How to detect and investigate inactive user accounts
In large environments, user accounts aren't always deleted when employees leave an organization. As an IT administrator, you want to detect and resolve these obsolete user accounts because they represent a security risk.
This article explains a method to handle obsolete user accounts in Microsoft Entra ID.
Note
This article applies only to finding inactive user accounts in Microsoft Entra ID. It doesn't apply to finding inactive accounts in Azure AD B2C.
Prerequisites
- To access the
lastSuccessfulSignInDateTimeproperty using Microsoft Graph, you need a Microsoft Entra ID P1 or P2 license. - You need to grant the app the following Microsoft Graph permissions:
- AuditLog.Read.All
- User.Read.All
- Reports Reader is the least privileged role required to access the activity logs.
- For a full list of roles, see Least privileged role by task.
What are inactive user accounts?
Inactive accounts are user accounts that aren't required anymore by members of your organization to gain access to your resources. One key identifier for inactive accounts is that they haven't been used for a while to sign in to your environment. Because inactive accounts are tied to the sign-in activity, you can use the timestamp of the last time an account attempted to sign in to detect inactive accounts.
The challenge of this method is to define what for a while means for your environment. For example, users might not sign in to an environment for a while, because they are on vacation. You need to consider all legitimate reasons for not signing in to your environment. In many organizations, a reasonable window for inactive user accounts is between 90 and 180 days.
The last sign-in date provides potential insights into a user's continued need for access to resources. It can help with determining if group membership or app access is still needed or could be removed. For external user management, you can determine if an external user is still active within the tenant or should be removed.
How to find and investigate inactive user accounts
You can use the Microsoft Entra admin center or the Microsoft Graph API to find inactive user accounts. While there isn't a built-in report for inactive user accounts, you can use the last sign-in date and time to determine if a user account is inactive.
To find the last sign-in time for a user, you can look at your user list in the Microsoft Entra admin center. While all users can see the list of users, some columns and details are only available to users with the appropriate permissions.
Find the last sign-in time for all users
Sign in to the Microsoft Entra admin center as at least a Reports Reader.
Browse to Identity > Users > All users.
Select Manage view and then Edit columns.
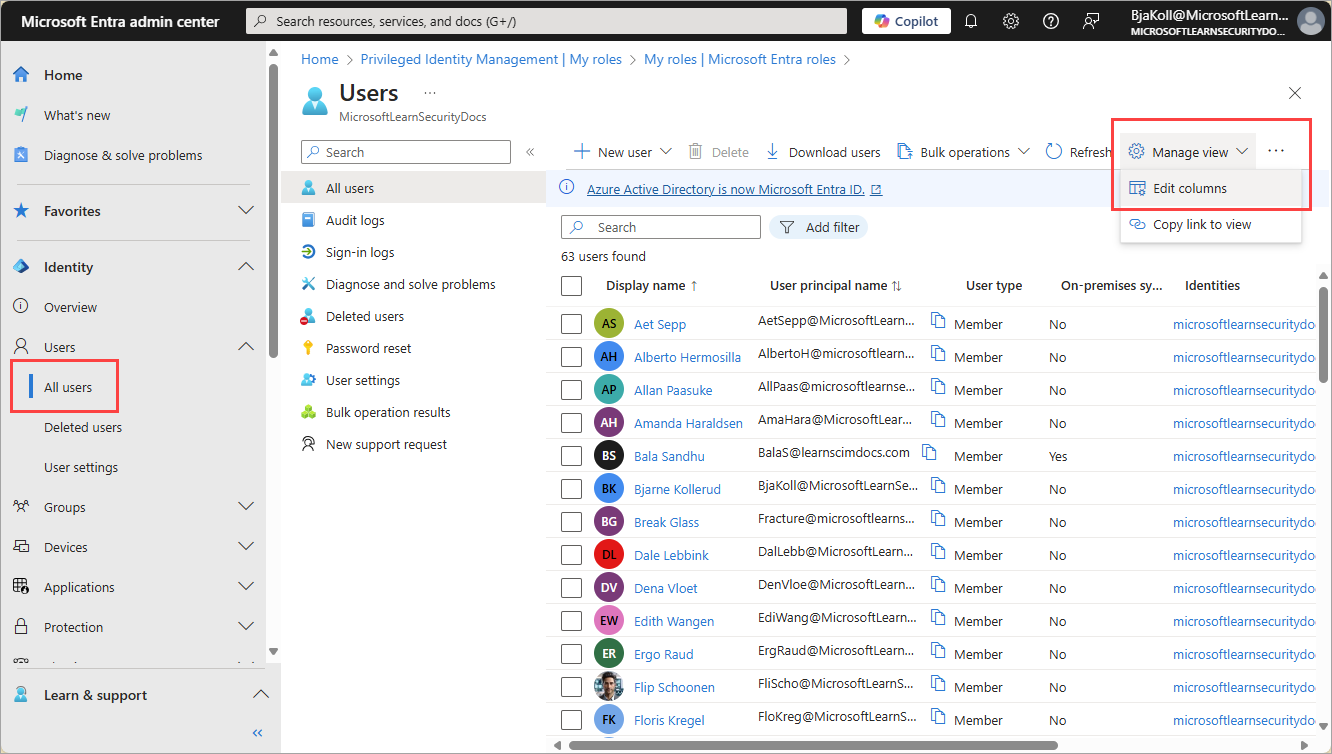
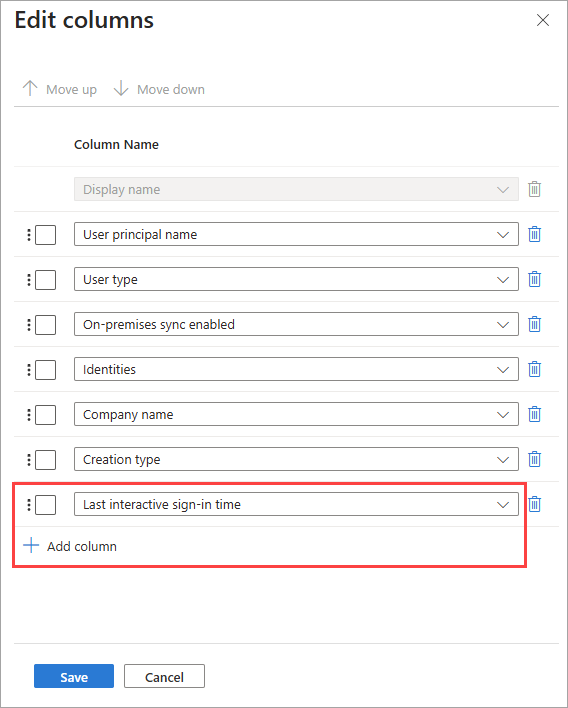
From the list, select + Add column, select Last interactive sign-in time from the list, then select Save.
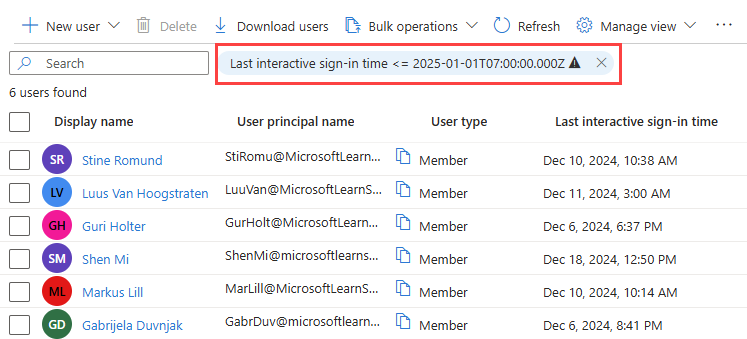
With the column now visible in the all users list, select Add filter and set a time frame for your search using the filter options.
- Select < = as the Operator, then select the date to find the last sign-in before that selected date.
Investigate a single user
If you need to view the latest sign-in activity for a user, you can view the user's sign-in details in Microsoft Entra ID. You can also use the Microsoft Graph API described in the Users by name section.
Sign in to the Microsoft Entra admin center as at least a Reports Reader.
Browse to Identity > Users > All users.
Select a user from the list.
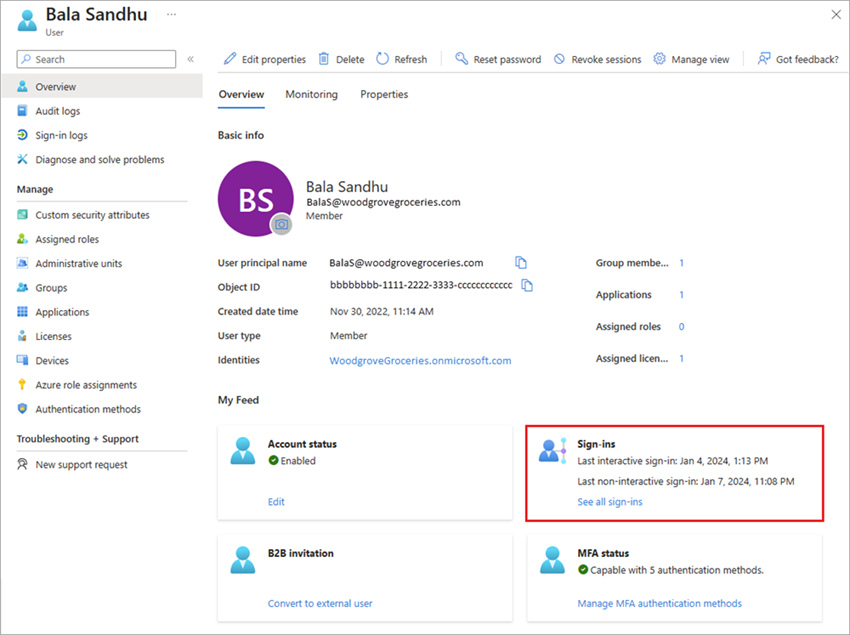
In the My Feed area of the user's Overview, locate the Sign-ins tile.
The last sign-in date and time shown on this tile might take up to 24 hours to update, which means the date and time might not be current. If you need to see the activity in near real time, select the See all sign-ins link on the Sign-ins tile to view all sign-in activity for that user.
How to address inactive users
After identifying inactive users, start by asking the following questions:
- Is the user still employed by the organization?
- Does the user still need access to the resources they have access to?
- Is the user account still needed for any other reason?
How you address inactive users depends on your scenario, but cleaning up unused accounts or over-privileged accounts should be your priority to reduce security risks. The following features and options are a great place to start, but note that some of these features might require additional licensing.
- Clean up stale guest accounts
- Consider dynamic membership group to automatically add or remove users from groups based on their user properties.
- Use Microsoft Entra ID Governance access reviews to audit your users' access.