Setting up Microsoft Sentinel for Azure Managed HSM
You can use Microsoft Sentinel to automatically detect suspicious activity on your Azure resources. Microsoft Sentinel comes with many out-of-the-box connectors for Microsoft services, which integrate in real time. You can find the specific "Solution Package" for protecting Azure Key Vaults in the Microsoft Sentinel's Content Hub. You can use this for Managed HSM as well. However, there are a few key steps to take to ensure you are using it for Managed HSM properly.
Follow the instructions found in Quickstart: Onboard to Microsoft Sentinel | Microsoft Learn to enable Microsoft Sentinel.
Navigate to your Microsoft Sentinel workspace, and then select Content hub under Content management.
Search for Azure Key Vault in the Content Hub and select it.
Select Install on the sidebar that appears.
Select Analytics under Configuration.
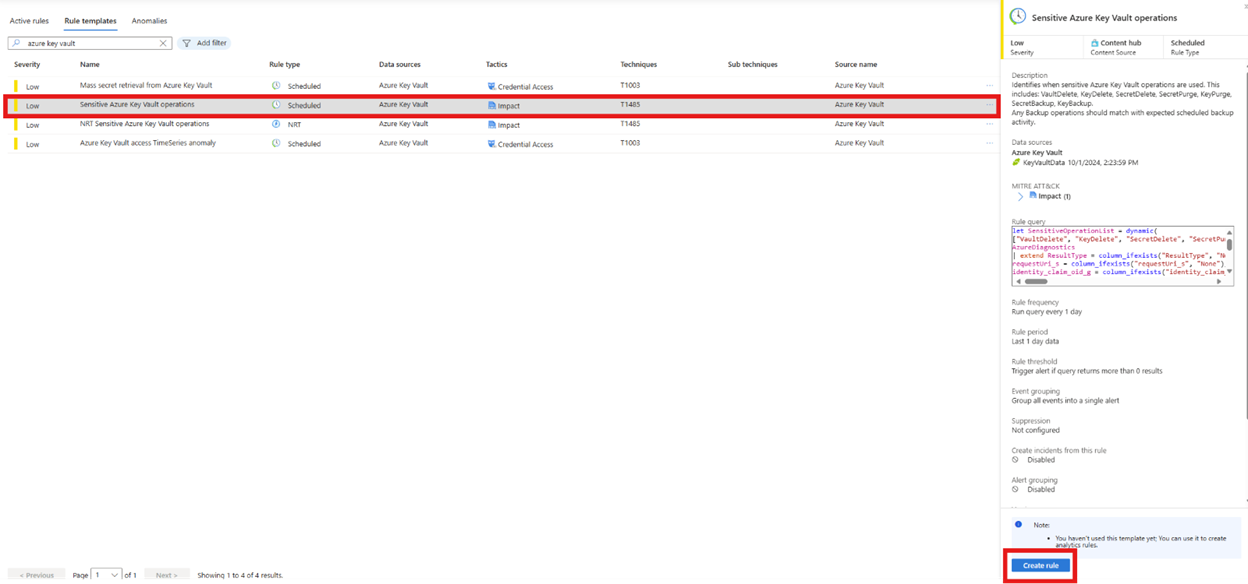
Select Rule templates, and then search for Azure Key Vault or use the filter to filter Data sources to Azure Key Vault.
Use the rule template that matches your use case best. In this example, we select Sensitive Key Vault operations. In the sidebar that appears, select Create rule.
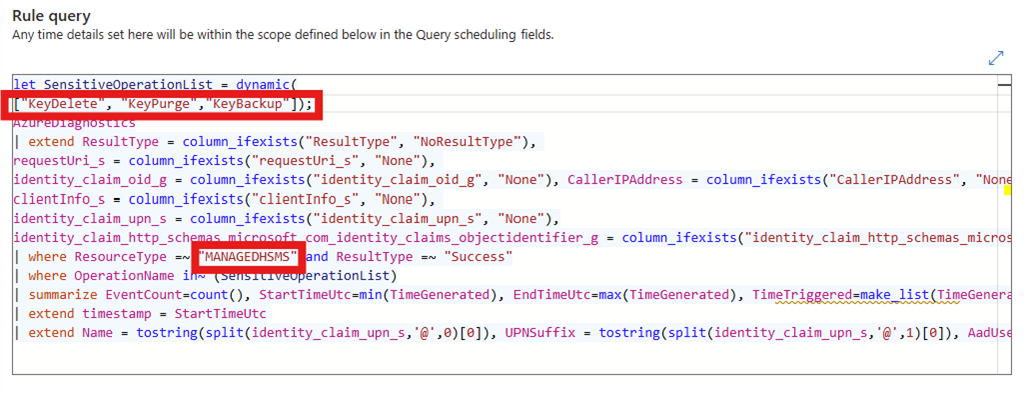
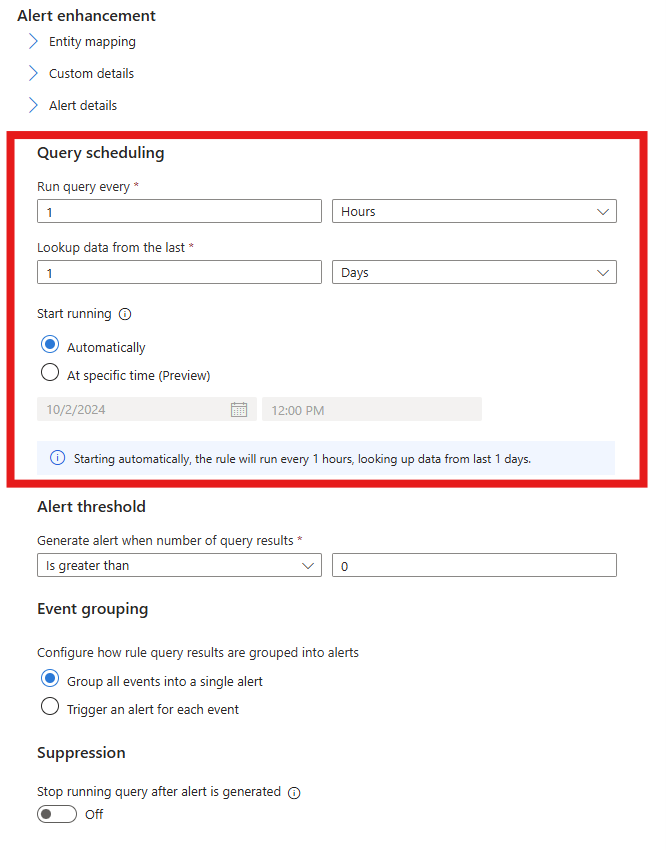
In the Set rule logic tab, edit the rule query. Change "VAULTS" to "MANAGEDHSMS". In this example, we also changed the
SensitiveOperationListto include key-related operations only.In this example, we schedule the query to run once every hour.
Review and save the rule. You should now see the rule you created on the Analytics page.
You can test the rule by creating and deleting a key. The
KeyDeleteoperation is one of the sensitive operations searched by the Analytic Rule named "Sensitive Azure Managed HSM operations".