Vulnerability assessments for Docker Hub external registry with Microsoft Defender Vulnerability Management
A key aspect of Defender for Containers' security solution is to provide container image vulnerability assessment throughout its lifecycle, from code development to cloud deployment.
To achieve this goal, comprehensive coverage is needed for all stages of the container image life cycle, including container images from external registries. Docker Hub, widely used by enterprises, SMBs, and the open-source community, is supported in this feature. Customers using Docker Hub can use Defender for Containers for inventory discovery, security posture evaluation, and vulnerability assessment - enjoying the same security capabilities available for cloud-native registries like ACR, ECR, and GCR.
Functionality
Inventory – identify and list all available container images within the Docker Hub organization
Vulnerability Assessment– Regularly scan the Docker Hub organization account for supported container images, identify vulnerabilities, and provide recommendations for issues to be addressed.
Prerequisites
To use Microsoft Defender for Containers with your organizational Docker Hub accounts, you must own a Docker Hub organization account and have admin permission to manage users. For more information, see How to set up Docker Hub as an external registry
Enable Microsoft Defender for Containers or Defender for CSPM for at least one subscription in Microsoft Defender for Cloud
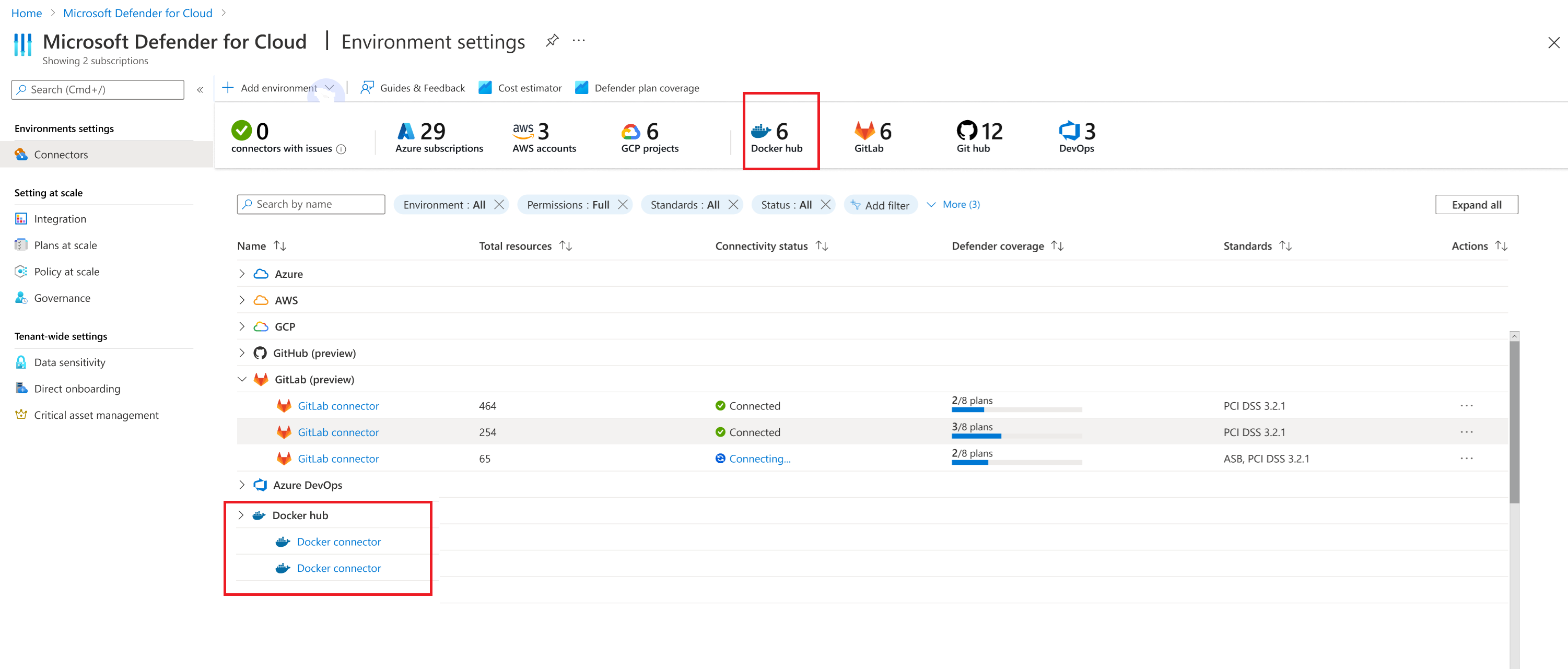
Onboard the Docker Hub environment
Individuals who have security administrator privileges in Microsoft Defender for Cloud can add a new Docker Hub environment, provided they have the necessary permissions on the "Environment Settings" page.
Each environment corresponds to a distinct Docker Hub organization. The onboarding interface for adding a new external registry allows the user to designate the type of container registry as a new environment classified as "Docker Hub".
The environment wizard assists with the onboarding process:
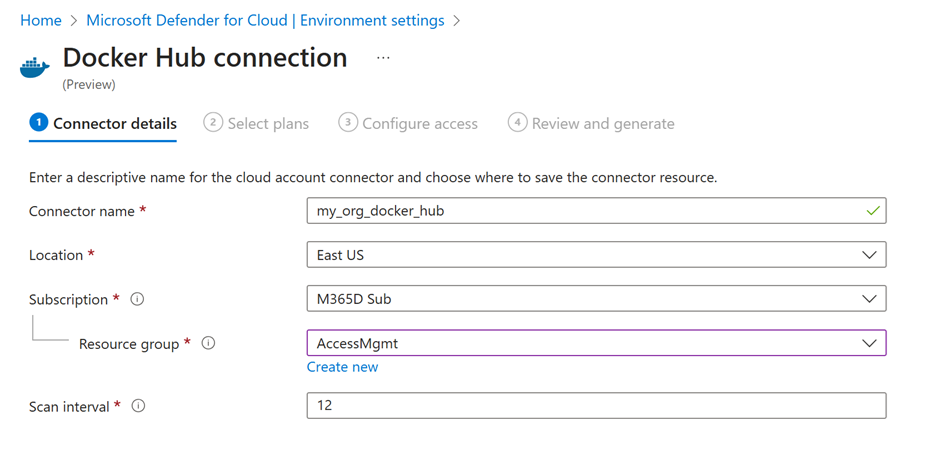
Connector Details
Connector name: Specify a unique connector name.
Location: Specify the geographic location where Defender for Cloud stores the data associated with this connector.
Subscription: The hosting subscription that defines the RBAC scope, and billing entity for the Docker Hub environment.
Resource group: for RBAC purposes
Note
Only one subscription can be linked to a Docker Hub environment instance. However, container images from this instance can be deployed to multiple environments protected by Defender for Cloud, outside the boundaries of the associated subscription.
Scanning intervals: Select an interval for scanning the container registry for vulnerabilities.
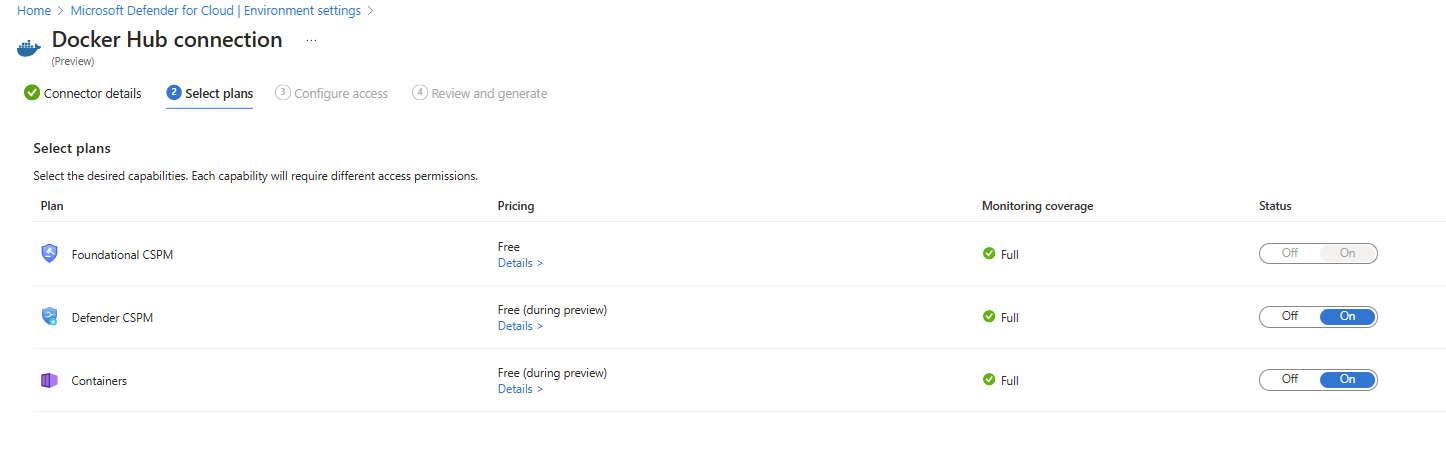
Select Plans
Multiple plans exist for these kinds of environments:
Foundational CSPM: Basic plan available for all customers, provides inventory capabilities only.
Containers: Offers inventory and vulnerability assessment features.
Defender CSPM: Offers inventory and vulnerability assessment features, plus extra capabilities like attack path analysis and code-to-cloud mapping.
For information regarding the plan pricing review Microsoft Defender for Cloud pricing.
Ensure your Docker Hub environment plans are in sync with your cloud environment plans and share the same subscription to maximize coverage.
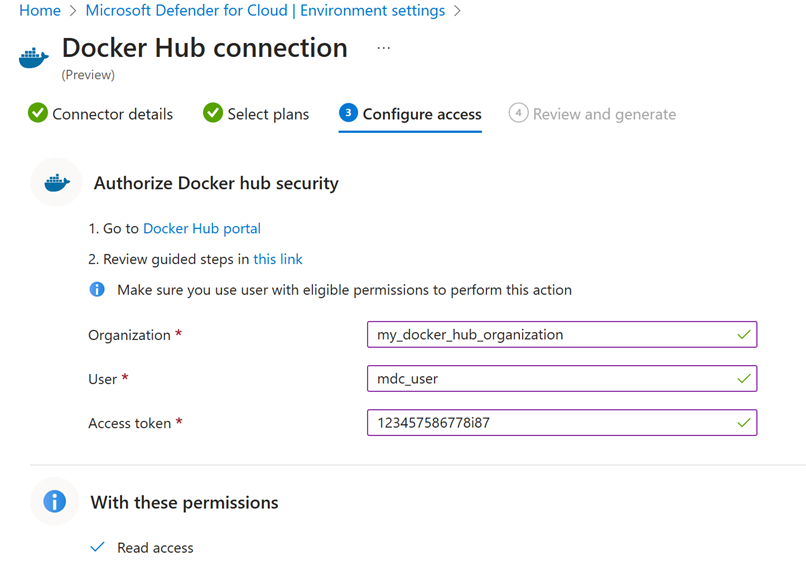
Configure Access
To maintain a continuous and secure link between Defender for Cloud and your Docker Hub organization, ensure you have a dedicated user with an organization email address. Each Docker Hub connector corresponds to one Docker Hub organization. Therefore onboard a separate Docker Hub environment connector in Defender for Cloud for each Docker Hub organization you manage to achieve optimal security coverage for your container software supply chain.
Follow the steps in How to set up Docker Hub as an external registry to prepare your Docker Hub organization account for integration.
Provide these parameters from your Docker Hub user to establish a connection.
Organization: Docker Hub organization name
User: Assigned Docker Hub username
Access token: Docker Hub user read-only access token
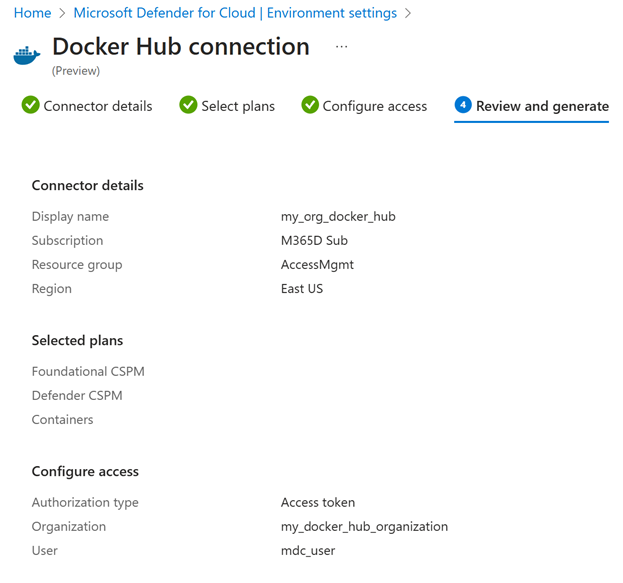
Review and generate
Review all the configured connector details before onboarding finalization.
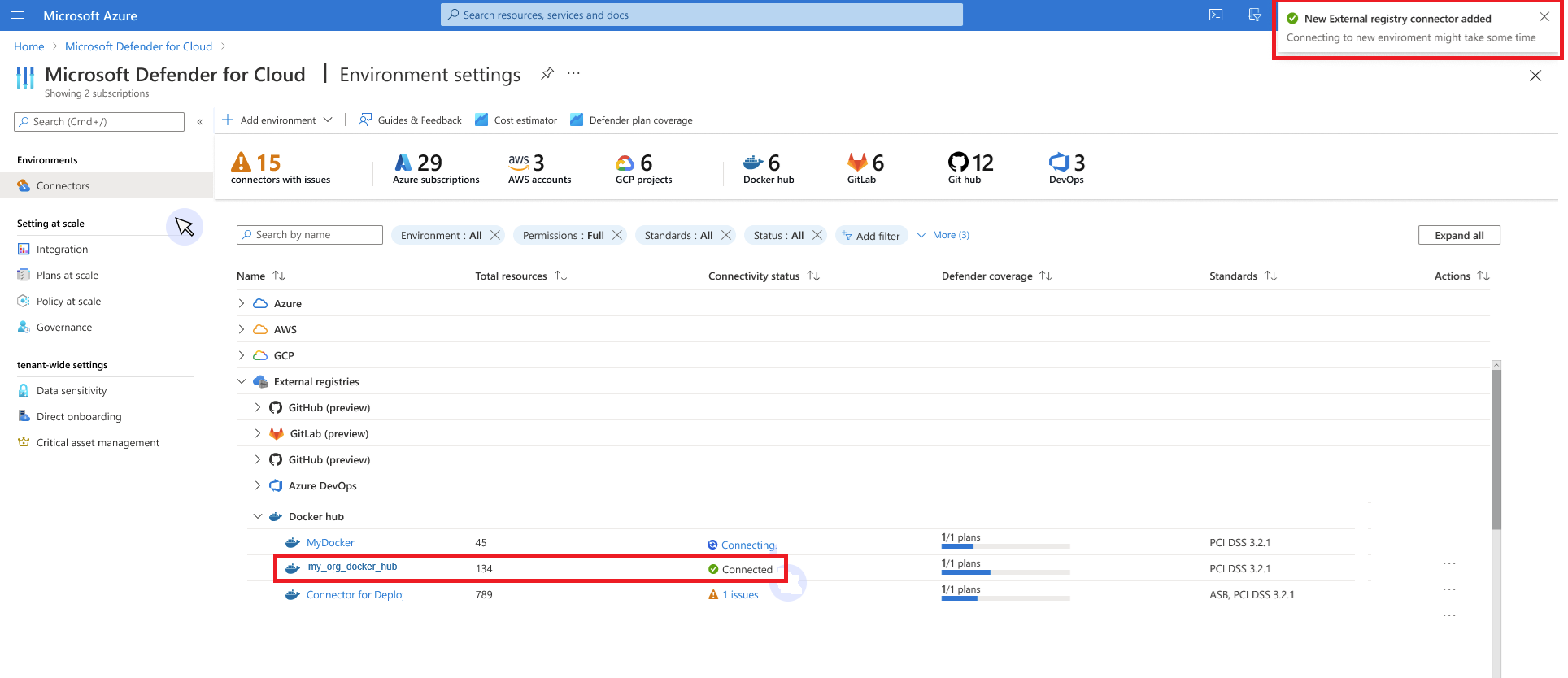
Validate connectivity
Verify the connection is successful and displays "Connected" on the environment's settings screen.
Validate feature capabilities
Docker Hub initiates container registry scanning within one hour after onboarding:
Inventory – Make sure your Docker Hub connector and its security status appear in the Inventory view.
Vulnerability Assessment – Ensure you receive the recommendation "(Preview) Container images in Docker Hub registry should have vulnerability findings resolved" for addressing security issues in your Docker Hub container images.