OpenLDAP, Microsoft Active Directory Lightweight Directory Services, 389 Directory Server, Apache Directory Server, IBM Tivoli DS, Isode Directory, NetIQ eDirectory, Novell eDirectory, Open DJ, Open DS, Oracle (previously Sun ONE) Directory Server Enterprise Edition, and RadiantOne Virtual Directory Server (VDS). You can map the attributes of the users in Microsoft Entra ID to the attributes of the user in those directories, and set an initial password if required.
For organizations with applications relying upon a SQL database, you can configure Microsoft Entra ID to provision users into a SQL database via the database's ODBC driver. Supported databases include Microsoft SQL Server, Azure SQL, IBM DB2 9.x, IBM DB2 10.x, IBM DB2 11.5, Oracle 10g and 11g, Oracle 12c and 18c, MySQL 5.x, MySQL 8.x, and Postgres. You can map the attributes of the users in Microsoft Entra ID to the table columns, or stored procedure parameters, for those databases. For SAP HANA, see SAP Cloud Identity Services SAP HANA Database Connector (beta).
If there are existing users in a non-AD directory or database that were provisioned by SAP IDM and are not already in Microsoft Entra ID and can't be correlated to a worker in SAP SuccessFactors or other HR source, see govern an application's existing users for guidance on how to bring those users into Microsoft Entra ID.
Microsoft Entra has built-in provisioning integrations with hundreds of SaaS applications; for a complete list of applications that support provisioning see Microsoft Entra ID Governance integrations. Microsoft partners also deliver partner-driven integrations with additional specialized applications.
For other in-house developed applications, Microsoft Entra can provision to cloud applications via SCIM, and to on-premises applications via SCIM, SOAP or REST, PowerShell, or partner-delivered connectors that implement the ECMA API. If you had previously been using SPML for provisioning from SAP IDM, we recommend updating applications to support the newer SCIM protocol.
For applications with no provisioning interface, consider using the Microsoft Entra ID Governance feature to automate ServiceNow ticket creation to assign a ticket to an application owner when a user is assigned or loses access to an access package.
Migrate authentication and single sign-on
Microsoft Entra ID acts as a security token service, enabling users to authenticate to Microsoft Entra ID with multi-factor and passwordless authentication, and then have single sign-on to all their applications. Microsoft Entra ID single sign-on uses standard protocols including SAML, OpenID Connect and Kerberos. For more information on single sign-on to SAP cloud applications or applications on SAP BTP, see Microsoft Entra single sign-on integration with SAP Cloud Identity Services.
Organizations that have an existing identity provider, such as Windows Server AD, for their users can configure hybrid identity authentication, so that Microsoft Entra ID relies upon an existing identity provider. For more information on integration patterns, see choose the right authentication method for your Microsoft Entra hybrid identity solution.
If you have on-premises SAP systems, then you can modernize how your organization's users connect to those systems with the Global Secure Access Client of Microsoft Entra Private Access. Remote workers don't need to use a VPN to access these resources if they have the Global Secure Access Client installed. The client quietly and seamlessly connects them to the resources they need. For more information, see Microsoft Entra Private Access.
Migrate end user self-service
Organizations may have used SAP IDM Logon Help to enable their end users to reset their Windows Server AD password.
Microsoft Entra self-service password reset (SSPR) gives users the ability to change or reset their password, without needing administrator or help desk involvement. Once you configure Microsoft Entra SSPR, you can require users to register when they sign in. Then, if a user's account is locked or they forget their password, they can follow prompts to unblock themselves and get back to work. When users change or reset their passwords using SSPR in the cloud, the updated passwords can also be written back to an on-premises AD DS environment. For more information on how SSPR works, see Microsoft Entra self-service password reset. If you need to send password changes to other on-premises systems in addition to Microsoft Entra ID and Windows Server AD, you can do this using a tool like the Password Change Notification Service (PCNS) with Microsoft Identity Manager (MIM). To find information on this scenario, see the article Deploy the MIM Password Change Notification Service.
Microsoft Entra also supports end user self-service for group management, and self-service access requests, approval, and reviews. For more information on self-service access management through Microsoft Entra ID Governance, see the following section on access lifecycle management.
Migrate access lifecycle management scenarios
Organizations may have integrated SAP IDM with SAP AC, formerly SAP GRC, or SAP IAG for access approvals, risk assessments, separation of duties checks and other operations.
Microsoft Entra includes multiple access lifecycle management technologies to enable organizations to bring their identity and access management scenarios to the cloud. The choice of technologies depends upon your organization's application requirements and Microsoft Entra licenses.
Access management through Microsoft Entra ID security group management. Traditional Windows Server AD-based applications relied upon checking membership of security groups for authorization. Microsoft Entra makes dynamic membership group available to applications via SAML claims, provisioning, or by writing groups to Windows Server AD. You can manage access to SAP BTP applications using group memberships sent as claims in OpenID Connect to SAP Cloud Identity Services. SAP Cloud Identity Services can also read groups from Microsoft Entra ID via Graph, and provision those groups to other SAP applications.
In Microsoft Entra, administrators can manage dynamic membership groups, create access reviews of dynamic membership group, and enable self-service group management. With self-service, the group owners can approve or deny membership requests and delegate control of dynamic membership groups. You can also use Privileged Identity Management (PIM) for groups to manage just-in-time membership in the group or just-in-time ownership of the group.
Access management through Entitlement management access packages.. Entitlement management is an identity governance feature that enables organizations to manage identity and access lifecycle at scale, by automating access request and approval workflows, access assignments, reviews, and expiration. Entitlement management can be used for fine-grained access assignments to applications that use groups, application role assignments, or that have connectors for Azure Logic Apps.
Entitlement management enables organizations to implement their practices for how users are assigned access across multiple resources, using standardized collection of access rights called access packages. Each access package grants membership to groups, assignment to application roles, or membership in SharePoint Online sites. Access packages can be used to represent business roles, which incorporate technical roles or privileges across one or more applications. You can configure entitlement management so that users receive access package assignments automatically based on user properties such as their department or cost center. You can also configure lifecycle workflows to add or remove assignments when people join and leave. Administrators can also request that users have assignments to access packages, and users can also request to have an access package themselves. The access packages available for a user to request are determined by the security dynamic membership group of the user. Users can request access they need immediately or request access in the future, can specify a time limit of hours or days, and can include answers to questions or provide values for additional attributes. A request can be configured for auto-approval, or go through multiple stages of approval by a manager, role owner, or other approvers, with escalation approvers in case an approver is unavailable or does not respond. Once approved, requestors are notified that they have been assigned access. Assignments to an access package can be time limited, and you can configure recurring access reviews to have a manager, resource owner, or other approvers regularly recertify or reattest the user's need for continued access. For more information on how to migrate authorization policies represented in a role model to entitlement management, see migrate an organizational role model. To automate the migration process, you can use PowerShell to create access packages.
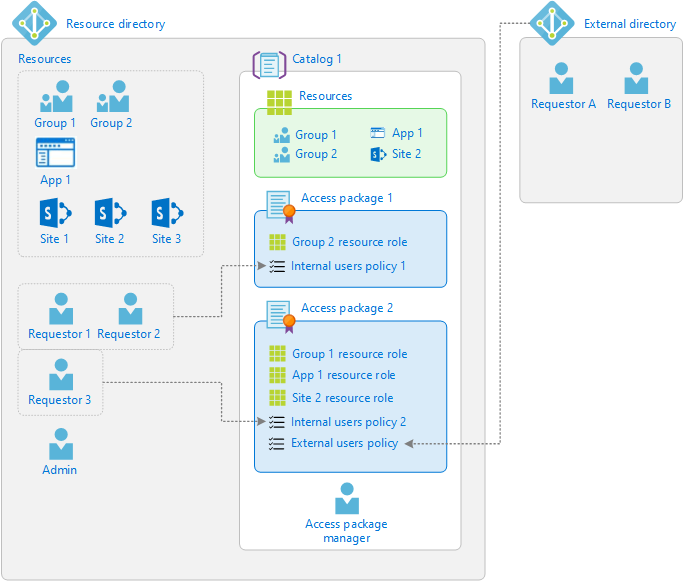
Access management through Entitlement management and an external GRC product. With Microsoft Entra integrations to SAP access governance, to Pathlock and to other partner products, customers can take advantage of additional risk and fine-grained separation-of-duties checks enforced in those products, with access packages in Microsoft Entra ID Governance.
Use Microsoft Entra for reporting
Microsoft Entra includes built-in reports, as well as workbooks that surface in Azure Monitor based on audit, sign-in, and provisioning log data. The reporting options available in Microsoft Entra include:
- Microsoft Entra built-in reports in the admin center, including usage and insights reports for an application-centric view on sign-in data. You can use those reports to monitor for unusual account creation and deletion, and unusual account usage.
- You can export data from Microsoft Entra admin center for use in generating your own reports. For example, you can download a list of users and their attributes or download logs, including the provisioning logs, from the Microsoft Entra admin center.
- You can query Microsoft Graph to obtain data for use in a report. For example, you can retrieve a list of inactive user accounts in Microsoft Entra ID.
- You can use the PowerShell cmdlets atop Microsoft Graph APIs to export and restructure content suitable for reporting. For example, if you are using Microsoft Entra entitlement management access packages, you can retrieve a list of assignments to an access package in PowerShell.
- You can export collections of objects, such as users or groups, from Microsoft Entra to Azure Data Explorer. For more information, see customized reports in Azure Data Explorer (ADX) using data from Microsoft Entra ID.
- You can get alerts, and use workbooks, custom queries and reports on audit, sign-in, and provisioning logs that have been sent to Azure Monitor. For example, you can Archive logs and report on entitlement management in Azure Monitor from the Microsoft Entra admin center or using PowerShell. The audit logs include details on who created and changed objects in Microsoft Entra. Azure Monitor also provides options for longer term data retention.
Migrate exchanging identity information across organizational boundaries
Some organizations may be using SAP IDM identity federation to exchange identity information about users across company boundaries.
Microsoft Entra includes capabilities for a multitenant organization, that more than one Microsoft Entra ID tenant, to bring together users from one tenant for application access or collaboration in another tenant. The following diagram shows how you can use the multitenant organization cross-tenant synchronization feature to automatically enable users from one tenant to have access to applications in another tenant in your organization.
Microsoft Entra External ID includes B2B collaboration capabilities that allow your workforce to work securely with business partner organizations and guests, and share your company's applications with them. Guest users sign in to your apps and services with their own work, school, or social identities. For business partner organizations that have their own Microsoft Entra ID tenant where their users authenticate, you can configure cross-tenant access settings. And for those business partner organizations that do not have a Microsoft Entra tenant but instead have their own identity providers, you can configure federation with SAML/WS-Fed identity providers for guest users. Microsoft Entra entitlement management enables you to govern the identity and access lifecycle for those external users, by configuring access package with approvals before a guest can be brought into a tenant, and automatic removal of guests when they are denied ongoing access during an access review.
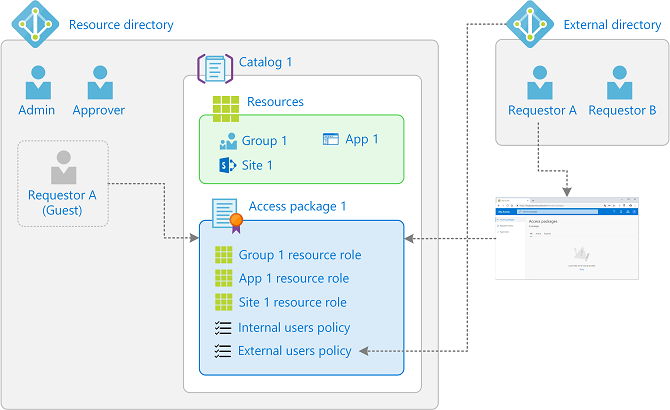
Migrate applications requiring directory services
Some organizations may be using SAP IDM as a directory service, for applications to call into to read and write identities. Microsoft Entra ID provides a directory service for modern applications, enabling applications to call via the Microsoft Graph API to query and update users, groups and other identity information.
For applications that still require an LDAP interface to read users or groups, Microsoft Entra provides several options:
Microsoft Entra Domain Services provides identity services to applications and VMs in the cloud, and is compatible with a traditional AD DS environment for operations such as domain join and secure LDAP. Domain Services replicates identity information from Microsoft Entra ID, so it works with Microsoft Entra tenants that are cloud-only, or those synchronized with an on-premises AD DS environment.
If you are using Microsoft Entra to populate workers from SuccessFactors into on-premises Active Directory, then the applications can read users from that Windows Server Active Directory. If your applications also require dynamic membership group, then you can populate Windows Server AD groups from corresponding groups in Microsoft Entra. For more information, see Group writeback with Microsoft Entra Cloud Sync.
If your organization has been using another LDAP directory, then you can configure Microsoft Entra ID to provision users into that LDAP directory.
Extend Microsoft Entra through integration interfaces
Microsoft Entra includes multiple interfaces for integration and extension across its services, including:
- Applications can call Microsoft Entra via the Microsoft Graph API to query and update identity information, configuration and policies, and retrieve logs, status, and reports.
- Administrators can configure provision to applications via SCIM, SOAP or REST, and the ECMA API.
- Administrators can use the inbound provisioning API to bring in worker records from other system of record sources to supply user updates to Windows Server AD and Microsoft Entra ID.
- Administrators in a tenant with Microsoft Entra ID Governance can also configure calls to custom Azure Logic Apps from entitlement management and lifecycle workflows. These allow customization of the user onboarding, offboarding, and access request and assignment processes.
Next steps
- Plan deploying Microsoft Entra for user identity provisioning with SAP source and target applications
- Manage access to your SAP applications
- Guidance for migrating from ADFS
- Guidance for migrating from MIM
- Deploy SAP NetWeaver AS ABAP 7.51
- Author SAP ECC 7 Template for ECMA2Host
- Configuring Microsoft Entra ID to provision users into SAP ECC with NetWeaver AS ABAP 7.0 or later