Stream Azure Spring Apps application console logs in real time
Note
The Basic, Standard, and Enterprise plans will be deprecated starting from mid-March, 2025, with a 3 year retirement period. We recommend transitioning to Azure Container Apps. For more information, see the Azure Spring Apps retirement announcement.
The Standard consumption and dedicated plan will be deprecated starting September 30, 2024, with a complete shutdown after six months. We recommend transitioning to Azure Container Apps. For more information, see Migrate Azure Spring Apps Standard consumption and dedicated plan to Azure Container Apps.
This article applies to: ✅ Java ✅ C#
This article applies to: ✅ Basic/Standard ✅ Enterprise
This article describes how to enable log streaming in the Azure CLI to get real-time application console logs for troubleshooting. You can also use diagnostics settings to analyze diagnostics data in Azure Spring Apps. For more information, see Analyze logs and metrics with diagnostics settings. For more information on streaming logs, see Stream Azure Spring Apps job logs in real time and Stream Azure Spring Apps managed component logs in real time.
Prerequisites
- Azure CLI with the Azure Spring Apps extension, version 1.0.0 or higher. You can install the extension by using the following command:
az extension add --name spring - An instance of Azure Spring Apps with a running application. For more information, see Quickstart: Deploy your first application to Azure Spring Apps.
Stream logs
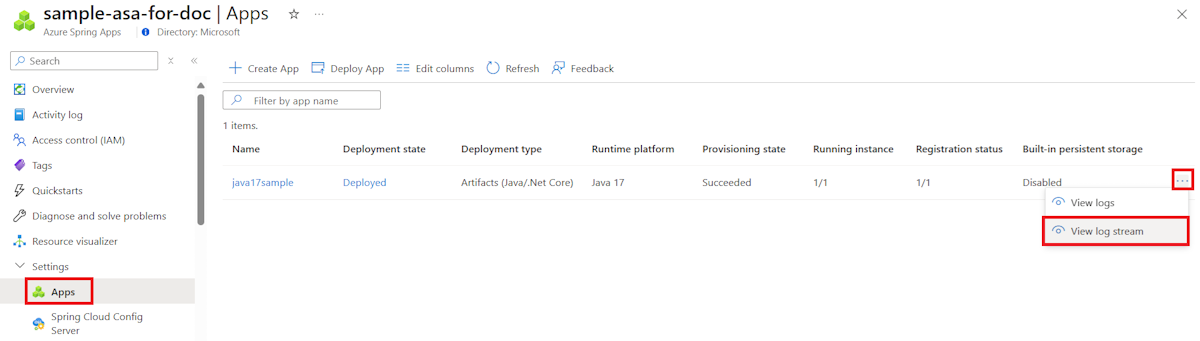
Use the following steps to stream logs in the Azure portal:
Go to the Overview page for your Azure Spring Apps service instance and then select Apps in the navigation pane.
Find your target app and select the context menu.
In the pop-up context menu, select View log stream.
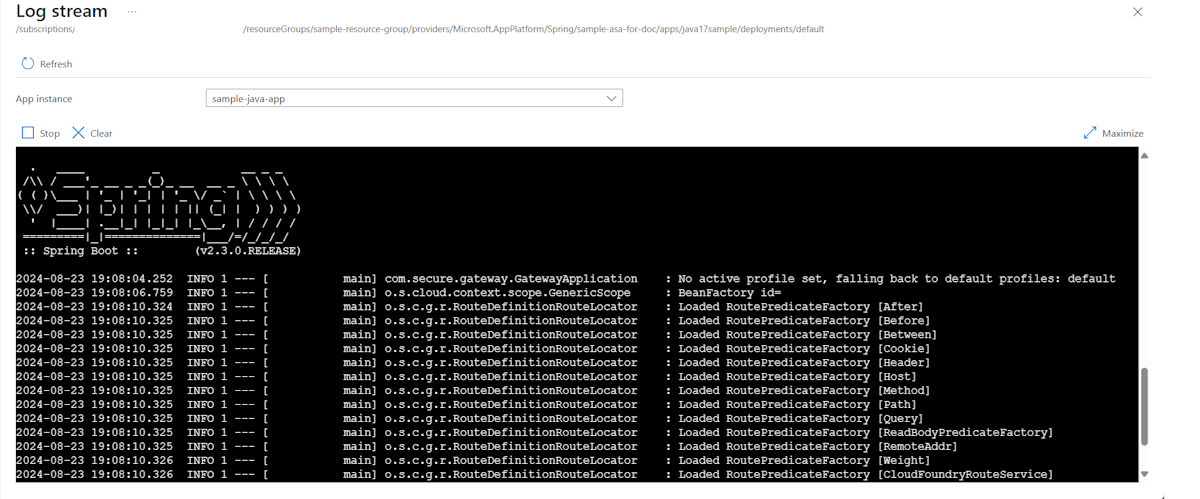
By default, logs start streaming for a randomly selected app instance. You can select yours afterwards.
For convenience, there are many entry points to stream logs. You can find them in the following panes:
- The App list pane
- The Deployment list pane
- The App instance list pane
Stream an Azure Spring Apps app log in a virtual network injection instance
For an Azure Spring Apps instance deployed in a custom virtual network, you can access log streaming by default from a private network. For more information, see Deploy Azure Spring Apps in a virtual network
Azure Spring Apps also enables you to access real-time app logs from a public network using Azure portal or the Azure CLI.
Note
Enabling the log streaming endpoint on the public network adds a public inbound IP to your virtual network. Be sure to use caution if this is a concern for you.
Use the following steps to enable a log streaming endpoint on the public network:
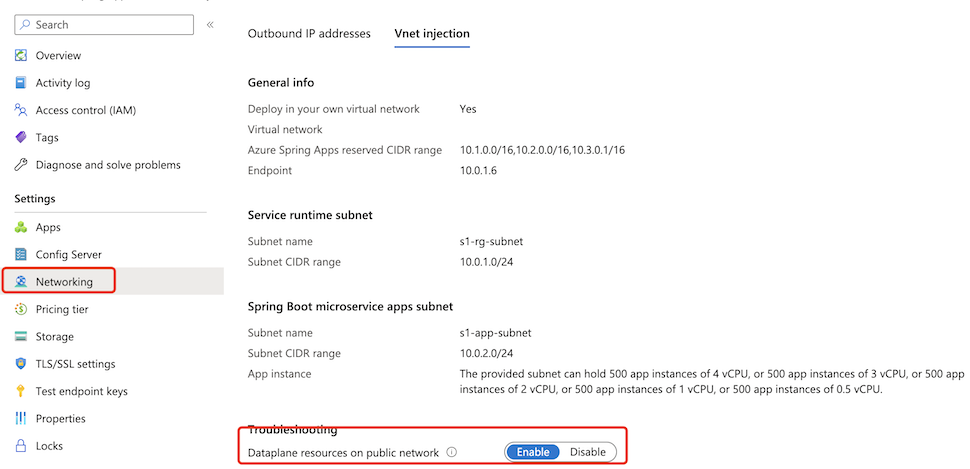
Select the Azure Spring Apps service instance deployed in your virtual network and then select Networking in the navigation menu.
Select the Vnet injection tab.
Switch the status of Dataplane resources on public network to enable to enable a log streaming endpoint on the public network. This process takes a few minutes.
After you enable the log stream public endpoint, you can access the app log from a public network just like you would access a normal instance.
Secure traffic to the log streaming public endpoint
Log streaming uses the same key as the test endpoint described in Set up a staging environment in Azure Spring Apps to authenticate the connections to your deployments. As a result, only users who have read access to the test keys can access log streaming.
To ensure the security of your applications when you expose a public endpoint for them, secure the endpoint by filtering network traffic to your service with a network security group. For more information, see Tutorial: Filter network traffic with a network security group using the Azure portal. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources. For each rule, you can specify source and destination, port, and protocol.
Note
If you can't access app logs in the virtual network injection instance from the internet after you enable a log stream public endpoint, check your network security group to see whether you allowed such inbound traffic.
The following table shows an example of a basic rule that we recommend. You can use commands like nslookup with the endpoint <service-name>.private.azuremicroservices.io to get the target IP address of a service.
| Priority | Name | Port | Protocol | Source | Destination | Action |
|---|---|---|---|---|---|---|
| 100 | Rule name | 80 | TCP | Internet | Service IP address | Allow |
| 110 | Rule name | 443 | TCP | Internet | Service IP address | Allow |