Secure by default with Microsoft Purview and protect against oversharing
Microsoft Purview sensitivity labeling provides an efficient and robust capability to protect data. This protection is centered around encrypting your data and preventing oversharing. Labels can then be used as conditions in other solutions such as Microsoft Purview Data Loss Prevention (DLP) and Microsoft Purview Insider Risk Management.
The traditional 'crawl-walk-run' approach is often challenging or slow to adopt due to:
- Defining the label taxonomy
- Concerns about encryption affecting end users and line of business applications
- Limited adoption through manual labeling and/or only using auto-labeling to label
In this guide, we provide a deployment model focusing on a different approach. We show how to:
- Configure secure by default sensitivity labeling.
- Use label publishing defaults and auto-labeling in the Office client.
- Use contextual defaults in SharePoint sites to rapidly achieve deployment velocity.
When you derive Teams and SharePoint site labeling to file labels, you can reach high labeling volumes with limited end user interactions. This will also achieve a measured approach that helps overcome traditional challenges.
Tip
Securing by default by deriving labels from SharePoint sites, your organization can quickly reduce the risk associated with unintentional and intentional oversharing. Training end users on how to manage exceptions, instead of when to protect, helps accelerate adoption velocity.
Before you begin
This guide is for administrators with knowledge of Microsoft Purview Information Protection, DLP, and Insider Risk Management. If you're new to Purview, refer to these articles to learn more about Purview:
This guide includes the following articles:
- Introduction (this page)
- Phase 1: Foundational – Start with default labeling
- Phase 2: Managed – Address files with highest sensitivity
- Phase 3: Optimized – Expand to your entire Microsoft 365 data estate
- Phase 4: Strategic – Operate, expand, and retroactive actions
These articles cover:
- A focus on the required solutions to only meet the goal of a model’s scenario.
- The starting point for your deployment, recommended by the engineering team.
- High level activities and deployment tips to help you plan an implementation.
- A solid foundation to grow on and augment with more scenarios.
These articles won't cover:
- A complete project plan
- A deep dive technical reference (however, this guide contains links to several articles on Microsoft Learn for additional information)
- Comprehensive guides for all solutions in Microsoft Purview
Licensing and Subscriptions
See the Microsoft 365 guidance for security & compliance for details on the subscriptions that support the features you're deploying from this guide:
- Sensitivity Labels (auto-labeling and default library labeling in SharePoint)
- Data Loss Prevention
- Insider Risk Management (adaptive protection)
For information on licensing, see Microsoft 365, Office 365, Enterprise Mobility + Security, and Windows 11 Subscriptions for Enterprises.
Simplify your deployment strategy with the following actions
- Secure by default and protect information to All employees (and users within your identity ecosystem).
- Derive file labels from site (container) labels to quickly reach scale.
- Train users to update labels for sharing exceptions (instead of when to protect).
- Auto-labeling is for higher sensitivity recommendations and more restriction.
- Accelerate Data Loss Prevention deployment to restrict sharing of labeled content.
- Insider Risk Management to identify suspicious user labeling and sharing behaviors (intentional and unintentional).
Why labeling matters in protecting your content?
- Protection travels with your document – Easy to use encryptions for all users
- Simple, integrated, and consistent – Built-in Office, Acrobat Reader, Teams, Power BI, Defender for Cloud Apps, and more
- Copilot – End-to-end protection of sensitive information with Copilot interactions
- Protection beyond Microsoft 365 – Protect data assets in Azure, Amazon Web Services (AWS), and more
Purview deployment blueprint
The blueprint provides:
- a recommended label taxonomy to get your organization started
- options for end users to manage exceptions, if encryption prevents them from working effectively
- help to enable your organization to augment its data security rapidly
It’s important to review and adapt this blueprint based on your existing deployment, data security objectives, and experience. There are more options to help you deploy in stages. You're in complete control of your deployment experience.
Note
This blueprint is closely aligned with how Microsoft deployed internally. Learn more about Microsoft labeling deployment at: Empowering employee self-service with guardrails: How we’re using sensitivity labels to make Microsoft more secure - Inside Track Blog
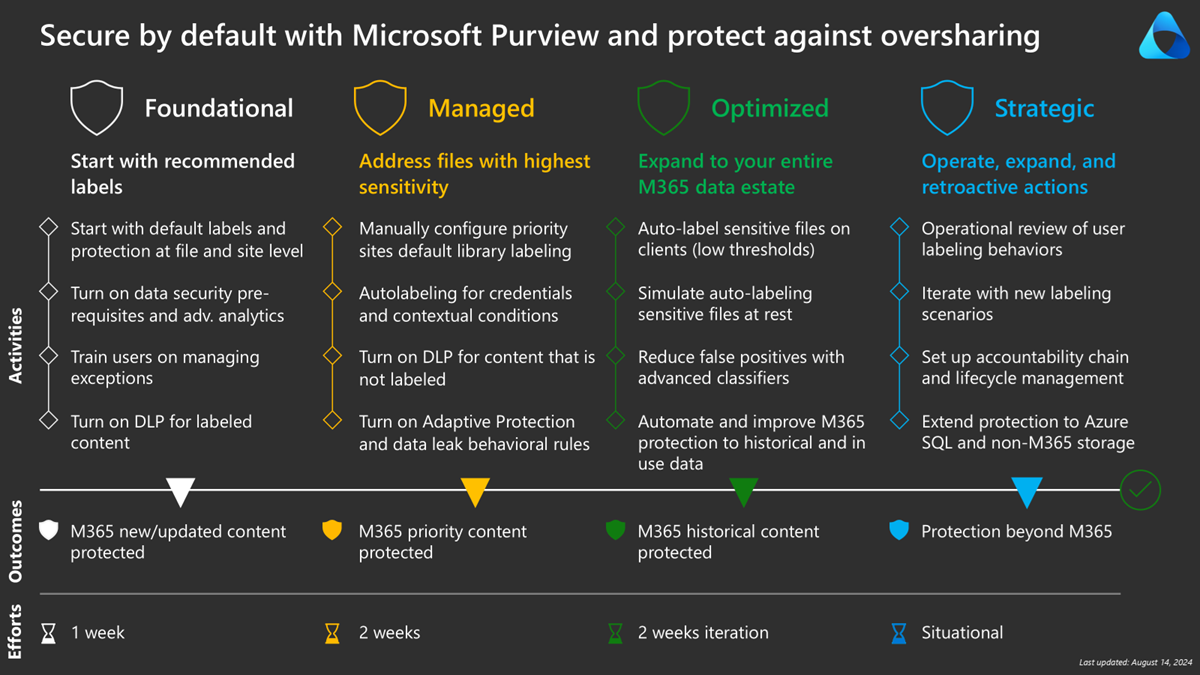
Articles on Phases 1-4 will provide more details. Begin with Phase 1: Foundational – Start with default labeling