Hi @Adam Day
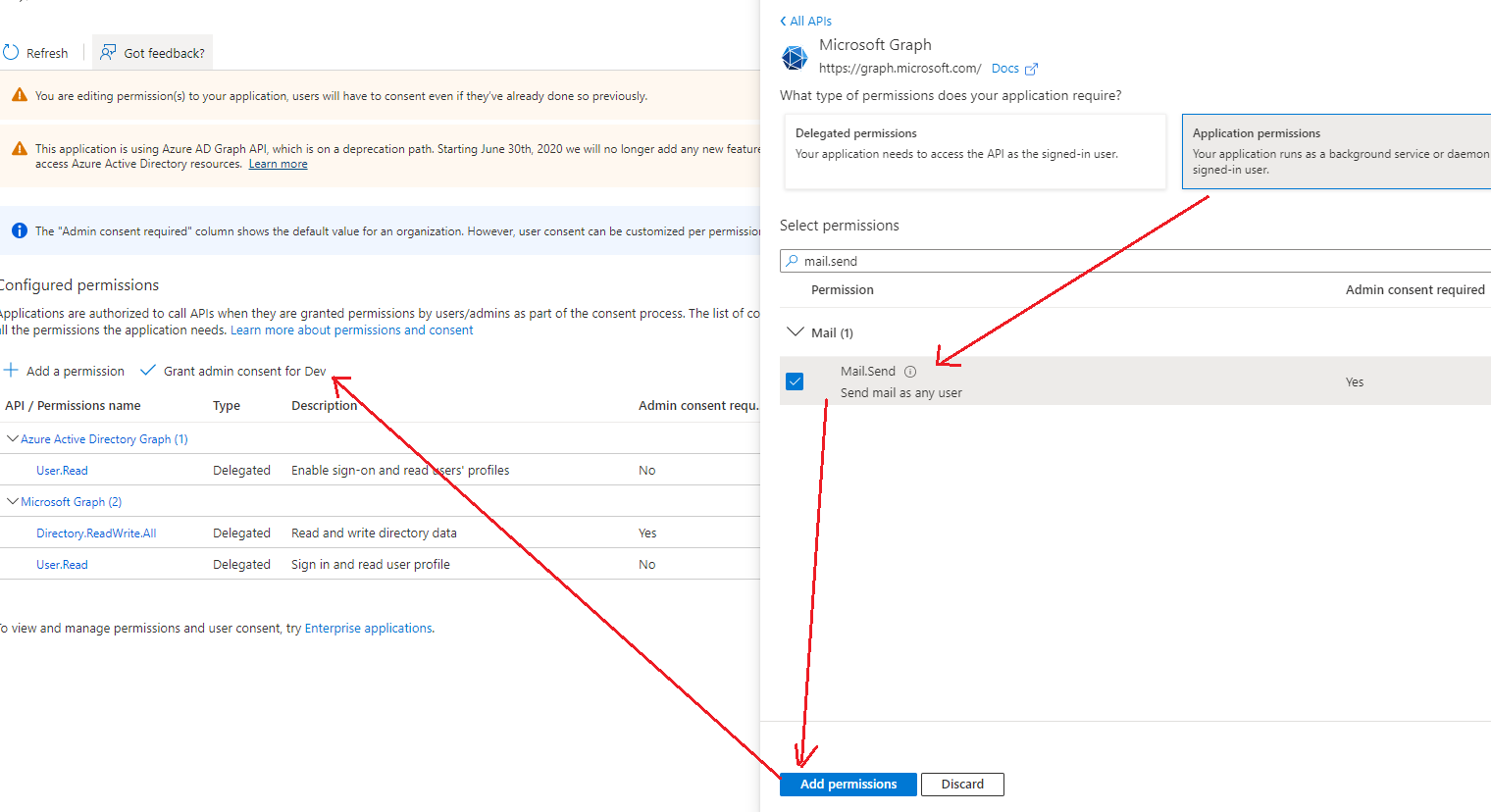
The delegated Mail.Send permission certainly cannot be used as a background service. Delegated permissions are usually used in scenarios that require user interaction, and are not suitable for daemons.
Server-to-server interactions are only supported with application permissions. So please grant the mail.send application permission to your application, then your application will be able to send emails on behalf of other users without the user logging in.
If the answer is helpful, please click "Accept Answer" and kindly upvote it. If you have extra questions about this answer, please click "Comment".
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.
