Hello,
Recently I have create a system like below image
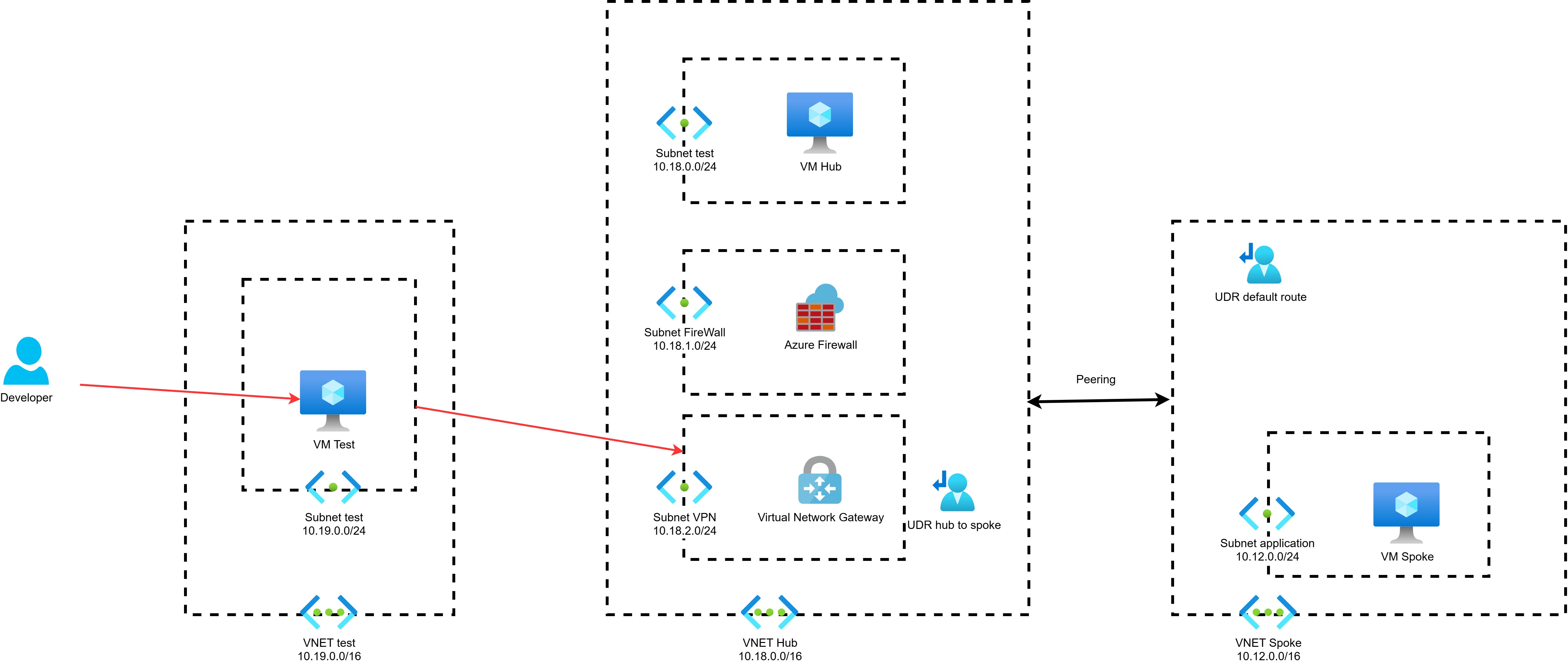
I have config 3 VNET:
- VNET test(10.19.0.0/16) : in this vnet, I config a subnet(10.19.0.0/24) and a test VM (OS window server 2022) with a public IP named publicIPDev. I want to remote to this test VM, then connect VPN Site-to-Site to Hub, then connect remote desktop to VM on VNET Spoke
- VNET hub(10.18.0.0/16): in this vnet, I config 3 subnets:
- Subnet for VPN (10.18.2.0/24): this subnet I also create a VPN Site-to-Site
- Subnet for Firewall(10.18.1.0/24): this subnet I also create a Firewall. The firewall rule configuration is:
- Basic firewall SKU
- Assigned a public IP
- Not enabled Firewall Management NIC
- Use basic firewall policy.
- Create a network rule collection. Select allow. then create a rule like below:
- Name: AllowRDP rule
- Protocol: TCP
- Source type, IP address.
- Source: 10.18.0.0/24. - this is address space of vnetHub
- Destination type,:IP address.
- Destination Address: 10.12.0.0/16. - this is address space of vnetSpoke
- Destination Ports: 3389.
- Subnet for testing(10.18.0.0/24): this subnet I create a VM called VMHub, this VM is just assigned a private IP (10.18.0.4)
- VNET spoke(10.12.0.0/16): This subnet I config a subnet(10.12.0.0/24). In this subnet, I also create a VM called VMSpoke, this VM is just assigned a private IP (10.12.0.4)
VNET hub and VNET spoke is also peer. I follow instruction to create peering in this link https://learn.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-peering-gateway-transit
I also config 2 route table:
- A route table UDR hub to spoke, I set as below
- I set a route with below config:
- Destination type: IP addresses
- Destination IP addresses/CIDR range: 10.12.0.0/16 - this is Vnet spoke address space
- Next hop type: Virtual appliance
- Next hop address: Firewall's private IP
- Attach to Subnet for VPN (10.18.2.0/24)
- A route table UDR default route. I understand that this default route will allow outbound traffic for VM in Vnet Spoke. I set as below
- I set a route with below config:
- Destination type: IP addresses
- Destination IP addresses/CIDR range: 0.0.0.0/0
- Next hop type: Virtual appliance
- Next hop address: Firewall's private IP
- Attach to Subnet of Vnet Spoke (10.12.2.0/24)
In test VM, I config and connect successfully to VPN. And from there, I can connect Remote desktop to VMHub via private IP: 10.18.0.4
However, I cannot connect Remote desktop to VMSpoke via private IP: 10.12.0.4.
The VM VMSpoke's port 3389 is opened. When I connect from testVM through VPN to VMHub, in VMHub i can conenct remote desktop to VMSpoke
Please help me to review my configuration
