Use npm audit to detect and fix package vulnerabilities
Azure DevOps Services
The npm audit command performs a thorough scan of your project, identifying potential security vulnerabilities and generating a detailed report that highlights any issues found. Conducting security audits is a vital step in recognizing and resolving vulnerabilities within the project's dependencies. The npm audit fix command automatically addresses the detected vulnerabilities, updating insecure package versions to the latest secure releases. Addressing these vulnerabilities is crucial for preventing potential problems like data loss, service disruptions, and unauthorized access to sensitive information.
Warning
Executing npm audit will transmit the names of all packages specified in your package.json to the public registry.
Run npm audit locally
npm audit can be executed locally without needing to authenticate with your feed. This allows you to scan your project for vulnerabilities and receive a detailed report on the detected security issues and their severity.
If you want to fix the detected vulnerabilities, you can run npm audit fix, but you must be authenticated with your feed in order to do so. This command updates insecure package versions to the latest secure releases available.
When you run npm audit fix, it not only updates the local project's package.json and package-lock.json but also syncs these changes with the associated Azure Artifacts feed. The newly secured versions of the packages will be automatically available in your feed.
This synchronization ensures that other projects sharing the same feed will also benefit from these updates. It helps maintain a consistent and secure set of package versions across all projects.
Run the following command in your project directory to perform an npm audit:
npm auditIf you want to attempt to upgrade to non-vulnerable package versions, make sure you're connected to your feed first, then run the following command in your project directory:
npm audit fix
After running npm audit fix, make sure to conduct a thorough testing on your application to confirm that the updates didn't introduce any breaking changes. If a fix requires a major version update, it's recommended to review the package's release notes for any potential breaking changes. Keep in mind that while a private package with public vulnerable dependencies receives vulnerability alerts, it won't receive fixes through npm audit fix.
Note
npm audit automatically runs with each execution of npm install, but it only works for public packages.
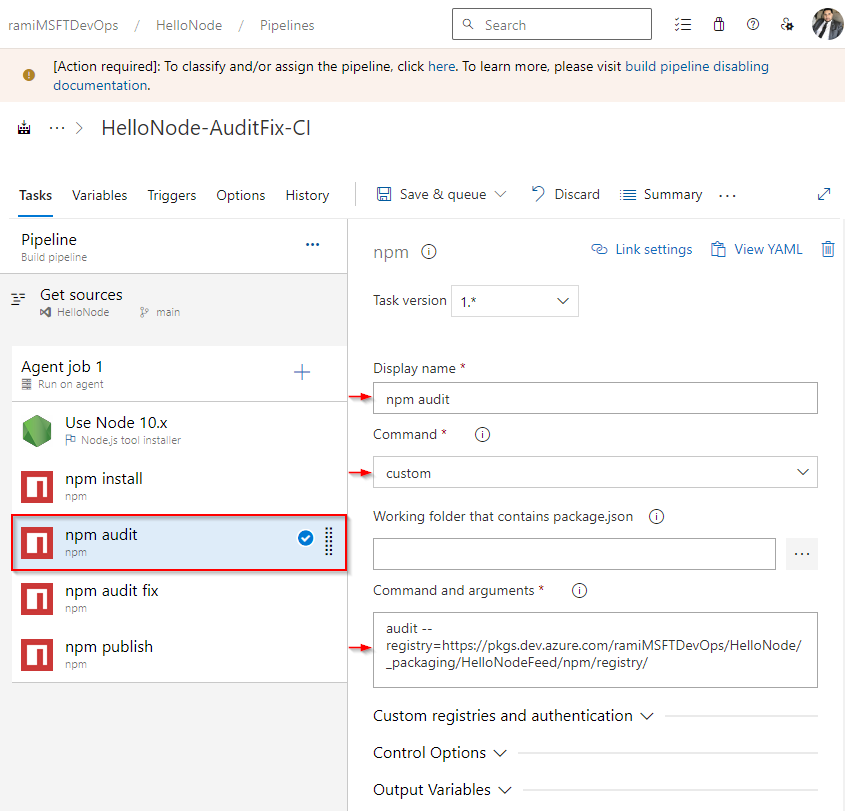
Run npm audit from your pipeline
Azure Pipelines doesn't currently support npm audit. If you try using the regular npm audit command in your pipeline, it will fail. Instead, execute npm audit with the --registry argument and provide your feed's source URL.
Sign in to your Azure DevOps organization, and then navigate to your project.
Select Pipelines, select your pipeline, and then select Edit to modify it.
From your pipeline definition, select the
+sign to add a new task.Search for the npm task, and then select Add to add it to your pipeline.
Enter a Display name for your task, and select custom from the Command dropdown menu.
Paste your custom command into the Command and arguments text box:
Use the following command to perform an npm audit and scan for package vulnerabilities. Replace the placeholder with your feed's source URL:
audit --registry=<FEED_SOURCE_URL>If you want to attempt to upgrade to non-vulnerable package versions, use the following command. Replace the placeholder with your feed's source URL:
audit fix --registry=<FEED_SOURCE_URL>