Exclude assets from automated responses in automatic attack disruption
This article provides information on how to exclude assets from being automatically contained by automatic attack disruption in Microsoft Defender XDR.
Automatic attack disruption enables the exclusion of specific user accounts, devices, and IP addresses from automated containment actions. Once excluded, these assets won't be affected by automated actions triggered by attack disruption.
Caution
Excluding assets from automated responses is not recommended. Excluding assets from automated responses can reduce the effectiveness of automatic attack disruption in protecting your environment from sophisticated, high-impact attacks.
Prerequisites
To exclude assets from automated responses in automatic attack disruption, you must have one of the following roles assigned in either Microsoft Entra ID (https://portal.azure.com) or in the Microsoft 365 admin center (https://admin.microsoft.com):
- Global Administrator
- Security Administrator
Review or change automated response exclusions for assets
To exclude assets from automated responses in automatic attack disruption, follow these steps:
Go to the Microsoft Defender portal (https://security.microsoft.com) and sign in.
Go to Settings > Microsoft Defender XDR.
Exclude user accounts
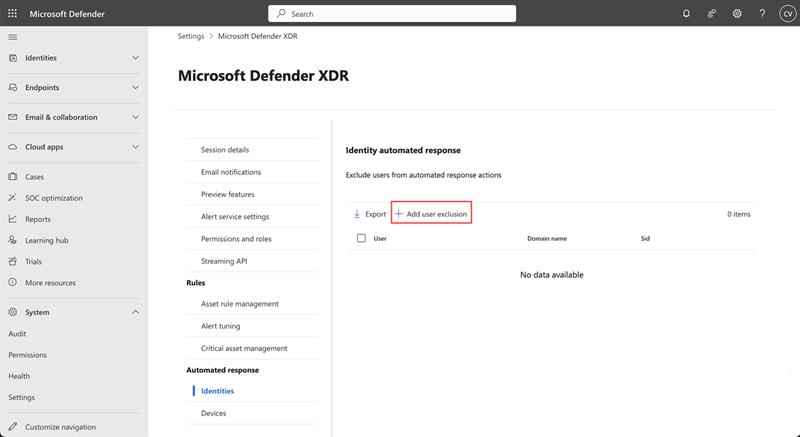
Under Automated response, select Identities.
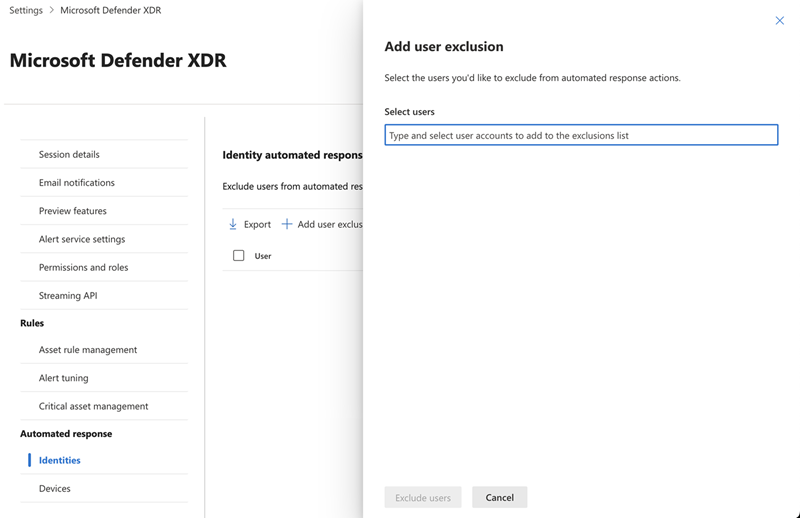
To exclude a user account, select Add user exclusion. A flyout pane appears.
In the flyout pane, enter the user account names in the Select users box and select the user accounts you want to exclude.
Select Exclude users to save the exclusion.
Exclude device groups
Caution
Excluding device groups from automated responses also impacts automated investigation and response actions.
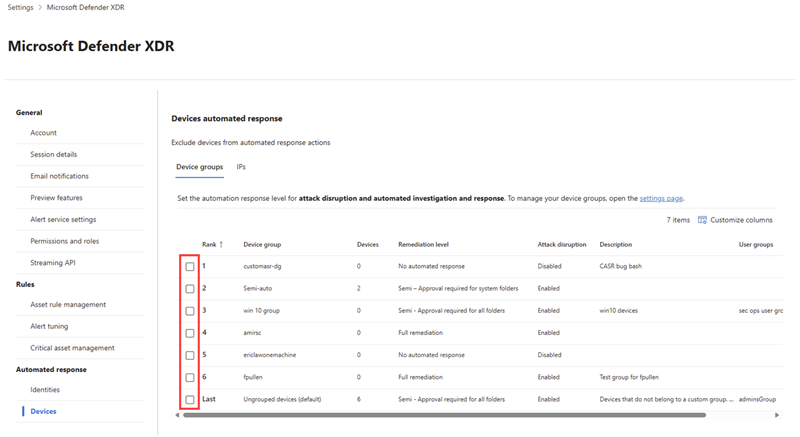
Under Automated responses, select Devices.
In the Device groups tab, choose a device group by selecting the checkbox next to the group name from the list to configure attack disruption automation settings.
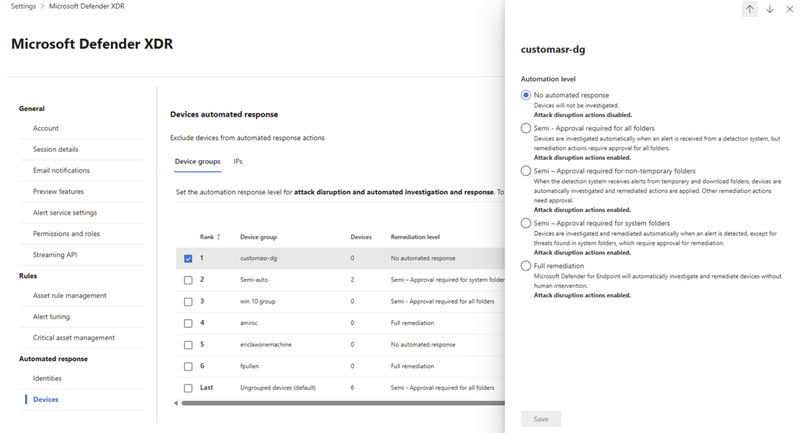
In the flyout pane, select the appropriate automation level for the device group. You can choose from any of the following automation levels appropriate for your device group:
- Full - remediate threats automatically: Automatically contain devices when a threat is detected.
- Semi - require approval for core folders: Automatically investigate devices when an alert is received and apply remediation actions except to items within core system folders. Remediation actions for the core folders require approval.
- Semi - require approval for non-temp folders: Automatically investigate and apply remediation to actions within temp and download folders when an alert is received. All other remediation actions require approval.
- Semi - require approval for all folders: Automatically investigate devices when an alert is received. All remediation actions require approval.
- No automated response: No automated investigation or response is taken for devices in this group.
Select Save to save the automation level for the device group.
Important
Some information in this article relates to a prereleased product, which may be substantially modified before it's commercially released. Microsoft makes no warranties expressed or implied, with respect to the information provided here.
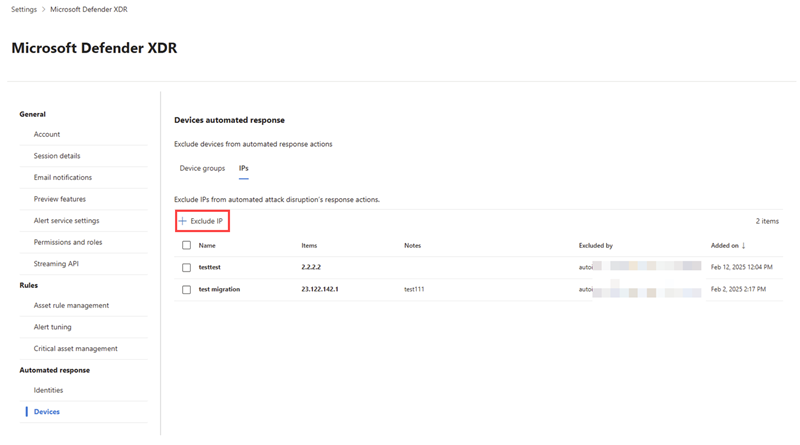
Exclude IPs
Under Automated responses, select Devices.
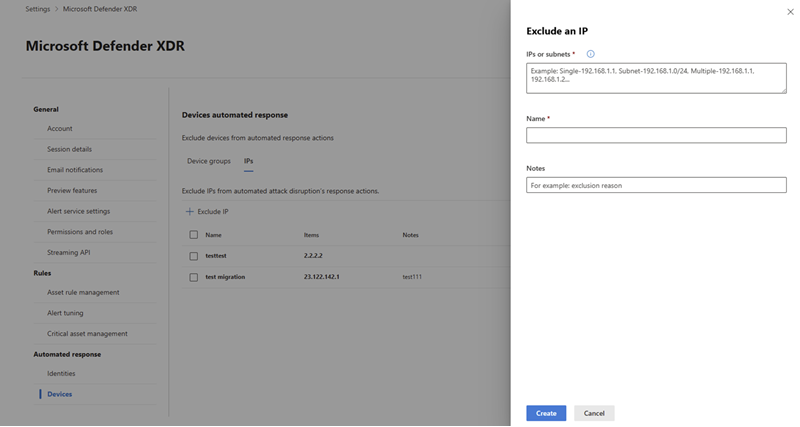
In the IPs tab, select Exclude IP to exclude an IP address.
In the flyout pane, enter the IP address/IP range/IP subnet you want to exclude. You can add multiple IP addresses and IP subnets by separating them with a comma.
Add a name and note for the exclusion. Select Create to save the exclusion.
Remove exclusions
To remove an exclusion:
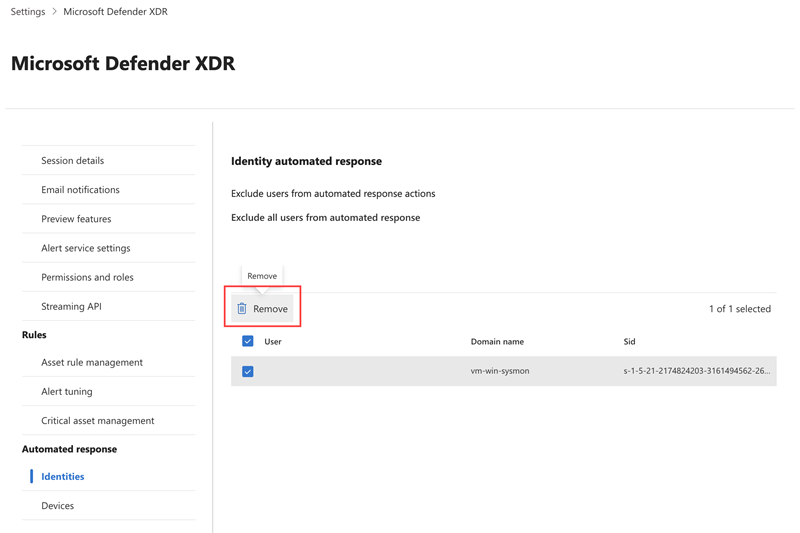
- Go to the Identities page. Select the user account you want to remove from the list and then select Remove.
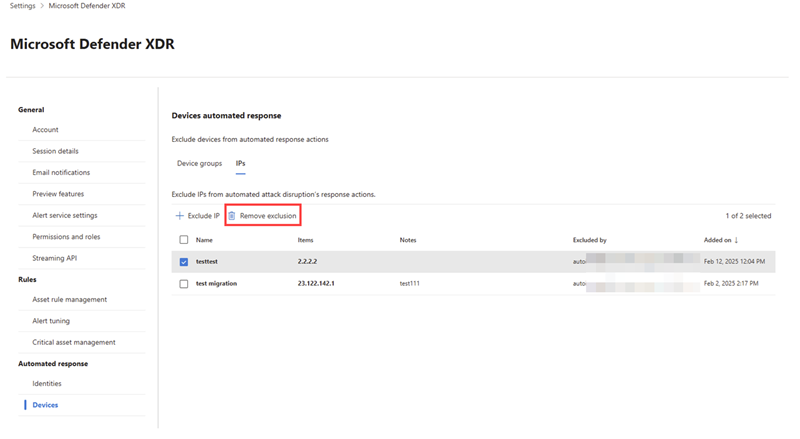
- Go to the Devices page and navigate to the IPs tab. Select the IP address you want to remove from the list and then select Remove exclusion.
- Device group exclusions can be configured in the Device groups tab. Select the device group you want to configure from the list and choose the appropriate exclusion from the flyout pane. Select Save to save the exclusion.
See also
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender XDR Tech Community.