Microsoft Entra authentication for Azure Database for MySQL - Flexible Server
Microsoft Entra authentication is a mechanism of connecting to Azure Database for MySQL Flexible Server by using identities defined in Microsoft Entra ID. With Microsoft Entra authentication, you can manage database user identities and other Microsoft services in a central location, simplifying permission management.
Benefits
- Authentication of users across Azure Services in a uniform way
- Management of password policies and password rotation in a single place
- Multiple forms of authentication supported by Microsoft Entra ID, which can eliminate the need to store passwords
- Customers can manage database permissions using external (Microsoft Entra ID) groups.
- Microsoft Entra authentication uses MySQL database users to authenticate identities at the database level
- Support of token-based authentication for applications connecting to Azure Database for MySQL Flexible Server
Use the steps below to configure and use Microsoft Entra authentication
Select your preferred authentication method for accessing the Flexible Server. By default, the authentication selected is set to MySQL authentication only. Select Microsoft Entra authentication only or MySQL and Microsoft Entra authentication to enable Microsoft Entra authentication.
Select the user managed identity (UMI) with the following privileges to configure Microsoft Entra authentication:
- User.Read.All: Allows access to Microsoft Entra user information.
- GroupMember.Read.All: Allows access to Microsoft Entra group information.
- Application.Read.ALL: Allows access to Microsoft Entra service principal (application) information.
Add Microsoft Entra Admin. It can be Microsoft Entra users or Groups, which has access to a Flexible Server.
Create database users in your database mapped to Microsoft Entra identities.
Connect to your database by retrieving a token for a Microsoft Entra identity and logging in.
Note
For detailed, step-by-step instructions about how to configure Microsoft Entra authentication with Azure Database for MySQL Flexible Server, see Set up Microsoft Entra authentication for Azure Database for MySQL - Flexible Server
Architecture
User-managed identities are required for Microsoft Entra authentication. When a User-Assigned Identity is linked to the Flexible Server, the Managed Identity Resource Provider (MSRP) issues a certificate internally to that identity. When the managed identity is deleted, the corresponding service principal is automatically removed.
The service then uses the managed identity to request access tokens for services that support Microsoft Entra authentication. Azure Database currently supports only a User-assigned Managed Identity (UMI) for Azure Database for MySQL Flexible Server. For more information, see Managed identity types in Azure.
The following high-level diagram summarizes how authentication works using Microsoft Entra authentication with Azure Database for MySQL Flexible Server. The arrows indicate communication pathways.
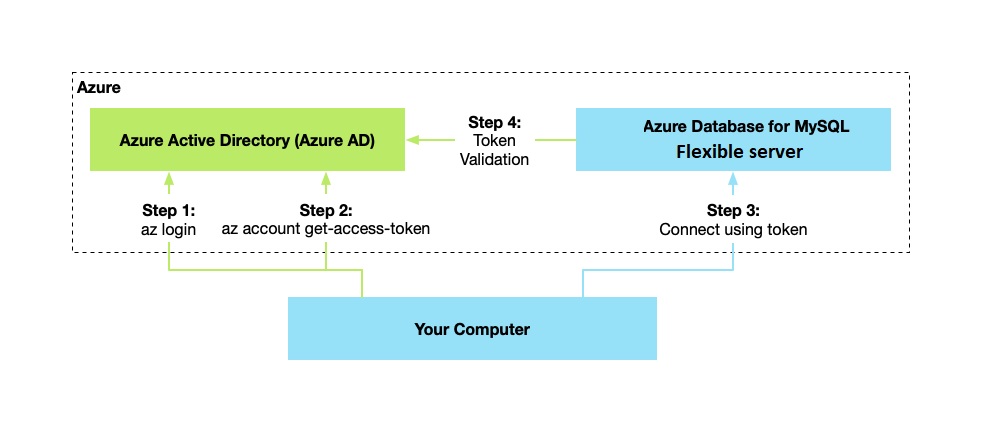
- Your application can request a token from the Azure Instance Metadata Service identity endpoint.
- When you use the client ID and certificate, a call is made to Microsoft Entra ID to request an access token.
- A JSON Web Token (JWT) access token is returned by Microsoft Entra ID. Your application sends the access token on a call to your Flexible Server.
- The Flexible Server validates the token with Microsoft Entra ID.
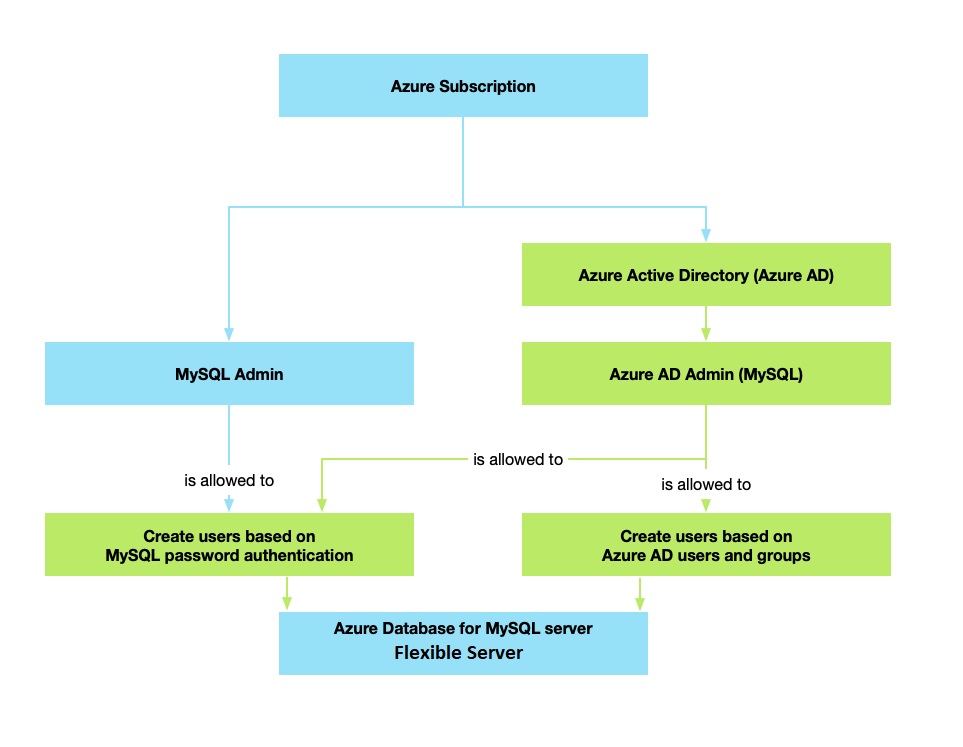
Administrator structure
There are two Administrator accounts for Azure Database for MySQL Flexible Server when using Microsoft Entra authentication: the original MySQL administrator and the Microsoft Entra administrator.
Only the administrator based on a Microsoft Entra account can create the first Microsoft Entra ID contained database user in a user database. The Microsoft Entra administrator sign-in can be a Microsoft Entra user or a Microsoft Entra group. When the administrator is a group account, it can be used by any group member, enabling multiple Microsoft Entra administrators for the Flexible Server. Using a group account as an administrator enhances manageability by allowing you to centrally add and remove group members in Microsoft Entra ID without changing the users or permissions in the Flexible server. Only one Microsoft Entra administrator (a user or group) can be configured at a time.
Methods of authentication for accessing the Flexible Server include:
MySQL authentication only - This is the default option. Only the native MySQL authentication with a MySQL sign-in and password can be used to access the Flexible Server.
Only Microsoft Entra authentication - MySQL native authentication is disabled, and users are able to authenticate using only their Microsoft Entra user and token. To enable this mode, the server parameter aad_auth_only is set to ON.
Authentication with MySQL and Microsoft Entra ID - Both native MySQL authentication and Microsoft Entra authentication are supported. To enable this mode, the server parameter aad_auth_only is set to OFF.
Permissions
The following permissions are required to allow the UMI to read from the Microsoft Graph as the server identity. Alternatively, give the user-assigned managed identity the Directory Readers role.
Important
Only a user with at least the Privileged Role Administrator role can grant these permissions.
- User.Read.All: Allows access to Microsoft Entra user information.
- GroupMember.Read.All: Allows access to Microsoft Entra group information.
- Application.Read.ALL: Allows access to Microsoft Entra service principal (application) information.
For guidance about how to grant and use the permissions, refer to Overview of Microsoft Graph permissions
After you grant the permissions to the UMI, they're enabled for all servers created with the UMI assigned as a server identity.
Token Validation
Microsoft Entra authentication in Azure Database for MySQL Flexible Server ensures that the user exists in the MySQL server and checks the token's validity by validating the token's contents. The following token validation steps are performed:
- Token is signed by Microsoft Entra ID and hasn't been tampered.
- Token was issued by Microsoft Entra ID for the tenant associated with the server.
- Token hasn't expired.
- Token is for the Flexible Server resource (and not another Azure resource).
Connect using Microsoft Entra identities
Microsoft Entra authentication supports the following methods of connecting to a database using Microsoft Entra identities:
- Microsoft Entra Password
- Microsoft Entra integrated
- Microsoft Entra Universal with MFA
- Using Active Directory Application certificates or client secrets
- Managed Identity
Once you authenticate against the Active Directory, you retrieve a token. This token is your password for logging in.
Note
That management operation, such as adding new users, is only supported for Microsoft Entra user roles.
Note
For more information on how to connect with an Active Directory token, see Set up Microsoft Entra authentication for Azure Database for MySQL - Flexible Server.
Other considerations
You can only configure one Microsoft Entra administrator per Flexible Server at any time.
Only a Microsoft Entra administrator for MySQL can initially connect to the Flexible Server using a Microsoft Entra account. The Active Directory administrator can configure subsequent Microsoft Entra database users or a Microsoft Entra group. When the administrator is a group account, it can be used by any group member, enabling multiple Microsoft Entra administrators for the Flexible Server. Using a group account as an administrator enhances manageability by allowing you to centrally add and remove group members in Microsoft Entra ID without changing the users or permissions in the Flexible Server.
If a user is deleted from Microsoft Entra ID, that user can no longer authenticate with Microsoft Entra ID. Therefore, acquiring an access token for that user is no longer possible. Although the matching user is still in the database, connecting to the server with that user isn't possible.
Note
Log in with the deleted Microsoft Entra user can still be done until the token expires (up to 60 minutes from token issuing). If you remove the user from Azure Database for MySQL Flexible Server, this access is revoked immediately.
If the Microsoft Entra admin is removed from the server, the server is no longer associated with a Microsoft Entra tenant, and therefore all Microsoft Entra logins are disabled for the server. Adding a new Microsoft Entra admin from the same tenant re-enables Microsoft Entra logins.
A Flexible Server matches access tokens to the Azure Database for MySQL Flexible Server users using the user's unique Microsoft Entra user ID instead of the username. This means that if a Microsoft Entra user is deleted in Microsoft Entra ID and a new user is created with the same name, the Flexible Server considers that a different user. Therefore, if a user is deleted from Microsoft Entra ID and then a new user with the same name is added, the new user isn't able to connect with the existing user.
Note
The subscriptions of a Flexible Server with Microsoft Entra authentication enabled can't be transferred to another tenant or directory.