Register a SAML app in your external tenant (preview)
Applies to:  Workforce tenants
Workforce tenants  External tenants (learn more)
External tenants (learn more)
In external tenants, you can register applications that use the OpenID Connect (OIDC) or Security Assertion Markup Language (SAML) protocol for authentication and single sign-on. The app registration process is designed specifically for OIDC apps. But you can use the Enterprise applications feature to create and register your SAML app. This process generates a unique application ID (client ID) and adds your app to the App registrations, where you can view and manage its properties.
This article describes how to register your own SAML application in your external tenant by creating a non-gallery app in Enterprise applications.
Note
The following capabilities aren't supported for SAML apps in external tenants:
- Preintegrated SAML applications in the Microsoft Entra gallery aren't supported in external tenants.
- The availability of the Provisioning tab in the SAML app settings is a known issue. Provisioning isn't supported for apps in external tenants.
- IdP initiated flow isn't supported.
Prerequisites
- An Azure account that has an active subscription. Create an account for free.
- A Microsoft Entra external tenant.
- A sign-up and sign-in user flow.
Create and register a SAML app
Sign in to the Microsoft Entra admin center as at least an Application Administrator.
If you have access to multiple tenants, use the Settings icon
 in the top menu and switch to your external tenant from the Directories menu.
in the top menu and switch to your external tenant from the Directories menu.Go to Identity > Applications > Enterprise Applications (Preview).
Select New application.
Select Create your own application.
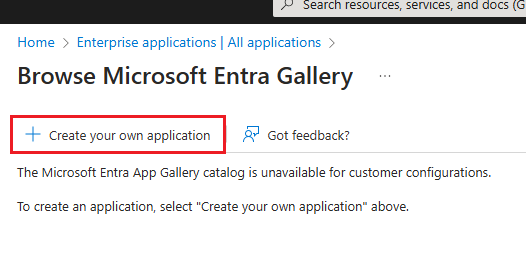
On the Create your own application pane, enter a name for your app.
Note
You might see a gallery app selector, but you can disregard it as gallery apps aren't supported in external tenants.
Select "(Preview) Integrate any other application you don't find in the gallery (Non-gallery)".
Select Create.
The app Overview page opens. In the left menu under Manage, select Properties. Switch the Assignment required? toggle to No so that users can use self-service sign-up, and then select Save.

In the left menu under Manage, select Single sign-on (Preview).
Under Select a single sign-on method, select SAML (preview).
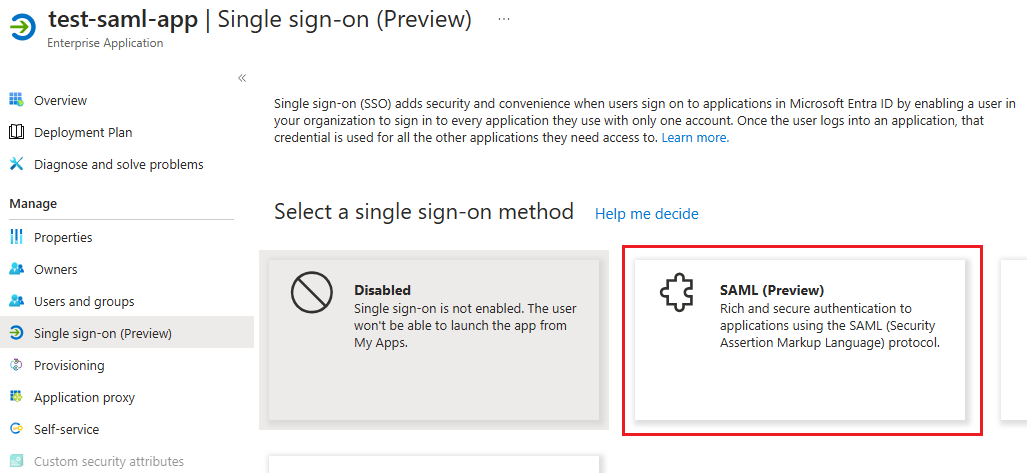
On the SAML-based Sign-on (Preview) page, do one of the following:
- Select Upload metadata file, browse to the file containing your metadata, and then select Add. Select Save.
- Or, use the Edit pencil option to update each section, and then select Save.
Note
Make sure your SAML app uses your
ciamloginendpoint, for exampledomainname.ciamlogin.com, instead oflogin.microsoft.com. If you're downloading the federation metadata URL, it should be in the formdomain.ciamlogin.com/<tenantid>/federationmetadata/2007-06/federationmetadata.xml?appid=<appid>.Select Test, and then select the Test sign-in button to see if single sign-on is working. This test verifies that your current admin account can sign in using the
https://login.microsoftonline.comendpoint.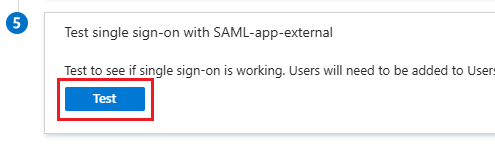
You can test external user sign-in with these steps:
- Create a sign-up and sign-in user flow if you haven't already.
- Add your SAML application to the user flow.
- Run your application.