Connect to Microsoft Azure
TFS 2017
Note
In Microsoft Team Foundation Server (TFS) 2018 and previous versions, build and release pipelines are called definitions, runs are called builds, service connections are called service endpoints, stages are called environments, and jobs are called phases.
To deploy your app to an Azure resource (to an app service or to a virtual machine), you need an Azure Resource Manager service connection.
For other types of connection, and general information about creating and using connections, see Service connections for builds and releases.
Create an Azure Resource Manager service connection with an existing service principal
If you want to use a predefined set of access permissions, and you don't already have a suitable service principal defined, follow one of these tutorials to create a new service principal:
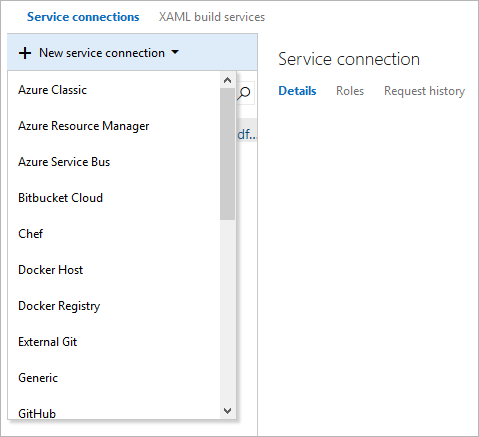
In Azure DevOps, open the Service connections page from the project settings page. In TFS, open the Services page from the "settings" icon in the top menu bar.
Choose + New service connection and select Azure Resource Manager.
Choose Service Principal (manual) option and enter the Service Principal details.
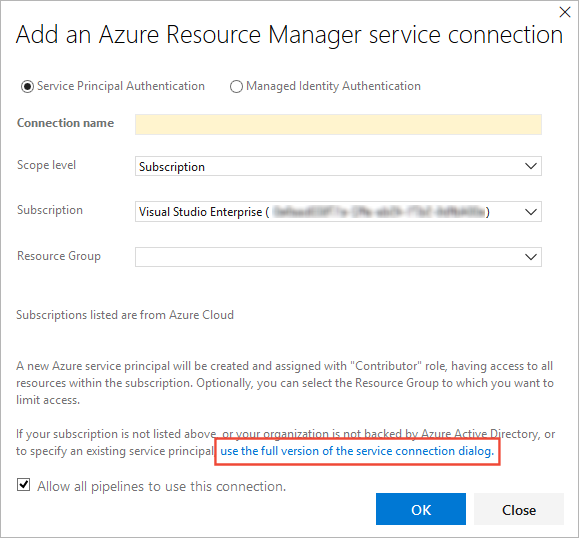
Enter a user-friendly Connection name to use when referring to this service connection.
Select the Environment name (such as Azure Cloud, Azure Stack, or an Azure Government Cloud).
If you do not select Azure Cloud, enter the Environment URL. For Azure Stack, this will be something like
https://management.local.azurestack.externalSelect the Scope level you require:
- If you choose Subscription, select an existing Azure subscription. If you don't see any Azure subscriptions or instances, see Troubleshoot Azure Resource Manager service connections. |
- If you choose Management Group, select an existing Azure management group. See Create management groups. |
Enter the information about your service principal into the Azure subscription dialog textboxes:
- Subscription ID
- Subscription name
- Service principal ID
- Either the service principal client key or, if you have selected Certificate, enter the contents of both the certificate and private key sections of the *.pem file.
- Tenant ID
You can obtain this information if you don't have it to hand by downloading and running this PowerShell script in an Azure PowerShell window. When prompted, enter your subscription name, password, role (optional), and the type of cloud such as Azure Cloud (the default), Azure Stack, or an Azure Government Cloud.
Choose Verify connection to validate the settings you entered.
After the new service connection is created:
- If you are using it in the UI, select the connection name you assigned in the Azure subscription setting of your pipeline.
- If you are using it in YAML, copy the connection name into your code as the azureSubscription value.
If required, modify the service principal to expose the appropriate permissions. For more details, see Use Role-Based Access Control to manage access to your Azure subscription resources. This blog post also contains more information about using service principal authentication.
See also: Troubleshoot Azure Resource Manager service connections.
Create an Azure Resource Manager service connection to a VM with a managed service identity
Note
You are required to use a self-hosted agent on an Azure VM in order to use managed service identity
You can configure Azure Virtual Machines (VM)-based agents with an Azure Managed Service Identity in Azure Active Directory (Azure AD). This lets you use the system assigned identity (Service Principal) to grant the Azure VM-based agents access to any Azure resource that supports Azure AD, such as Key Vault, instead of persisting credentials in Azure DevOps for the connection.
In Azure DevOps, open the Service connections page from the project settings page. In TFS, open the Services page from the "settings" icon in the top menu bar.
Choose + New service connection and select Azure Resource Manager.

Select the Managed Identity Authentication option.
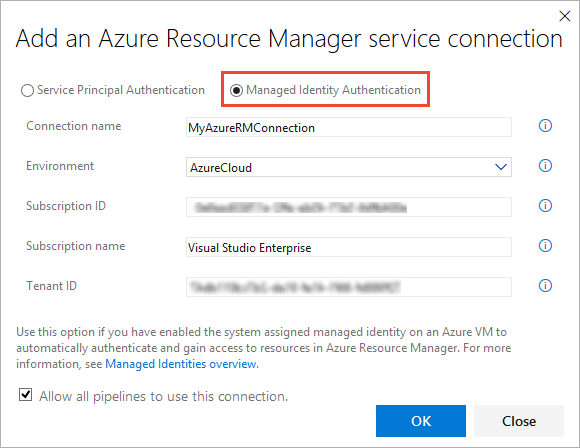
Enter a user-friendly Connection name to use when referring to this service connection.
Select the Environment name (such as Azure Cloud, Azure Stack, or an Azure Government Cloud).
Enter the values for your subscription into these fields of the connection dialog:
- Subscription ID
- Subscription name
- Tenant ID
After the new service connection is created:
- If you are using it in the UI, select the connection name you assigned in the Azure subscription setting of your pipeline.
- If you are using it in YAML, copy the connection name into your code as the azureSubscription value.
Ensure that the VM (agent) has the appropriate permissions. For example, if your code needs to call Azure Resource Manager, assign the VM the appropriate role using Role-Based Access Control (RBAC) in Azure AD. For more details, see How can I use managed identities for Azure resources? and Use Role-Based Access Control to manage access to your Azure subscription resources.
See also: Troubleshoot Azure Resource Manager service connections.
Connect to an Azure Government Cloud
For information about connecting to an Azure Government Cloud, see:
Connect to Azure Stack
For information about connecting to Azure Stack, see: