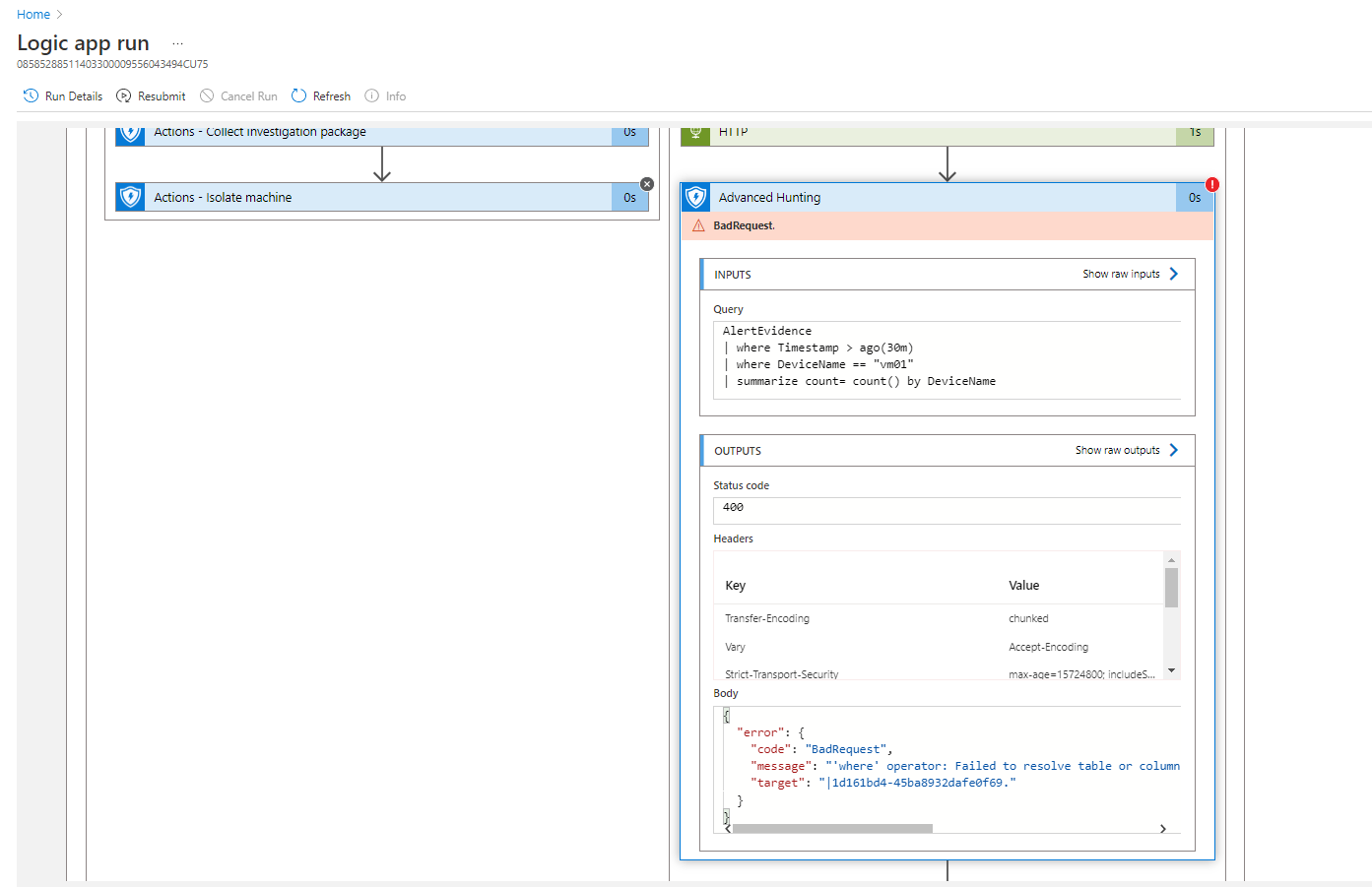
Apparently, I did find the answer to this. The answer secondarily is MS' Poor Documentation. The actual answer.
The tables AlertEvidence AND AlertInfo are new tables that broke down from DeviceAlertEvents which was their old API I guess. But apparently, the MDEATP connector still supports the old one. So to correct this, your new query would be
DeviceAlertEvents | where ... etc