Hello @Klaus Teddy Bøgelund Andresen,
Thank you for posting your query on Microsoft Q&A.
I understand that you want to implement automatic key rotation in Azure Key Vault. Ideally you don't want to specify the expiration date using the attributes parameter, but it should still work in the sense that the key itself should not expire.
Please note that based on your requirement, you can configure cryptographic key auto-rotation in Azure Key Vault or you can configure key auto-rotation in Azure key Vault Managed HSM.
1.Configure cryptographic key auto-rotation in Azure Key Vault:
Automated cryptographic key rotation in Key Vault allows users to configure Key Vault to automatically generate a new key version at a specified frequency. To configure rotation you can use key rotation policy, which can be defined on each individual key.
Our recommendation is to rotate encryption keys at least every two years to meet cryptographic best practices.
Permissions required
Key Vault key rotation feature requires key management permissions. You can assign a "Key Vault Crypto Officer" role to manage rotation policy and on-demand rotation.
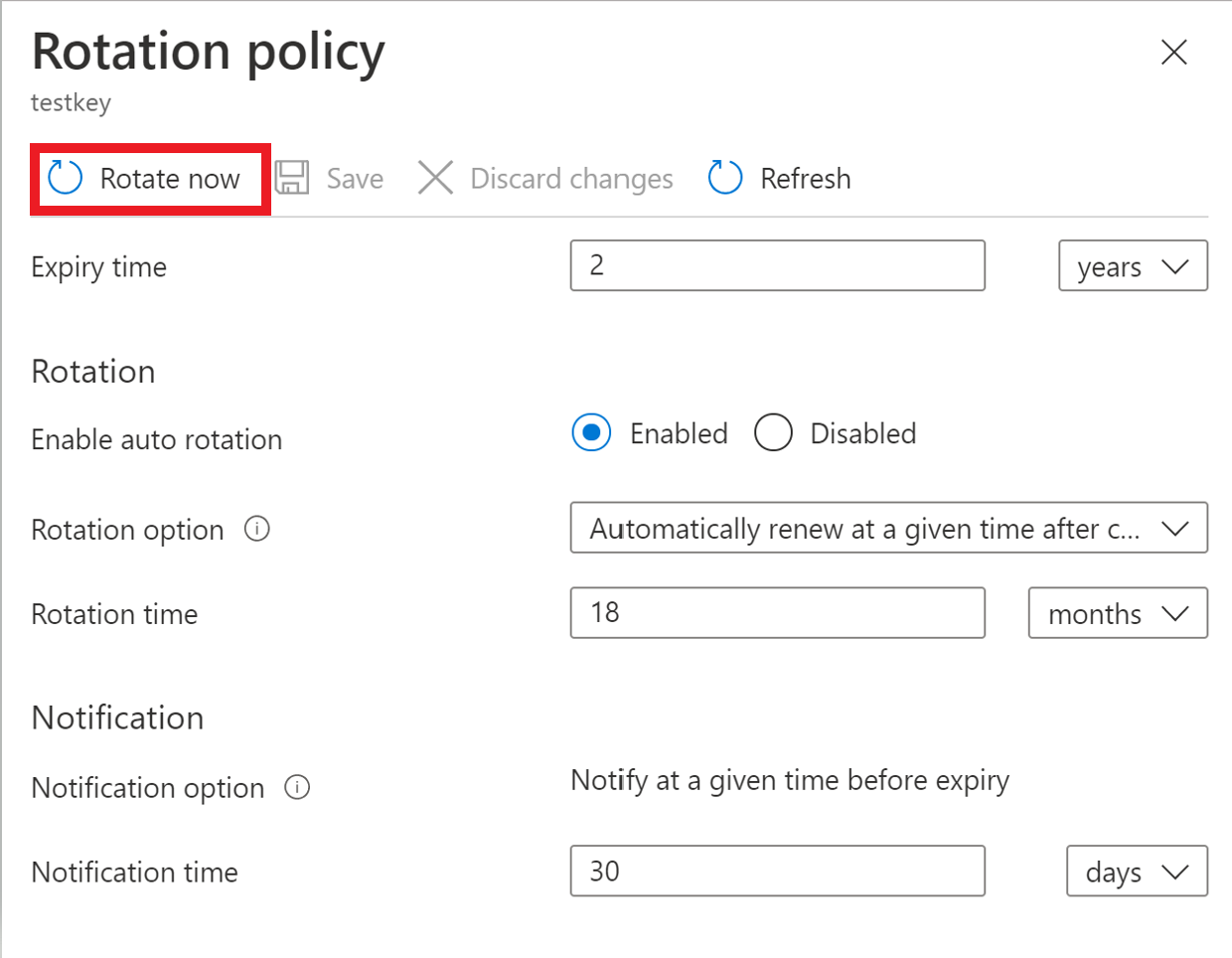
Key rotation policy
The key rotation policy allows users to configure rotation and Event Grid notifications near expiry notification.
Key rotation policy settings:
- Expiry time: key expiration interval. It's used to set expiration date on newly rotated key. It doesn't affect a current key.
- Enabled/disabled: flag to enable or disable rotation for the key
- Rotation types:
- Automatically renew at a given time after creation (default)
- Automatically renew at a given time before expiry. It requires 'Expiry Time' set on rotation policy and 'Expiration Date' set on the key.
- Rotation time: key rotation interval, the minimum value is seven days from creation and seven days from expiration time
- Notification time: key near expiry event interval for Event Grid notification. It requires 'Expiry Time' set on rotation policy and 'Expiration Date' set on the key.
Azure CLI
Save key rotation policy to a file. Key rotation policy example:
{
"lifetimeActions": [
{
"trigger": {
"timeAfterCreate": "P18M",
"timeBeforeExpiry": null
},
"action": {
"type": "Rotate"
}
},
{
"trigger": {
"timeBeforeExpiry": "P30D"
},
"action": {
"type": "Notify"
}
}
],
"attributes": {
"expiryTime": "P2Y"
}
}
Rotation on demand
Key rotation can be invoked manually.
Portal
Click 'Rotate Now' to invoke rotation.
Azure CLI
Use Azure CLI az keyvault key rotate command to rotate key.
az keyvault key rotate --vault-name <vault-name> --name <key-name>
For more additional details, please refer to the below document for your reference.
Configure cryptographic key auto-rotation in Azure Key Vault | Microsoft Learn
2.Configure key auto-rotation in Azure Managed HSM
Automated key rotation in Managed HSM allows users to configure Managed HSM to automatically generate a new key version at a specified frequency. You can set a rotation policy to configure rotation for each individual key and optionally rotate keys on demand. Our recommendation is to rotate encryption keys at least every two years to meet cryptographic best practices.
Permissions required
Rotating a key or setting a key rotation policy requires specific key management permissions. You can assign the "Managed HSM Crypto User" role to get sufficient permissions to manage rotation policy and on-demand rotation.
Key rotation policy
The key rotation policy allows users to configure rotation intervals and set the expiration interval for rotated keys. It must be set before keys can be rotated on-demand.
Note:
Managed HSM does not support Event Grid Notifications
Key rotation policy settings:
- Expiry time: key expiration interval (minimum 28 days). It is used to set expiration date on a newly rotated key (e.g. after rotation, the new key is set to expire in 30 days).
- Rotation types:
- Automatically renew at a given time after creation
- Automatically renew at a given time before expiry. 'Expiration Date' must be set on the key for this event to fire.
Configure a key rotation policy:
Azure CLI
Write a key rotation policy and save it to a file. Use ISO8601 Duration formats to specify time intervals. Some example policies are provided in the next section. Use the following command to apply the policy to a key.
az keyvault key rotation-policy update --hsm-name <hsm-name> --name <key-name> --value </path/to/policy.json>
Example policies
Rotate the key 18 months after creation and set the new key to expire after two years.
{
"lifetimeActions": [
{
"trigger": {
"timeAfterCreate": "P18M",
"timeBeforeExpiry": null
},
"action": {
"type": "Rotate"
}
}
],
"attributes": {
"expiryTime": "P2Y"
}
}
Rotation on demand
Once a rotation policy is set for the key, you can also rotate the key on-demand. You must set a key rotation policy first.
Azure CLI
az keyvault key rotate --hsm-name <hsm-name> --name <key-name>
For more additional details, please refer to the below document for your reference.
Configure key auto-rotation in Azure Key Vault Managed HSM | Microsoft Learn
I hope this above information provided is helpful. Please feel free to reach out if you have any further questions.
If the answer is helpful, please click "Accept Answer" and kindly upvote it. If you have extra questions about this answer, please click "Comment".