Review changes in file integrity monitoring
In Defender for Servers Plan 2 in Microsoft Defender for Cloud, the file integrity monitoring feature helps keeps enterprise assets and resources secure by scanning and analyzing files, and comparing their current state with previous scans.
File integrity monitoring uses the Microsoft Defender for Endpoint agent to collect data from machines, in accordance with collection rules. Defender for Endpoint is integrated by default with Defender for Cloud.
Note
The older method of data collection uses the Log Analytics agent (also known as the Microsoft Monitoring agent (MMA)). Support for using the MMA will end in November 2024.
This article shows you how to review file changes.
Prerequisites
- Defender for Servers Plan 2 must be enabled.
- File integrity monitoring with the Defender for Endpoint agent must be enabled. If it isn't enabled this message appears - File Integrity Monitoring is not enabled. To enable select Onboard subscriptions, and then enable the feature.
Monitor entities and files
To monitor entities and files, follow these steps:
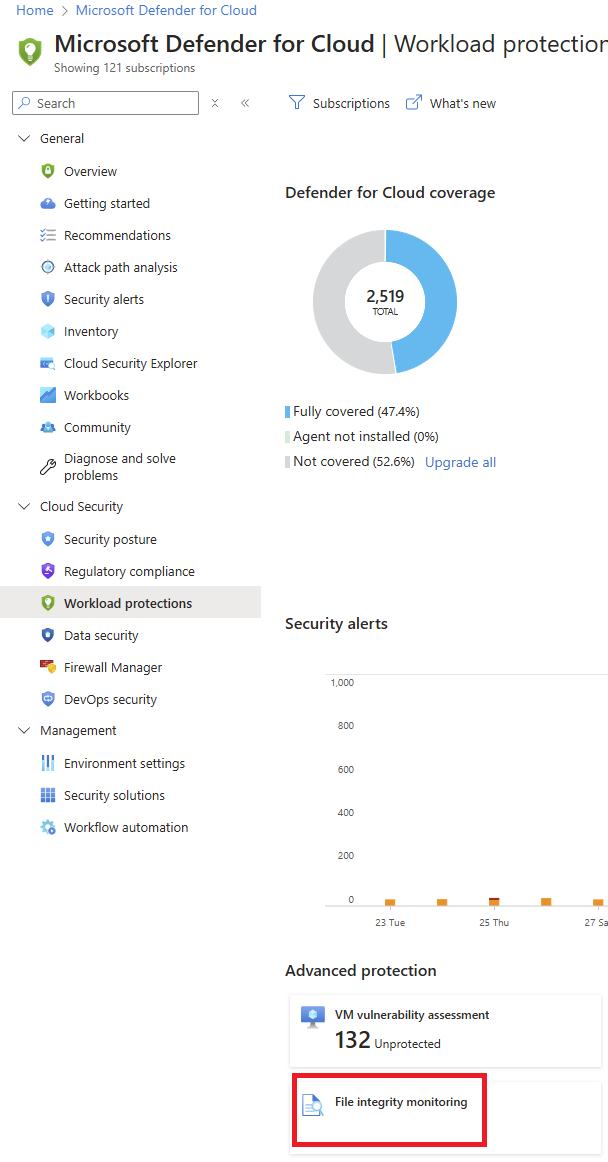
From Defender for Cloud's sidebar, go to Workload protections > File integrity monitoring.
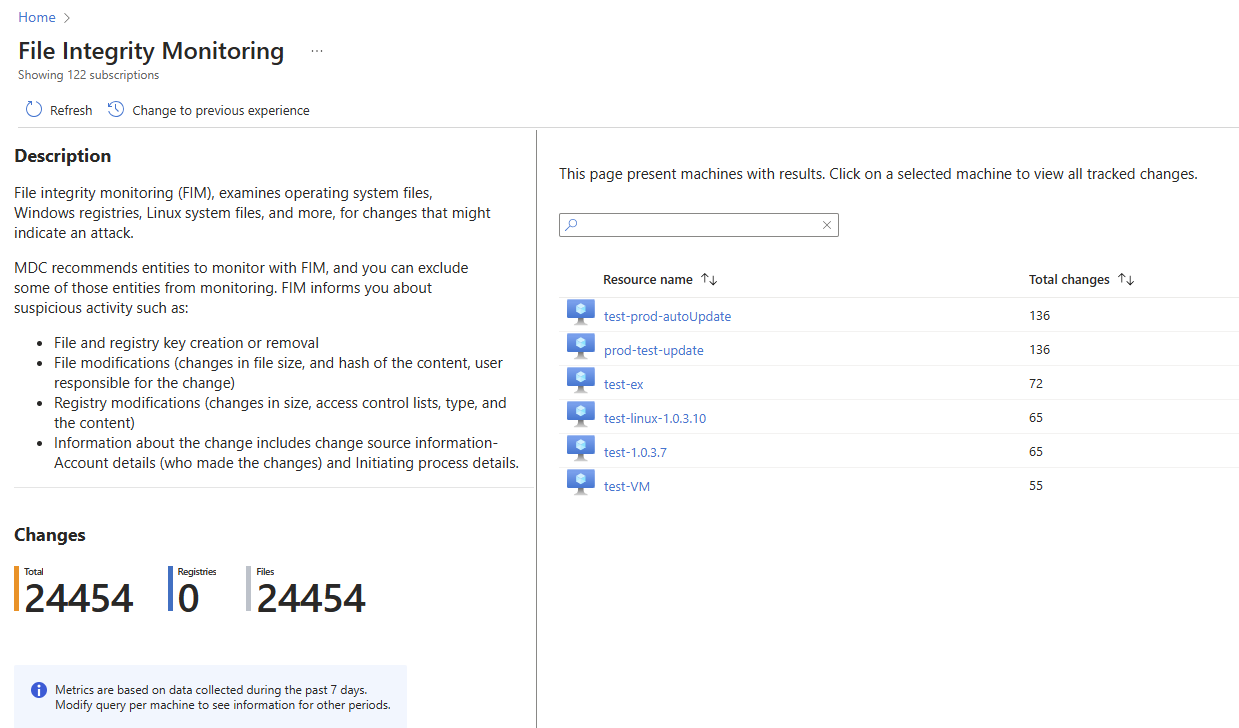
A window opens with all resources that contain tracked changed files and registries.
If you select a resource, a window opens with a query showing the changes made to the tracked files and registries on that resource.
If you select the subscription of the resource (under the column Subscription name), a query opens with all the tracked files and registries in that subscription.
Note
If you previously used File Integrity Monitoring over MMA, you can return to that method by selecting Change to previous experience. This will be available until the FIM over MMA feature is deprecated. For information on the deprecation plan, see Prepare for retirement of the Log Analytics agent.
Retrieve and analyze file integrity monitoring data
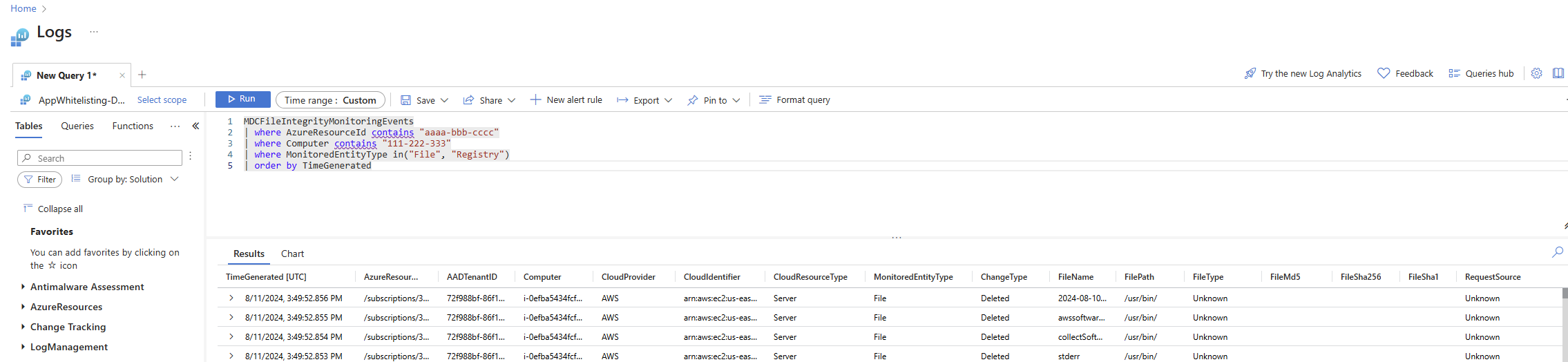
The file integrity monitoring data resides within the Azure Log Analytics workspace in the MDCFileIntegrityMonitoringEvents table.
Set a time range to retrieve a summary of changes by resource. In the following example, we retrieve all changes in the last 14 days in the categories of registry and files:
MDCFileIntegrityMonitoringEvents | where TimeGenerated > ago(14d) | where ConfigChangeType in ('Registry', 'Files') | summarize count() by Computer, ConfigChangeTypeTo view detailed information about registry changes:
Remove
Filesfrom thewhereclause.Replace the summarization line with an ordering clause:
MDCFileIntegrityMonitoringEvents | where TimeGenerated > ago(14d) | where ConfigChangeType == 'Registry' | order by Computer, RegistryKeyThe reports can be exported to CSV for archival purposes and channeled to a Power BI report for further analysis.