Enable screen capture protection in Azure Virtual Desktop
Screen capture protection, alongside watermarking, helps prevent sensitive data from being captured on client devices using specific operating system (OS) features and APIs. When you enable screen capture protection, remote content is automatically blocked in screenshots and screen sharing.
When screen capture protection is enabled, users can't share their remote window using local collaboration software, such as Microsoft Teams. With Teams, the local Teams app or using Teams with media optimization can't share protected content.
Tip
To increase the security of your sensitive information, you should also disable clipboard, drive, and printer redirection. Disabling redirection helps prevent users from copying content from the remote session. To learn about supported redirection values, see Device redirection.
To discourage other methods of screen capture, such as taking a photo of a screen with a physical camera, you can enable watermarking, where admins can use a QR code to trace the session.
Determine your configuration
The steps to configure screen capture protection depend on where you configure it, which platforms your users are connecting from and what scenario you want to achieve.
Windows and macOS devices: you prevent screen capture by configuring session hosts using an Intune device configuration policy or Group Policy. Windows App or the Remote Desktop client enforces screen capture protection settings from a session host without further configuration.
When you configure screen capture protection on session hosts, there are two further settings you can configure to help meet your requirements:
Block screen capture on client: prevents screen capture from the local device of applications running in the remote session.
Block screen capture on client and server: prevents screen capture from the local device of applications running in the remote session, but also prevents tools and services within the session host capturing the screen.
In this scenario, here's the outcome when connecting from each platform type:
Platform Connection allowed Screen capture blocked Windows ✅ ✅ macOS ✅ ✅ iOS/iPadOS ❌ N/A Android ❌ N/A Web ❌ N/A iOS/iPadOS and Android devices: you prevent screen capture by configuring local devices using an Intune app protection policy, part of mobile application management (MAM). It doesn't prevent tools and services within the session host capturing the screen.
In this scenario, here's the outcome when connecting from each platform type:
Platform Connection allowed Screen capture blocked Windows ✅ ❌ macOS ✅ ❌ iOS/iPadOS ✅ ✅ Android ✅ ✅ Web ✅ ❌
Important
You need to choose which local devices to use with screen capture protection based on your requirements. There isn't a scenario where you can enable screen capture protection on all platforms from the same session hosts at the same time. If both are configured, screen capture protection on session hosts takes precedence over using an Intune MAM policy on local devices.
Prerequisites
For scenarios where you need to configure session hosts, those session hosts must be running a Windows 11, version 22H2 or later, or Windows 10, version 22H2 or later.
Users must connect to Azure Virtual Desktop with Windows App or the Remote Desktop app to use screen capture protection. The following table shows supported scenarios:
Windows App:
Platform Minimum version Desktop session RemoteApp session Windows App on Windows Any Yes Yes. Local device OS must be Windows 11, version 22H2 or later. Windows App on macOS Any Yes Yes Windows App on iOS/iPadOS 11.0.8 Yes Yes Windows App on Android (preview)¹ 1.0.145 Yes Yes 1. Doesn't include support for Chrome OS because Intune MAM isn't supported on Chrome OS.
Remote Desktop client:
Platform Minimum version Desktop session RemoteApp session Windows (desktop client) 1.2.1672 Yes Yes. Local device OS must be Windows 11, version 22H2 or later. Windows (Azure Virtual Desktop Store app) Any Yes Yes. Local device OS must be Windows 11, version 22H2 or later. macOS 10.7.0 or later Yes Yes
To configure Microsoft Intune, you need:
Microsoft Entra ID account that is assigned the Policy and Profile manager built-in RBAC role.
A group containing the devices you want to configure.
To configure Group Policy, you need:
A domain account that is a member of the Domain Admins security group.
A security group or organizational unit (OU) containing the devices you want to configure.
Enable screen capture protection on session hosts using an Intune device configuration policy or Group Policy
Select the relevant tab for your scenario.
To configure screen capture protection on session hosts using Microsoft Intune:
Sign in to the Microsoft Intune admin center.
Create or edit a configuration profile for Windows 10 and later devices, with the Settings catalog profile type.
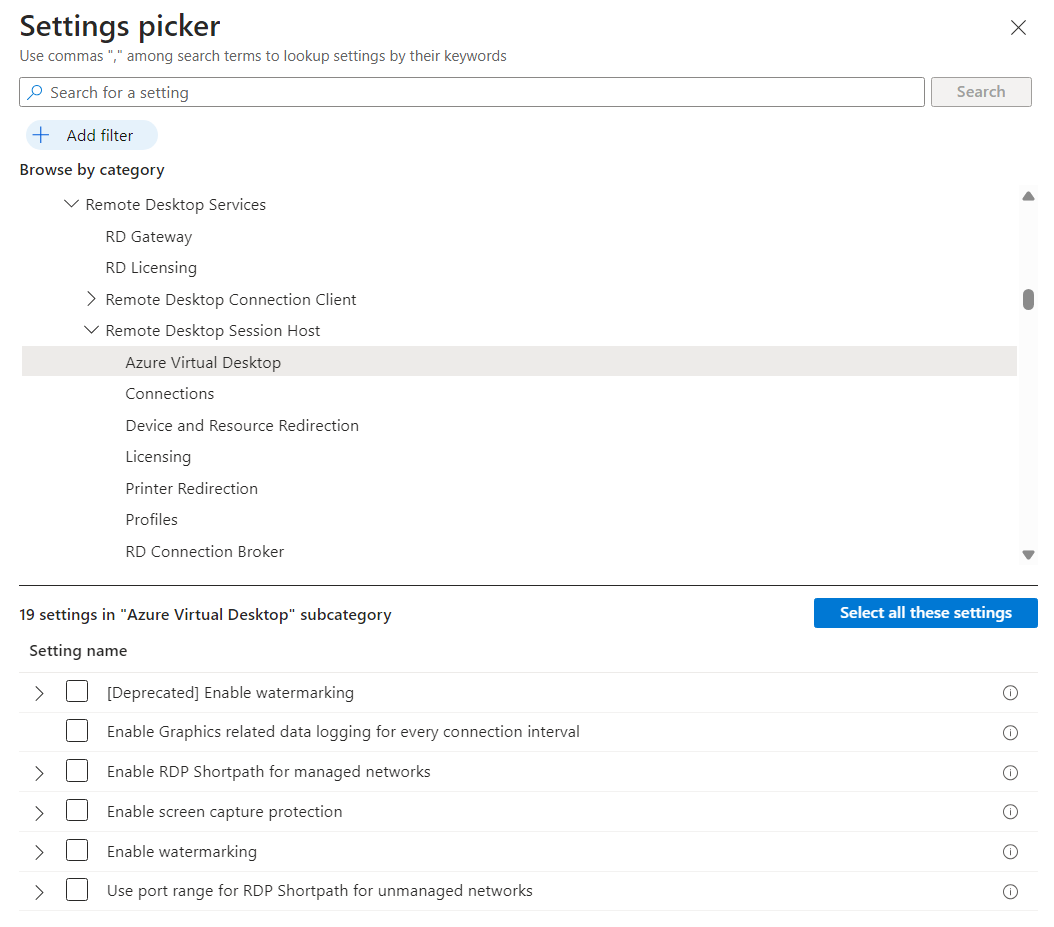
In the settings picker, browse to Administrative templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Azure Virtual Desktop.
Check the box for Enable screen capture protection, then close the settings picker.
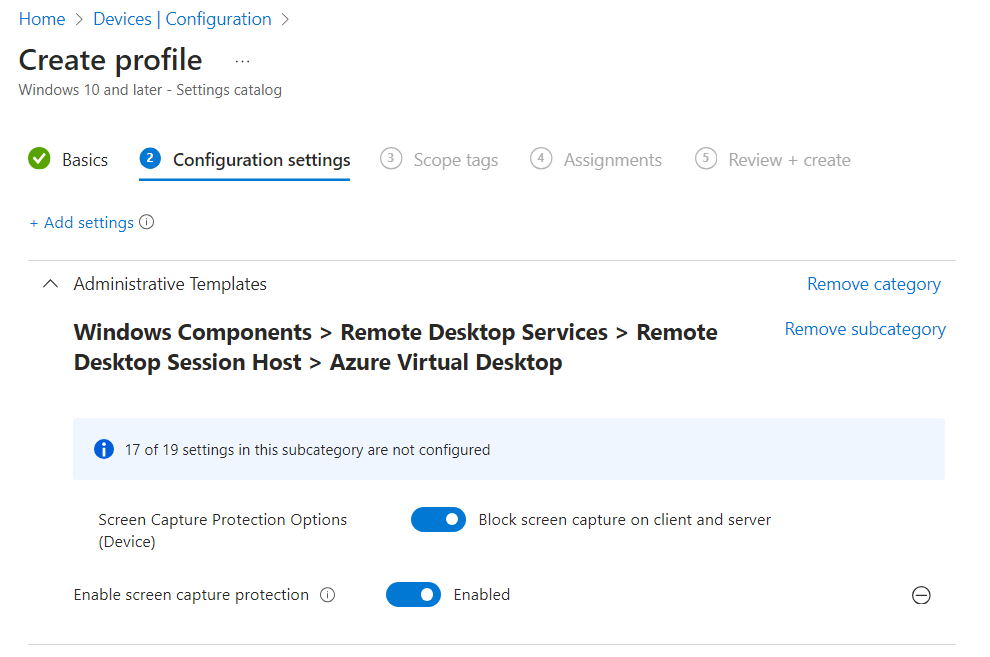
Expand the Administrative templates category, then toggle the switch for Enable screen capture protection to Enabled.
Toggle the switch for Screen Capture Protection Options (Device) to off for Block screen capture on client, or on for Block screen capture on client and server based on your requirements, then select OK.
Select Next.
Optional: On the Scope tags tab, select a scope tag to filter the profile. For more information about scope tags, see Use role-based access control (RBAC) and scope tags for distributed IT.
On the Assignments tab, select the group containing the computers providing a remote session you want to configure, then select Next.
On the Review + create tab, review the settings, then select Create.
Once the policy applies to the computers providing a remote session, restart them for the settings to take effect.
Enable screen capture protection on local devices using Intune MAM
To use screen capture protection on iOS/iPadOS and Android devices running Windows App, you need to configure an Intune app protection policy.
To configure an Intune app protection policy to enable screen capture protection on iOS/iPadOS and Android devices:
Follow the steps to Configure client device redirection settings for Windows App and the Remote Desktop app using Microsoft Intune. Configuration of screen capture protection is part of an app protection policy.
When configuring an app protection policy, on the Data protection tab, configure the following setting, depending on the platform:
For iOS/iPadOS, set Send org data to other apps to None.
For Android, set Screen capture and Google Assistant to Block.
Configure other settings based on your requirements and target the app protection policy to users and devices.
Verify screen capture protection
To verify screen capture protection is working:
Connect to a new remote session with a supported client. Don't reconnect to an existing session. You need to sign out of any existing sessions and sign back in again for the change to take effect.
From a local device, take a screenshot or share your screen in a Teams call or meeting. The content is blocked or hidden.
On Windows and macOS devices, if you enabled Block screen capture on client and server on your session hosts, try to capture the screen using a tool or service within the session host. The content is blocked or hidden.
If you enable screen capture protection on session hosts, you must connect from a supported device. If you don't, you see an error message indicating that screen capture protection is enabled. The error message looks similar to these screenshots:
Web browser:

iOS/iPadOS:

Related content
Enable watermarking, where admins can use a QR code to trace the session.
Learn about how to secure your Azure Virtual Desktop deployment at Security best practices.