Resilient end-user experience using Azure AD B2C
The sign-up and sign-in end-user experience is made up of the following elements:
- Interfaces the user interacts with, such as CSS, HTML, and JavaScript
- User flows and custom policies you create, for example sign-up, sign-in, and profile edit
- Identity providers (IDPs) for your application, such as local account username or password, Microsoft Outlook, Facebook, and Google
User flow and custom policy
To help you set up the most common identity tasks, Azure AD B2C provides built-in configurable user flows. You can also build your own custom policies that offer you maximum flexibility. However, we recommended use of custom policies to address complex scenarios.
Select user flow or custom policy
Choose built-in user flows that meet your business requirements. Microsoft tests built-in flows, therefore you can minimize testing for validating policy-level functional, performance, or scale. However, test applications for functionality, performance, and scale.
With custom policies ensure policy-level testing for functional, performance, or scale. Conduct application-level testing.
To learn more, you can compare user flows and custom polices.
Choose multiple IdPs
When using an external IdP such as Facebook, create a fallback plan if the external IdP is unavailable.
Set up multiple IdPs
In the external IdP registration process, include a verified identity claim, such as user mobile number or email address. Commit the verified claims to the underlying Azure AD B2C directory instance. If an external IdP is unavailable, revert to the verified identity claim, and fall back to the phone number as an authentication method. Another option is to send the user a one-time passcode (OTP) for sign-in.
You can build alternate authentication paths:
- Configure sign-up policy to allow sign-up by local account and external IDPs.
- Configure a profile policy to allow users to link the other identity to their account after they sign in.
- Notify and allow users to switch to an alternate IDP during an outage.
Availability of multifactor authentication
If you use a phone service for multifactor authentication, consider an alternative service provider. The local phone service provider might experience service disruptions.
Select alternate multifactor authentication
The Azure AD B2C service has a phone-based MFA provider to deliver time-based, one-time passcodes (OTPs). It's a voice call and text message to user preregistered phone numbers.
With user flows, there are two methods to build resilience:
Change user flow configuration: During disruption in phone-based OTP delivery, change the OTP delivery method to email. Redeploy the user flow.
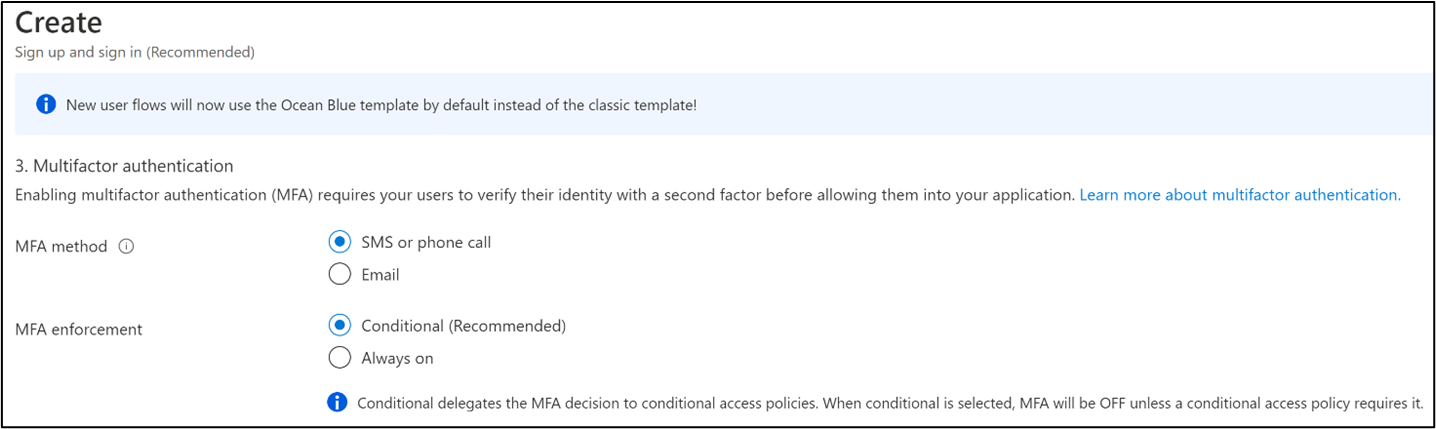
Change applications: For identity tasks, such as sign-up and sign-in, define two sets of user flows. Configure the first set to use phone-based OTP, and the second to email OTP. During a disruption in phone-based OTP delivery, switch from the first set of user flows to the second, leaving the user flows unchanged.
If you use custom policies, there are four methods to build resilience. The list is on order of complexity. Redeploy updated policies.
Enable user selection of phone OTP or email OTP: Expose both options to enable users to self-select. Don't changes policies or applications.
Dynamically switch between phone OTP and email OTP: Collect phone and email information at sign-up. Define custom policy to switch conditionally, during phone disruption, to email OTP. Don't change policies or applications.
Use an authentication app: Update custom policy to use an authentication app. If your MFA is phone or email OTP, redeploy custom policies and use an authentication app.
Note
Users configure Authenticator integration during sign-up.
Security questions: If none of the previous methods are applicable, use security questions. These questions are for users during onboarding, or profile edit. Answers are stored in a separate database. This method doesn't meet the MFA requirement of something you have, for example, a phone, but is something that you know.
Content delivery network
Content delivery networks (CDNs) perform better and are less expensive than blob stores for storing custom user flow UI. The web page content goes from a geographically distributed network of highly available servers.
Periodically, test CDN availability and the performance of content distribution through end-to-end scenario and load testing. For surges due to promotions or holiday traffic, revise estimates for load testing.