Data governance roles and permissions in Microsoft Purview
Important
This article covers Microsoft Purview data governance permissions in the new Microsoft Purview portal using Unified Catalog.
- For governance permissions the new Microsoft Purview portal using classic Data Catalog, see governance permissions for the classic Data Catalog.
- For general permissions in the new Microsoft purview portal, see permissions in the Microsoft Purview portal.
- For classic risk and compliance permissions, see the permissions in the Microsoft Purview compliance portal article.
- For data governance permissions in the classic Microsoft Purview portal, see the permissions in the Microsoft Purview governance portal article.
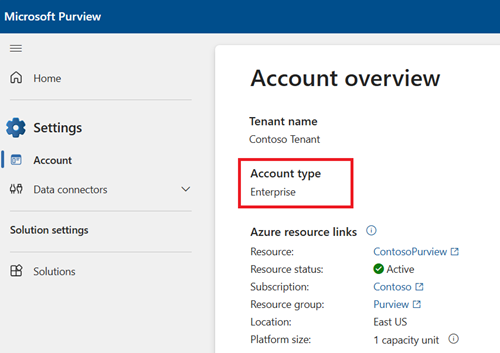
Microsoft Purview data governance has two solutions in the Microsoft Purview Portal: Data Map and Unified Catalog. These solutions use tenant/organizational-level permissions, existing data access permissions, and domain/collection permissions to provide users access to governance tools and data assets. The kind of permissions available to use depends on your Microsoft Purview account type. You can check your account type in the Microsoft Purview portal under the Settings card, and Account.
| Account Type | Tenant/Organization permissions | Data access permissions | Domain and collection permissions | Unified Catalog permissions |
|---|---|---|---|---|
| Free | x | x | ||
| Enterprise | x | x | x | x |
For more information about each permission type, see these guides:
- Tenant/organization permissions - assigned at the organizational level, they provide general and administrative permissions.
- Unified Catalog permissions - permissions in the Microsoft Purview Unified Catalog so users can browse and manage the catalog.
- Domain and collection level permissions - permissions in the Microsoft Purview Data Map that grant access to data assets in Microsoft Purview.
- Data access permissions - permissions users already have on their Azure data sources.
For more information about permission based on account type, see these guides:
Important
For users newly created in Microsoft Entra ID, it may take some time for permissions to propagate even after correct permissions have been applied.
Tenant level role groups
Assigned at the organizational level, tenant level role groups provide general, and administrative permissions for both the Microsoft Purview Data Map and Unified Catalog. If you're managing your Microsoft Purview account or your organization's data governance strategy, you probably need one or several of these roles.
The currently available governance tenant-level role groups are:
| Role group | Description | Account type availability |
|---|---|---|
| Purview administrator | Create, edit, and delete domains and perform role assignments. | Free and enterprise accounts |
| Data Source Administrators | Manage data sources and data scans in the Microsoft Purview Data Map. | Enterprise accounts |
| Data Governance | Grants access to data governance roles within Microsoft Purview. | Free and enterprise accounts |
For a full list of all available roles and role groups, not just for data governance, see roles, and role groups in the Microsoft Defender XDR and Microsoft Purview portals.
How to assign and manage role groups
Important
To assign roles in Microsoft Purview, a user needs to be assigned the role management role.
To assign and manage roles in Microsoft Purview, see permissions in Microsoft Purview.
Unified Catalog permissions
The Unified Catalog also uses three levels of permissions to allow users to access information:
- Data governance - a tenant/organizational-level role group that has the Data Governance Admin role. That role delegates the first level of access for governance domain creators. (This role isn't surfaced in Unified Catalog, but affects your ability to assign permissions in Unified Catalog.)
- Catalog-level permissions - permissions to grant ownership to governance domains and access to health management.
- Governance domain level permissions - permissions to access and manage resources inside specific governance domains.
Catalog-level permissions
Permissions that are assigned on Unified Catalog itself, and provide only high-level access.
| Role | Description | Application |
|---|---|---|
| Governance domain creator | Creates domains and delegates governance domain owner (or remains governance domain owner by default) | Unified Catalog |
| Data health owner | Create, update, and read artifacts in health management. | Health management |
| Data health reader | Can read artifacts in health management. | Health management |
How to assign catalog-level roles
Important
To be able to assign roles in Microsoft Purview a user needs to be a data governance admin at the tenant/organization level.
- In the Microsoft Purview portal, select Settings.
- Under Solution settings, select Unified Catalog.
- Select Roles and permissions.
- Select Governance domain creators or another role add user icon.
- Search the user you wish to add.
- Select the user.
- Select Save.
Governance domain level permission
Tip
The Governance domain owner is important to delegate to someone running data governance or Unified Catalog as it is an essential role to be able to start to build governance domains, data products, glossary terms, etc. It's recommended that you have at least two people assigned as governance domain owners.
Governance domain permissions provide access within a specific governance domain, and should be granted to data experts and business users to read and manage objects within the governance domain.
These are the governance domain roles currently available in Unified Catalog:
| Role | Description |
|---|---|
| Governance domain owner | Ability to delegate all other governance domain permissions, configure data quality scan alerts, and set domain level access policies. |
| Governance domain reader | Ability to read metadata for published governance domains. |
| Data steward* | Create, update, and read artifacts and policies within their governance domain. Can also read artifacts from other governance domains. |
| Data product owner* | Create, update, and read data products only within their governance domain. Can read artifacts from other domains to build relationships between the concepts. |
| Data Catalog reader | Read published concepts in the catalog across all governance domains as well as all business concepts in the governance domain they are granted access to. |
| Data quality steward | Able to use data quality features like data quality rule management, data quality scanning, browsing data quality insights, data quality scheduling, job monitoring, configuring threshold and alerts. Data quality steward is a subrole so the individual also needs Govennance domain reader and Data Catalog reader roles to perform data quality stewardship work. |
| Data quality reader | Browse all data quality insight, data quality rules definition, and data quality error files. This role can’t run data quality scanning and data profiling job, and this role won't have access to data profiling column level insight as column level insight. This is a subrole, to perform this role the individual also need Governance domain reader and Data Catalog reader roles. |
| Data quality metadata reader | Browse data quality insights (except profiling results column level insight), data quality rule definition, and rule level scores. This role won't have access to error records and can't run profiling and DQ scanning job. This is a subrole, to perform this role the individual also needs Governance domain reader and Data Catalog reader roles. |
| Data profile steward | Run data profiling jobs and have access to browse profiling insight details. This role can also browse through all data quality insights and can monitor profiling jobs. This role can’t create rules and can’t run data quality scanning. This is a subrole, to perform this role the individual also needs Governance domain reader and Data Catalog reader roles. |
| Data profile reader | This role will have required permissions to browse all data quality insights and can drill down the profiling results to browse the statistics in column level. This is a subrole, to perform this role the individual also needs Governance domain reader and Data Catalog reader roles. |
Note
*To be able to add data assets to a data product, data product owners and data stewards also need Data Map permissions to read those data assets in Data Map.
How to assign governance domain roles
Important
To assign roles in Microsoft Purview a user needs to be a governance domain owner in the governance domain. This role is assigned by data governance administrators, or governance domain creators.
Governance domain roles are assigned under the Roles tab in a governance domain. For more information, see how to manage governance domains.
Permissions to search the full Unified Catalog
No specific permissions are needed in Unified Catalog to be able to search the Unified Catalog. However, searching Unified Catalog will only return relevant data assets that you have permissions to view in Data Map.
Users can find a data asset in Unified Catalog when:
- The user searches data products in a governance domain where they have catalog reader permissions
- The user has at least read permissions on an available Azure or Microsoft Fabric resource
- The user has data reader permissions on a domain or collection in Data Map where the asset is stored
Permissions to these assets are managed at the resource level and at the Data Map level, respectively. For more information on providing this access, follow the links provided.
Tip
If your catalog is well-curated, day-to-day business users shouldn't need to search the full catalog. They should be able to find data they need in data products. For more information about setting up the Unified Catalog, see get started with data governance, and plan for Unified Catalog.
What Unified Catalog permissions do I need?
| Element | Action | Data governance admin | Governance domain creator | Governance domain owner | Data catalog reader | Data steward | Data product owner | Data health owner | Data health reader | Data quality steward | Data quality reader |
|---|---|---|---|---|---|---|---|---|---|---|---|
| Application role assignments | Read | x | x | ||||||||
| Edit | x | x | |||||||||
| Governance domains | Read | x | x | x | x | x | x | ||||
| Edit | x | x | |||||||||
| Data products | Read | x | x | x | x | x | |||||
| Edit | x | ||||||||||
| Health items | Read | x | x | ||||||||
| Edit | x | ||||||||||
| Data quality items | Read | x | x | x | |||||||
| Edit | x | ||||||||||
| Data access policies | Read | x | x | x | x | ||||||
| Edit | x | x |
Note
This table covers the basics, but not all roles, and not all scenarios for each role. Refer to the full list of roles for full details.
Unified Catalog roles
Here's the full list of all roles used to access and manage the Unified Catalog.
| Role | Description | Permission level | Available actions |
|---|---|---|---|
| Data governance admin | Delegates the first level of access for governance domain creators and other application-level permissions. | Tenant/organization | roleassignment/read, roleassignment/write |
| Governance domain creator | Creates domains and delegates governance domain owner (or remains governance domain owner by default). | Application | businessdomain/read, businessdomain/write |
| Governance domain owner | Ability to delegate all other governance domain permissions, configure data quality scan alerts, and set domain level access policies. | Governance domain | roleassignment/read, roleassignment/write, businessdomain/read, businessdomain/write, dataquality/scope/read, dataquality/scope/write, dataquality/scheduledscan/read, dataquality/scheduledscan/write, dataquality/scheduledscan/execute, datahealth/alert/read, datahealth/alert/write, dataquality/monitoring/read, dataquality/monitoring/write, dataproduct/read, glossaryterm/read, okr/read, dataaccess/domainpolicy/read, dataaccess/domainpolicy/write, dataaccess/dataproductpolicy/read, dataaccess/glossarytermpolicy/read |
| Data Catalog reader | Ability to read all published domains, data products, policies, and OKRs. | Governance domain | roleassignment/read, businessdomain/read, dataproduct/read, glossaryterm/read, okr/read, dataaccess/domainpolicy/read, dataaccess/glossarytermpolicy/read |
| Data steward | Create, update, and read critical data elements, glossary terms, OKRs, and policies within their governance domain. They can also read and build relationships with concepts in other governance domains. | Governance domain | roleassignment/read, businessdomain/read, dataquality/observer/write, dataproduct/read, data product/curate, glossaryterm/read, glossaryterm/write, okr/read, okr/write, dataaccess/domainpolicy/read, dataaccess/domainpolicy/write, dataaccess/dataproductpolicy/read, dataaccess/dataproductpolicy/write, dataaccess/glossarytermpolicy/read, dataaccess/glossarytermpolicy/write |
| Data product owner | Create, update, and read data products only within their governance domain. They can also read and build relationships with concepts in governance domains. | Governance domain | roleassignment/read, businessdomain/read, dataproduct/write, dataproduct/read, glossaryterm/read, okr/read, dataaccess/domainpolicy/read, dataaccess/dataproductpolicy/read, dataaccess/dataproductpolicy/write, dataaccess/glossarytermpolicy/read |
| Data health owner | Create, update, and read artifacts in health management. | Application | datahealth/read, datahealth/write |
| Data health reader | Can read artifacts in health management. | Application | datahealth/read |
| Data quality stewards | Able to use data quality features like data quality rule management, data quality scanning, browsing data profiling and data quality insights, data quality scheduling, job monitoring, configuring threshold and alerts. | Governance domain | businessdomain/read, dataquality/scope/read, dataquality/scope/write, dataquality/scheduledscan/read, dataquality/scheduledscan/write, dataquality/scheduledscan/execute/action, datahealth/alert/read, datahealth/alert/write, dataquality/monitoring/read, dataquality/monitoring/write, dataquality/connection/write, dataquality/connection/read, dataquality/schemadetection/execute/action, dataquality/observer/read, dataquality/observer/write, dataquality/observer/execute/action, dataquality/history/scores/read, dataquality/history/ruledetails/read, dataquality/history/ruleerrorfile/read, dataquality/history/ruleerrorfile/delete, dataquality/history/delete, dataproduct/read, glossaryterm/read |
| Data quality reader | Browse all data quality insights and data quality rules definitions. This role can’t run data quality scanning and data profiling jobs, and this role won't have access to data profiling column level insight as column level insight. | Governance domain | dataquality/connection/read, dataquality/observer/read, dataquality/observer/execute/action, dataquality/history/scores/read, dataquality/history/ruledetails/read |
| Data quality metadata reader | Browse data quality insights (except profiling results column level insight), data quality rule definition, and rule level scores. This role won't have access to error records and can't run profiling and DQ scanning job. This is a subrole, to perform this role the individual also needs Governance domain reader and Data Catalog reader roles. | Governance domain | dataquality/connection/read, dataquality/observer/read, dataquality/history/scores/read, dataquality/history/ruledetails/read |
| Data profile steward | Run data profiling jobs and have access to browse profiling insight details. This role can also browse through all data quality insights and can monitor profiling jobs. This role can’t create rules and can’t run data quality scanning. This is a subrole, to perform this role the individual also needs Governance domain reader and Data Catalog reader roles. | Governance domain | dataquality/connection/read, dataquality/schemadetection/execute/action, dataquality/profile/read, dataquality/profile/execute/action, dataquality/profilehistory/read, dataquality/profilehistory/delete |
| Data profile reader | This role will have required permissions to browse all profiling insights and can drill down the profiling results to browse the statistics in column level. | Governance domain | dataquality/connection/read, dataquality/profile/read, dataquality/profilehistory/read |
Data Map permissions
Domains and collections are tools used by Data Map to group assets, sources, and other artifacts into a hierarchy for discoverability, and to manage access control within Data Map.
Domain and collection permissions
Data Map uses a set of predefined roles to control who can access what within the account. These roles are:
- Domain admin (domain level only) - Can assign permissions within a domain and manage its resources.
- Collection administrator - a role for users that will need to assign roles to other users in the Microsoft Purview governance portal or manage collections. Collection admins can add users to roles on collections where they're admins. They can also edit collections, their details, and add subcollections. A collection administrator on the root collection also automatically has permission to the Microsoft Purview governance portal. If your root collection administrator ever needs to be changed, you can follow the steps in the section below.
- Data curators - a role that provides access to the Microsoft Purview Unified Catalog to manage assets, configure custom classifications, create and manage glossary terms, and view data estate insights. Data curators can create, read, modify, move, and delete assets. They can also apply annotations to assets.
- Data readers - a role that provides read-only access to data assets, classifications, classification rules, collections and glossary terms.
- Data source administrator - a role that allows a user to manage data sources and scans. If a user is granted only to Data source admin role on a given data source, they can run new scans using an existing scan rule. To create new scan rules, the user must be also granted as either Data reader or Data curator roles.
- Insights reader - a role that provides read-only access to insights reports for collections where the insights reader also has at least the Data reader role. For more information, see insights permissions.
- Policy author - a role that allows a user to view, update, and delete Microsoft Purview policies through the Data policy app within Microsoft Purview.
- Workflow administrator - a role that allows a user to access the workflow authoring page in the Microsoft Purview governance portal, and publish workflows on collections where they have access permissions. Workflow administrator only has access to authoring, and so will need at least Data reader permission on a collection to be able to access the Purview governance portal.
Note
At this time, Microsoft Purview policy author role is not sufficient to create policies. The Microsoft Purview data source admin role is also required.
Important
The user that created the account is automatically assigned domain admin on the default domain and collection admin on the root collection.
Add role assignments
Open the Microsoft Purview Data Map.
Select the domain or collection where you want to add your role assignment.
Select the Role assignments tab to see all the roles in a collection or a domain. Only a collection admin or domain admin can manage role assignments.
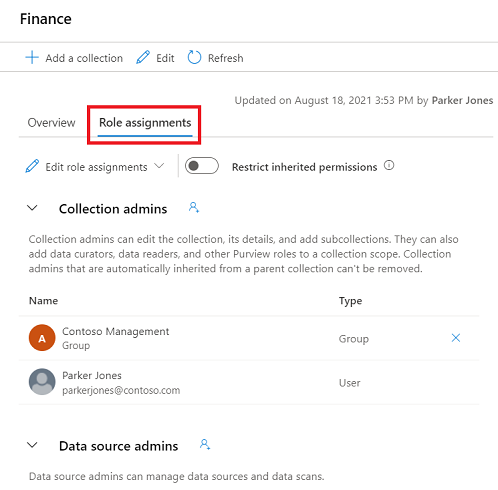
Select Edit role assignments or the person icon to edit each role member.
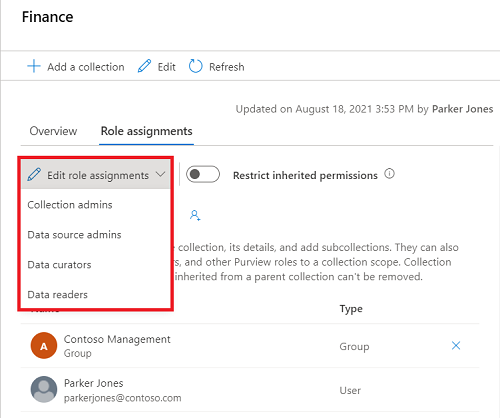
Type in the textbox to search for users you want to add to the role member. Select X to remove members you don't want to add.
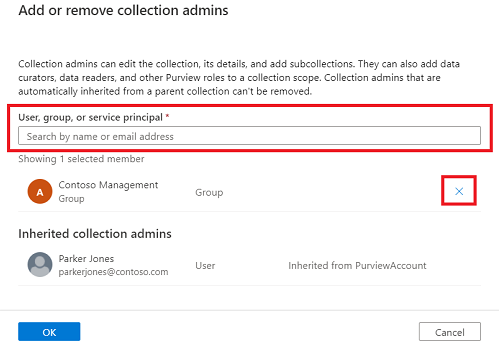
Select OK to save your changes, and you'll see the new users reflected in the role assignments list.
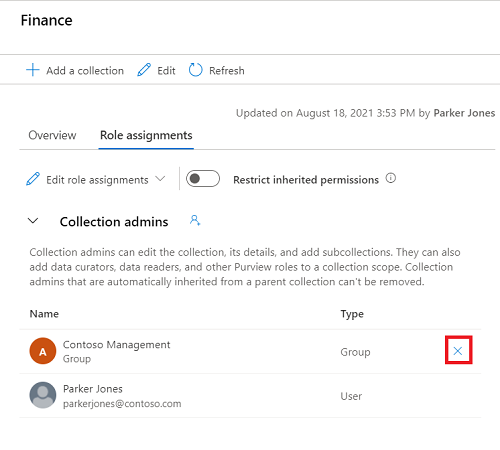
Remove role assignments
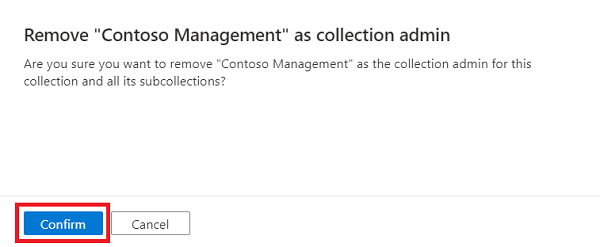
Select X button next to a user's name to remove a role assignment.
Select Confirm if you're sure to remove the user.
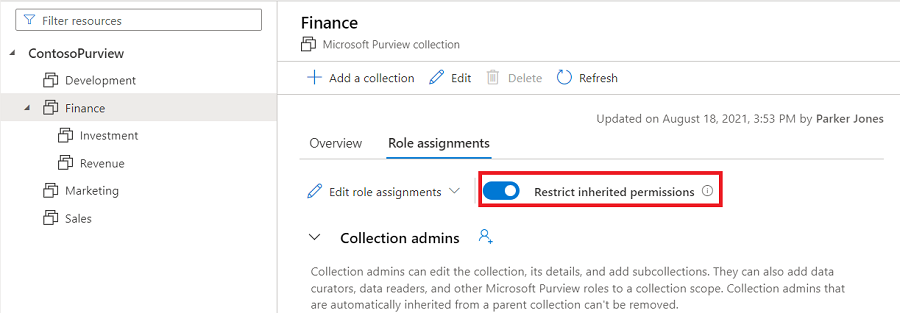
Restrict inheritance
Collection permissions are inherited automatically from the parent collection. You can restrict inheritance from a parent collection at any time, using the restrict inherited permissions option.
Note
Currently permissions from the default domain cannot be restricted. Any permissions assigned at the default domain will be inherited by the domain's direct subcollections.
Once you restrict inheritance, you'll need to add users directly to the restricted collection to grant them access.
Navigate to the collection where you want to restrict inheritance and select the Role assignments tab.
Select Restrict inherited permissions and select Restrict access in the popup dialog to remove inherited permissions from this collection and any subcollections. Collection admin permissions won't be affected.
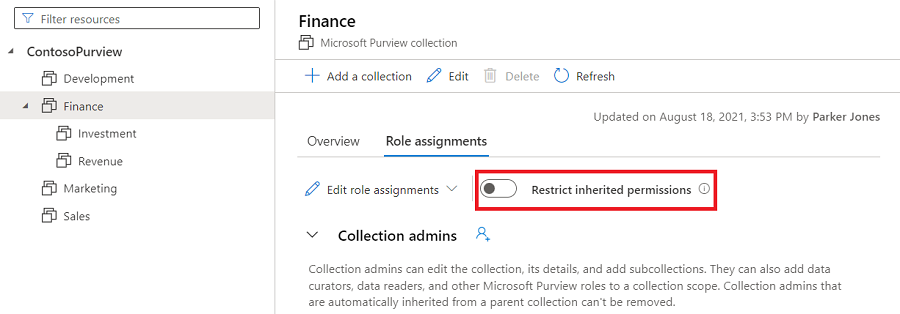
After restriction, inherited members are removed from the roles expect for collection admin.
Select the Restrict inherited permissions toggle button again to revert.
Tip
For more detailed information about the roles available in collections see the who should be assigned what roles table or the collections example.
Data access permissions
Data access permissions are permissions users already have on their Azure data sources. These existing permissions also grant permission to access and manage the metadata for those sources, depending on the level of permissions:
Currently, these features are only available for some Azure sources:
| Data source | Reader permission |
|---|---|
| Azure SQL Database | Reader, or these actions. |
| Azure Blob Storage | Reader, or these actions. |
| Azure Data Lake Storage Gen2 | Reader, or these actions. |
| Azure Subscription | Read permission on subscription, or these actions. |
The reader role contains enough permissions, but if you're building a custom role, your users need to have these actions included:
| Data source | Reader permission |
|---|---|
| Azure SQL Database | "Microsoft.Sql/servers/read", "Microsoft.Sql/servers/databases/read", "Microsoft.Sql/servers/databases/schemas/read", "Microsoft.Sql/servers/databases/schemas/tables/read", "Microsoft.Sql/servers/databases/schemas/tables/columns/read" |
| Azure Blob Storage | "Microsoft.Storage/storageAccounts/read", "Microsoft.Storage/storageAccounts/blobServices/read", "Microsoft.Storage/storageAccounts/blobServices/containers/read" |
| Azure Data Lake Storage Gen2 | "Microsoft.Storage/storageAccounts/read", "Microsoft.Storage/storageAccounts/blobServices/read", "Microsoft.Storage/storageAccounts/blobServices/containers/read" |
| Azure Subscription | "Microsoft.Resources/subscriptions/resourceGroups/read" |
Reader permissions
Users who have at least the reader role on available Azure resources are also able to access those resources metadata in the free and enterprise account types.
Users can search and browse for assets from these sources in the Unified Catalog and view their metadata.
These are the permissions needed on the resources for users to be considered 'readers':
| Data source | Reader permission |
|---|---|
| Azure SQL Database | Reader, or these actions. |
| Azure Blob Storage | Reader, or these actions. |
| Azure Data Lake Storage Gen2 | Reader, or these actions. |
| Azure Subscription | Read permission on subscription, or these actions. |
Owner permissions
Users who have the owner role or write permissions on available Azure resources can access and edit metadata for those resources in free and enterprise account types.
Owning users can search and browse for assets from these sources in Unified Catalog, and view their metadata. They can also update and manage the metadata for those resources. For more information about this metadata curation, see our metadata curation article.
These are the permissions needed on the resources for users to be considered 'owners':
| Data source | Owner permission |
|---|---|
| Azure SQL Database | "Microsoft.Sql/servers/write", "Microsoft.Sql/servers/databases/write", "Microsoft.Authorization/roleAssignments/write" |
| Azure Blob Storage | "Microsoft.Storage/storageAccounts/write", "Microsoft.Authorization/roleAssignments/write" |
| Azure Data Lake Storage Gen2 | "Microsoft.Storage/storageAccounts/write", "Microsoft.Authorization/roleAssignments/write" |
Permissions in the free version
All users are able to view data assets for available sources where they have at least Read permissions already. Owning users are able to manage the metadata for available assets where they have at least Owner/Write permissions already. For more information, see the data access permissions section.
Extra permissions can also be assigned using tenant level role groups.
Important
For users newly created in Microsoft Entra ID, it may take some time for permissions to propagate even after correct permissions have been applied.
Permissions in enterprise version
All users are able to view data assets for available sources where they have at least Read permissions already. Owning users are able to manage the metadata for assets where they have at least Owner/Write permissions already. For more information, see the data access permissions section.
Extra permissions can also be assigned using tenant level role groups.
Permissions can also be assigned in Data Map so users can browse assets in Data Map or Unified Catalog search that they don't already have data access to.
Unified Catalog permissions can be assigned to grant users permission to the catalog to build out their data governance solutions.
Data asset lifecycle example
To understand how permissions work between Data Map and Unified Catalog, review the table below on the full lifecycle of an Azure SQL table in the environment:
| Step | Role | Role Assignment Level |
|---|---|---|
| 1. The Azure SQL Database is registered in Data Map | data source administrator | Data Map permissions |
| 2. The Azure SQL Database is scanned in Data Map | data curator or data source administrator | Data Map permissions |
| 3. The Azure SQL table is curated and certified | data curator | Data Map permissions |
| 4. A governance domain is created in the Microsoft Purview Account | Governance Domain Creator | application-level role |
| 5. A data product is created in the governance domain | Governance Domain Owner and/or Data Product Owner | governance domain-level role |
| 6. The Azure SQL table is added as an asset to the data product | Data Product Owner and/or Steward | governance domain-level role |
| 7. An access policy is added to the data product | Data Product Owner and/or Steward | governance domain-level role |
| 8. A user searches Unified Catalog, looking for data assets that match their needs | Asset permissions or data reader permission | Asset permissions or Data Map permissions |
| 9. A user searches data products, looking for a product that matches their needs | Data Catalog Reader | application-level role |
| 10. A user requests access to the resources in the Data Product | Data Catalog Reader | application-level role |
| 11. A user views Data Health Insights to track the health of their Data Catalog | Data Health Reader | application-level role |
| 12. A user wants to develop a new report to track data health progress in their catalog | Data Health Owner | application-level role |