Remediate Defender for Endpoint misconfigurations (agentless)
Microsoft Defender for Cloud integrates natively with Defender for Endpoint to provide endpoint detection and response (EDR) capabilities for machines connected to Defender for Cloud.
As part of these integrated EDR capabilities, Defender for Cloud agentlessly scans machines to assess whether they're running an EDR solution. In addition, for machines using Defender for Endpoint as an EDR, Defender for Servers agentlessly scans the machines with security checks that assess whether Defender for Endpoint is configured correctly. Checks include:
Both full and quick scans are out of 7 daysSignature out of dateAnti-virus is off or partially configured
When misconfigurations are found, Defender for Cloud makes recommendations to fix them. This article describes how to remediate those recommendations.
Note
- Defender for Cloud uses agentless scanning to assess EDR settings.
- Agentless scanning replaces the Log Analytics agent (also known as the Microsoft Monitoring Agent (MMA)), which was previously used to collect machine data.
- The MMA is set to retire. Scanning using the MMA will be deprecated in November 2024.
Prerequisites
| Requirement | Details |
|---|---|
| Plan | Defender for Cloud must be available in the Azure subscription and one of these plans must be enabled: - Defender for Servers Plan 2 - Defender Cloud Security Posture Management (CSPM) |
| Agentless scanning | Agentless scanning for machines must be turned on. It's enabled by default in the plans, but if you need to turn it on manually, follow these instructions. |
| Machines | Defender for Endpoint must be running as the EDR solution on VMs. |
Investigate misconfiguration recommendations
In Defender for Cloud > Recommendations.
Search for and select one of the following recommendations:
EDR configuration issues should be resolved on virtual machinesEDR configuration issues should be resolved on EC2sEDR configuration issues should be resolved on GCP virtual machines
Select each of the security checks to review the affected resources.
Expand the Affected resources section
Drill into the security check, and follow the remediation steps.
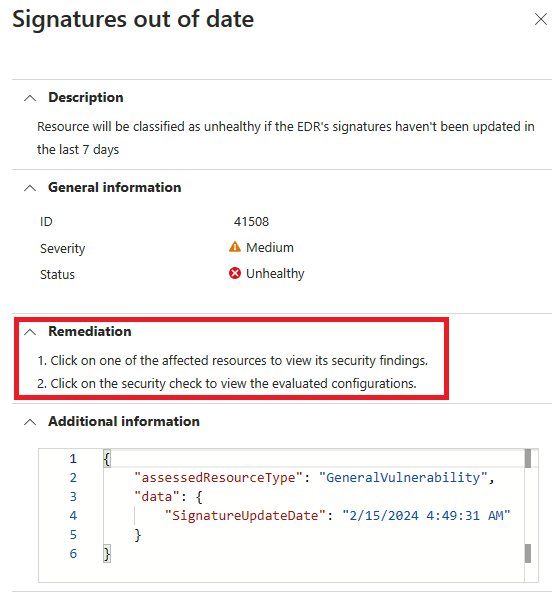
After the process is completed, it can take up to 24 hours until your machine appears in the Healthy resources tab.
Related content
Verify that machines have an EDR solution configured.


