Azure Synapse Analytics IP firewall rules
This article will explain IP firewall rules and teach you how to configure them in Azure Synapse Analytics.
IP firewall rules
IP firewall rules grant or deny access to your Azure Synapse workspace based on the originating IP address of each request. You can configure IP firewall rules for your workspace. IP firewall rules configured at the workspace level apply to all public endpoints of the workspace (dedicated SQL pools, serverless SQL pool, and development). The maximum number of IP firewall rules is limited to 128. If you have the Allow Azure Services and resources to access this server setting enabled, this counts as a single firewall rule for the workspace.
Create and manage IP firewall rules
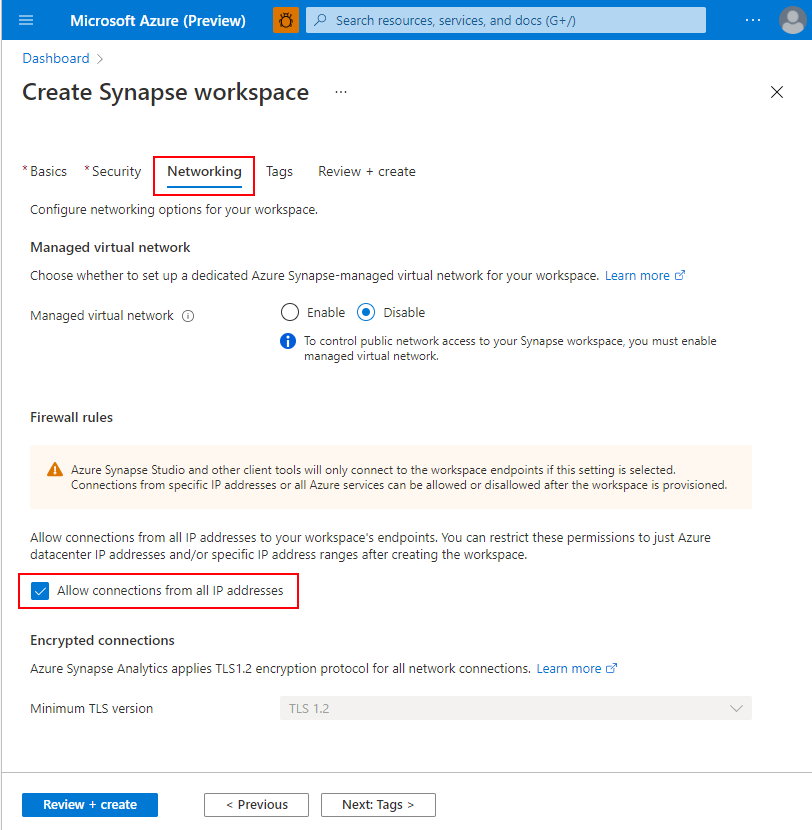
There are two ways IP firewall rules are added to an Azure Synapse workspace. To add an IP firewall to your workspace, select Networking and check Allow connections from all IP addresses during workspace creation.
Important
This feature is only available to Azure Synapse workspaces not associated with a Managed Virtual Network.
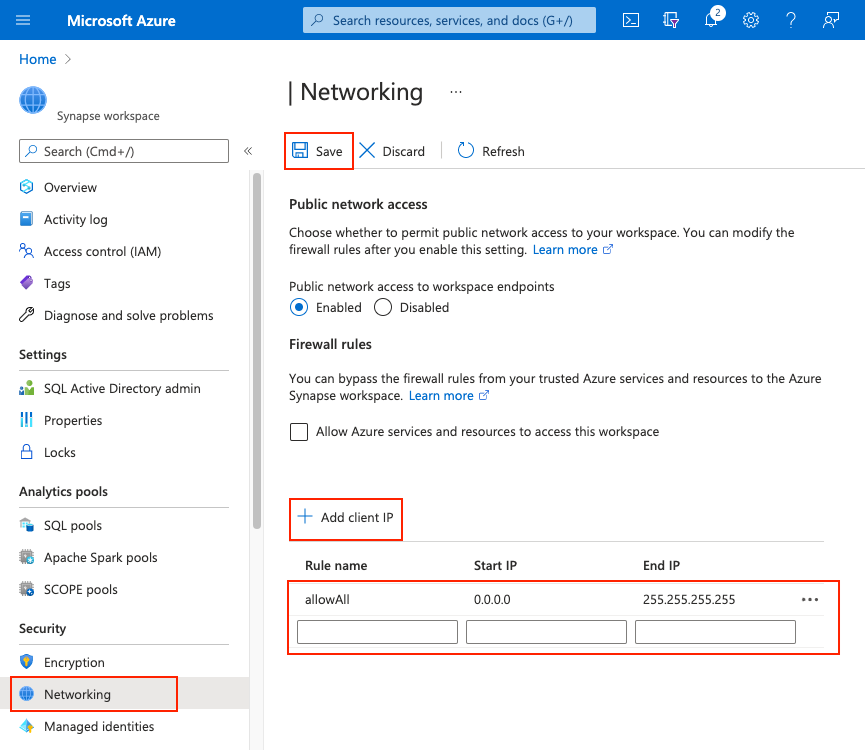
You can also add IP firewall rules to a Synapse workspace after the workspace is created. Select Firewalls under Security from Azure portal. To add a new IP firewall rule, give it a name, Start IP, and End IP. Select Save when done.
Note
The Public network access feature is only available to Azure Synapse workspaces associated with Azure Synapse Analytics Managed Virtual Network. However, you can still open your Azure Synapse workspaces to the public network regardless of its association with managed virtual network. For more information, see Public network access.
Connect to Azure Synapse from your own network
You can connect to your Synapse workspace using Synapse Studio. You can also use SQL Server Management Studio (SSMS) to connect to the SQL resources (dedicated SQL pools and serverless SQL pool) in your workspace.
Make sure that the firewall on your network and local computer allows outgoing communication on TCP ports 80, 443 and 1443. These ports are used by Synapse Studio.
To connect using tools such as SSMS and Power BI, you must allow outgoing communication on TCP port 1433. The 1433 port used by SSMS (Desktop Application).
Note
Azure Policy operates at a level above other Azure services by applying policy rules against PUT requests and GET responses of resource types exchanged between Azure Resource Manager and the owning resource provider (RP). However, updates to Synapse workspace firewall settings in the Azure Portal are made using POST calls, such as the replaceAllIpFirewallRules operation.
Due to this design, Azure Policy definitions cannot block changes to networking settings made via POST operations. As a result, modifications to firewall rules through the Azure Portal may bypass Azure Policy, even if restrictive policies are in place.
Manage the Azure Synapse workspace firewall
For more information on managing the firewall, see the Azure SQL documentation to manage server-level firewalls. Azure Synapse only supports server-level IP firewall rules. It doesn't support database-level IP firewall rules.
For more information on the methods to manage the firewall programmatically, see:
Related content
- Create an Azure Synapse Workspace
- Create an Azure Synapse workspace with a Managed workspace Virtual Network
- Troubleshoot Azure Private Link connectivity problems
- Troubleshoot Azure Private Endpoint connectivity problems