Step 2. Deploy attack detection and response
As a strongly recommended initial step for ransomware attack detection and response in your Microsoft 365 tenant, set up a trial environment to evaluate the features and capabilities of Microsoft Defender XDR.
For additional information, see these resources.
| Feature | Description | Where to start | How to use it for detection and response |
|---|---|---|---|
| Microsoft Defender XDR | Combines signals and orchestrates capabilities into a single solution. Enables security professionals to stitch together threat signals and determine the full scope and impact of a threat. Automates actions to prevent or stop the attack and self-heal affected mailboxes, endpoints, and user identities. |
Get started | Incident response |
| Microsoft Defender for Identity | Identifies, detects, and investigates advanced threats, compromised identities, and malicious insider actions directed at your organization through a cloud-based security interface uses your on-premises Active Directory Domain Services (AD DS) signals. | Overview | Working with the Microsoft Defender for Identity portal |
| Microsoft Defender for Office 365 | Safeguards your organization against malicious threats posed by email messages, links (URLs), and collaboration tools. Protects against malware, phishing, spoofing, and other attack types. |
Overview | Threat hunting |
| Microsoft Defender for Endpoint | Enables detection and response to advanced threats across endpoints (devices). | Overview | Endpoint detection and response |
| Microsoft Entra ID Protection | Automates detection and remediation of identity-based risks and investigation of those risks. | Overview | Investigate risk |
| Microsoft Defender for Cloud Apps | A cloud access security broker for discovery, investigation, and governance across all your Microsoft and third-party cloud services. | Overview | Investigate |
Note
All of these services require Microsoft 365 E5 or Microsoft 365 E3 with the Microsoft 365 E5 Security add-on.
Use these services to detect and respond to the following common threats from ransomware attackers:
Credential theft
- Microsoft Entra ID Protection
- Defender for Identity
- Defender for Office 365
Device compromise
- Defender for Endpoint
- Defender for Office 365
Escalation of privilege
- Microsoft Entra ID Protection
- Defender for Cloud Apps
Malicious app behavior
- Defender for Cloud Apps
Data exfiltration, deletion, or uploading
- Defender for Office 365
- Defender for Cloud Apps with anomaly detection policies
The following services use Microsoft Defender XDR and its portal (https://security.microsoft.com) as a common threat collection and analysis point:
- Defender for Identity
- Defender for Office 365
- Defender for Endpoint
- Defender for Cloud Apps
Microsoft Defender XDR combines threat signals into alerts and connected alerts into an incident so that your security analysts can more quickly detect, investigate, and remediate the phases of a ransomware attack.
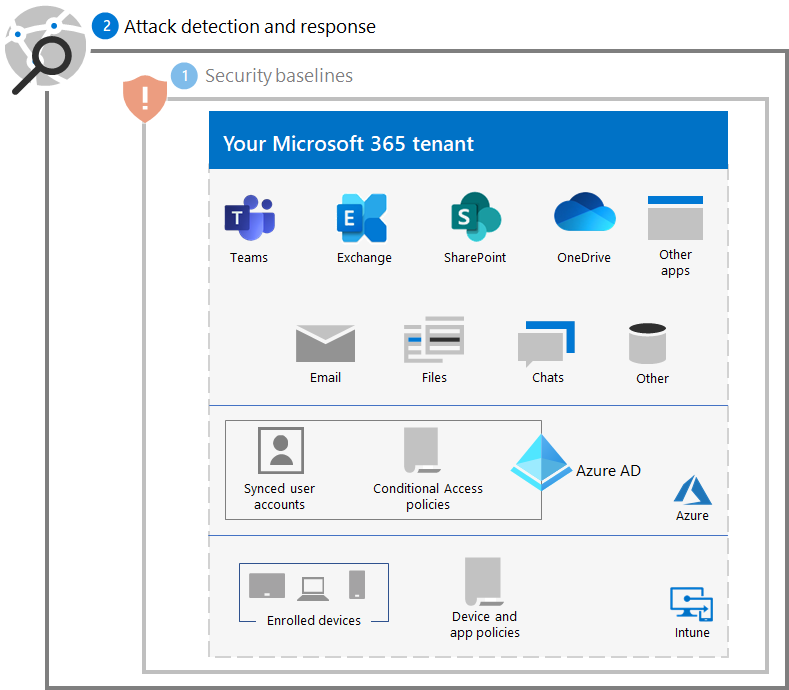
Resulting configuration
Here's the ransomware protection for your tenant for steps 1 and 2.
Next step
Continue with Step 3 to protect the identities in your Microsoft 365 tenant.