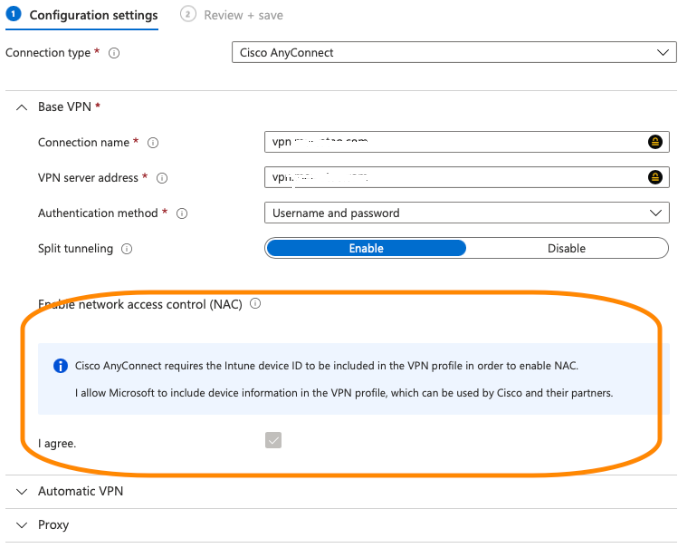
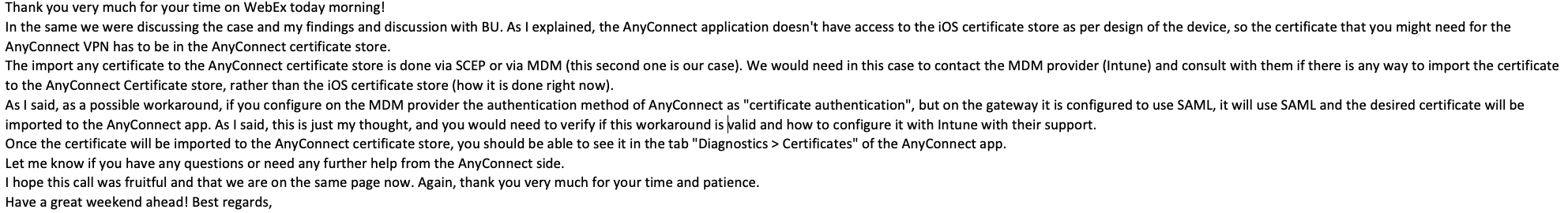
@Advent965 Thanks for explaining your setup, I understand the situation now. In order for me to help you understand where the problem lies I will have to explain you how conditional access work in depth. So here we go :
1) When you enroll a device in Intune (MDM), we do Azure AD registration for that device in AAD and create a device object in AAD that you see in Azure AD Device portal. And at this time Azure AD signs a device certificate which is in name of the Device Public key and is stored in Devices Keychain in IOS.
2) We then pass on the device to Intune service where it follows the enrollment process and gets enrolled into Intune service and depending on the compliance policies created in Intune portal, it evaluates the device and store Device Compliance status - true or false in that Azure AD device Object.
3) When a user tries to sign into any application which is protected by conditional access for devices (compliant, hybrid etc) the Azure AD needs to be aware of the device the user is signing from. For this reason the client needs to send the AAD Device ID to the AAD during sign in so that AAD can do further checks.
4) Different operating system have different Client side brokers for accessing the device certificate from device store and present to the Azure AD. For examples browser will prompt a user to select a certificate as they cannot access the certificate directly under normal scenarios.
5) In your example on IOS, for cisco any connect app to succeed in conditional access, at some point of time it will need to pass that Device ID to Azure AD so that AAD can do further check. But since the Device certificate is stored in keychain where only broker app like MS authenticator can only have access, it is not able to do so. Also, it is the responsibility of the client app to talk to broker app to get the certificate. This process is coded in the client App when they are integrated with MSAL : https://learn.microsoft.com/en-us/azure/active-directory/develop/msal-net-use-brokers-with-xamarin-apps
If the native client like Cisco Any connect app is not coded to perform this step, this is going to fail anyway as there is no way it can get access to that device certificate on its own.
On Android the broker is Company portal App.
Your setup will work fine without conditional access on devices and just with user MFA but will fail if you are checking compliance.
There are many other apps which fail to do so and in that case the client company needs to update their app code to work with Device compliance part.
If CISCO confirms that they have already updated the code to talk to MS Authenticator App on IOS which they can do by following : https://learn.microsoft.com/en-us/azure/active-directory/develop/msal-net-use-brokers-with-xamarin-apps and if it still does not work, I will be happy to escalate the case for you.
Hope you understand where the problem is and trust us we also do not like to keep you hanging in between. Do let us know if you have any questions will be happy to discuss further with you on this.
-----------------------------------------------------------------------------------------------------------------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.