Deploy the Microsoft Sentinel solution for SAP BTP
This article describes how to deploy the Microsoft Sentinel solution for SAP Business Technology Platform (BTP) system. The Microsoft Sentinel solution for SAP BTP monitors and protects your SAP BTP system. It collects audit logs and activity logs from the BTP infrastructure and BTP-based apps, and then detects threats, suspicious activities, illegitimate activities, and more. Read more about the solution.
Prerequisites
Before you begin, verify that:
- The Microsoft Sentinel solution is enabled.
- You have a defined Microsoft Sentinel workspace, and you have read and write permissions to the workspace.
- Your organization uses SAP BTP (in a Cloud Foundry environment) to streamline interactions with SAP applications and other business applications.
- You have an SAP BTP account (which supports BTP accounts in the Cloud Foundry environment). You can also use a SAP BTP trial account.
- You have the SAP BTP auditlog-management service and service key (see Set up the BTP account and solution).
- You have the Microsoft Sentinel Contributor role on the target Microsoft Sentinel workspace.
Set up the BTP account and solution
To set up the BTP account and the solution:
After you can sign in to your BTP account (see the prerequisites), follow the audit log retrieval steps on the SAP BTP system.
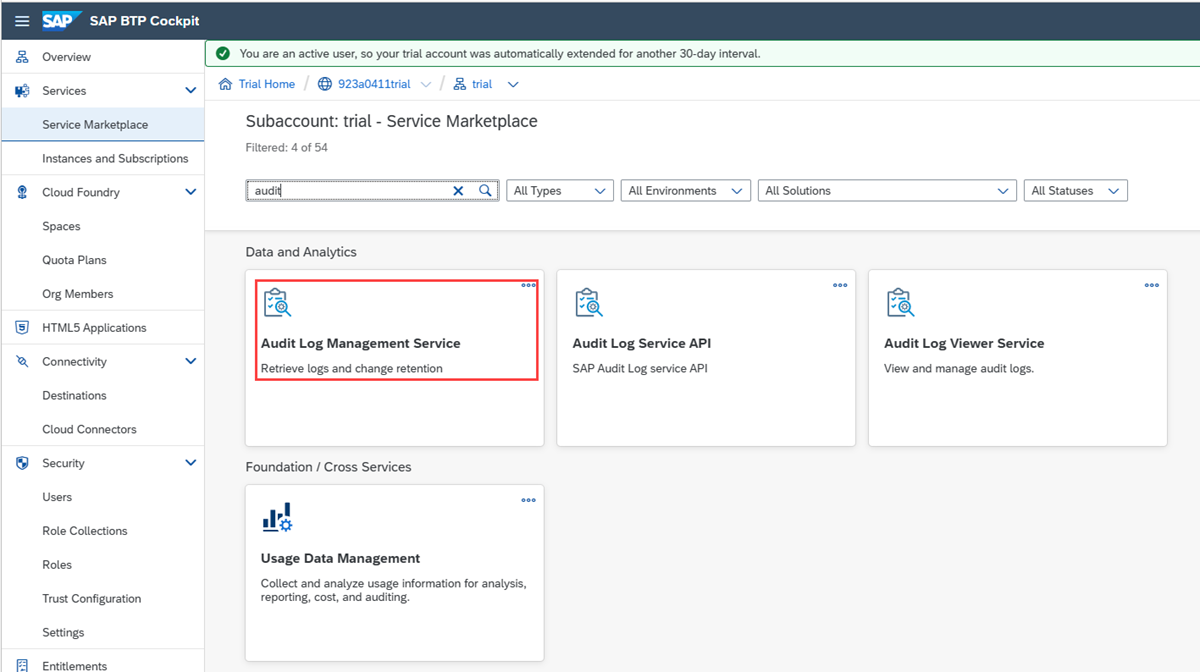
In the SAP BTP cockpit, select the Audit Log Management Service.
Create an instance of the Audit Log Management Service in the BTP subaccount.
Create a service key and record the values for
url,uaa.clientid,uaa.clientecret, anduaa.url. These values are required to deploy the data connector.Here are examples of these field values:
- url:
https://auditlog-management.cfapps.us10.hana.ondemand.com - uaa.clientid:
00001111-aaaa-2222-bbbb-3333cccc4444|auditlog-management!b1237 - uaa.clientsecret:
aaaaaaaa-0b0b-1c1c-2d2d-333333333333 - uaa.url:
https://trial.authentication.us10.hana.ondemand.com
- url:
Sign in to the Azure portal.
Go to the Microsoft Sentinel service.
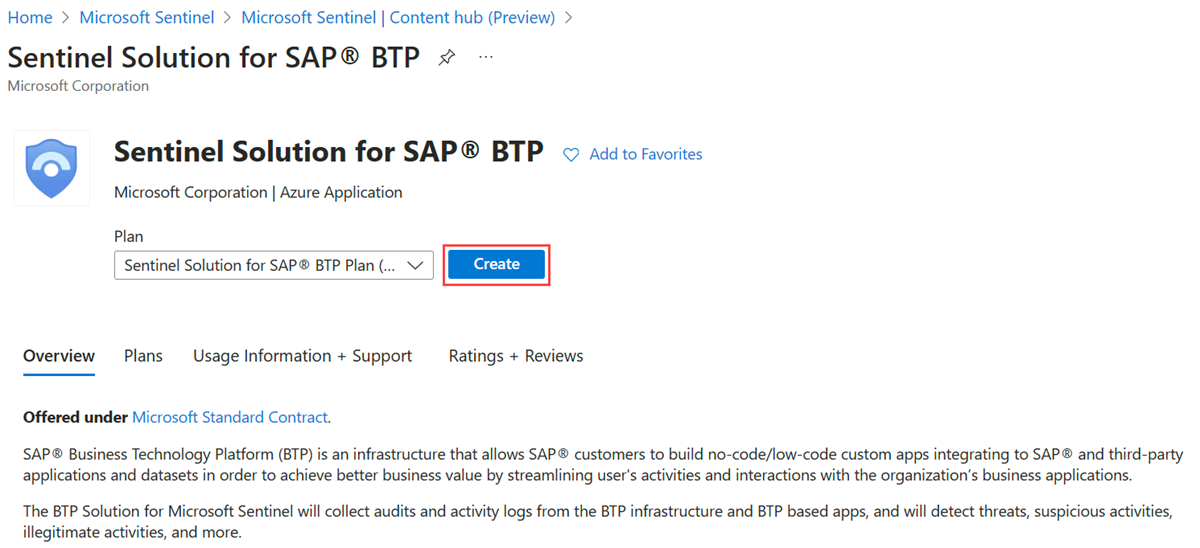
Select Content hub, and in the search bar, search for BTP.
Select SAP BTP.
Select Install.
For more information about how to manage the solution components, see Discover and deploy out-of-the-box content.
Select Create.
Select the resource group and the Microsoft Sentinel workspace in which to deploy the solution.
Select Next until you pass validation, and then select Create.
When the solution deployment is finished, return to your Microsoft Sentinel workspace and select Data connectors.
In the search bar, enter BTP, and then select SAP BTP.
Select Open connector page.
On the connector page, make sure that you meet the required prerequisites listed and complete the configuration steps. When you're ready, select Add account.
Specify the parameters that you defined earlier during the configuration. The subaccount name specified is projected as a column in the
SAPBTPAuditLog_CLtable, and can be used to filter the logs when you have multiple subaccounts.Note
Retrieving audits for the global account doesn't automatically retrieve audits for the subaccount. Follow the connector configuration steps for each of the subaccounts you want to monitor, and also follow these steps for the global account. Review these account auditing configuration considerations.
Make sure that BTP logs are flowing into the Microsoft Sentinel workspace:
- Sign in to your BTP subaccount and run a few activities that generate logs, such as sign-ins, adding users, changing permissions, and changing settings.
- Allow 20 to 30 minutes for the logs to start flowing.
- On the SAP BTP connector page, confirm that Microsoft Sentinel receives the BTP data, or query the SAPBTPAuditLog_CL table directly.
Enable the workbook and the analytics rules that are provided as part of the solution by following these guidelines.
Consider your account auditing configurations
The final step in the deployment process is to consider your global account and subaccount auditing configurations.
Global account auditing configuration
When you enable audit log retrieval in the BTP cockpit for the global account: If the subaccount for which you want to entitle the Audit Log Management Service is under a directory, you must entitle the service at the directory level first. Only then can you entitle the service at the subaccount level.
Subaccount auditing configuration
To enable auditing for a subaccount, complete the steps in the SAP subaccounts audit retrieval API documentation.
The API documentation describes how to enable the audit log retrieval by using the Cloud Foundry CLI.
You also can retrieve the logs via the UI:
- In your subaccount in SAP Service Marketplace, create an instance of Audit Log Management Service.
- In the new instance, create a service key.
- View the service key and retrieve the required parameters from step 4 of the configuration instructions in the data connector UI (url, uaa.url, uaa.clientid, and uaa.clientsecret).
Rotate the BTP client secret
We recommend that you periodically rotate the BPT subaccount client secrets. The following sample script demonstrates the process of updating an existing data connector with a new secret fetched from Azure Key Vault.
Before you start, collect the values you need for the scripts parameters, including:
- The subscription ID, resource group, and workspace name for your Microsoft Sentinel workspace.
- The key vault and the name of the key vault secret.
- The name of the data connector you want to update with a new secret. To identify the data connector name, open the SAP BPT data connector in the Microsoft Sentinel data connectors page. The data connector name has the following syntax: BTP_{connector name}
param(
[Parameter(Mandatory = $true)] [string]$subscriptionId,
[Parameter(Mandatory = $true)] [string]$workspaceName,
[Parameter(Mandatory = $true)] [string]$resourceGroupName,
[Parameter(Mandatory = $true)] [string]$connectorName,
[Parameter(Mandatory = $true)] [string]$clientId,
[Parameter(Mandatory = $true)] [string]$keyVaultName,
[Parameter(Mandatory = $true)] [string]$secretName
)
# Import the required modules
Import-Module Az.Accounts
Import-Module Az.KeyVault
try {
# Login to Azure
Login-AzAccount
# Retrieve BTP client secret from Key Vault
$clientSecret = (Get-AzKeyVaultSecret -VaultName $keyVaultName -Name $secretName).SecretValue
if (!($clientSecret)) {
throw "Failed to retrieve the client secret from Azure Key Vault"
}
# Get the connector from data connectors API
$path = "/subscriptions/{0}/resourceGroups/{1}/providers/Microsoft.OperationalInsights/workspaces/{2}/providers/Microsoft.SecurityInsights/dataConnectors/{3}?api-version=2024-01-01-preview" -f $subscriptionId, $resourceGroupName, $workspaceName, $connectorName
$connector = (Invoke-AzRestMethod -Path $path -Method GET).Content | ConvertFrom-Json
if (!($connector)) {
throw "Failed to retrieve the connector"
}
# Add the updated client ID and client secret to the connector
$connector.properties.auth | Add-Member -Type NoteProperty -Name "clientId" -Value $clientId
$connector.properties.auth | Add-Member -Type NoteProperty -Name "clientSecret" -Value ($clientSecret | ConvertFrom-SecureString -AsPlainText)
# Update the connector with the new auth object
Invoke-AzRestMethod -Path $path -Method PUT -Payload ($connector | ConvertTo-Json -Depth 10)
}
catch {
Write-Error "An error occurred: $_"
}