Describe the bug
Get-MgServicePrincipal doesn't return anything for the AppRoles or OAuth2PermissionGrants, despite the SP having both Delegated and App Perms assigned.
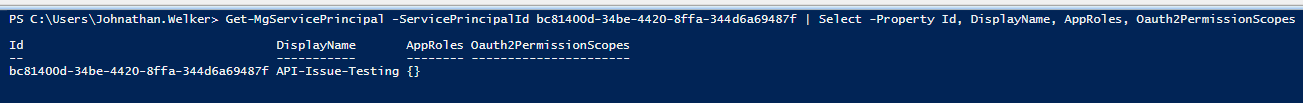
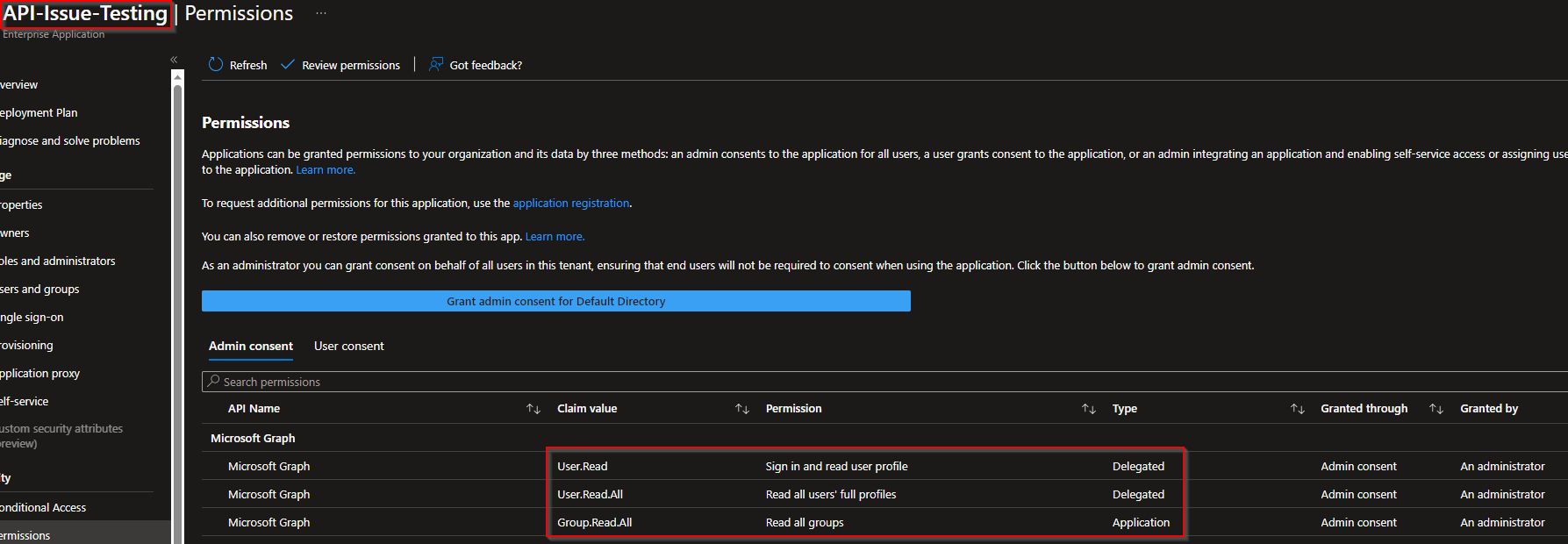
I am a Global Administrator, so I don't suspect a permission issue, especially since the rest of the object returns ok. I have run into this issue in several tenants. I also get this issue If I use the associated API as the documentation states here
Expected behavior
Per this documentation, I would expect a similar response object as the one below:
Welcome To Microsoft Graph!
Azure AD Graph service principal object and its supported permissions:
Application permissions:
AllowedMemberTypes : {Application}
Description : Allows the app to read applications and service principals without a signed-in user
DisplayName : Read all applications
Id : 3afa6a7d-9b1a-42eb-948e-1650a849e176
IsEnabled : True
Origin : Application
Value : Application.Read.All
AdditionalProperties : {}
Delegated permissions:
AdminConsentDescription : Allows users to sign in to the app, and allows the app to read the profile of signed-in users. It also allow the app to read basic company information of signed-in users.
AdminConsentDisplayName : Sign in and read user profile
Id : 311a71cc-e848-46a1-bdf8-97ff7156d8e6
IsEnabled : True
Origin :
Type : User
UserConsentDescription : Allows you to sign in to the app with your work account and let the app read your profile. It also allows the app to read basic company information.
UserConsentDisplayName : Sign you in and read your profile
Value : User.Read
AdditionalProperties : {}
Debug Output
No results to share here, as it is not returning anything at all. No errors.
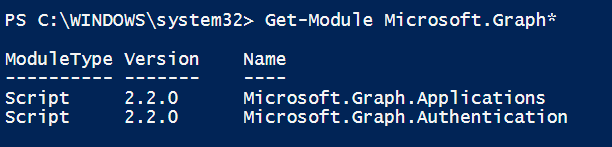
Module Version
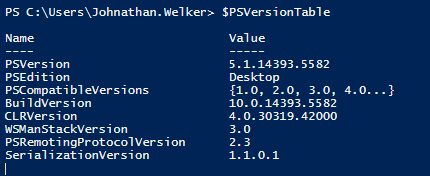
Environment Data
Screenshots
Inserted above
Additional context
For what it's worth, I'm able to return the data using Get-MgServicePrincipalAppRoleAssignment (mostly, still looking for how to return displayNames for the app perms) and Get-MgServicePrincipalOauth2PermissionGrant, but the object supposedly returned by Get-MgServicePrincipal is much easier to work with and saves me from having to make a second call. Any help is appreciated. Thanks.
