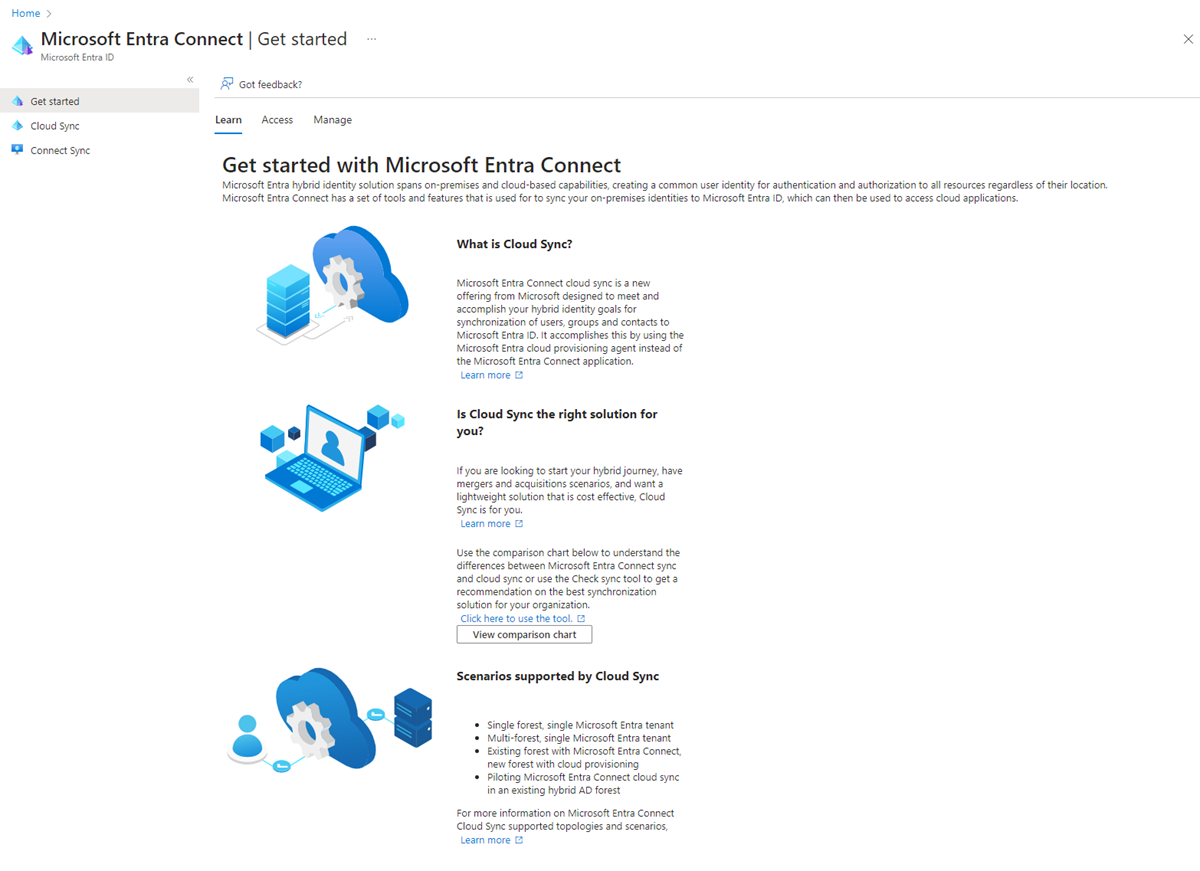
Integrate an existing forest and a new forest with a single Microsoft Entra tenant
This tutorial walks you through adding cloud sync to an existing hybrid identity environment.
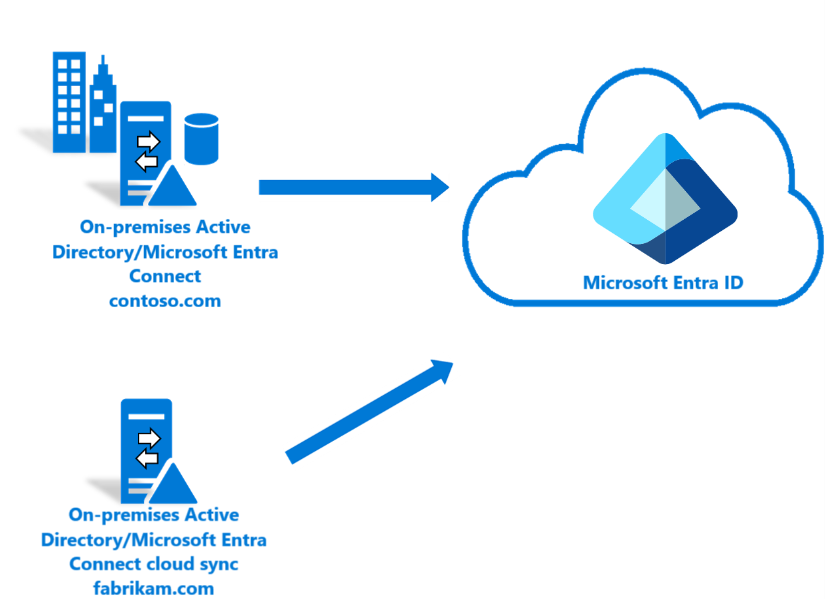
You can use the environment you create in this tutorial for testing or for getting more familiar with how a hybrid identity works.
In this scenario, there's an existing forest synced using Microsoft Entra Connect Sync to a Microsoft Entra tenant. And you have a new forest that you want to sync to the same Microsoft Entra tenant. You'll set up cloud sync for the new forest.
Prerequisites
In the Microsoft Entra admin center
- Create a cloud-only Hybrid Identity Administrator account on your Microsoft Entra tenant. This way, you can manage the configuration of your tenant should your on-premises services fail or become unavailable. Learn about adding a cloud-only Hybrid Identity Administrator account. Completing this step is critical to ensure that you don't get locked out of your tenant.
- Add one or more custom domain names to your Microsoft Entra tenant. Your users can sign in with one of these domain names.
In your on-premises environment
Identify a domain-joined host server running Windows Server 2012 R2 or greater with minimum of 4-GB RAM and .NET 4.7.1+ runtime
If there's a firewall between your servers and Microsoft Entra ID, configure the following items:
Ensure that agents can make outbound requests to Microsoft Entra ID over the following ports:
Port number How it's used 80 Downloads the certificate revocation lists (CRLs) while validating the TLS/SSL certificate 443 Handles all outbound communication with the service 8080 (optional) Agents report their status every 10 minutes over port 8080, if port 443 is unavailable. This status is displayed on the portal. If your firewall enforces rules according to the originating users, open these ports for traffic from Windows services that run as a network service.
If your firewall or proxy allows you to specify safe suffixes, then add connections to *.msappproxy.net and *.servicebus.windows.net. If not, allow access to the Azure datacenter IP ranges, which are updated weekly.
Your agents need access to login.windows.net and login.microsoftonline.com for initial registration. Open your firewall for those URLs as well.
For certificate validation, unblock the following URLs: mscrl.microsoft.com:80, crl.microsoft.com:80, ocsp.msocsp.com:80, and www.microsoft.com:80. Since these URLs are used for certificate validation with other Microsoft products, you may already have these URLs unblocked.
Install the Microsoft Entra provisioning agent
If you're using the Basic AD and Azure environment tutorial, it would be DC1. To install the agent, follow these steps:
In the Azure portal, select Microsoft Entra ID.
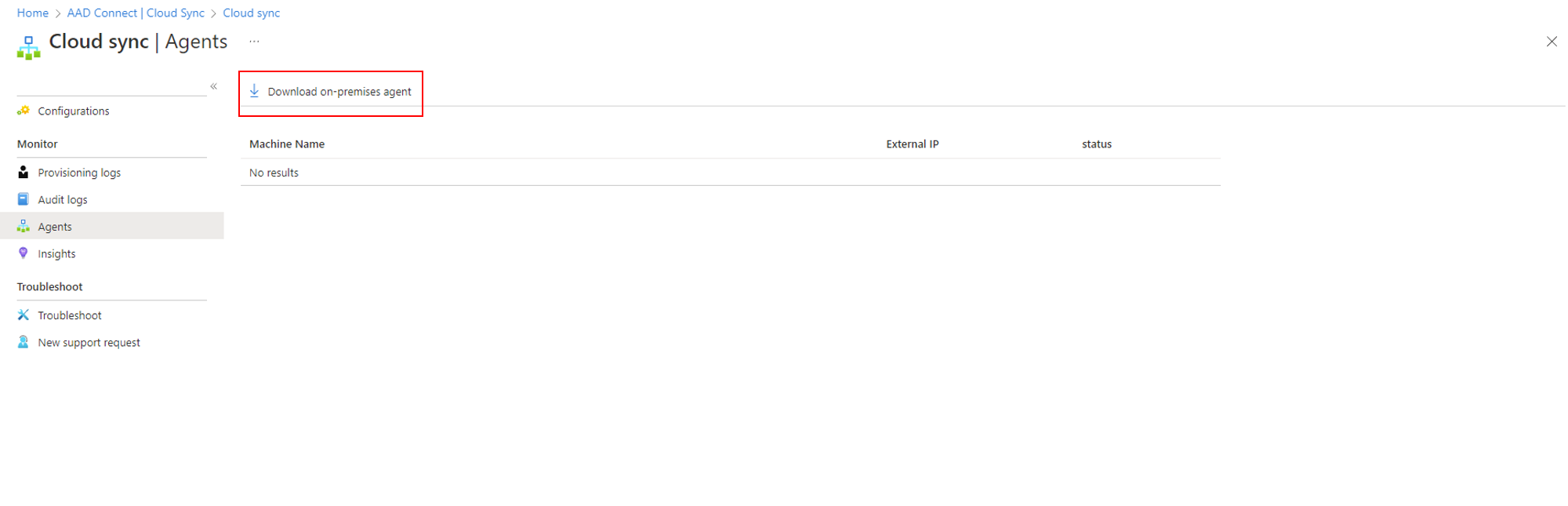
On the left pane, select Microsoft Entra Connect, and then select Cloud Sync.
On the left pane, select Agents.
Select Download on-premises agent, and then select Accept terms & download.
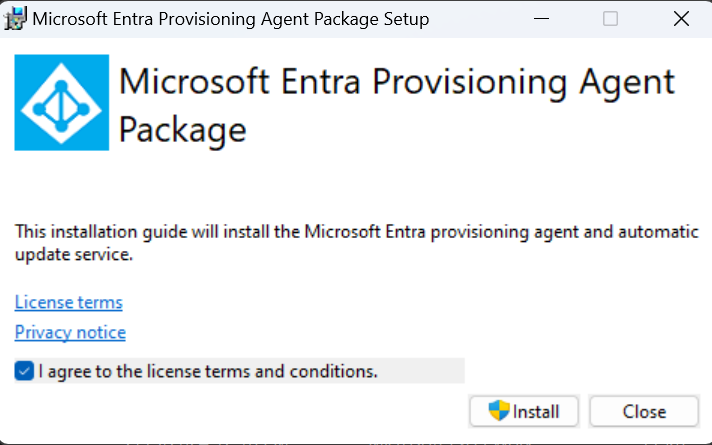
After you download the Microsoft Entra Connect Provisioning Agent Package, run the AADConnectProvisioningAgentSetup.exe installation file from your downloads folder.
Note
When you perform an installation for the US Government Cloud, use AADConnectProvisioningAgentSetup.exe ENVIRONMENTNAME=AzureUSGovernment. For more information, see Install an agent in the US Government Cloud.
On the screen that opens, select the I agree to the license terms and conditions checkbox, and then select Install.
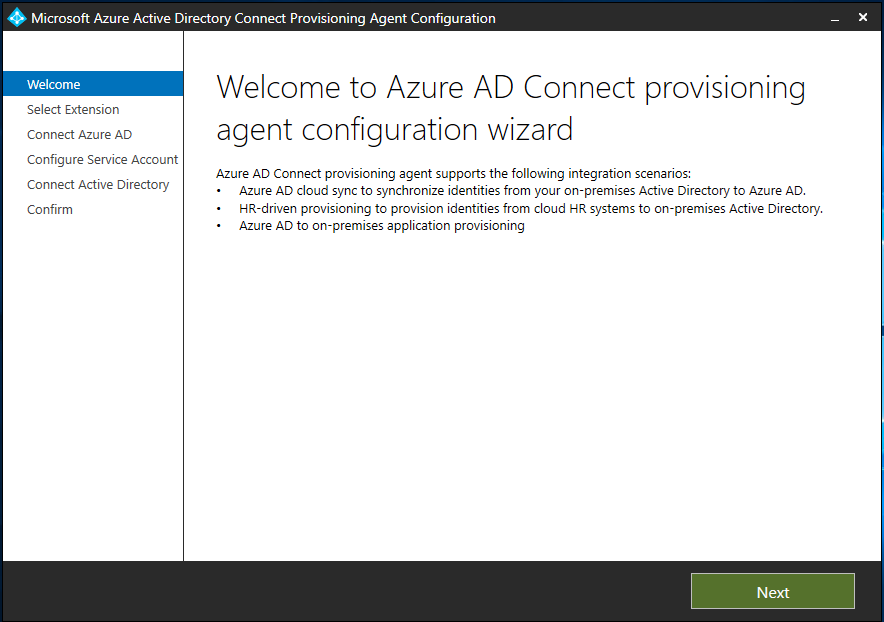
After the installation finishes, the configuration wizard opens. Select Next to start the configuration.
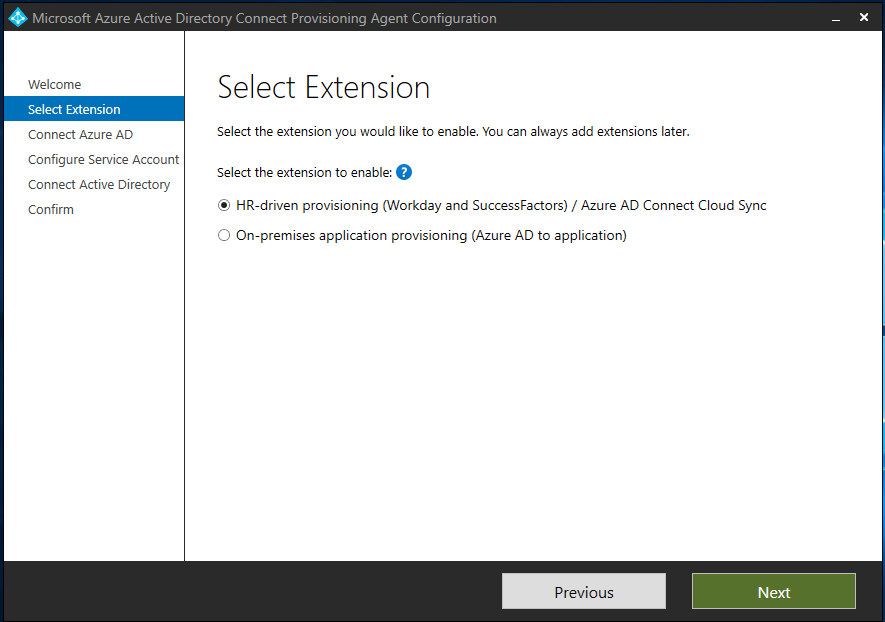
On the Select Extension screen, select HR-driven provisioning (Workday and SuccessFactors) / Azure AD Connect Cloud Sync, and then select Next.
Note
If you install the provisioning agent for use with Microsoft Entra on-premises application provisioning, select On-premises application provisioning (Microsoft Entra ID to application).
Sign in with an account with at least the Hybrid Identity administrator role. If you have Internet Explorer enhanced security enabled, it blocks the sign-in. If so, close the installation, disable Internet Explorer enhanced security, and restart the Microsoft Entra Connect Provisioning Agent Package installation.
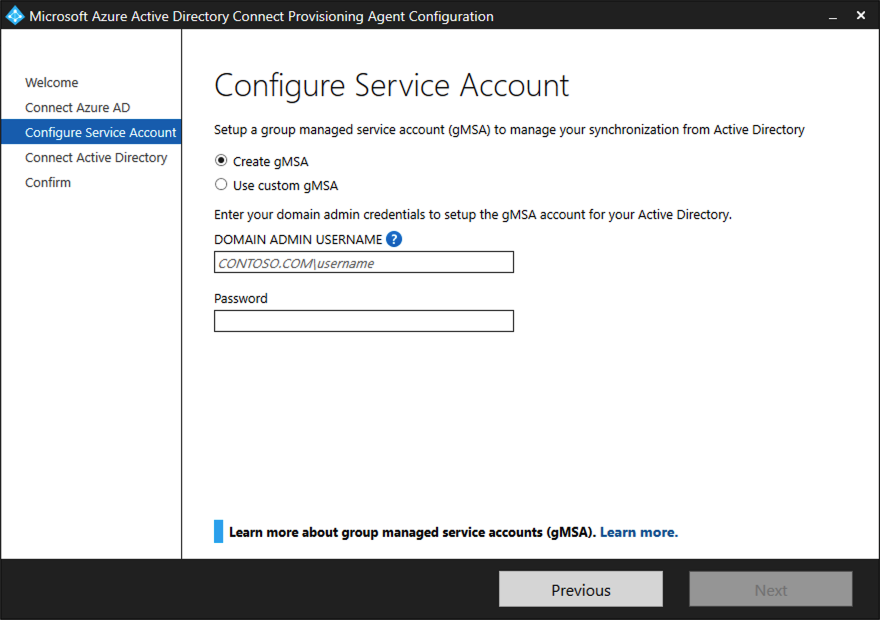
On the Configure Service Account screen, select a group Managed Service Account (gMSA). This account is used to run the agent service. If a managed service account is already configured in your domain by another agent and you're installing a second agent, select Create gMSA. The system detects the existing account and adds the required permissions for the new agent to use the gMSA account. When you're prompted, choose one of two options:
- Create gMSA: Let the agent create the provAgentgMSA$ managed service account for you. The group managed service account (for example,
CONTOSO\provAgentgMSA$) is created in the same Active Directory domain where the host server joined. To use this option, enter the Active Directory domain administrator credentials (recommended). - Use custom gMSA: Provide the name of the managed service account that you manually created for this task.
- Create gMSA: Let the agent create the provAgentgMSA$ managed service account for you. The group managed service account (for example,
To continue, select Next.
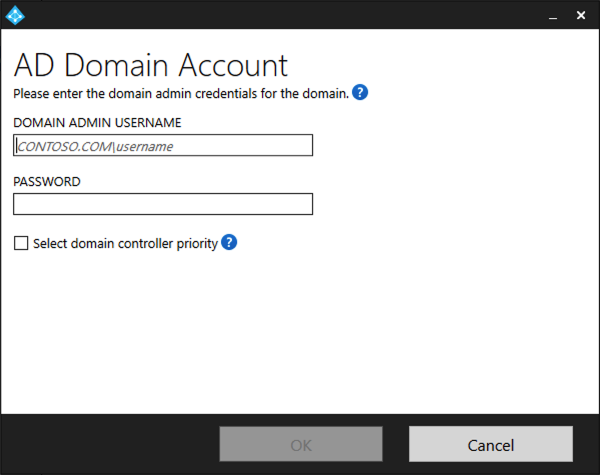
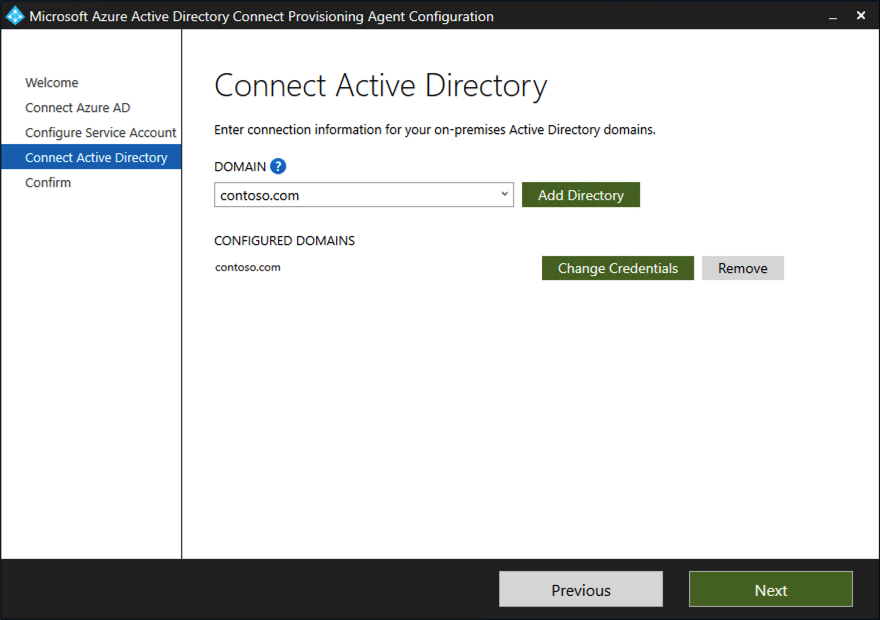
On the Connect Active Directory screen, if your domain name appears under Configured domains, skip to the next step. Otherwise, enter your Active Directory domain name, and select Add directory.
Sign in with your Active Directory domain administrator account. The domain administrator account shouldn't have an expired password. If the password is expired or changes during the agent installation, reconfigure the agent with the new credentials. This operation adds your on-premises directory. Select OK, and then select Next to continue.
The following screenshot shows an example of the domain configured for contoso.com. Select Next to continue.
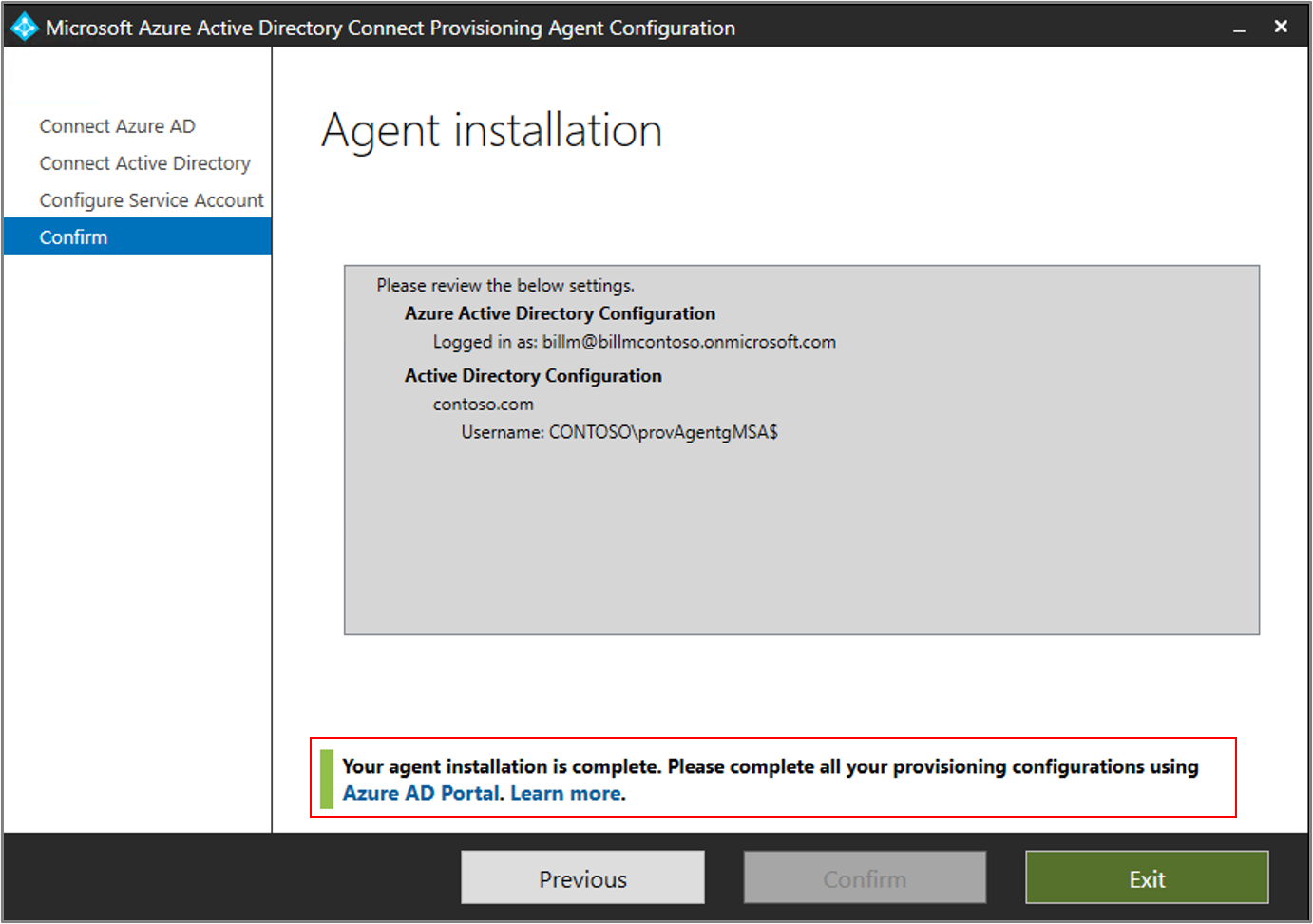
On the Configuration complete screen, select Confirm. This operation registers and restarts the agent.
After the operation finishes, you see a notification that your agent configuration was successfully verified. Select Exit.
If you still get the initial screen, select Close.
Verify agent installation
Agent verification occurs in the Azure portal and on the local server that runs the agent.
Verify the agent in the Azure portal
To verify that Microsoft Entra ID registers the agent, follow these steps:
Sign in to the Azure portal.
Select Microsoft Entra ID.
Select Microsoft Entra Connect, and then select Cloud Sync.
On the Cloud Sync page, you see the agents that you installed. Verify that the agent appears and that the status is healthy.
Verify the agent on the local server
To verify that the agent is running, follow these steps:
Sign in to the server with an administrator account.
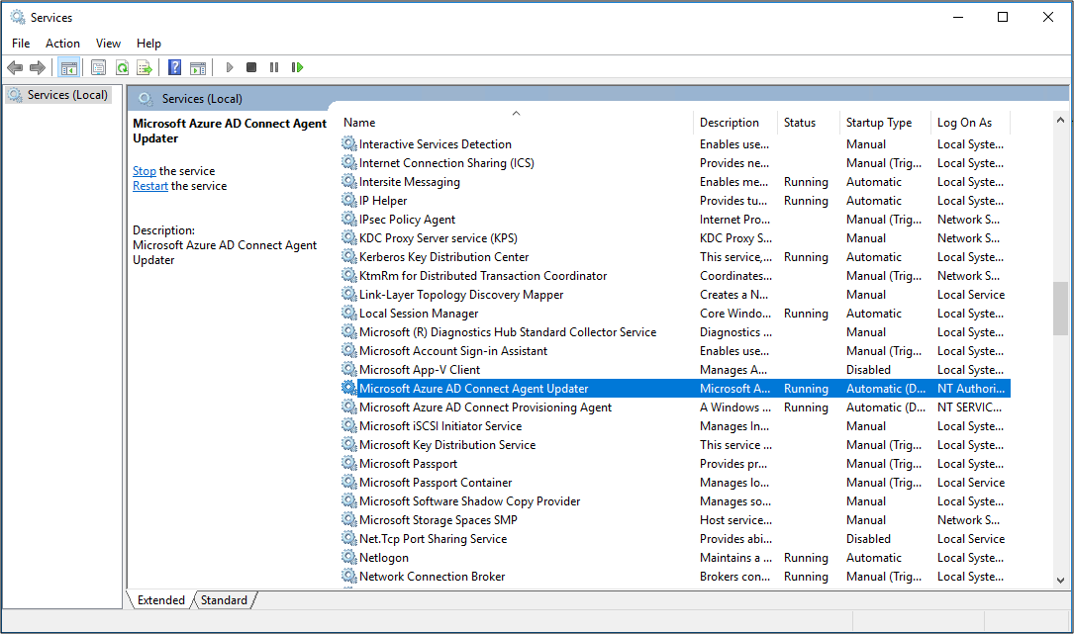
Go to Services. You can also use Start/Run/Services.msc to get to it.
Under Services, make sure that Microsoft Entra Connect Agent Updater and Microsoft Entra Connect Provisioning Agent are present and that the status is Running.
Verify the provisioning agent version
To verify the version of the agent that's running, follow these steps:
- Go to C:\Program Files\Microsoft Azure AD Connect Provisioning Agent.
- Right-click AADConnectProvisioningAgent.exe and select Properties.
- Select the Details tab. The version number appears next to the product version.
Configure Microsoft Entra Cloud Sync
Use the following steps to configure provisioning:
Sign in to the Microsoft Entra admin center as at least a hybrid identity administrator.
Browse to Identity > Hybrid management > Microsoft Entra Connect > Cloud Sync.
- Select New Configuration
- On the configuration screen, enter a Notification email, move the selector to Enable and select Save.
- The configuration status should now be Healthy.
Verify users are created and synchronization is occurring
You'll now verify that the users that you had in our on-premises directory have been synchronized and now exist in our Microsoft Entra tenant. This process may take a few hours to complete. To verify users are synchronized, do the following:
- Sign in to the Microsoft Entra admin center as at least a Hybrid Identity Administrator.
- Browse to Identity > Users.
- Verify that you see the new users in our tenant
Test signing in with one of our users
Browse to https://myapps.microsoft.com
Sign in with a user account that was created in our new tenant. You'll need to sign in using the following format: (user@domain.onmicrosoft.com). Use the same password that the user uses to sign in on-premises.

You have now successfully set up a hybrid identity environment that you can use to test and familiarize yourself with what Azure has to offer.