Share insider risk management data with other solutions
Important
Microsoft Purview Insider Risk Management correlates various signals to identify potential malicious or inadvertent insider risks, such as IP theft, data leakage, and security violations. Insider risk management enables customers to create policies to manage security and compliance. Built with privacy by design, users are pseudonymized by default, and role-based access controls and audit logs are in place to help ensure user-level privacy.
You can share data from insider risk management in either of the following ways:
- Export alert information to SIEM solutions
- Share user risk severity levels with Microsoft Defender XDR and Microsoft Purview data loss prevention (DLP) alerts
Export alert information to SIEM solutions
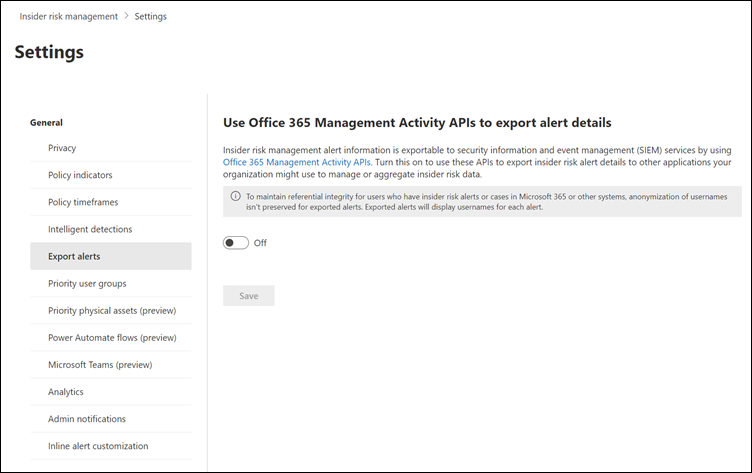
Microsoft Purview Insider Risk Management alert information is exportable to security information and event management (SIEM) and security orchestration automated response (SOAR) solutions by using the Office 365 Management Activity API schema. You can use the Office 365 Management Activity APIs to export alert information to other applications your organization may use to manage or aggregate insider risk information. Alert information is exported and available every 60 minutes via the Office 365 Management Activity APIs.
Tip
Get started with Microsoft Security Copilot to explore new ways to work smarter and faster using the power of AI. Learn more about Microsoft Security Copilot in Microsoft Purview.
If your organization uses Microsoft Sentinel, you can also use the out-of-the-box insider risk management data connector to import insider risk alert information to Sentinel. For more information, see Insider Risk Management in the Microsoft Sentinel article.
Important
To maintain referential integrity for users who have insider risk alerts or cases in Microsoft 365 or other systems, anonymization of usernames isn't preserved for exported alerts when using the exporting API or when exporting to Microsoft Purview eDiscovery solutions. Exported alerts will display usernames for each alert in this case. If you're exporting to CSV files from alerts or cases, anonymization is preserved.
Use the APIs to review insider risk alert information
Select the appropriate tab for the portal you're using. Depending on your Microsoft 365 plan, the Microsoft Purview compliance portal is retired or will be retired soon.
To learn more about the Microsoft Purview portal, see Microsoft Purview portal. To learn more about the Compliance portal, see Microsoft Purview compliance portal.
- Sign in to the Microsoft Purview portal using credentials for an admin account in your Microsoft 365 organization.
- Select Settings in the upper-right corner of the page.
- Select Insider Risk Management to go to the insider risk management settings.
- Select Export alerts. By default, this setting is disabled for your Microsoft 365 organization.
- Turn the setting to On.
- Filter the common Office 365 audit activities by SecurityComplianceAlerts.
- Filter SecurityComplianceAlerts by the InsiderRiskManagement category.
Alert information contains information from the Security and Compliance Alerts schema and the Office 365 Management Activity API common schema.
The following fields and values are exported for insider risk management alerts for the Security and Compliance Alerts schema:
| Alert parameter | Description |
|---|---|
| AlertType | Type of the alert is Custom. |
| AlertId | The GUID of the alert. Insider risk management alerts are mutable. As alert status changes, a new log with the same AlertID is generated. This AlertID can be used to correlate updates for an alert. |
| Category | The category of the alert is InsiderRiskManagement. This category can be used to distinguish from these alerts from other security and compliance alerts. |
| Comments | Default comments for the alert. Values are New Alert (logged when an alert is created) and Alert Updated (logged when there's an update to an alert). Use the AlertID to correlate updates for an alert. |
| Data | The data for the alert includes the unique user ID, user principal name, and date and time (UTC) when user was triggered into a policy. |
| Name | Policy name for insider risk management policy that generated the alert. |
| PolicyId | The GUID of the insider risk management policy that triggered the alert. |
| Severity | The severity of the alert. Values are High, Medium, or Low. |
| Source | The source of the alert. The value is Office 365 Security & Compliance. |
| Status | The status of the alert. Values are Active (Needs Review in insider risk), Investigating (Confirmed in insider risk), Resolved (Resolved in insider risk), Dismissed (Dismissed in insider risk). |
| Version | The version of the Security and Compliance Alerts schema. |
The following fields and values are exported for insider risk management alerts for the Office 365 Management Activity API common schema.
- UserId
- Id
- RecordType
- CreationTime
- Operation
- OrganizationId
- UserType
- UserKey
Share alert severity levels with other Microsoft security solutions
You can share alert severity levels from insider risk management to bring unique user context to alert investigation experiences in the following Microsoft security solutions:
Microsoft Defender XDR Microsoft Purview Communication Compliance Microsoft Purview data loss prevention (DLP)
Insider risk management analyzes user activities over a period of 90-120 days and looks for anomalous behavior over that period of time. Adding this data to other security solutions enhances the data available in those solutions to help analysts prioritize alerts.
Tip
Alert severity levels in insider risk management are different from insider risk levels that are defined in Adaptive Protection.
- Alert severity levels (Low, Medium, or High) are assigned to users based on activity detected in insider risk management policies. These levels are calculated based on alert risk scores assigned to all active alerts associated with the user. These levels help insider risk analysts and investigators prioritize and respond to user activity accordingly.
- Insider risk levels (Elevated, Moderate, or Minor) in Adaptive Protection are a measure of risk determined by admin-defined conditions such as the number of exfiltration activities users perform in a day or whether their activity generated a high-severity insider risk alert.
What happens when you share insider risk management alert severity levels?
In Microsoft Defender XDR
DLP Incidents page: An Insider risk severity field is added to the Impacted assets section of the Microsoft Defender DLP Incidents page for users that have a High or Medium risk level in insider risk management. If the user has a Low risk level, nothing is added to the Incidents page. This keeps distractions to a minimum for analysts so they can focus on the riskiest user activities.
You can select the risk level in the Impacted assets section to see an insider risk activity summary and activity timeline for that user. Having up to 120 days of analysis can help the analyst determine the overall riskiness of the user's activities.
If you select the DLP event in the DLP policy match page, an Impacted entities section appears in the DLP policy match section that shows all users that match the policy.
Users page: An Insider risk severity field is added to the Users page for users that have a High, Medium, or Low risk level in insider risk management. This data is available for any users with an active insider risk management alert.
An insider risk activity summary and activity timeline for that user appears on the right side of the Users page.
In communication compliance alerts
For every communication compliance policy match, you can view the user risk severity associated with the sender. View this information on the User activity tab in communication for the alert. This view provides risk profile, policy matches, and user activities captured by insider risk management and communication compliance.
The severity levels are categorized as High, Medium, Low, or None.
For risk severity levels of None, the reason may be for any of the following scenarios:
- The user isn't included in an insider risk policy.
- The user's activities aren't assigned a risk score, meaning the user isn't in the active scope for the policy.
- The user is included in an insider risk management policy, but hasn't engaged in any risky activity.
- The organization doesn't have an active insider risk management policy.
If the user risk severity isn't available, data sharing isn't enabled from insider risk management.
You can view insider risk activities for up to 120 days in the View Details section on the User history tab in insider risk management. Currently, only data from exfiltration indicators are shown in the user activity summary in communication compliance.
In DLP alerts
For the insider risk management policy that's associated with the DLP alert, an Insider risk severity column with values of High, Medium, Low, or None is added to the DLP alerts queue. If there are multiple users that have activities that match the policy, the user with the highest insider risk level is displayed.
A value of None can mean either of the following:
The user isn't part of any insider risk management policy.
The user is part of an insider risk management policy, but they haven't done risky activities to bring themselves into the scope of the policy (there's no exfiltration data).
You can select the insider risk level in the DLP alerts queue to access the User activity summary tab, which shows a timeline of all exfiltration activities for that user for the past 90-120 days. Like the DLP alerts queue, the User activity summary tab shows the user with the highest insider risk level. This deep context into what a user has done over the past 90 to 120 days provides a wider view of the risks presented by that user.
Only data from exfiltration indicators are shown in the user activity summary. Data from other sensitive indicators, such as HR, browsing, and so on, aren't shared with DLP alerts.
An Actor details section is added to the DLP Alert details page. You can use this page to see all users involved in the specific DLP alert. For each user involved in the DLP alert, you can view all the exfiltration activities for the past 90 to 120 days.
If you select Get a summary from Security Copilot in a DLP alert, the alert summary provided by Microsoft Security Copilot includes the insider risk management severity level in addition to the DLP summary info, if the user is in scope of an insider risk management policy.
Tip
You can also use Security Copilot to investigate DLP alerts. If the insider risk management Data sharing setting is turned on, you can then do a combined DLP/insider risk management investigation. For example, you might want to start by asking Copilot to summarize a DLP alert, and then ask Copilot to show the insider risk level associated with the user flagged in the alert. Or you might want to ask why the user is considered a high-risk user. The user risk information in this case comes from insider risk management. Security Copilot seamlessly integrates insider risk management with DLP to assist with investigations. Learn more about using the standalone version of Copilot for combined DLP/insider risk management investigations.
Prerequisites
To share insider risk management user risk levels with other Microsoft security solutions, the user:
- Must be part of an insider risk management policy.
- Must have performed exfiltration activities that bring the user into the scope of the policy.
- (For sharing with DLP): Must have DLP alert permissions. After the Data sharing setting is turned on, users with DLP alert permissions can access insider risk management context for DLP alert investigation and for the Microsoft Defender XDR Users page. Users with insider risk management permissions can also access this data.
- (For sharing with communication compliance): Users must be assigned either the Communication Compliance Analyst or Communication Compliance Investigator roles to view user risk severity levels and activity history in communication compliance.
Tip
If you have access to DLP alerts in Microsoft Purview and/or Microsoft Defender, you can view user context from insider risk management shared with those solutions.
Share data with other Microsoft security solutions
You can share insider risk management alert severity levels with other Microsoft security solutions by turning on a single setting.
- In insider risk management settings, select the Data sharing setting.
- Under the Sharing data with other Microsoft security solutions section, turn on the setting.
Note
If you don't turn this setting on, the value displayed in the DLP alerts Insider risk severity column is "User data is not available" and is displayed as "Insider Risk Activity not available" in communication compliance.