Manage public access on your Azure Cosmos DB for MongoDB vCore cluster
APPLIES TO:
MongoDB vCore
You can use cluster-level firewall rules to manage public access to an Azure Cosmos DB for MongoDB vCore cluster. Public access can be enabled from a specific IP address or a range of IP addresses on the public Internet.
Prerequisites
- An existing Azure Cosmos DB for MongoDB vCore cluster.
- If you don't have an Azure subscription, create an account for free.
- If you have an existing Azure subscription, create a new Azure Cosmos DB for MongoDB vCore cluster.
Enable public access during cluster creation in the Azure portal
Note
If no firewall rules are added to your Azure Cosmos DB for MongoDB vCore cluster, public network access to the cluster is disabled. If you don't add any firewall rules or private endpoints during cluster creation, your cluster is created in a locked-down state. To enable access to a locked-down cluster, you must add firewall rules for public access or create private endpoints for private access after the cluster is created.
To enable public access during cluster creation:
On the Networking tab, select Public access (allowed IP addresses) in the Connectivity method section to open the firewall rules creation controls.
To add firewall rules, in the Firewall rules section, type in the firewall rule name, start IP v4 address, and end IP v4 address.
- To allow a single IP address, enter the same address in both the Start IP address and End IP address fields.
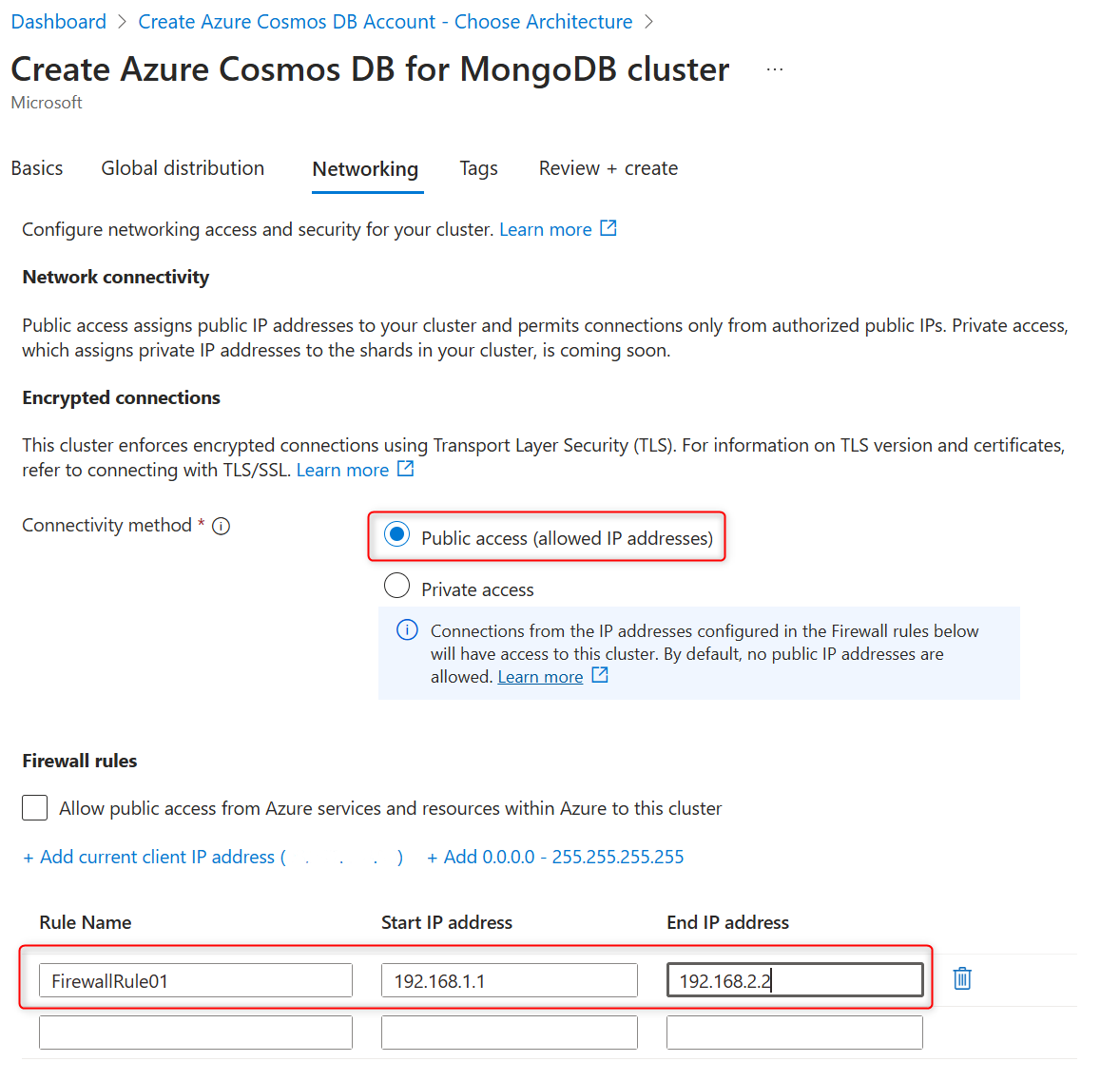
To quickly add your current public IP address (the address of the machine or device from which you’re accessing the Azure portal), select Add current client IP address.
Tip
Verify your IP address before saving the configuration. In some cases, the IP address detected by the Azure portal may differ from the IP address used when accessing the Internet. To check your actual IP address, use a search engine to find tools like what is my IP.
To allow cluster access from any IP address on the Internet, select Add 0.0.0.0 - 255.255.255.255. Even with this rule in place, users must authenticate with the correct username and password to access the cluster. However, it’s recommended to allow global access only temporarily and for non-production databases.
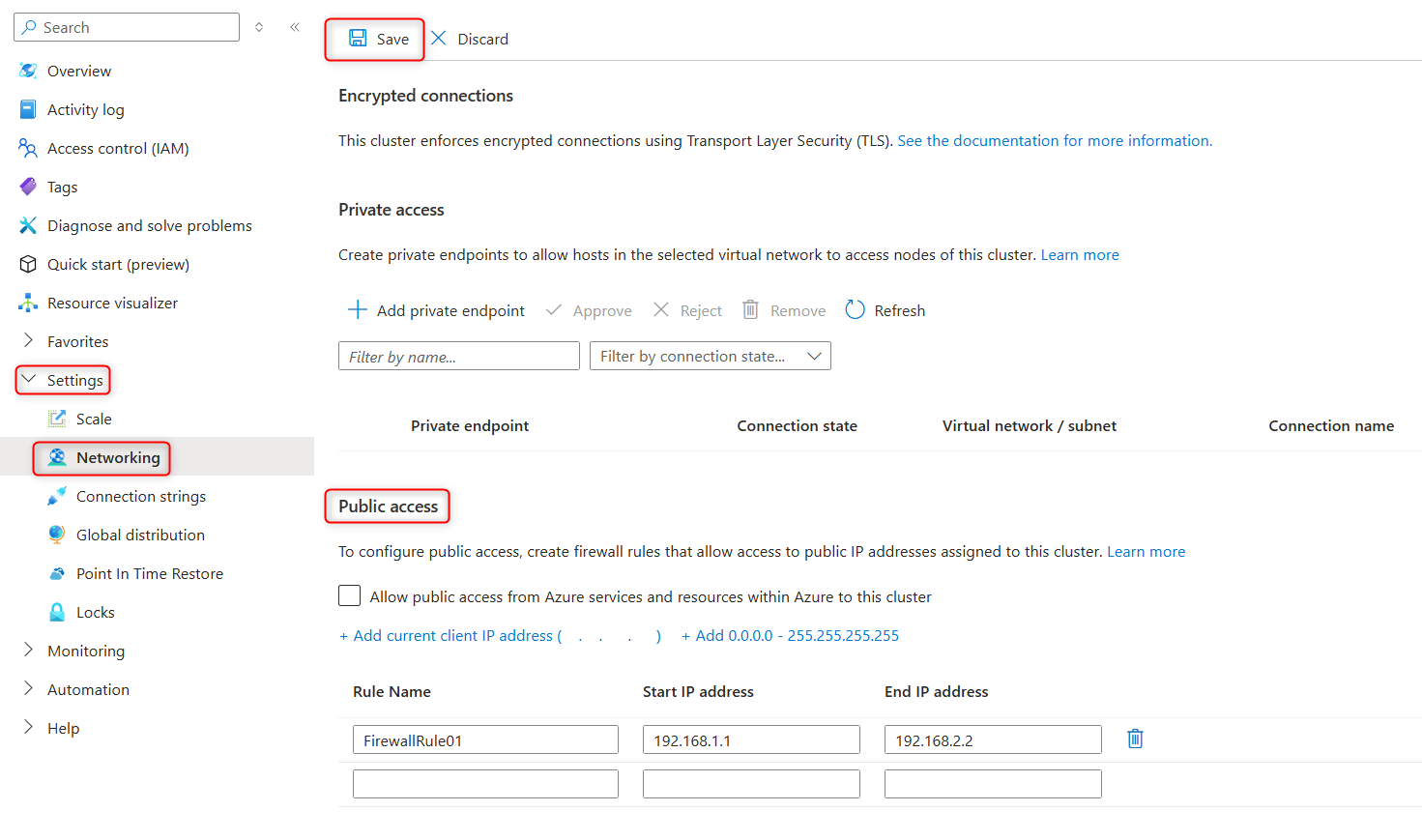
Manage existing cluster-level firewall rules through the Azure portal
You can modify firewall rules for an existing cluster through the Azure portal.
To add a firewall rule:
On the Azure Cosmos DB for MongoDB vCore cluster page, under Settings, select Networking.
In the Public access, in the Firewall rules section, type in the firewall rule name, start IP v4 address, and end IP v4 address.
- To allow a single IP address, enter the same address in both the Start IP address and End IP address fields.
To quickly add your current public IP address (the address of the machine or device from which you’re accessing the Azure portal), select Add current client IP address.
Tip
Verify your IP address before saving the configuration. In some cases, the IP address detected by the Azure portal may differ from the IP address used when accessing the Internet. To check your actual IP address, use a search engine to find tools like what is my IP.
To allow cluster access from any IP address on the Internet, select Add 0.0.0.0 - 255.255.255.255. Even with this rule in place, users must authenticate with the correct username and password to access the cluster. However, it’s recommended to allow global access only temporarily and for non-production databases.
Select Save on the toolbar to save the changes in cluster-level firewall rules. Wait for the confirmation that the update was successful.
To remove a firewall rule on your cluster, follow these steps:
- On the Azure Cosmos DB for MongoDB vCore cluster page, under Settings, select Networking.
- In the Public access, in the Firewall rules section, locate the firewall rule to delete.
- Select delete icon next to the firewall rule.
- Select Save on the toolbar to save the changes in cluster-level firewall rules. Wait for the confirmation that the update was successful.
Connect from Azure
There's an easy way to grant cluster access to applications hosted on Azure, such as an Azure Web Apps application or those applications running in an Azure VM.
- On the portal page for your cluster, under Networking, in the Public access, select the Allow Azure services and resources to access this cluster checkbox.
- Select Save on the toolbar to save the changes. Wait for the confirmation that the update was successful.
Important
Enabling this option allows connections from any Azure service, including from services and hosts in other customer subscriptions. Ensure your login credentials and user permissions restrict access to authorized users only.
Disable public access
To disable public access on a cluster:
- On the portal page for your cluster, under Networking, in the Public access, remove all firewall rules.
- Clear the Allow Azure services and resources to access this cluster checkbox.
- Select Save on the toolbar to save the changes. Wait for the confirmation that the update was successful.