Configure an automatic assignment policy for an access package in entitlement management
You can use rules to determine access package assignment based on user properties in Microsoft Entra ID, part of Microsoft Entra. In Entitlement Management, an access package can have multiple policies, and each policy establishes how users get an assignment to the access package, and for how long. As an administrator, you can establish a policy for automatic assignments by supplying a membership rule, that Entitlement Management follows to create and remove assignments automatically. Similar to a dynamic group, when an automatic assignment policy is created, user attributes are evaluated for matches with the policy's membership rule. When an attribute changes for a user, these automatic assignment policy rules in the access packages are processed for membership changes. Assignments to users are then added or removed depending on whether they meet the rule criteria.
You can have at most one automatic assignment policy in an access package, and the policy can only be created by an administrator. (Catalog owners and access package managers can't create automatic assignment policies.)
This article describes how to create an access package automatic assignment policy for an existing access package.
Before you begin
You need to have attributes populated on the users who will be in scope for being assigned access. The attributes you can use in the rules criteria of an access package assignment policy are those attributes listed in supported properties, along with extension attributes and custom extension properties. These attributes can be brought into Microsoft Entra ID by patching the user, an HR system such as SuccessFactors, Microsoft Entra Connect cloud sync or Microsoft Entra Connect Sync. The rules can include up to 15,000 users per policy.
License requirements
Using this feature requires Microsoft Entra ID Governance or Microsoft Entra Suite licenses. To find the right license for your requirements, see Microsoft Entra ID Governance licensing fundamentals.
Create an automatic assignment policy
To create a policy for an access package, you need to start from the access package's policy tab. Follow these steps to create a new automatic assignment policy for an access package.
Sign in to the Microsoft Entra admin center as at least an Identity Governance Administrator.
Browse to Identity governance > Entitlement management > Access package.
On the Access packages page, open an access package.
Select Policies and then Add auto-assignment policy to create a new policy.
In the first tab, you specify the rule. Select Edit.
Provide a rule for dynamic membership groups using the membership rule builder or by clicking Edit on the rule syntax text box.
Note
The rule builder might not be able to display some rules constructed in the text box, and validating a rule currently requires the you to be in the Groups Administrator role. For more information, see rule builder in the Microsoft Entra admin center.
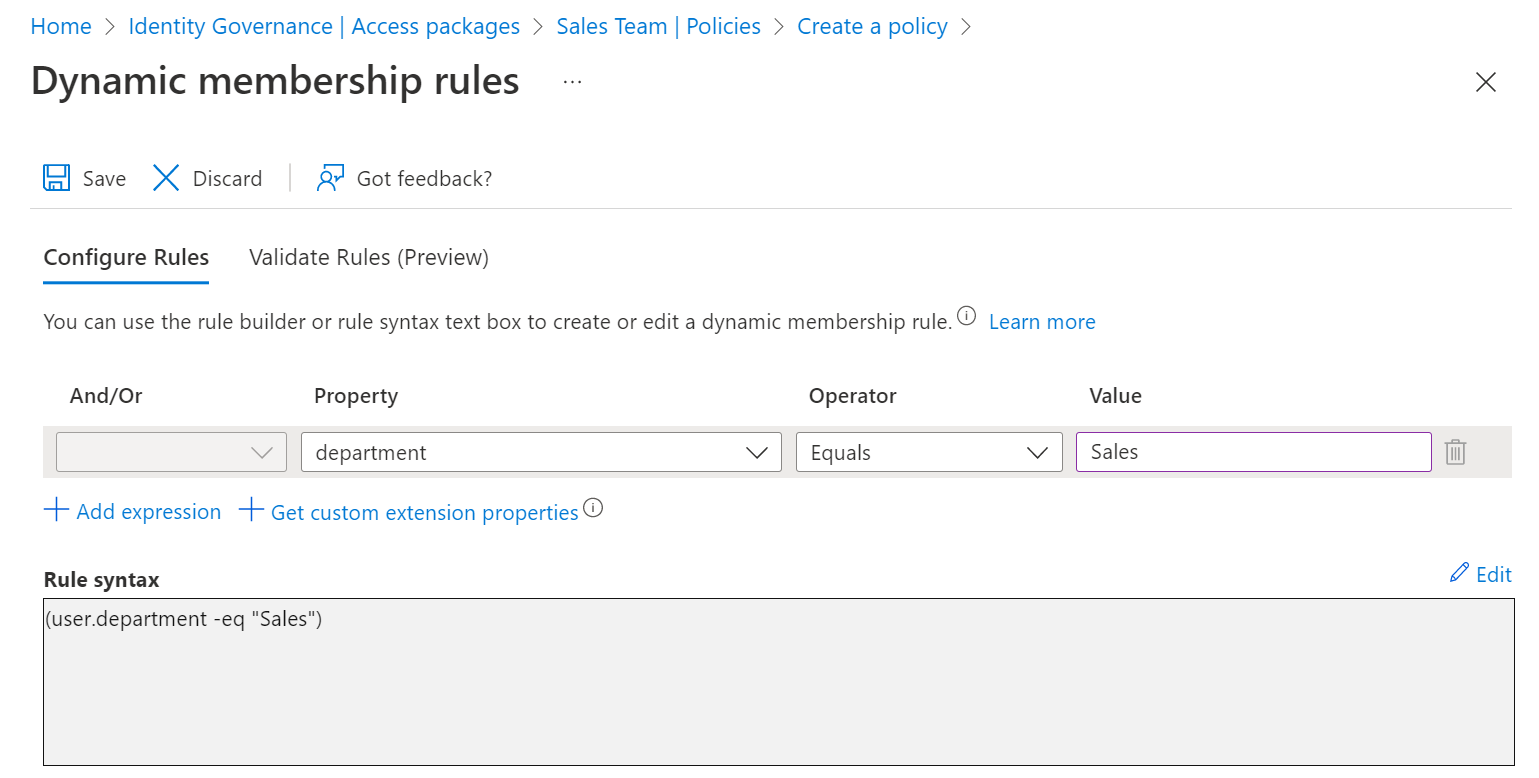
Select Save to close the rule editor for dynamic membership groups.
By default, the checkboxes to automatically create and remove assignments should remain checked.
If you wish users to retain access for a limited time after they go out of scope, you can specify a duration in hours or days. For example, when an employee leaves the sales department, you could wish to allow them to continue to retain access for seven days to allow them to use sales apps and transfer ownership of their resources in those apps to another employee.
Select Next to open the Custom Extensions tab.
If you have custom extensions in your catalog you wish to have run when the policy assigns or removes access, you can add them to this policy. Then select next to open the Review tab.
Type a name and a description for the policy.
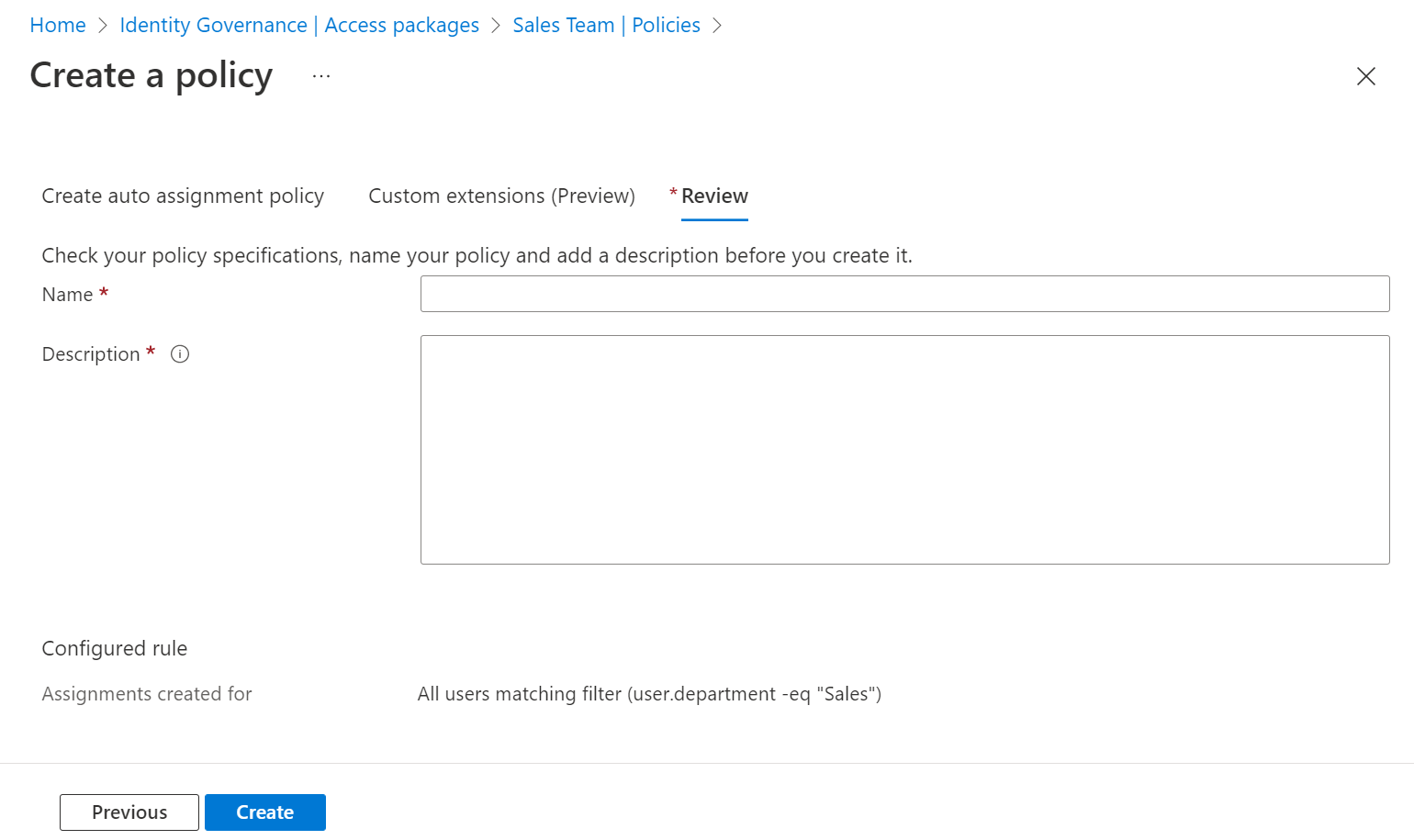
Select Create to save the policy.
Note
At this time, Entitlement management will automatically create a dynamic security group corresponding to each policy, in order to evaluate the users in scope. This group should not be modified except by Entitlement Management itself. This group can also be modified or deleted automatically by Entitlement Management, so don't use this group for other applications or scenarios.
Microsoft Entra ID evaluates the users in the organization that are in scope of this rule, and create assignments for those users who don't already have assignments to the access package. A policy can include at most 15,000 users in its rule. It can take several minutes for the evaluation to occur, or for subsequent updates to user's attributes to be reflected in the access package assignments.
Create an automatic assignment policy programmatically
There are two ways to create an access package assignment policy for automatic assignment programmatically, through Microsoft Graph and through the PowerShell cmdlets for Microsoft Graph.
Create an access package assignment policy through Graph
You can create a policy using Microsoft Graph. A user in an appropriate role with an application that has the delegated EntitlementManagement.ReadWrite.All permission, or an application in a catalog role or with the EntitlementManagement.ReadWrite.All permission, can call the create an assignmentPolicy API. In your request payload, include the displayName, description, specificAllowedTargets, automaticRequestSettings and accessPackage properties of the policy.
Create an access package assignment policy through PowerShell
You can also create a policy in PowerShell with the cmdlets from the Microsoft Graph PowerShell cmdlets for Identity Governance module version 1.16.0 or later.
This following script illustrates using the v1.0 profile, to create a policy for automatic assignment to an access package. See create an assignmentPolicy and Create an access package in entitlement management for an application with a single role using PowerShell for more examples.
Connect-MgGraph -Scopes "EntitlementManagement.ReadWrite.All"
$apid = "00001111-aaaa-2222-bbbb-3333cccc4444"
$pparams = @{
DisplayName = "Sales department users"
Description = "All users from sales department"
AllowedTargetScope = "specificDirectoryUsers"
SpecificAllowedTargets = @( @{
"@odata.type" = "#microsoft.graph.attributeRuleMembers"
description = "All users from sales department"
membershipRule = '(user.department -eq "Sales")'
} )
AutomaticRequestSettings = @{
RequestAccessForAllowedTargets = $true
}
AccessPackage = @{
Id = $apid
}
}
New-MgEntitlementManagementAssignmentPolicy -BodyParameter $pparams