Connect to Azure with a private path for SQL Server enabled by Azure Arc
This article describes how to configure communication for a SQL Server enabled by Azure Arc instance so that it connects to Azure without going over internet paths.
This design deploys forward proxy servers in Azure to allow SQL Server to communicate over a site-to-site VPN or ExpressRouteConnection with private IP addresses. The proxies communicate with Arc URLs over the Azure backbone network.
Important
This implementation uses Azure Firewall Explicit proxy - which is currently available in preview.
The following diagram represents this pattern.
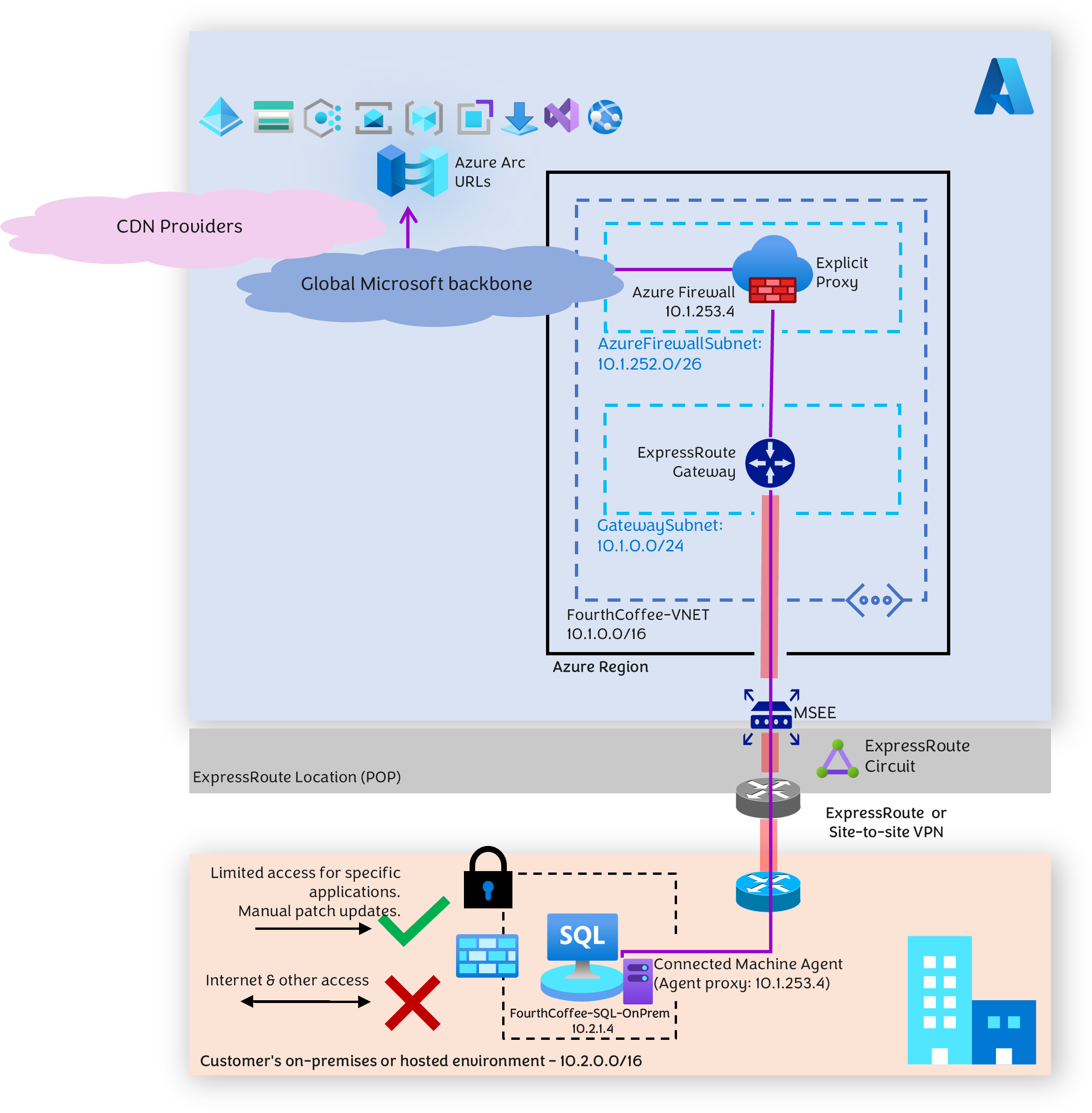
For the forward proxy, choose either:
Azure Firewall Explicit proxy (preview) feature, which is a Platform as a Service (PaaS) network security Service.
Or
A third-party proxy Network Virtual Appliance (NVA).
The diagram shows Azure Firewall Explicit proxy.
Use case
Use this architecture for SQL Server enabled by Azure Arc when:
The SQL Server instance is isolated and protected.
Azure Connected Machine agent can only communicate with a forward proxy over a private IP hosted within your Virtual Network in Azure. The URLs and public IPs that the forward proxy communicates with, for accessing Arc-related URLs, are within the Microsoft backbone, not over the internet. Therefore, traffic doesn't go over the public internet.
Traffic between the SQL Server instance and the forward proxy has to be secure. In the previous diagram, ExpressRoute is depicted for connectivity between the SQL server and the forward proxy, but it can also be achieved using a site-to-site VPN.
The traffic traverses over ExpressRoute's private peering rather than public peering.
The proxy configuration is performed within the Arc Connected Machine agent and not at the OS level. This configuration might not affect your security-related policies.
Arc communication is encrypted over port 443, and employing ExpressRoute or site-to-site VPN adds an additional layer of security.
Prerequisite - An Azure virtual network with two subnets
This architecture requires a virtual network in Azure with two subnets. The following steps prepare for site-to-site VPN instead of ExpressRoute.
- Create a virtual network and subnet for the Azure VPN gateway.
- Create a separate subnet for Azure Firewall.
A later step deploys Azure Firewall as a forward proxy.
Create a VPN between the SQL Server and Azure
Create a site-to-site VPN from your SQL Server location to Azure.
Follow the steps at Tutorial: Create and manage a VPN gateway using the Azure portal to create VPN Gateway.
Create a Local Network Gateway before creating a Site 2 Site VPN. Follow the steps at Tutorial: Create a site-to-site VPN connection in the Azure portal.
Create firewall and configure the proxy
- Create an Azure Firewall along with Firewall Manager.
- Configure Azure Firewall Explicit proxy (preview) setting to act as forward proxy.
- Create a rule to allow the SQL Server IP (
10.2.1.4).
The Azure Connected Machine agent uses that rule to access https outbound through the firewall.
Connect SQL server using Azure Arc
From Azure portal, generate an onboarding script. As explained here, Connect your SQL Server to Azure Arc.
Run the script to install the Azure Connected Machine agent with the correct configurations. You can configure the proxy settings when you generate your script.
In this article, we update the private path proxy settings after we install the Arc Connected Machine agent extension.
Configure Azure Connected Machine agent
To configure Azure Connected Machine agent, use azcmagent CLI:
Set the proxy URL
azcmagent config set proxy.url "http://<ip address>:8443"Verify proxy URL
azcmagent config get proxy.urlThe console returns the current proxy URL.
Verify agent is connected.
azcmagent show | find | "Agent Status"The console returns the agent status. If the agent is configured the console returns:
Agent Status: Connected
Bypass URLs
You might need to configure the agent to bypass certain URLs from going through the proxy, and instead allow direct access. Proxy URL bypass if you need to support private endpoints. For more information, review Proxy bypass for private endpoints.
Configure firewall for log analytics
You can also configure the firewall to send its logs to Azure Log Analytics. For details, review Monitor Azure Firewall.
Clean up resources
If you're not going to continue to use this application, delete these resources.
To delete the resources from Azure portal:
- Enter the name of your resource group in the search box select it from the search results.
- Select Delete resource group.
- Confirm the resource group name at Type the resource group name, and select Delete.