Apply Conditional Access policies to Global Secure Access traffic
You apply Conditional Access policies to Global Secure Access traffic. With Conditional Access, you can require multifactor authentication and device compliance for accessing Microsoft resources.
This article describes how to apply Conditional Access policies to your Global Secure Access internet traffic.
Prerequisites
- Administrators who interact with Global Secure Access features must have one or more of the following role assignments depending on the tasks they're performing.
- The Global Secure Access Administrator role role to manage the Global Secure Access features.
- The Conditional Access Administrator role to create and interact with Conditional Access policies.
- The product requires licensing. For details, see the licensing section of What is Global Secure Access. If needed, you can purchase licenses or get trial licenses.
Create a Conditional Access policy targeting Global Secure Access internet traffic
The following example policy targets all users except for your break-glass accounts and guest/external users, requiring multifactor authentication, device compliance, or a Microsoft Entra hybrid joined device for Global Secure Access internet traffic.
Sign in to the Microsoft Entra admin center as at least a Conditional Access Administrator.
Browse to Identity > Protection > Conditional Access.
Select Create new policy.
Give your policy a name. We recommend that organizations create a meaningful standard for the names of their policies.
Under Assignments, select the Users and groups link.
- Under Include, select All users.
- Under Exclude:
- Select Users and groups and choose your organization's emergency access or break-glass accounts.
- Select Guest or external users and select all checkboxes.
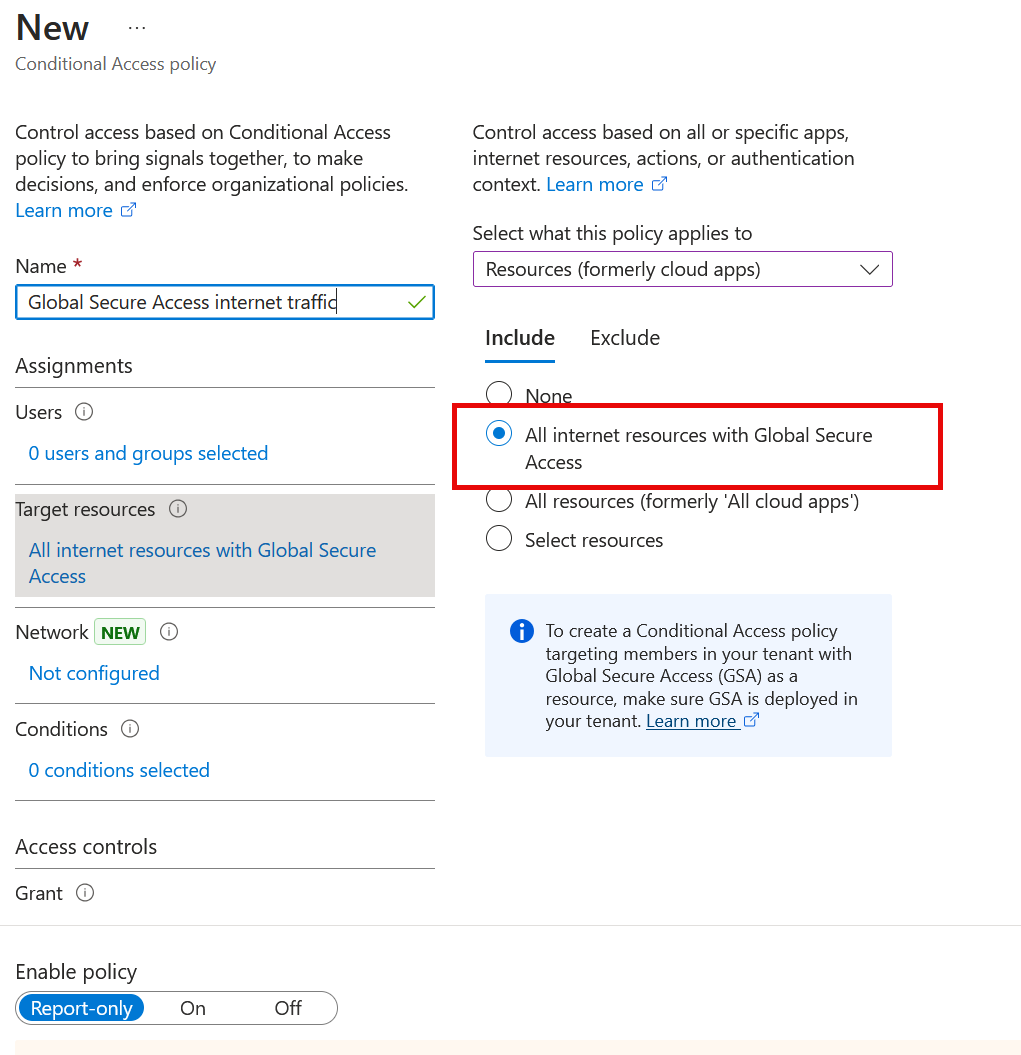
Under Target resources > Resources (formerly cloud apps).
- Choose All internet resources with Global Secure Access.
Note
To only enforce the Internet Access traffic forwarding profile and not the Microsoft traffic forwarding profile then choose Select resources and select Internet resources from the app picker and configure a security profile.
Under Access controls > Grant.
- Select Require multifactor authentication, Require device to be marked as compliant, and Require Microsoft Entra hybrid joined device
- For multiple controls select Require one of the selected controls.
- Select Select.
After administrators confirm the policy settings using report-only mode, an administrator can move the Enable policy toggle from Report-only to On.
User exclusions
Conditional Access policies are powerful tools, we recommend excluding the following accounts from your policies:
- Emergency access or break-glass accounts to prevent lockout due to policy misconfiguration. In the unlikely scenario all administrators are locked out, your emergency-access administrative account can be used to log in and take steps to recover access.
- More information can be found in the article, Manage emergency access accounts in Microsoft Entra ID.
- Service accounts and Service principals, such as the Microsoft Entra Connect Sync Account. Service accounts are non-interactive accounts that aren't tied to any particular user. They're normally used by back-end services allowing programmatic access to applications, but are also used to sign in to systems for administrative purposes. Calls made by service principals won't be blocked by Conditional Access policies scoped to users. Use Conditional Access for workload identities to define policies targeting service principals.
- If your organization has these accounts in use in scripts or code, consider replacing them with managed identities.
Next steps
The next step for getting started with Microsoft Entra Internet Access is to review the Global Secure Access logs.
For more information about traffic forwarding, see the following articles: