Use managed identities to access Azure Key Vault certificates
Managed identities provided by Microsoft Entra ID enable your Azure Front Door instance to securely access other Microsoft Entra protected resources, such as Azure Key Vault, without the need to manage credentials. For more information, see What are managed identities for Azure resources?.
Note
Managed identity support in Azure Front Door is limited to accessing Azure Key Vault. It can't be used to authenticate from Front Door to origins such as Blob Storage or Web Apps.
After you enable managed identity for Azure Front Door and granting the necessary permissions to your Azure Key Vault, Front Door will use the managed identity to access certificates. Without these permissions, custom certificate autorotation and adding new certificates fail. If managed identity is disabled, Azure Front Door will revert to using the original configured Microsoft Entra App, which isn't recommended and will be deprecated in the future.
Azure Front Door supports two types of managed identities:
- System-assigned identity: This identity is tied to your service and is deleted if the service is deleted. Each service can have only one system-assigned identity.
- User-assigned identity: This is a standalone Azure resource that can be assigned to your service. Each service can have multiple user-assigned identities.
Managed identities are specific to the Microsoft Entra tenant where your Azure subscription is hosted. If a subscription is moved to a different directory, you need to recreate and reconfigure the identity.
You can configure Azure Key Vault access using either role-based access control (RBAC) or access policy.
Prerequisites
Before setting up managed identity for Azure Front Door, ensure you have an Azure Front Door Standard or Premium profile. To create a new profile, see create an Azure Front Door.
Enable managed identity
Navigate to your existing Azure Front Door profile. Select Identity under Security in the left menu.
Choose either a System assigned or User assigned managed identity.
System assigned - A managed identity tied to the Azure Front Door profile lifecycle, used to access Azure Key Vault.
User assigned - A standalone managed identity resource with its own lifecycle, used to authenticate to Azure Key Vault.
System assigned
Toggle the Status to On and select Save.
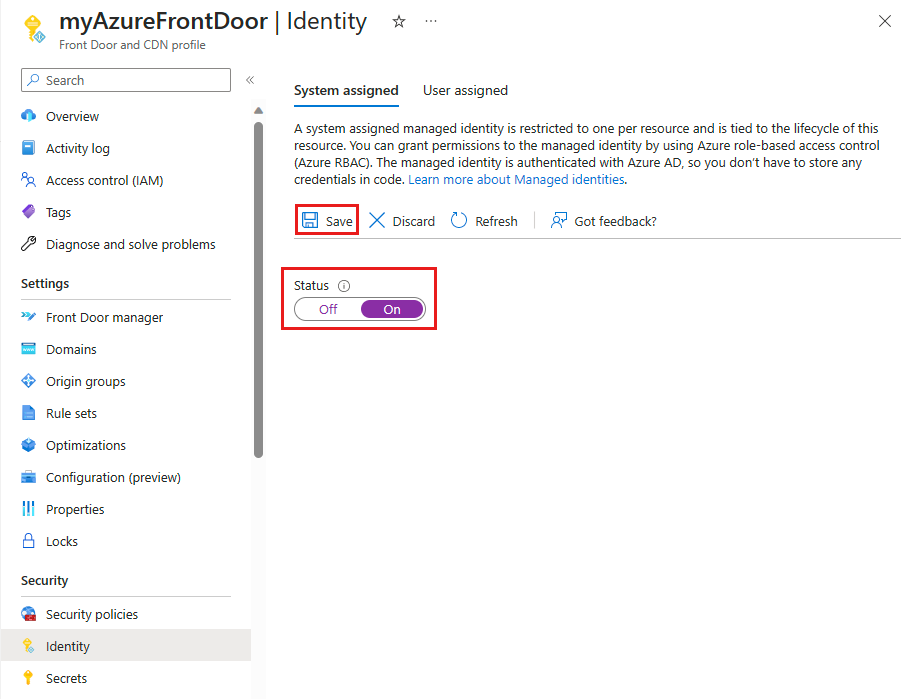
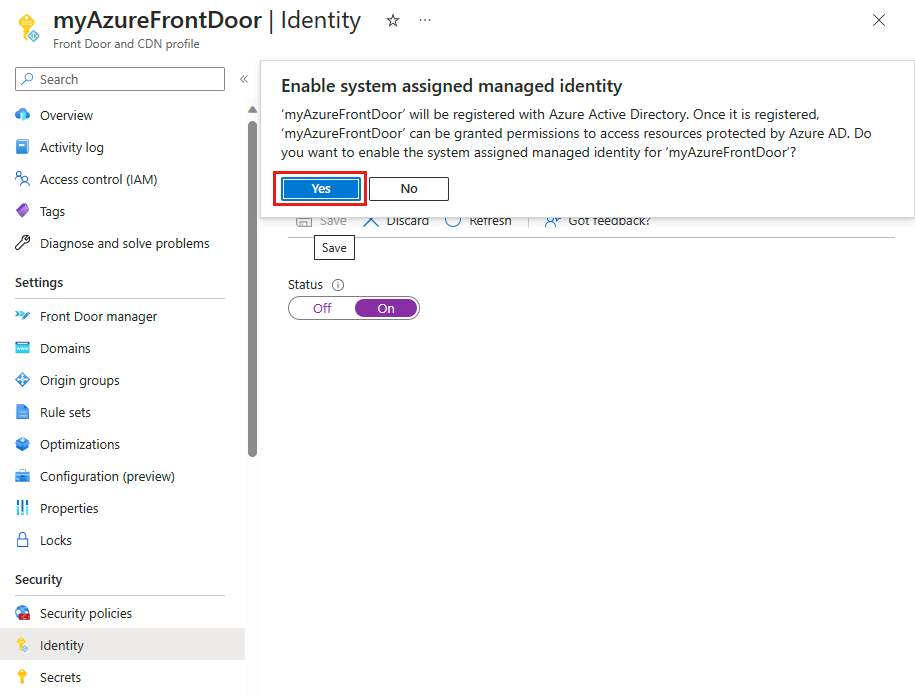
Confirm the creation of a system managed identity for your Front Door profile by selecting Yes when prompted.
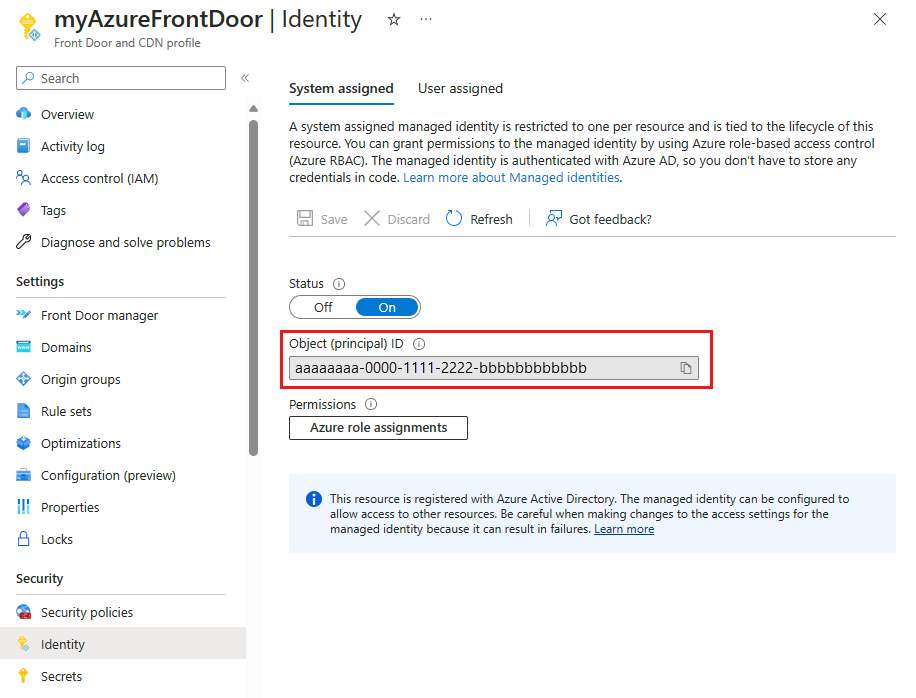
Once created and registered with Microsoft Entra ID, use the Object (principal) ID to grant Azure Front Door access to your Azure Key Vault.
User assigned
To use a user-assigned managed identity, you must have one already created. For instructions on creating a new identity, see create a user-assigned managed identity.
In the User assigned tab, select + Add to add a user-assigned managed identity.
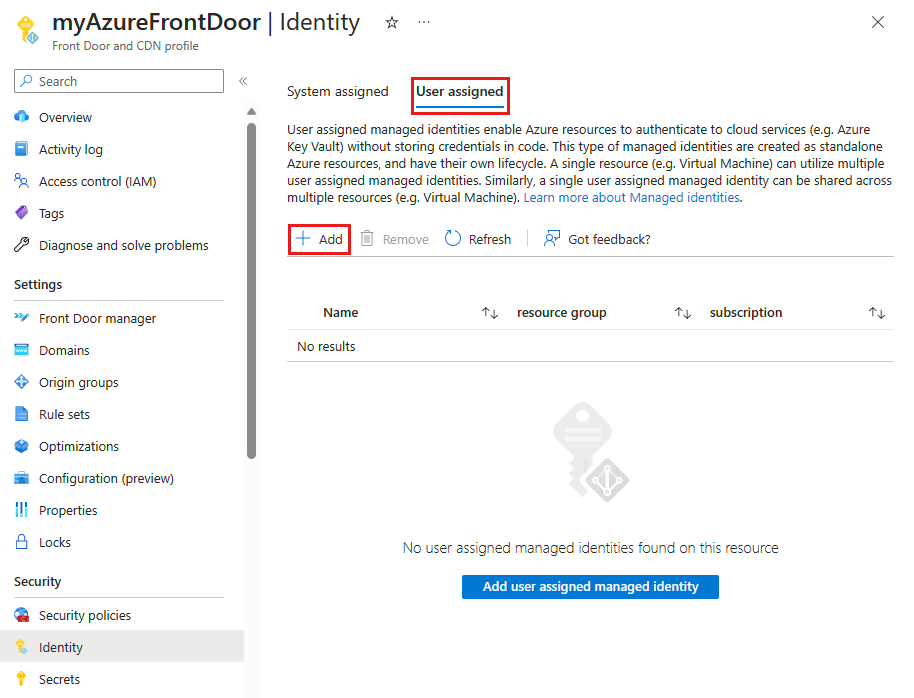
Search for and select the user-assigned managed identity. Then select Add to attach it to the Azure Front Door profile.
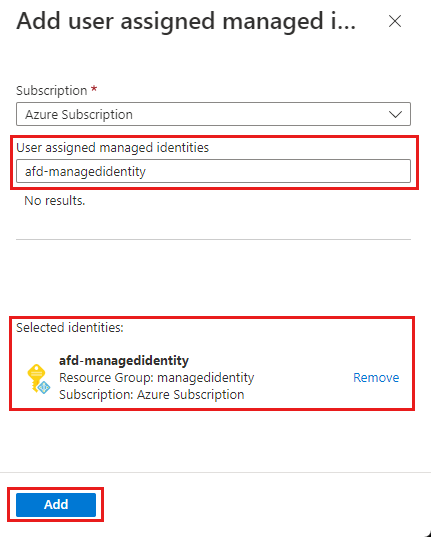
The name of the selected user-assigned managed identity appears in the Azure Front Door profile.
Configure Key Vault access
You can configure Azure Key Vault access using either of the following methods:
- Role-based access control (RBAC) - Provides fine-grained access control using Azure Resource Manager.
- Access policy - Uses native Azure Key Vault access control.
For more information, see Azure role-based access control (Azure RBAC) vs. access policy.
Role-based access control (RBAC)
Navigate to your Azure Key Vault. Select Access control (IAM) from the Settings menu, then select + Add and choose Add role assignment.
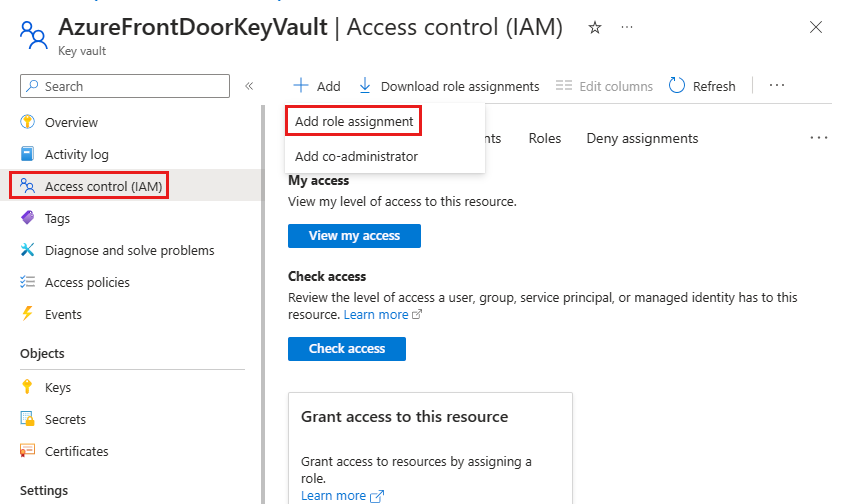
On the Add role assignment page, search for Key Vault Secret User and select it from the search results.
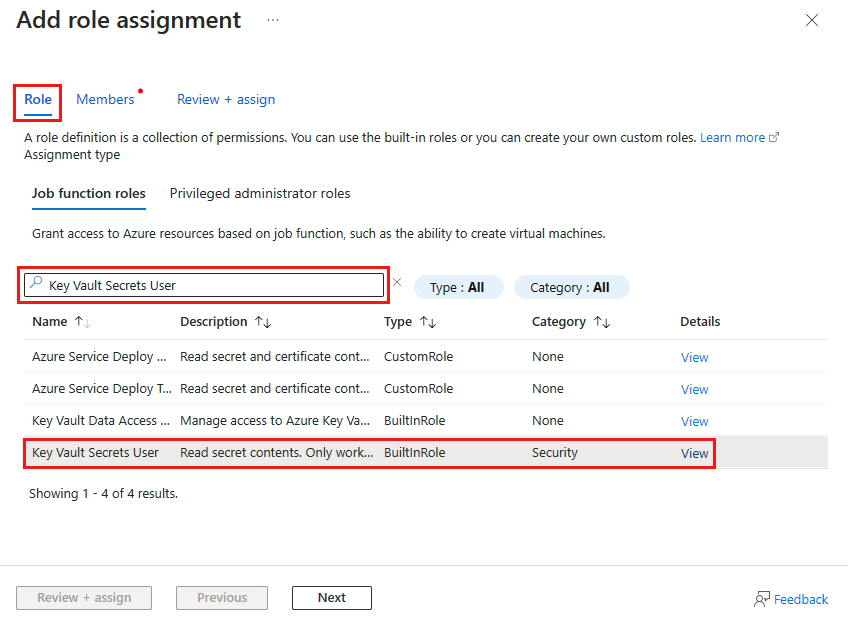
Go to the Members tab, select Managed identity, then select + Select members.
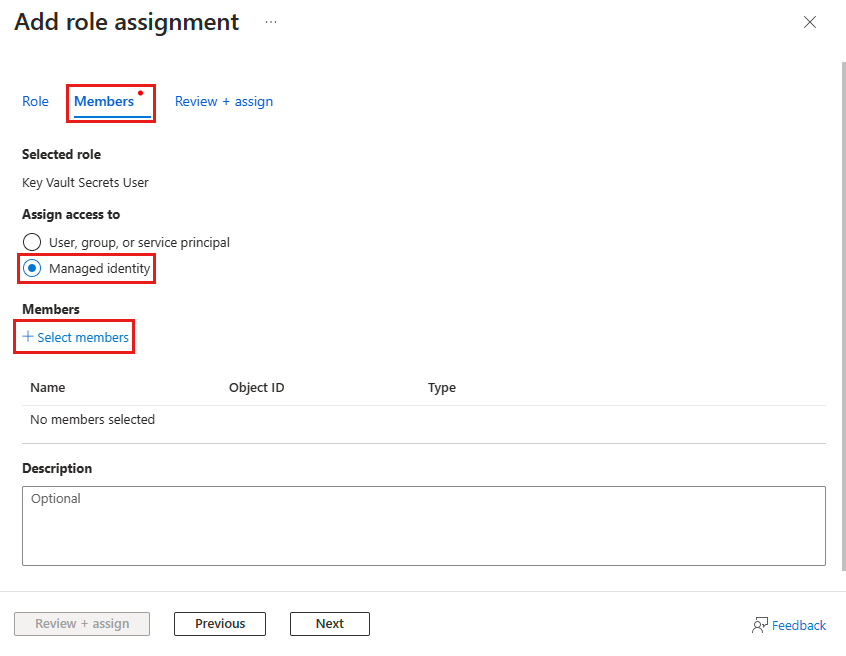
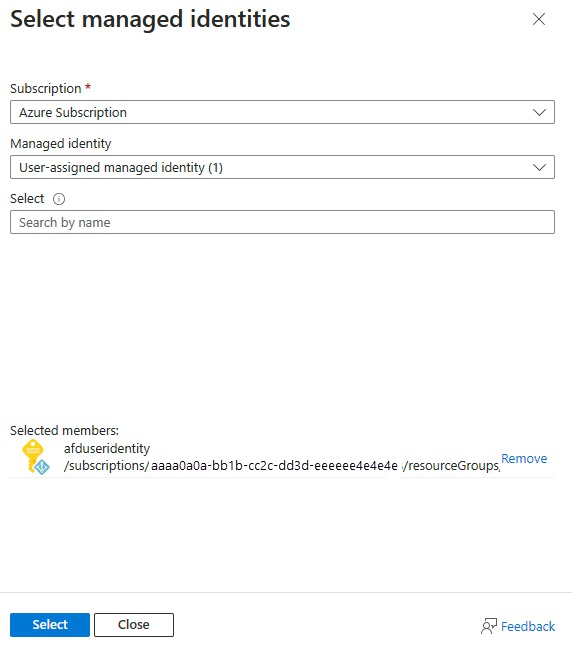
Choose the system-assigned or user-assigned managed identity associated with your Azure Front Door, then select Select.
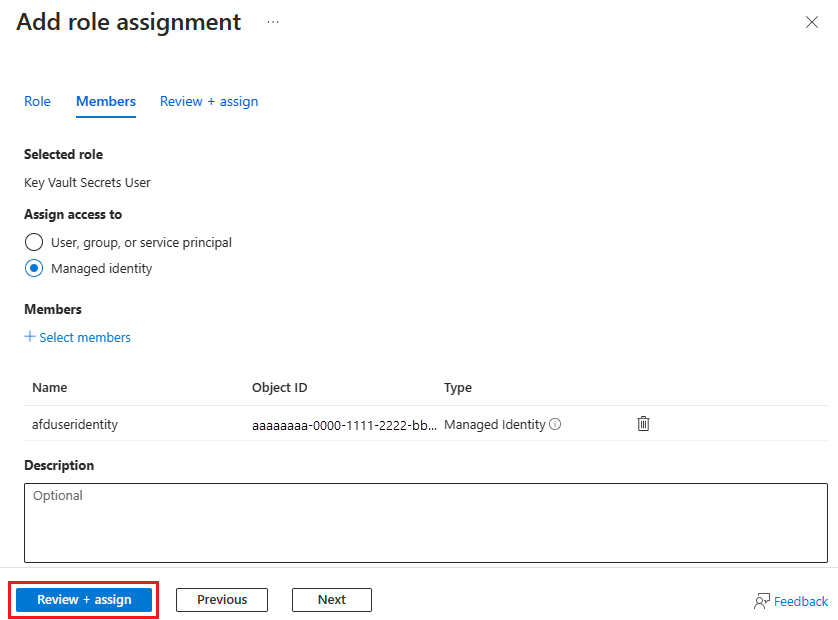
Select Review + assign to finalize the role assignment.
Access policy
Navigate to your Azure Key Vault. Under Settings, select Access policies and then select + Create.
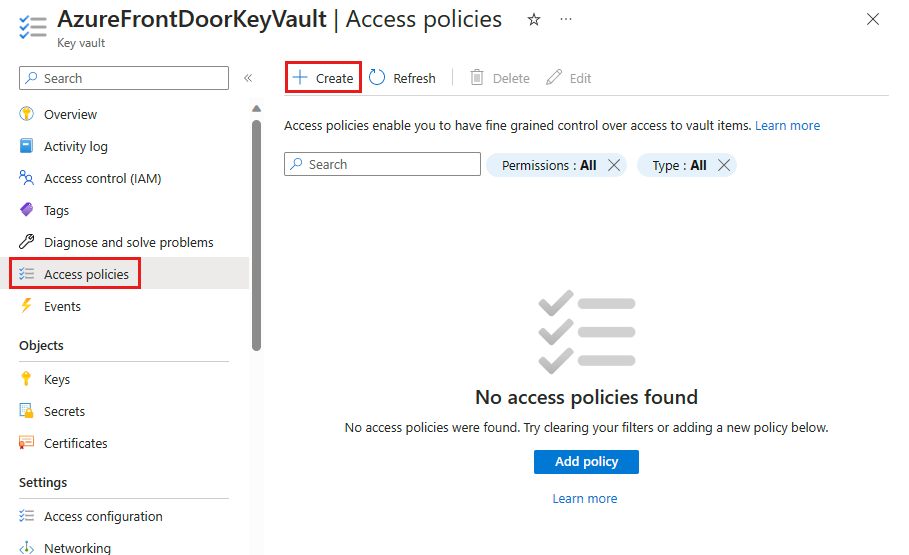
On the Create an access policy page, go to the Permissions tab. Under Secret permissions, select List and Get. Then select Next to proceed to the principal tab.
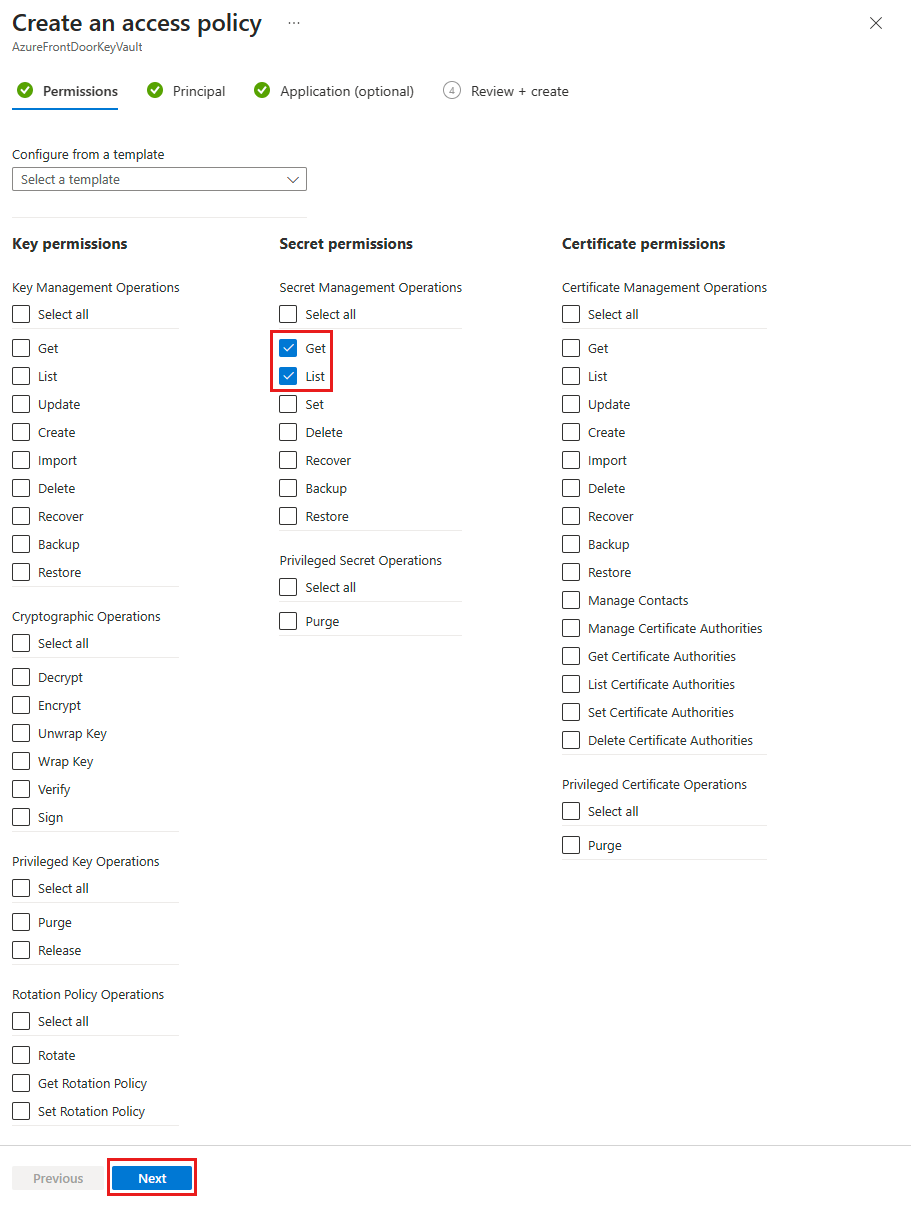
On the Principal tab, enter the object (principal) ID for a system-assigned managed identity or the name for a user-assigned managed identity. Then select Review + create. The Application tab is skipped as Azure Front Door is automatically selected.
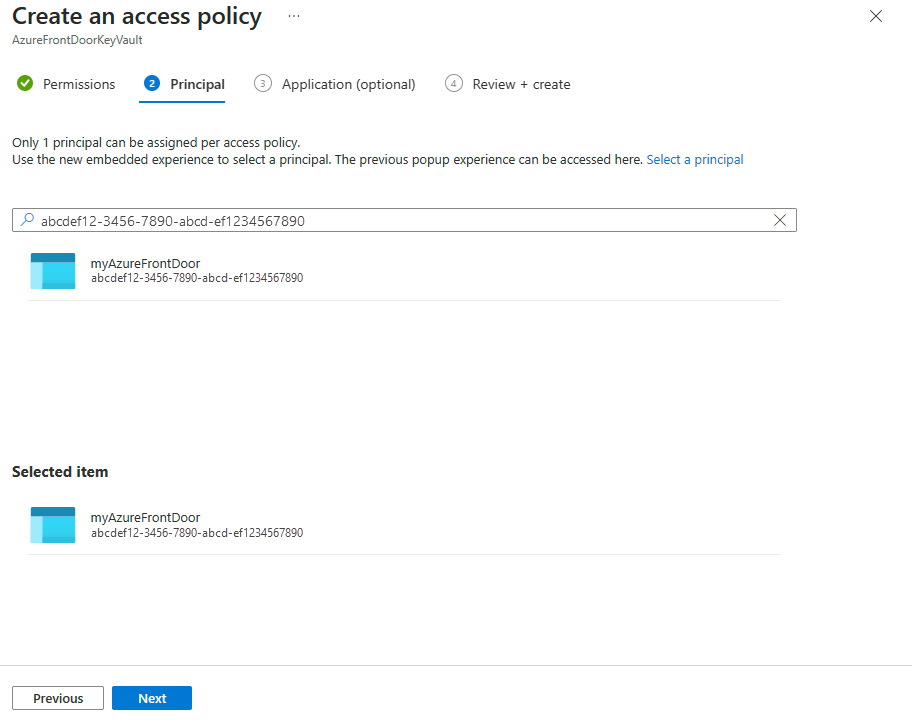
Review the access policy settings and select Create to finalize the access policy.
Verify access
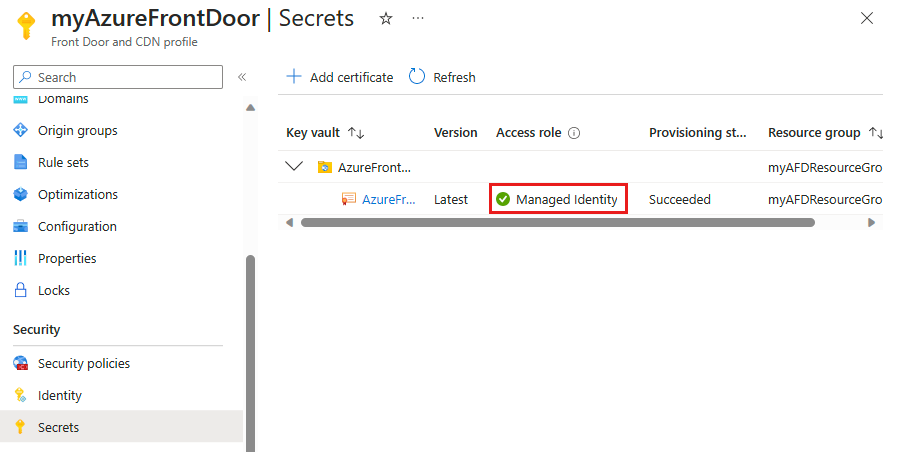
Go to the Azure Front Door profile where you enabled managed identity and select Secrets under Security.
Confirm that Managed identity appears under the Access role column for the certificate used in Front Door. If setting up managed identity for the first time, add a certificate to Front Door to see this column.
Next steps
- Learn more about End-to-end TLS encryption.
- Learn how to configure HTTPS on an Azure Front Door custom domain.