Kubernetes node malware detection
Defender for Containers uses the Microsoft Defender Antivirus anti-malware engine to scan and detect malicious files in Kubernetes nodes. When threats are detected, security alerts are directed into Defender for Cloud and Defender XDR, where they can be investigated and remediated.
Prerequisites
Malware detection in Kubernetes nodes must be enabled by turning on the Agentless scanning for machines option in the Defender for Containers or Defender for Servers P2 plan.
Note
Malware detection is not performed on Kubernetes nodes if agentless scanning for machines is enabled through the Defender Cloud Security Posture Management Plan. Agentless scanning for machines must be enabled through Defender for Containers or Defender for Servers P2 plan.
Review and remediate the Kubernetes node malware security alerts
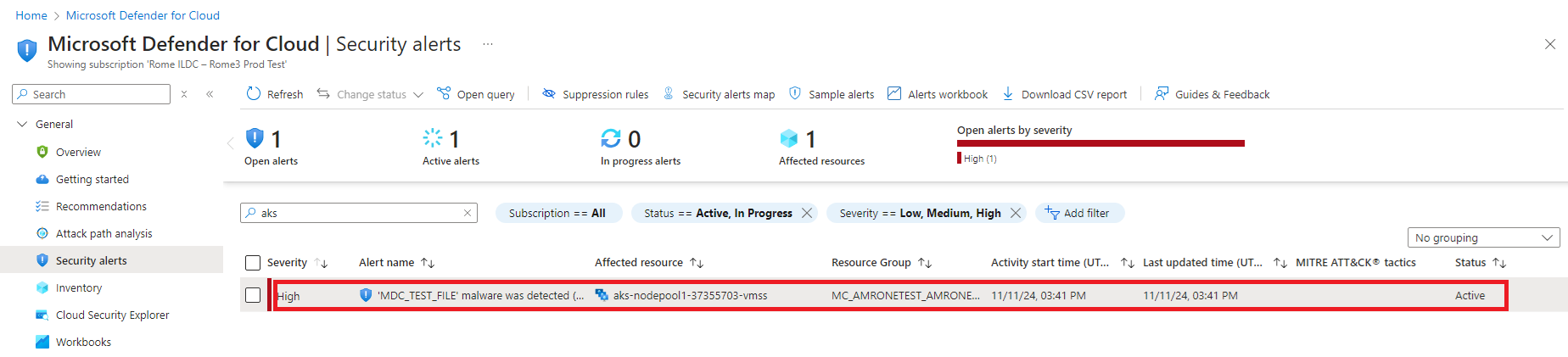
If malware is found in Kubernetes nodes, a malware security alert is generated for the customer to review. To review a Kubernetes node malware security alert in the Azure portal:
Select Security Alerts from the Defender for Cloud menu and select the line of the malware security alert for the Kubernetes node to the description.
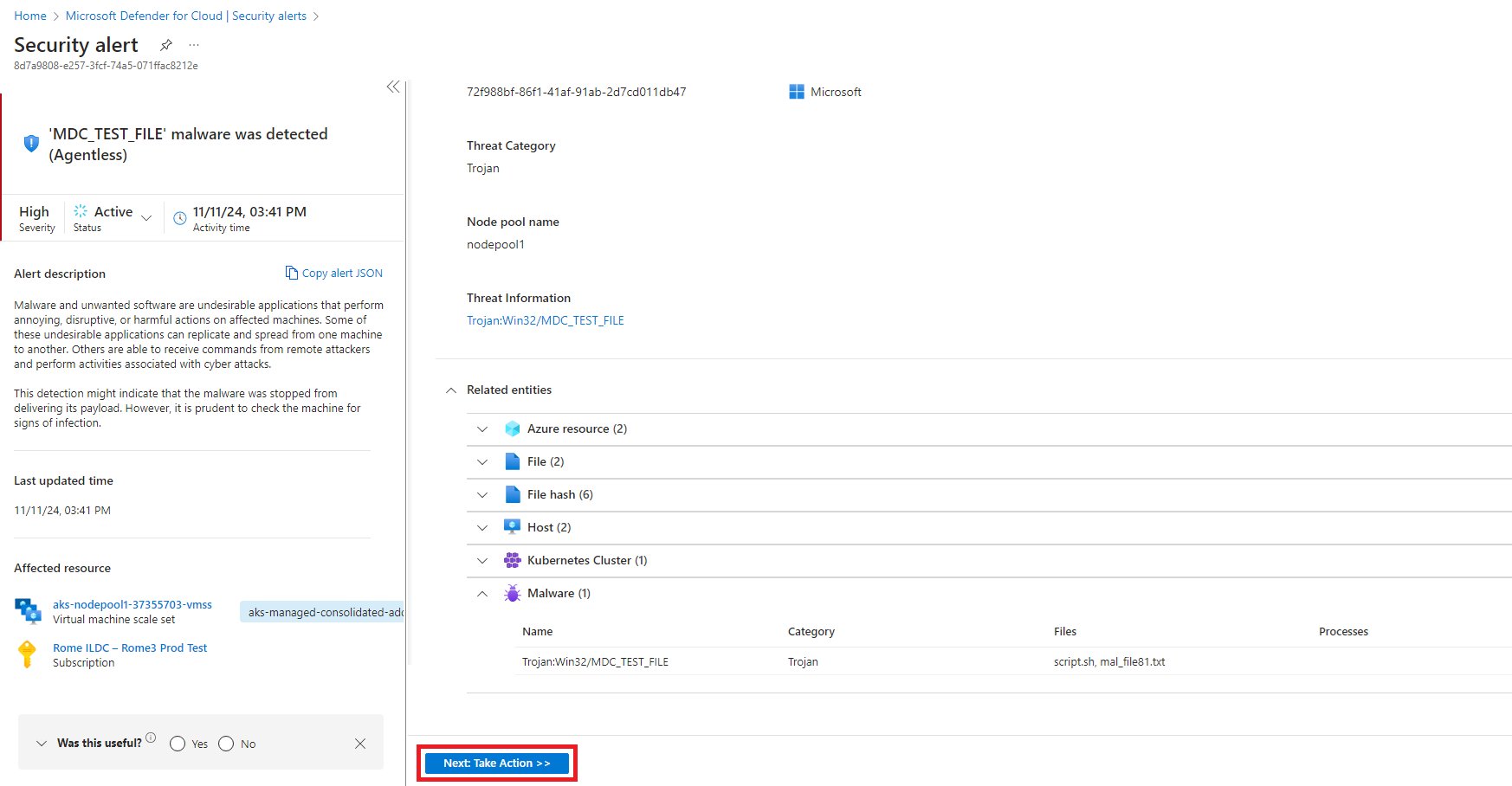
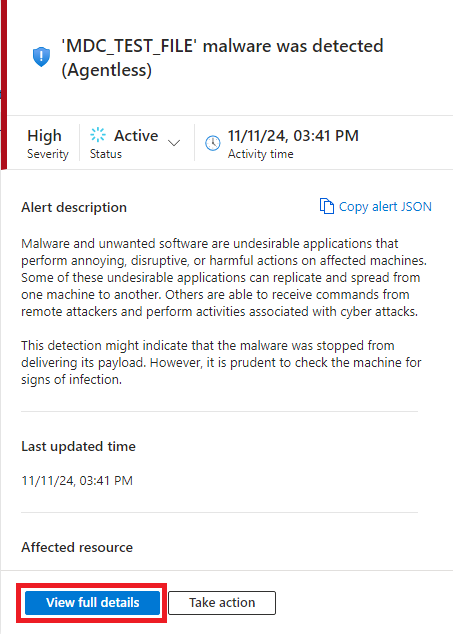
Select the View full details button to open the pane showing the full details of the malware found.
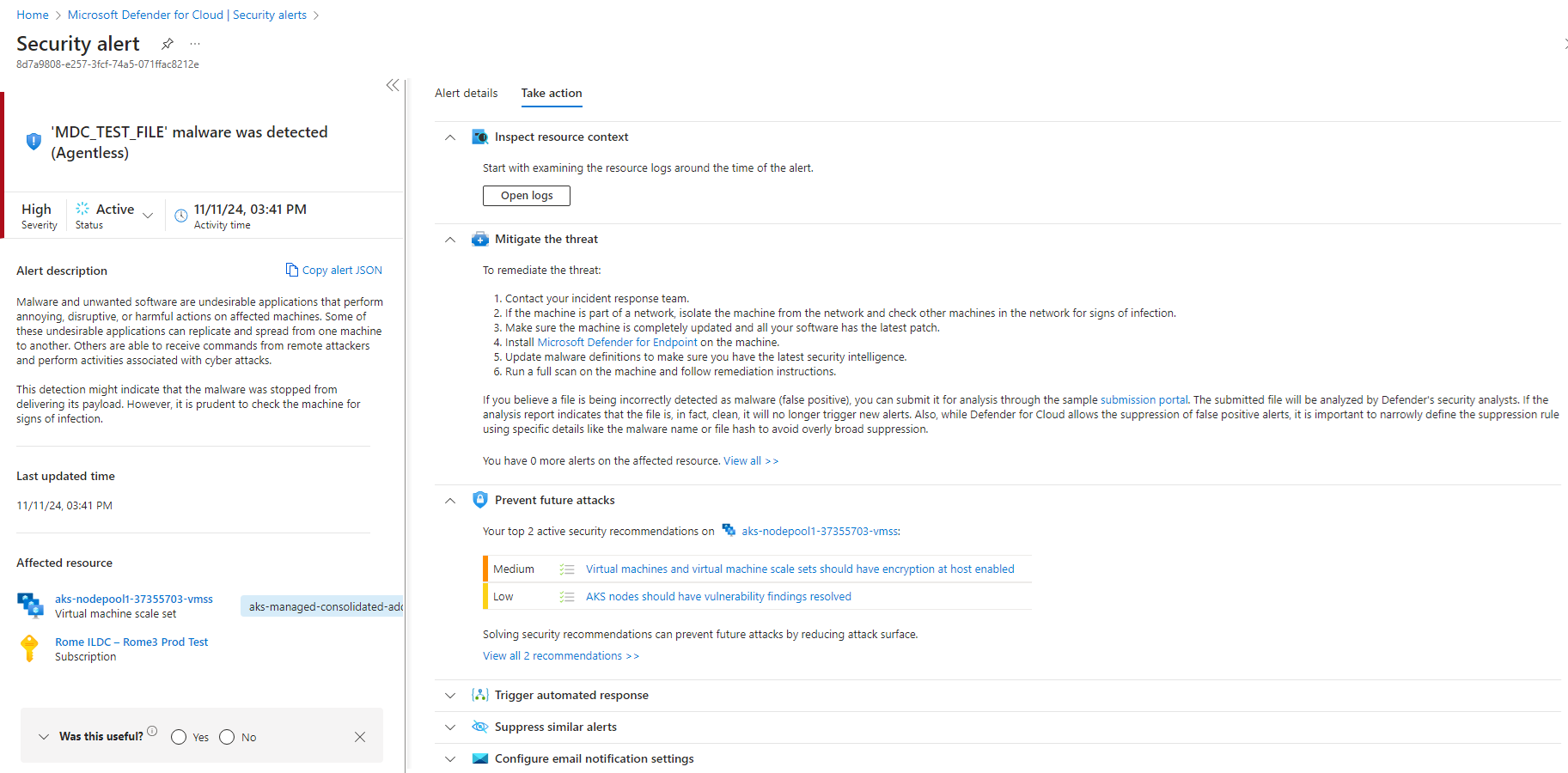
The security alert details describe the malware found, including the affected node pools and malware files found. Select the Next: Take Action button to view the instructions to remediate the threat.