Enable Defender for SQL Servers on Machines
The Defender for SQL Servers on Machines plan is one of the Defender for Databases plans in Microsoft Defender for Cloud. Use Defender for SQL Servers on Machines to protect SQL Server databases hosted on Azure VMs and Azure Arc-enabled VMs.
Prerequisites
| Requirement | Details |
|---|---|
| Permissions | To deploy the plan on a subscription including Azure Policy, you need Subscription Owner permissions. The Windows user on the SQL VM must have the Sysadmin role on the database. |
| Multicloud machines | Multicloud machines (AWS and GCP) must be onboarded as Azure Arc-enabled VMs. They can be automatically onboarded as Azure Arc machines when onboarded with the connector. Onboard your AWS connector and automatically provision Azure Arc. Onboard your GCP connector and automatically provision Azure Arc. |
| On-premises machines | On-premises machines must be onboarded as Azure Arc-enabled VMs. Onboard on-premises machines and install Azure Arc. |
| Azure Arc | Review Azure Arc deployment requirements - Plan and deploy Azure Arc-enabled servers - Connected Machine agent prerequisites - Connected Machine agent network requirements - Roles specific to SQL Server enabled by Azure Arc |
| Extensions | Ensure these extensions aren't blocked in your environment. |
| Defender for SQL (IaaS and Arc) | - Publisher: Microsoft.Azure.AzureDefenderForSQL - Type: AdvancedThreatProtection.Windows |
| SQL IaaS Extension (IaaS) | - Publisher: Microsoft.SqlServer.Management - Type: SqlIaaSAgent |
| SQL IaaS Extension (Arc) | - Publisher: Microsoft.AzureData - Type: WindowsAgent.SqlServer |
| AMA extension (IaaS and Arc) | - Publisher: Microsoft.Azure.Monitor - Type: AzureMonitorWindowsAgent |
| Region requirement | When you enable the plan, a resource group is created in the East US. Ensure this region isn't blocked in your environment. |
| Resource naming conventions | Defender for SQL uses the following naming convention when creating our resources: - Data Collection Rule: MicrosoftDefenderForSQL--dcr - DCRA: /Microsoft.Insights/MicrosoftDefenderForSQL-RulesAssociation - Resource group: DefaultResourceGroup- - Log analytics workspace: D4SQL-- - Defender for SQL uses MicrosoftDefenderForSQL as a createdBy database tag. Ensure that Deny policies don't block this naming convention. |
| Operating Systems | SQL Server 2012 R2 or later is supported for SQL instances. |
Enable the plan
In the Azure portal, search for and select Microsoft Defender for Cloud.
In the Defender for Cloud menu, select Environment settings.
Select the relevant subscription.
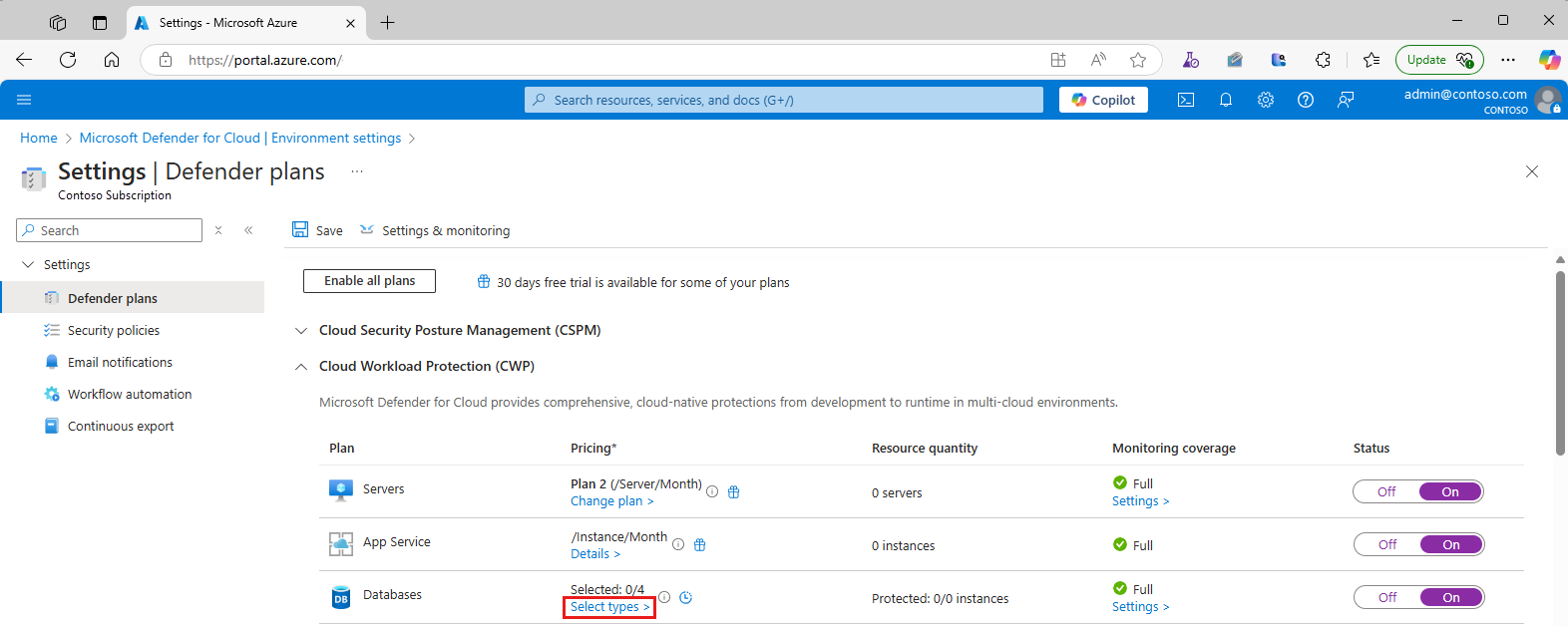
On the Defender plans page, locate the Databases plan and select Select types.
In the Resource types selection window, toggle the SQL Servers on Machines plan to On.
Select Continue > Save.
Select a workspace
Select a Log Analytics workspace to work with the Defender for SQL on Machines plan.
In the Defender plans page, in Databases, Monitoring Coverage column select Settings.
In the Azure Monitoring Agent for SQL Server on Machines section, in the Configurations column select Edit Configurations.
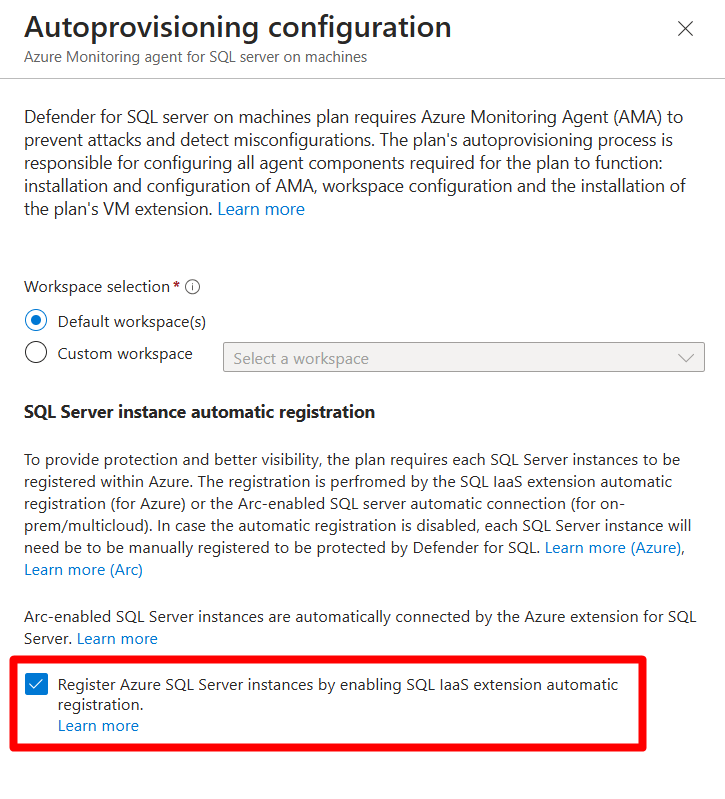
In the Autoprovisioning Configuration page, select the Default Workspace or specify a Custom Workspace.
In SQL Server automatic registration, make sure that you leave the Register Azure SQL Server instances by enabling SQL IaaS extension automatic registration option enabled.
Registration ensures that all SQL instances can be discovered and configured correctly.
Select Apply.
Verify that your machines are protected
Depending on your environment, it can take a few hours to discover and protect SQL instances. As a final step, you should verify that all machines are protected. Don't skip this step, as it's important to verify your deployment is protected.