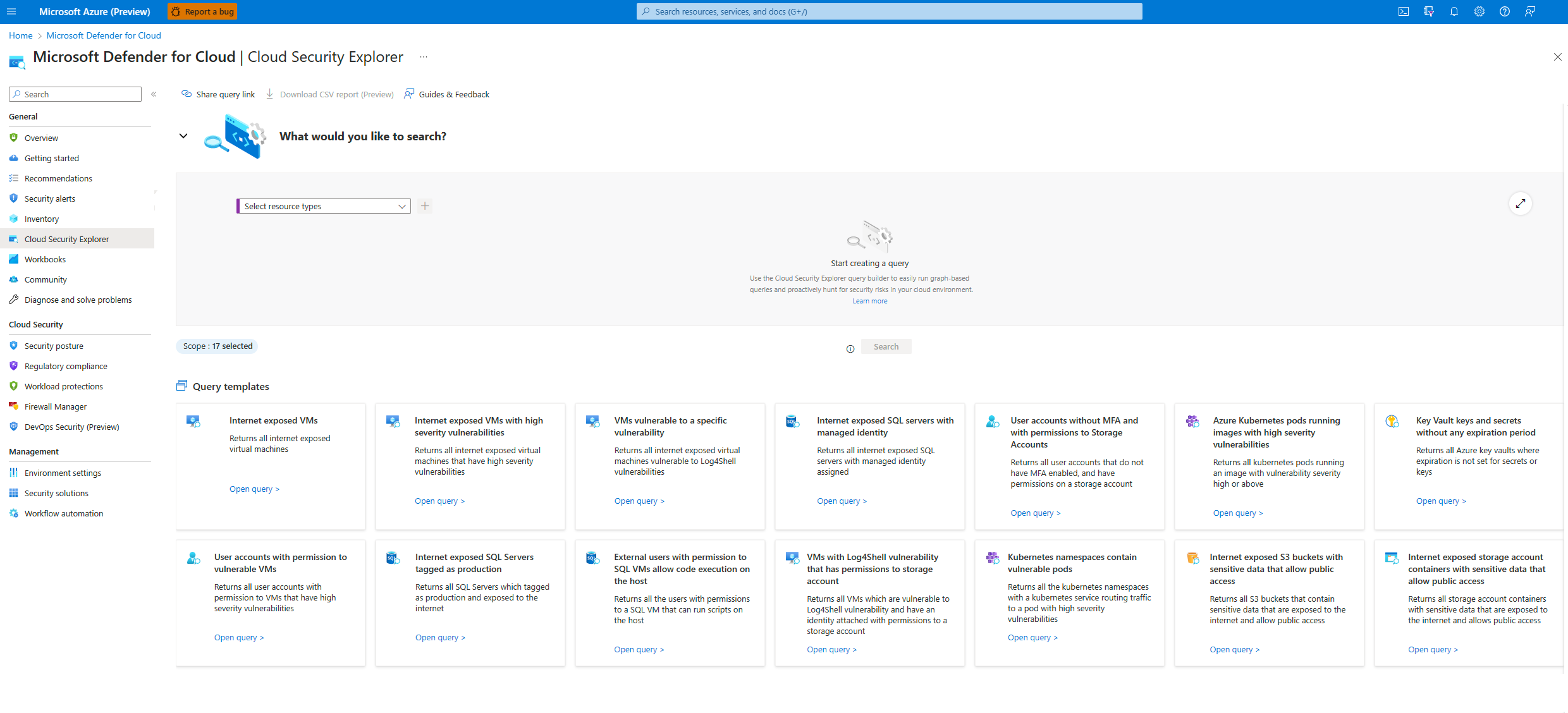
Build Cloud Security Explorer queries to identify vulnerabilities in Kubernetes clusters
You can use the Cloud Security Explorer to identify vulnerabilities in your Kubernetes clusters. The following examples demonstrate the building of queries that you can modify for your specific needs.
Read Build queries with Cloud Security Explorer for an introduction to Cloud Security Explorer queries.
Create a query to identify software vulnerabilities in container images
Sign in to the Azure portal.
Navigate to Microsoft Defender for Cloud > Cloud Security Explorer
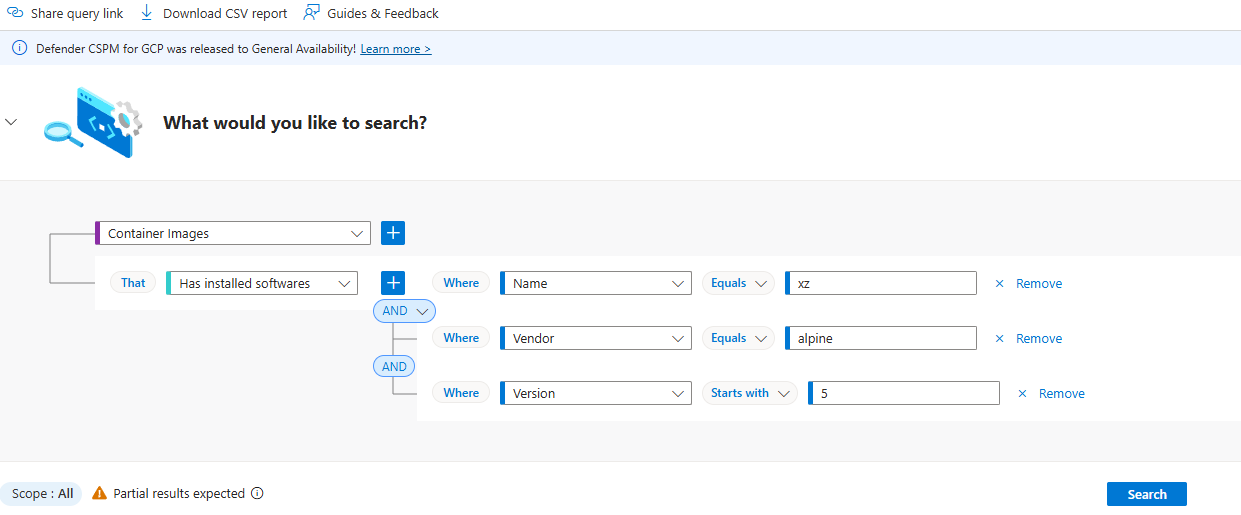
Filter on the software in the container images to query.
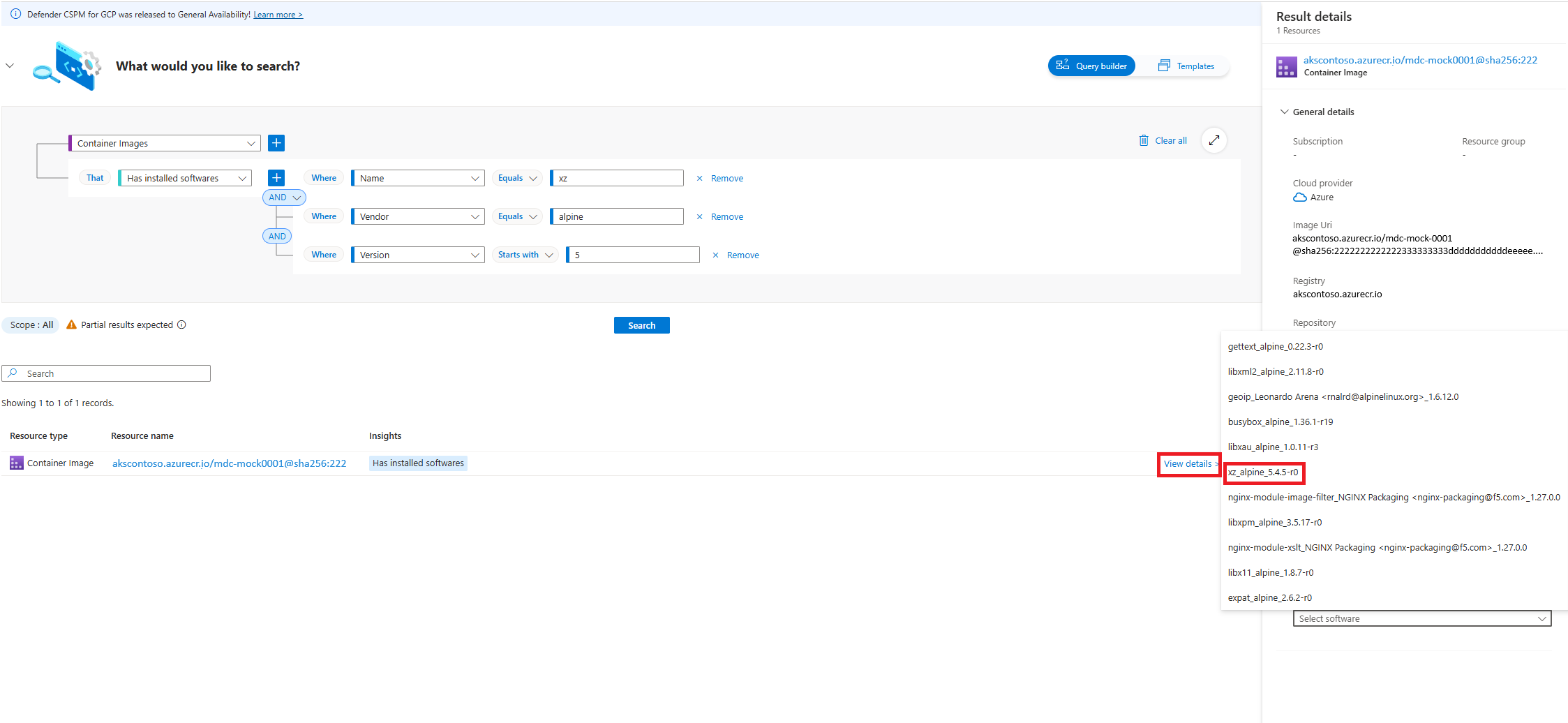
Select the View details link of the container image of interest to see the result details pane. In the Insights section of the Result details pane is a drop-drown list of the software installed on the container image. Select the installed software for review.
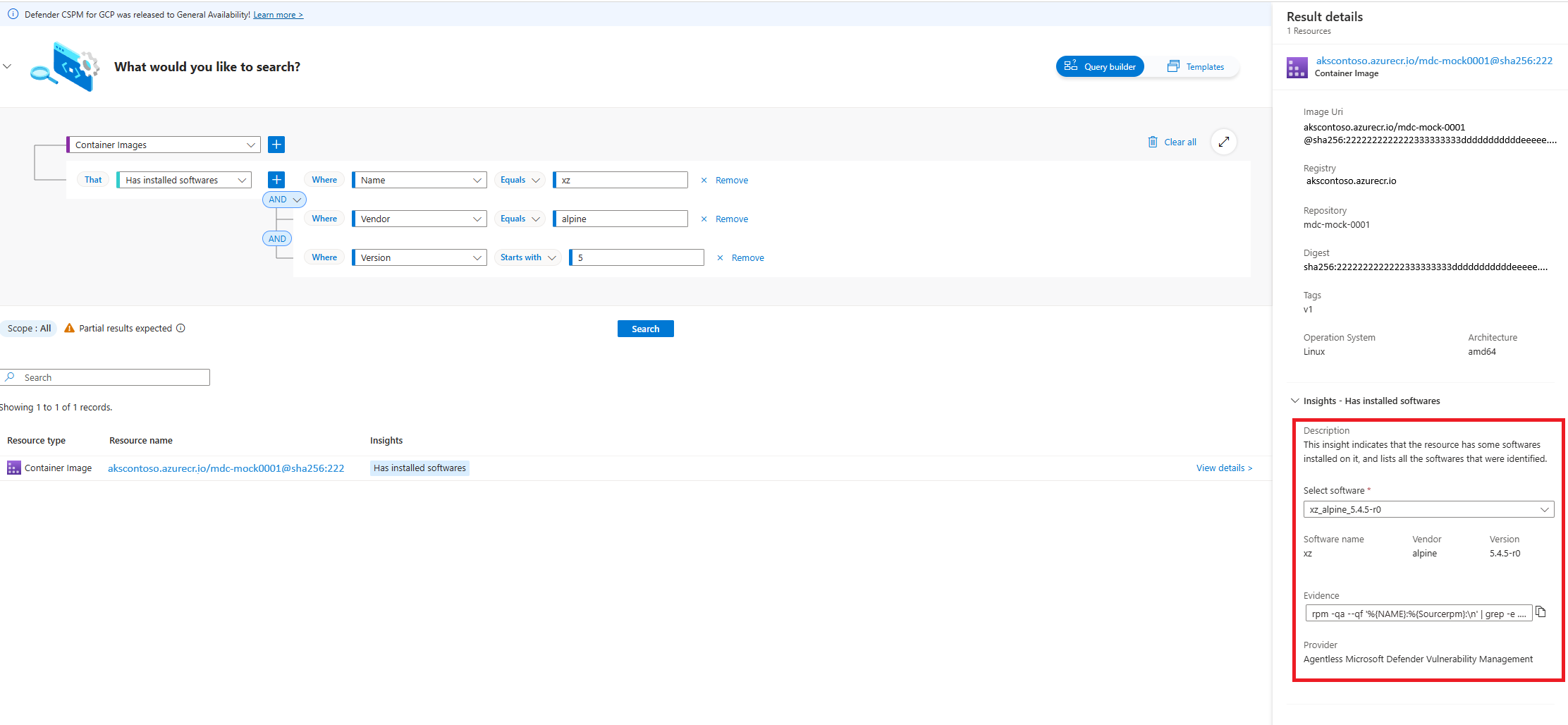
View the details of the installed software in the Insights section.
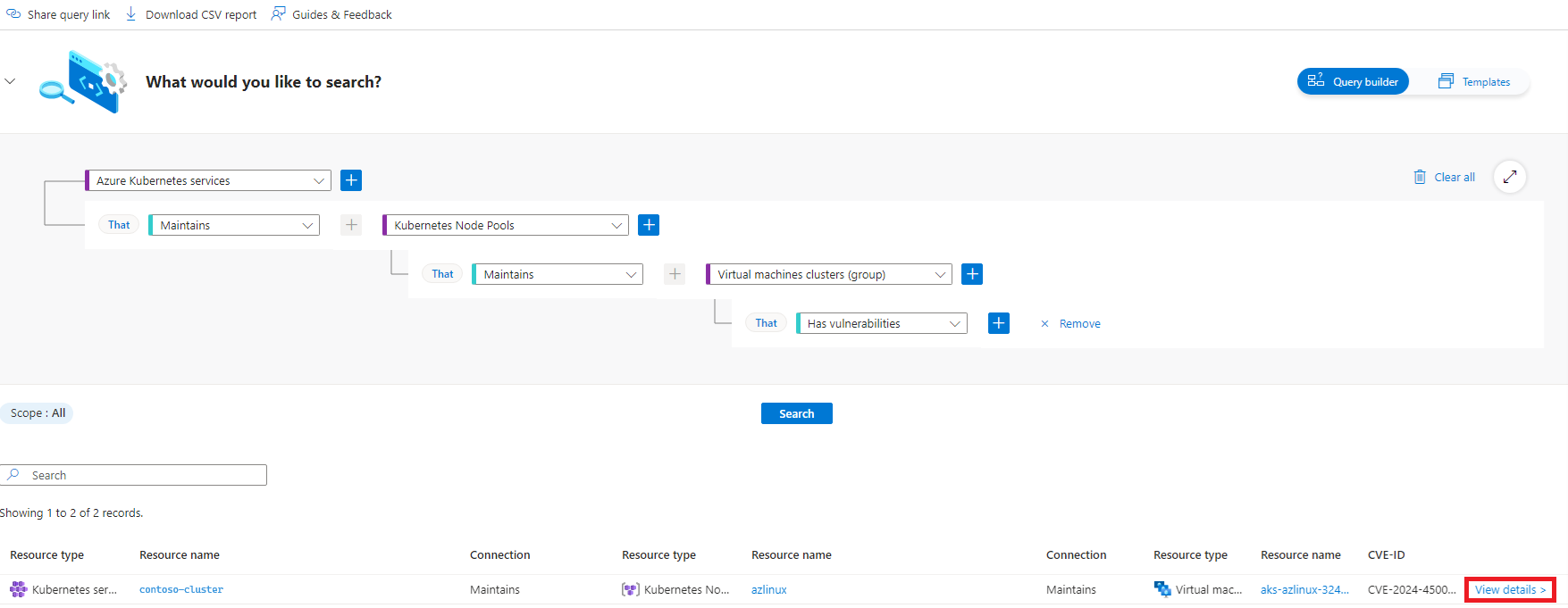
Create a query to identify vulnerabilities in cluster nodes
Sign in to the Azure portal.
Navigate to Microsoft Defender for Cloud > Cloud Security Explorer
Filter on the cluster nodes in the Azure Kubernetes Services environment to query.
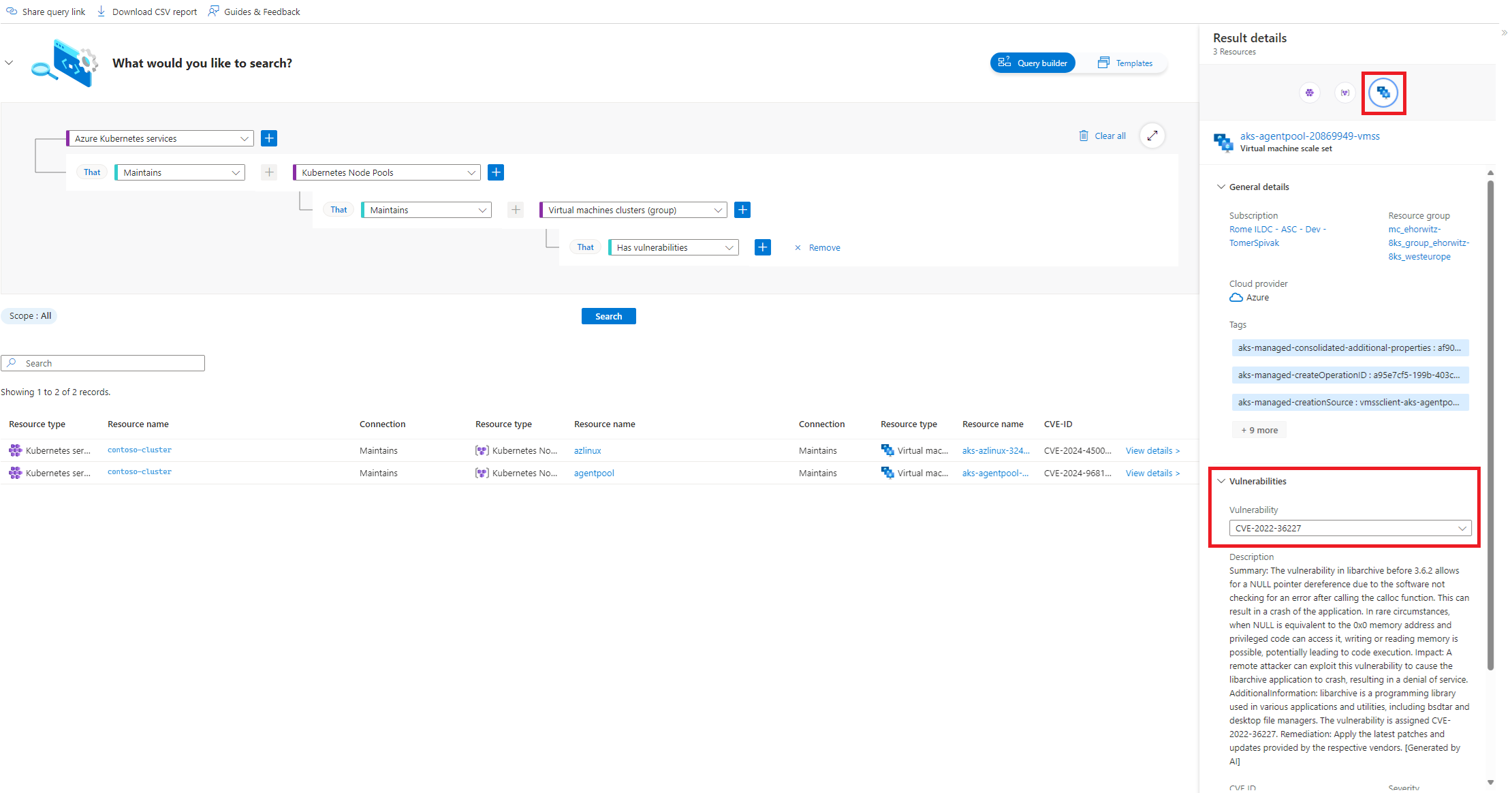
Select the View details link of the cluster node pool of interest to see the result details pane. In the Result details pane, select the virtual machine scale set icon, to see the vulnerabilities.